The Future of Work is Hybrid. What Does That Mean for IT Teams?
In the debate over whether the future of work should be remote or in-office, the answer increasingly appears to be “neither—and at the same time, both.”
Even as they prepare their offices for return-to-work, companies are announcing that employees will have more options to work from home. More than half of office workers say they won’t return to jobs that do not offer remote work or hybrid options.
Whether you call it “remote-first,” “remote-friendly,” or “flexible,” the bottom line is the same. Some people will be in the office, some will not—and they need to be able to work together, wherever they are.
The hybrid workplace: a cybersecurity nightmare?

IT teams can see the hybrid future coming—and they don’t expect it to be easy. Over half (53.4%) of IT professionals say the ongoing management of remote and hybrid workers is one of their biggest challenges, according to a survey by JumpCloud.
CTOs and tech journalists have called hybrid work a “cybersecurity nightmare” and “the worst of both worlds.”
But is it? Or is it another opportunity for IT to prove its indispensable role in the future of work? While it’s true that the hybrid workplace presents its challenges, it also lets IT teams reimagine organizational information architecture.
The global workforce has started a new chapter of what it means to “do work,” and IT teams sit squarely at the center of this paradigm shift.
Let’s talk about what that means—and what IT teams should do in light of it.
More devices, more networks, more risks
On a practical level, a hybrid work environment means that employees will work on more devices and from more networks than ever before. IT’s first challenge is to develop systems that allow them to effectively manage this technology sprawl.
“The biggest risks remain #data visibility and user behavior,” wrote Microsoft security architect Wayne Anderson on social media. “Today, organizations need to think about what that surface is and where the data is stored and flows.”
“The biggest risks remain #data visibility and user behavior.”
—Microsoft security architect Wayne Anderson
Bring Your Own Device (BYOD) policies were already in place long before the coronavirus pandemic. But in a hybrid world, BYOD will become BYOE—Bring Your Own Everything. Not only will employees sign on using their own computers and phones—they’ll be working from personal WiFi networks while using their own webcams, headphones, and other devices.
It’s not just more devices, either—hybrid workers will also utilize more software on those devices. Teams operating with some coworkers in the office, some at home, and others around the world, will need the right software to make this possible.
Collaboration tool use has grown 44% since 2019, and with the increase of product-led growth and bottoms-up sales models, end-user employees are increasingly able to adopt software on their own, without IT teams being involved or even aware.
More hardware and software means more points of exposure. More points of exposure mean more opportunities for company systems to be infiltrated and exploited.
Some of these cybersecurity threats are new. For example, Zoombombing became a phenomenon during the pandemic. Remote work meant more organizations using the video conferencing tool. More traffic led to more threat actors exploiting vulnerabilities in Zoom’s software to infiltrate company systems.
Hybrid work also leaves the door open for cybercrime’s greatest hits; phishing and ransomware incidents both increased as employees worked from home.
The cost of a breach increased as well—up to $21,659 per incident on average and $1 million or more in as many as 5% of cases.
Faced with the logistical headaches that hybrid work presents, it’s tempting from an IT perspective to want to lock everything down, and impose the most secure—and restrictive—policies possible.
But there’s a business case to be made that this isn’t the best approach.
The business case for a hybrid workplace
The year-plus-long experiment in working from home gave analysts an opportunity to track the business impact of different approaches to remote-first work.
What they’ve found: fast, frequent, and easy technology adoption may be the difference between success and failure in a hybrid world.
A study by McKinsey showed that businesses that improved performance during the pandemic—a group it calls “Organizational Resilients”—adopted technology “faster and more often than Non-Resilients.”
According to the survey, “nearly 60% of the executives… at Organizational Resilients believed that their organizations made collaboration technologies easy to adopt, versus just a quarter of Non-Resilients.”
Hybrid workplaces can help organizations stay resilient and reach their bottom lines through positive retention rates, more effective use of office space, and maintaining or even increasing employee productivity.
Ensuring equal access for remote workers is a Diversity, Equity, and Inclusion (DEI) consideration as well. Parents, people of color, and people with disabilities are more likely to want or need a remote or flexible workplace. However, they have expressed concerns that this could harm their chances of recognition and advancement. Overly restrictive technology policies may interfere with remote employees’ ability to be as effective at their jobs as their in-office counterparts.
Improving organizational DEI is a worthy goal in and of itself. But, it has also proved to have tangible effects on business outcomes. For example, businesses with a racially diverse workforce are 36% more likely to outperform the median for financial performance than non-racially diverse companies, according to McKinsey.
If offering hybrid work options makes the workplace more profitable, competitive, and inclusive, businesses would be smart to have a hybrid-friendly technology infrastructure in place.
The new hybrid work environment needs transparency to be effective. But that transparency can’t come at the expense of IT teams tasked with keeping the business’s systems functional and secure.
The trick for IT teams will be to design systems and policies that strike the balance between enabling connectivity and collaboration—and ensuring stability and security.
The question is: How do they do that?
Hybrid work will take a hybrid approach
Just like there’s no one right way to work, there’s no one policy that can perfectly guarantee a secure work environment. Companies need a hybrid approach to manage hybrid work effectively, utilizing a combination of education, process, and tools.

Three ways to manage a hybrid workforce
- Educate employees to make informed technology choices
- Implement clear policies and processes regarding technology use
- Adopt tools that provide IT with visibility and control
1. Educate end-user employees
Employee education is an IT team’s first and best weapon when it comes to managing endpoint threats.
It’s no secret in IT that a business’s greatest vulnerability is its users. After all, almost “85% of successful data breaches involved defrauding humans, rather than exploiting flaws in computer code,” according to CBS News.
The first step for IT teams who want to ensure safe and productive hybrid work is to give employees the information they need to keep from contributing to that 85%.
The more employees understand the basics of front-line information security, the more effective they’ll be at preventing breaches at the source.
Some IT basics to teach employees about include:
- How do phishing attempts happen?
- How do you recognize a suspicious-looking email?
- What is company policy regarding software updates?
- What are best practices regarding sharing company systems and information with outside vendors?
This is particularly important as IT shifts toward more of a self-serve model, with individual employees making decisions like what software to adopt and who to share company data with, without IT oversight.
That said, there’s no need to overdo it when it comes to educating team members about potential threats.
“I don’t think [users] need to be paranoid,” Google chief internet evangelist Vint Cerf told VentureBeat. “But for the same reason that you don’t walk into traffic without looking in both directions—in case somebody else isn’t paying attention—you need to be thoughtful in the online environment for the same kinds of reasons.”
More: How to Prevent Network Security Threats
2. Implement clear policy & process
The next area where IT teams should focus is making sure that IT security policies and processes reflect the new hybrid reality.
That’s especially true for governing how company data is accessed and shared. IT needs to ensure it has policies and processes that make this manageable.
One particularly important area is identity and access management (IAM) protocols. With more employees working remotely, it will be critical to ensure that the people accessing company systems have proper authorization to do so. In fact, 70% of business executives plan to increase IAM spending in the next year, according to one study.
IT will also need to implement crystal clear policies and processes around how new tools are adopted and who can access them. While teams may increasingly implement tools without IT input, that shouldn’t exempt them from IT oversight.
“As these applications become more interwoven and interoperable, there’s going to be, at the very least, the need for some kind of cross-functional team to help ensure that governance and administration is done in concert with other parts of the business,” said Christopher Trueman, principal research analyst at Gartner.
Access control systems will become an increasingly important part of the IT tech stack as the workforce grows more and more distributed. The more teams rely on documentation and tools to work collaboratively across geographies and time zones, the more vital it becomes for IT to have the tools needed to effectively monitor and administer those systems in real-time.
More: What is an access control system, and why do you need it?
3. Adopt tools that enable real-time visibility and response
The final piece in the “make hybrid work” puzzle is for IT teams to adopt tools allowing them to monitor company technology use across a multitude of networks, devices, and tools.
In the hasty pivot to work from home, many organizations prioritized productivity over security. One survey by Palo Alto Networks found that 44% of IT professionals say their organization made investments to improve remote access to company networks—but invested relatively little in remote security.
That’s a risky trade-off to make—one that teams will need to correct now that remote work is no longer a stopgap, but a staple of how people work.
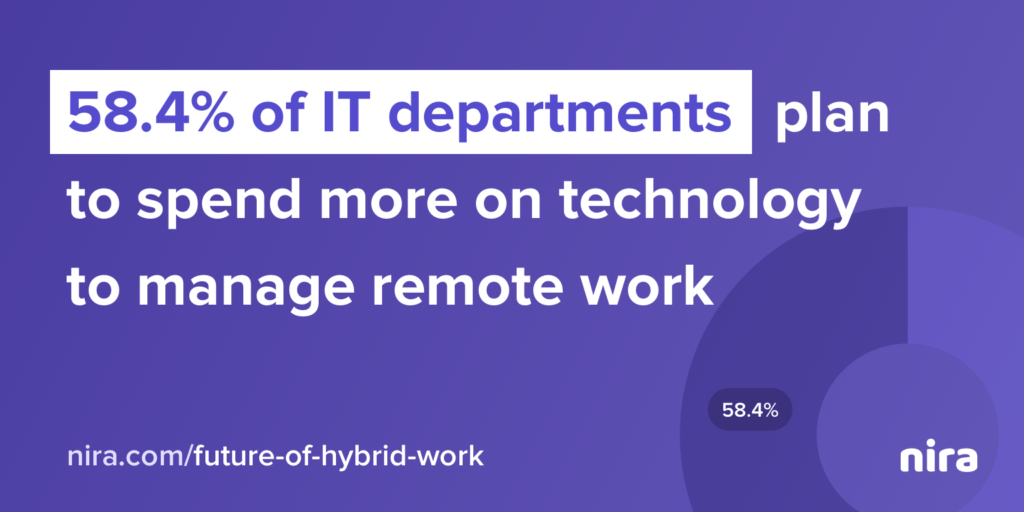
Fortunately, it appears many organizations have gotten the message. More than half (58.4%) of IT departments “plan to spend more on remote management technologies as they navigate the hybrid environment,” according to JumpCloud.
As for what kinds of remote management technologies IT teams should be looking to implement? There are two things teams should explore: visibility and control.
“If you don’t have real-time visibility into endpoints, threats will remain unknown and continue to propagate. You can’t stop what you have no visibility into.”
— Ben Rothke, IT leader at Tapad, on social media.
That last part is key: for IT teams to be effective at securing the hybrid future, it’s not enough for them to be able to identify threats—they need to be able to act on them, too. That’s a big part of why we’ve built Nira: the more we worked with companies on helping employees find documents, the more we learned that their biggest problem wasn’t finding documents—it was managing who had access to their crucial data.
Designing the hybrid workplace with IT in mind
We’ve talked before about IT’s central role in building the future of work, and nowhere is that more clear than in designing the hybrid workplace. With more people working on more devices than ever in the history of internet-enabled work, IT teams are fundamental to a company’s security infrastructure.
Fortunately, tools are available that make the information sprawl a little more manageable; it’s why we designed Nira in the first place. To learn more about access control, why it matters more than ever in a hybrid world, and how Nira can help, reach out for a demo.

