The State of IT Access Management
Access Management has become a critical issue for IT and Security leaders, as they are tasked with safeguarding millions and even upwards of billions of sensitive assets. With an increasing number of cyber threats and data breaches, IT and Security teams must maintain control over who has access to what valuable information, and must understand how to secure access in the complex landscape of cloud-based environments and applications.
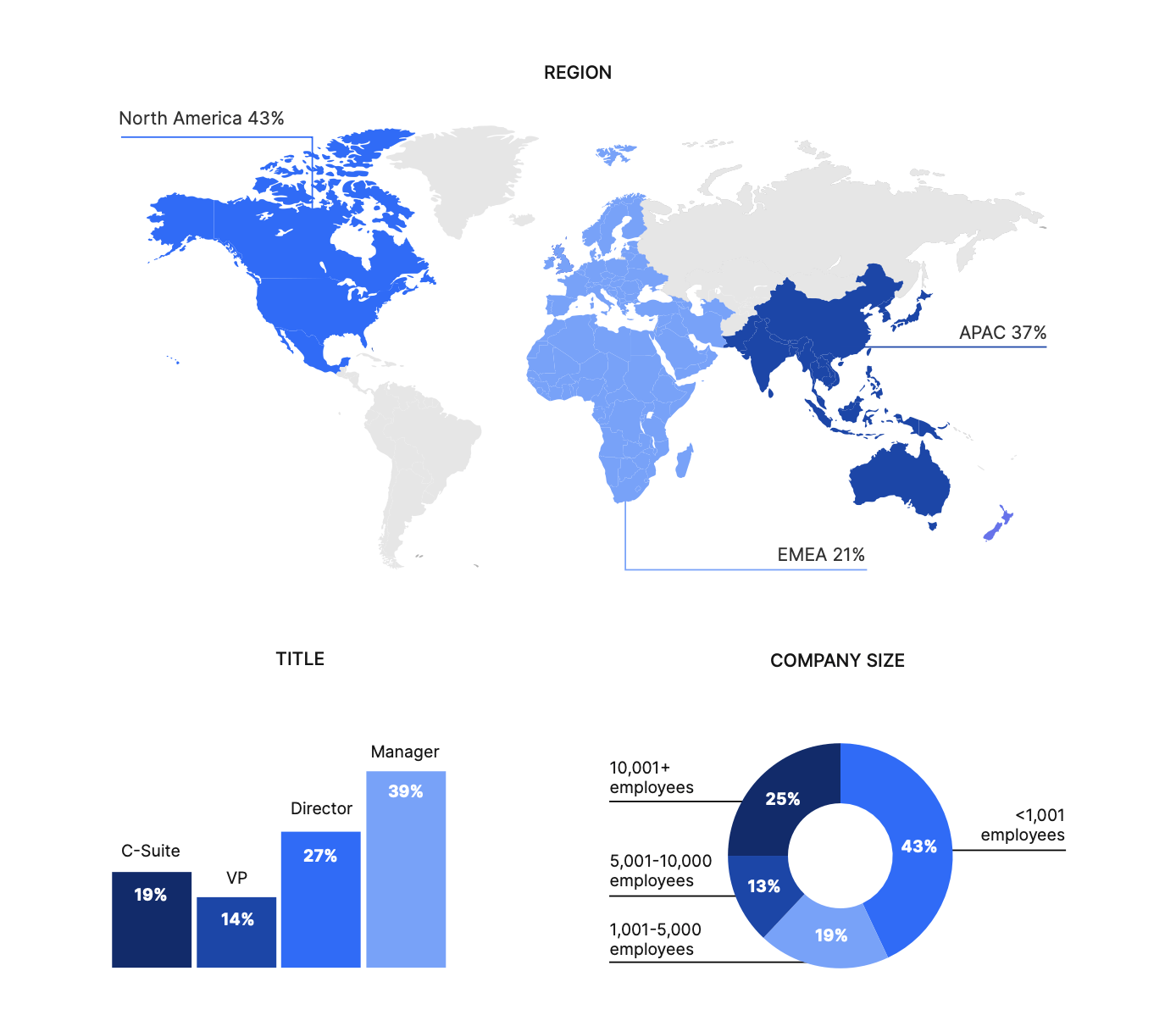
Nira utilized Gartner Peer Insights to ask 518 IT decision-makers about the state of IT Access Management and how organizations are making collaboration more secure for everyone.
IT Access Management is critical
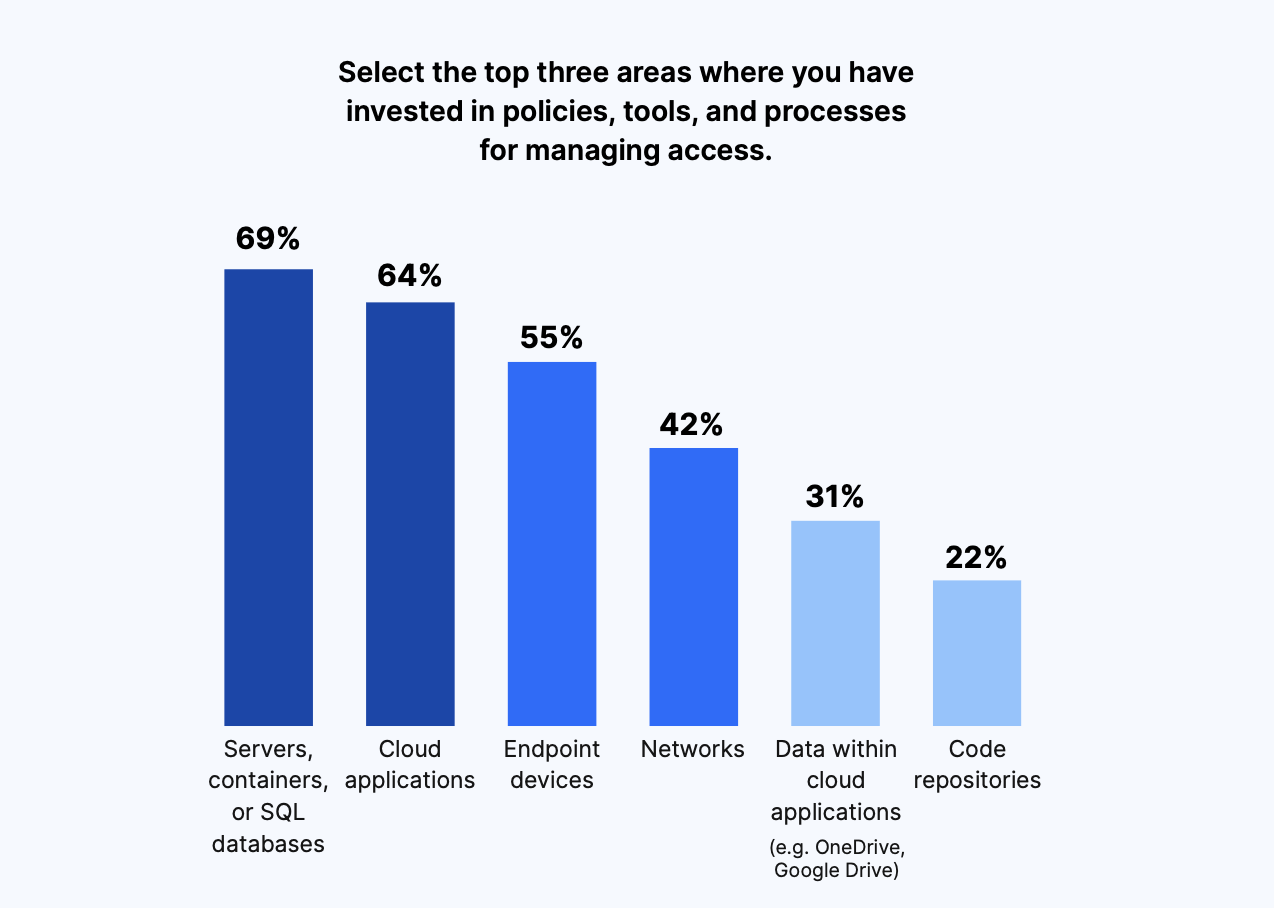
Today, the bulk of IT Access Management investment is going to the usual suspects. We found that the top three areas decision-makers were investing in policies, tools, and processes for managing access included servers, containers, or SQL databases (69%), cloud applications (64%), and endpoint devices (55%).
Meanwhile, only 31% were investing in managing access to data within cloud applications like OneDrive and Google Drive, and only 22% were doing this for code repositories.
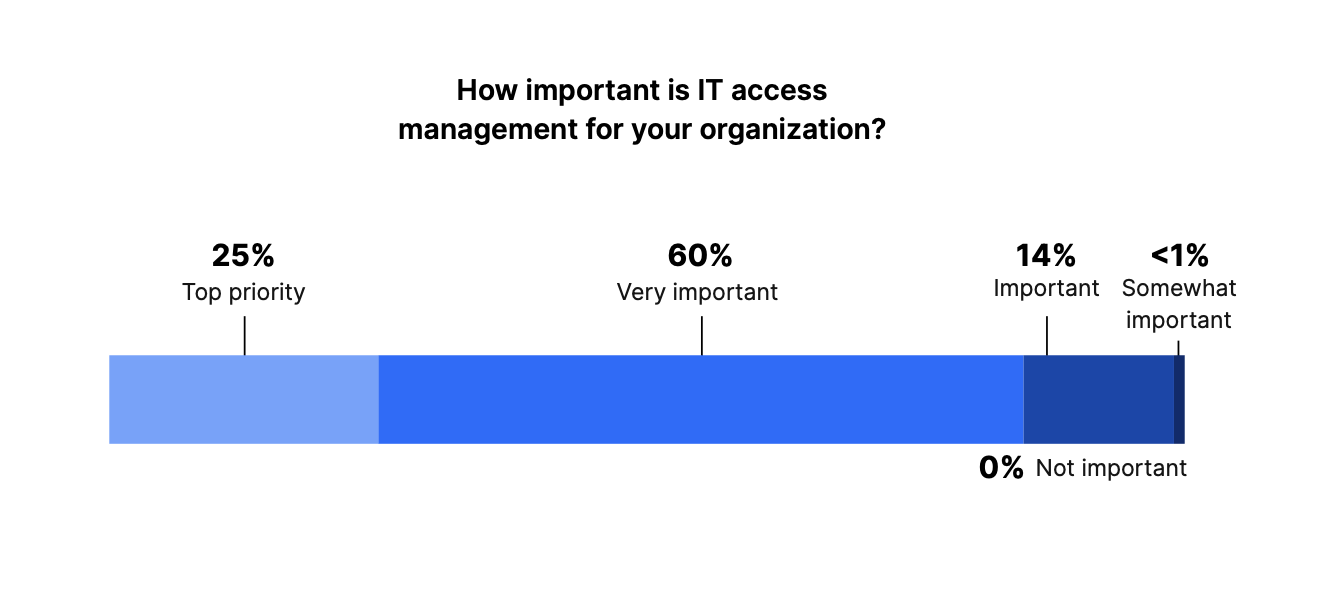
When asked, “How important is IT access management for your organization,” 25% of respondents said it was a top priority, while 60% said it was very important. Only 15% of IT and Security leaders viewed it as moderately important, and none of those surveyed deemed it not important.
Investments in IT Access Management show no signs of slowing down
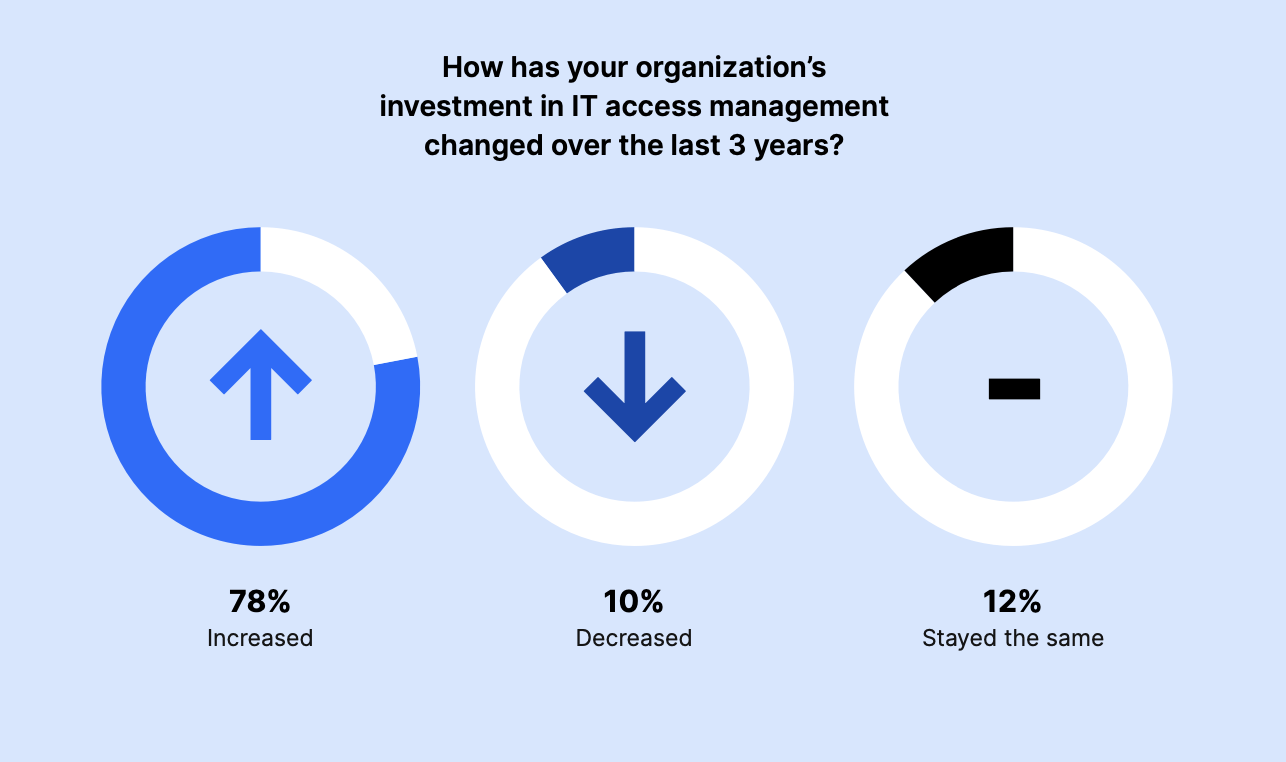
The majority of survey participants (78%) said they’ve increased their investment in IT Access Management over the last three years, while 12% maintained the same level of investment. Only 10% decreased their investment.
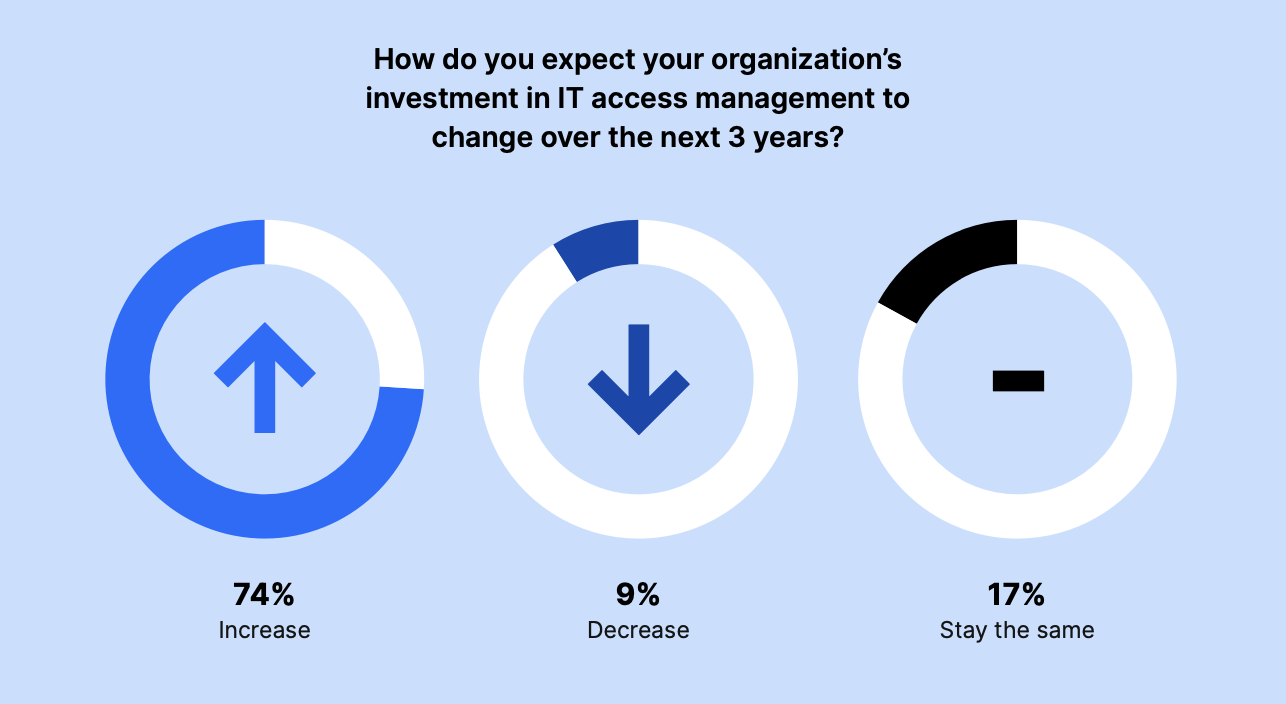
Just 26% of respondents expected their IT Access Management investments to decrease or stay the same over the next three years. The majority of leaders (74%) were planning for increased investment in the coming years.
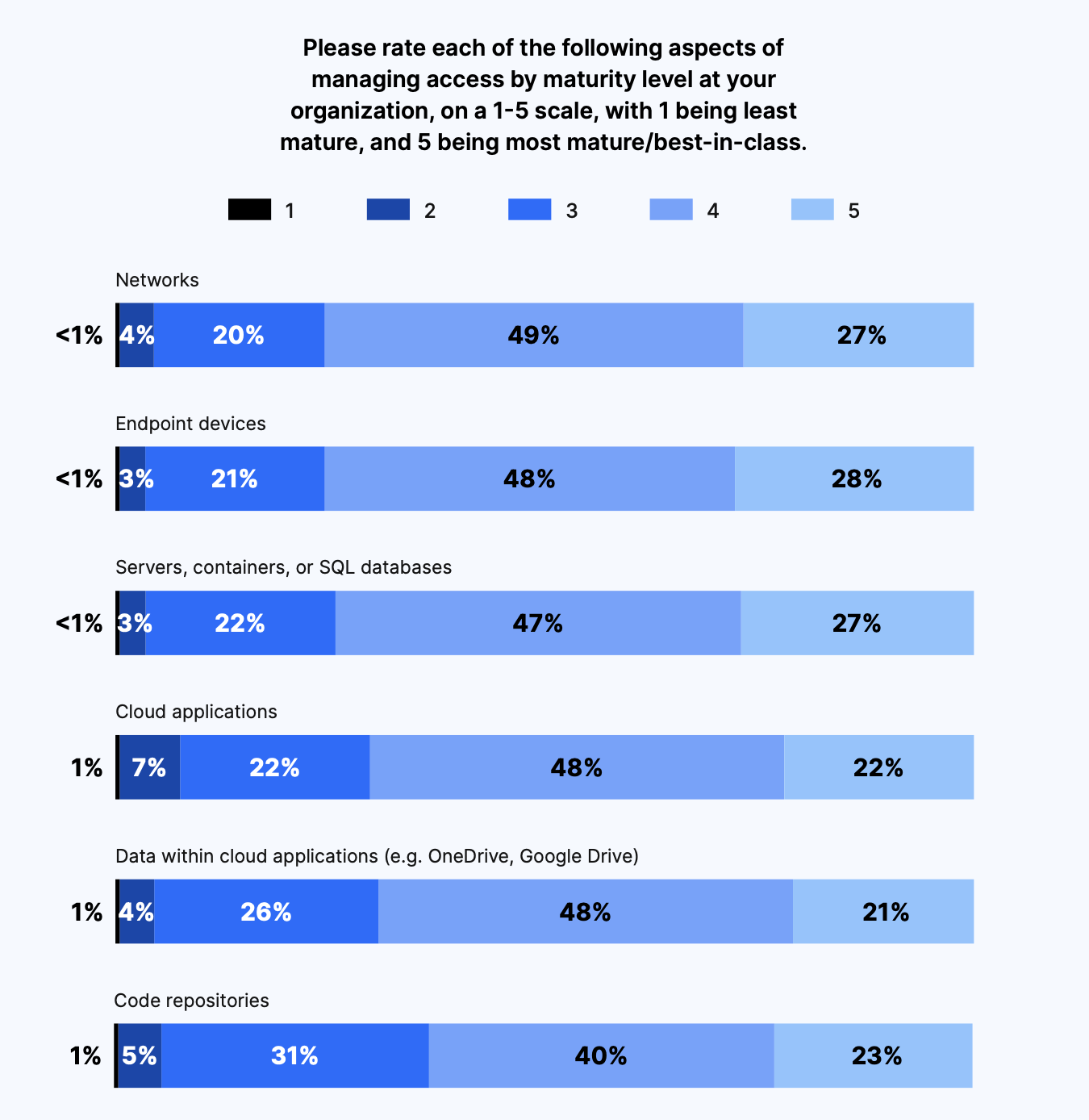
Access Management is fairly mature and confidence in cloud application tools and processes is high
The aspects of access management rated most mature were networks and endpoint devices. And those rated least mature were code repositories and data within cloud applications like OneDrive and Google Drive. This tracks with investment in tools, processes, and policies for managing access, which was lowest for data within cloud applications and code repositories.
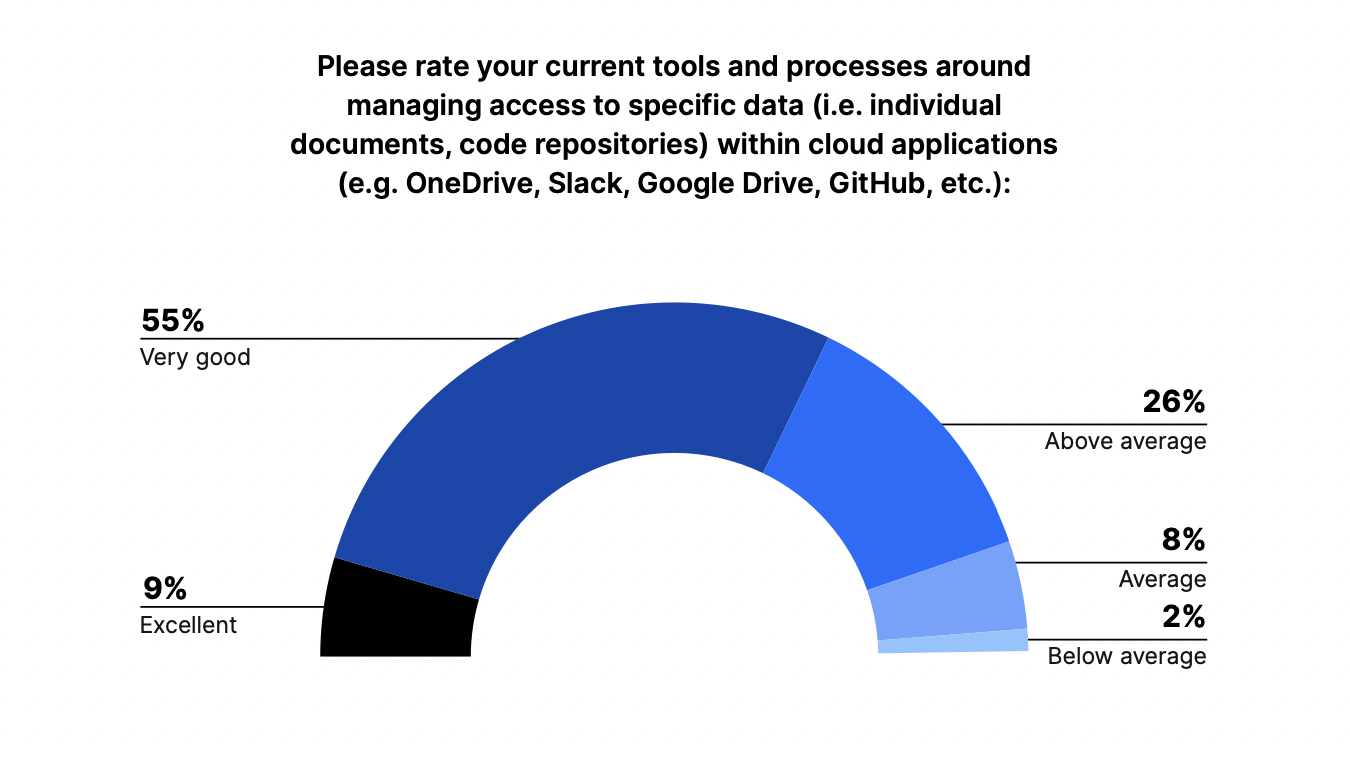
However, we found that IT leaders’ confidence in the tools and processes they used to manage access to data in cloud applications appeared to be above average.
Despite being considered a less developed aspect of access management, only 10% of respondents viewed their tools and processes for managing specific data within cloud applications as average (8%) or below average (2%). Over half (55%) viewed them as very good, and 9% viewed them as excellent. Twenty-six percent viewed themselves as being above average in this type of access management.
It appears that although IT and Security leaders are investing less in access management of data within cloud applications and code repositories, and rate themselves as less mature at access management in these areas, most (64%) believe they are either excellent or very good at managing access to that data.
Cyberattacks and data exfiltration leave IT leaders concerned about securing access to data stored in cloud collaboration applications
Sixty-five percent of IT and Security leaders expressed high levels of concern for securing access to data stored in cloud collaboration applications, despite seeming confident in their current tools and processes. Just 10% were slightly or not at all concerned. And 25% were only moderately concerned.
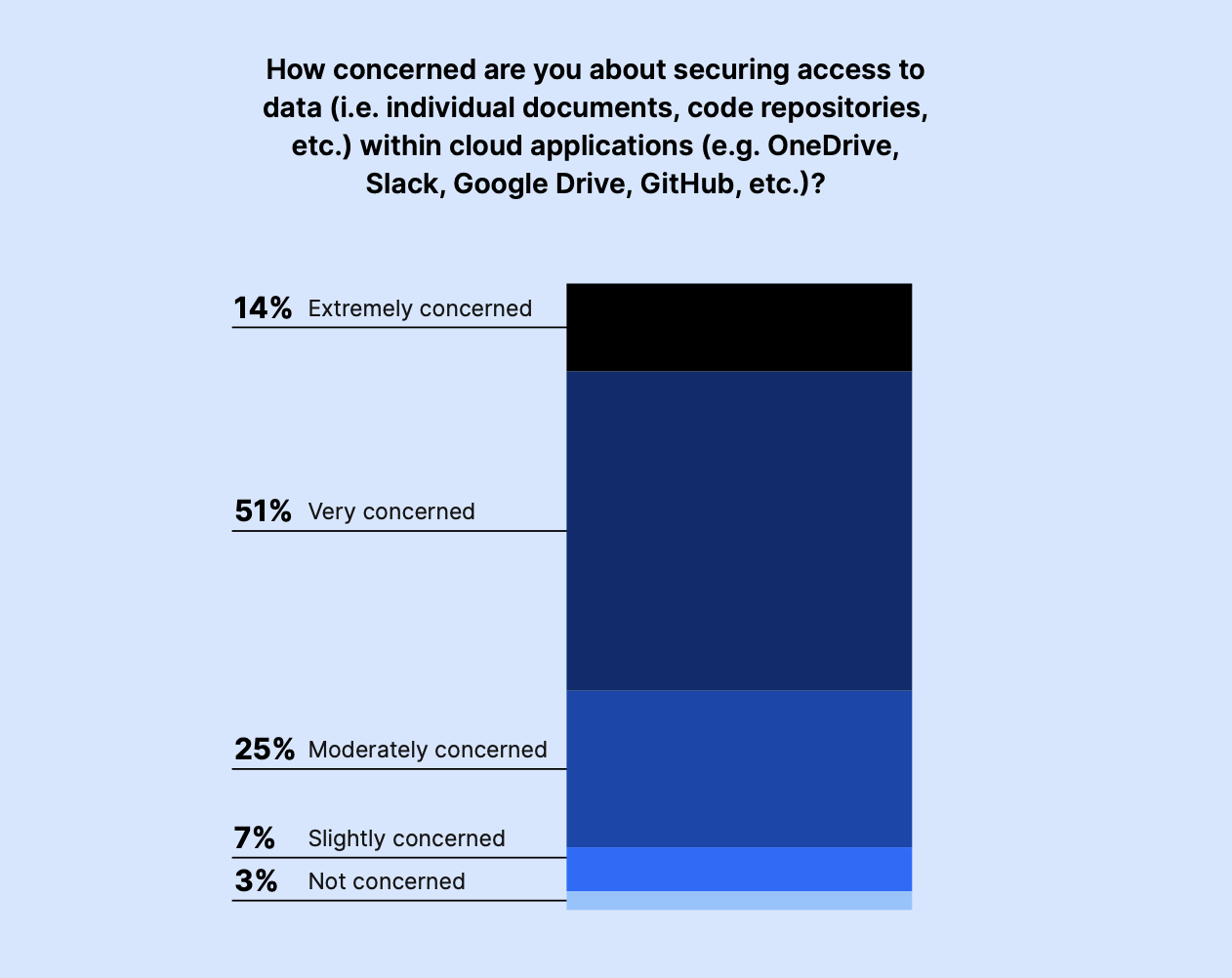
With an uptick in cyberattacks and data breaches, we’ve found that IT and Security leaders want to be proactive when securing access to their data. They may not have full visibility into their risks in cloud collaboration environments or need better tooling to gain comprehensive control.
When asked to further explain their level of concern, the top answers were:
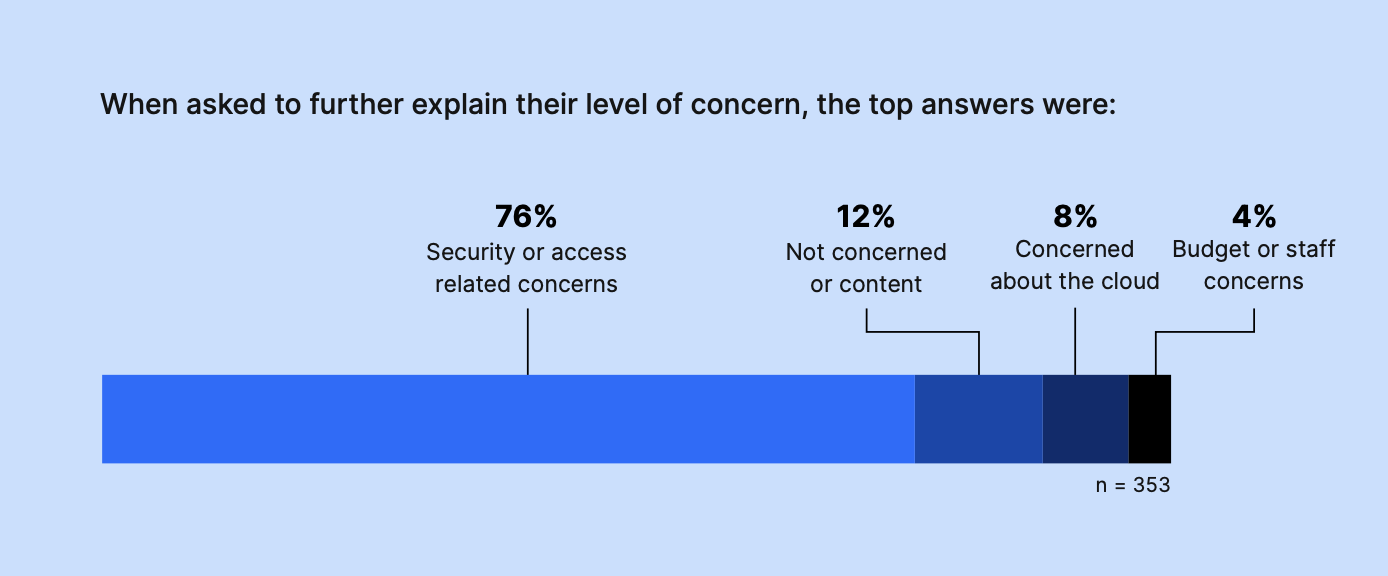
- Security or access-related concerns 76%
- Not concerned or content 12%
- Concerned about the cloud 8%
- Budget or staff concerns 4%
Here’s what a few respondents had to say:
“The amount of company data in an employee’s Google Drive is hard to measure. When one leaves, it’s very difficult to determine what data they may have there and how to get it to the appropriate people.”
– Director, Educational Services, North America, 201 – 500 employees
“With no centralized Access Management controls it is hard to manage disparate systems and maintain good security posture.”
– C-Suite, Professional Services, North America, 201-500 employees
“There is no disputing the value of data access. Because it serves as the foundation for everything we do, particularly in the digital era.”
– Manager, Educational Services, APAC, 5,001 – 10,000 employees
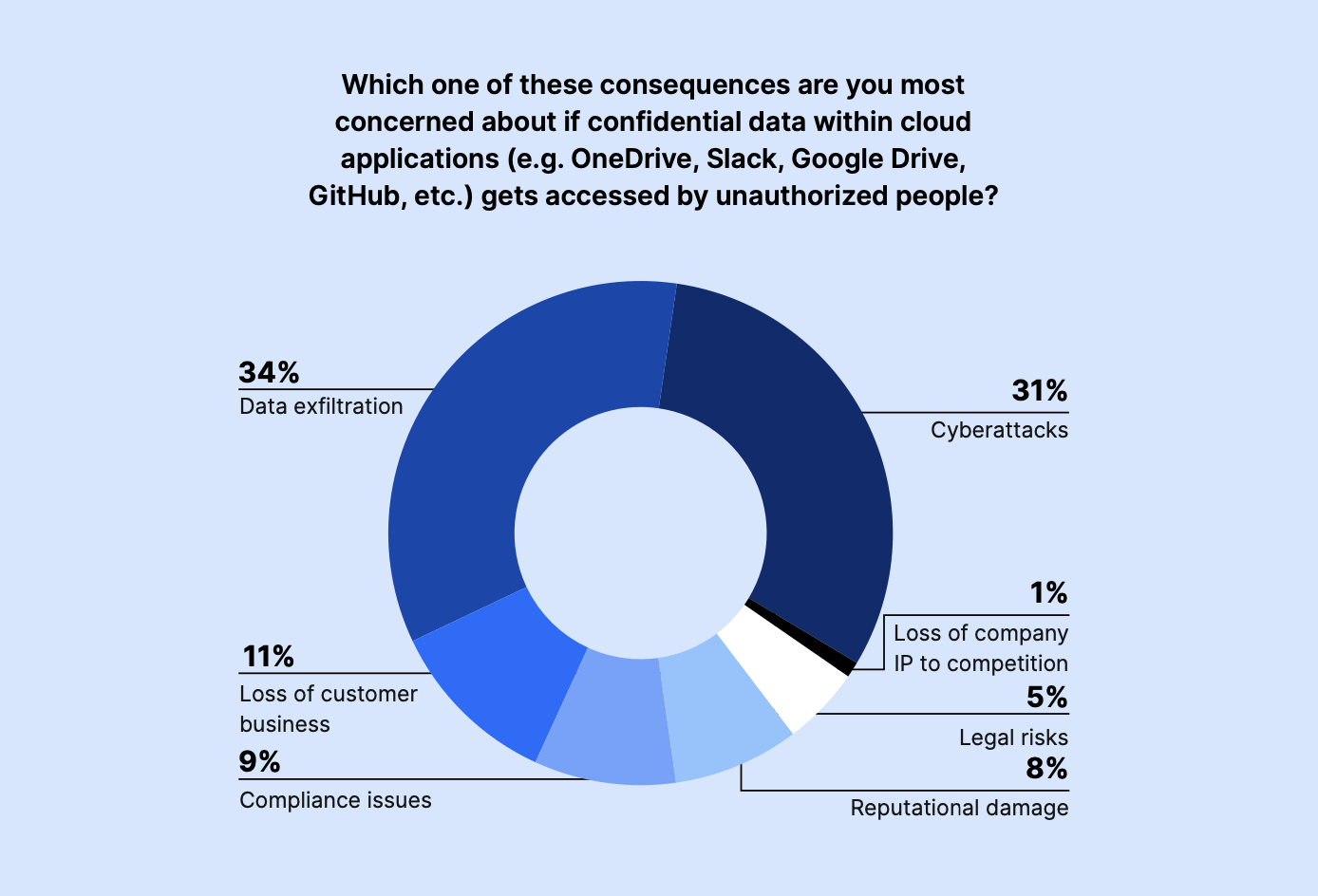
When asked what they were most concerned about if confidential data within cloud applications like Slack, OneDrive, GitHub, and Google Drive were accessed by unauthorized parties, top concerns cited included data exfiltration (34%) and cyberattacks (31%). The loss of customer business (11%) and compliance issues (9%) also worried IT and Security leaders.
Meanwhile, reputational damage (8%), legal risks (5%), and loss of company IP to competition (1%) seemed to be lower priorities for the majority of respondents surveyed.
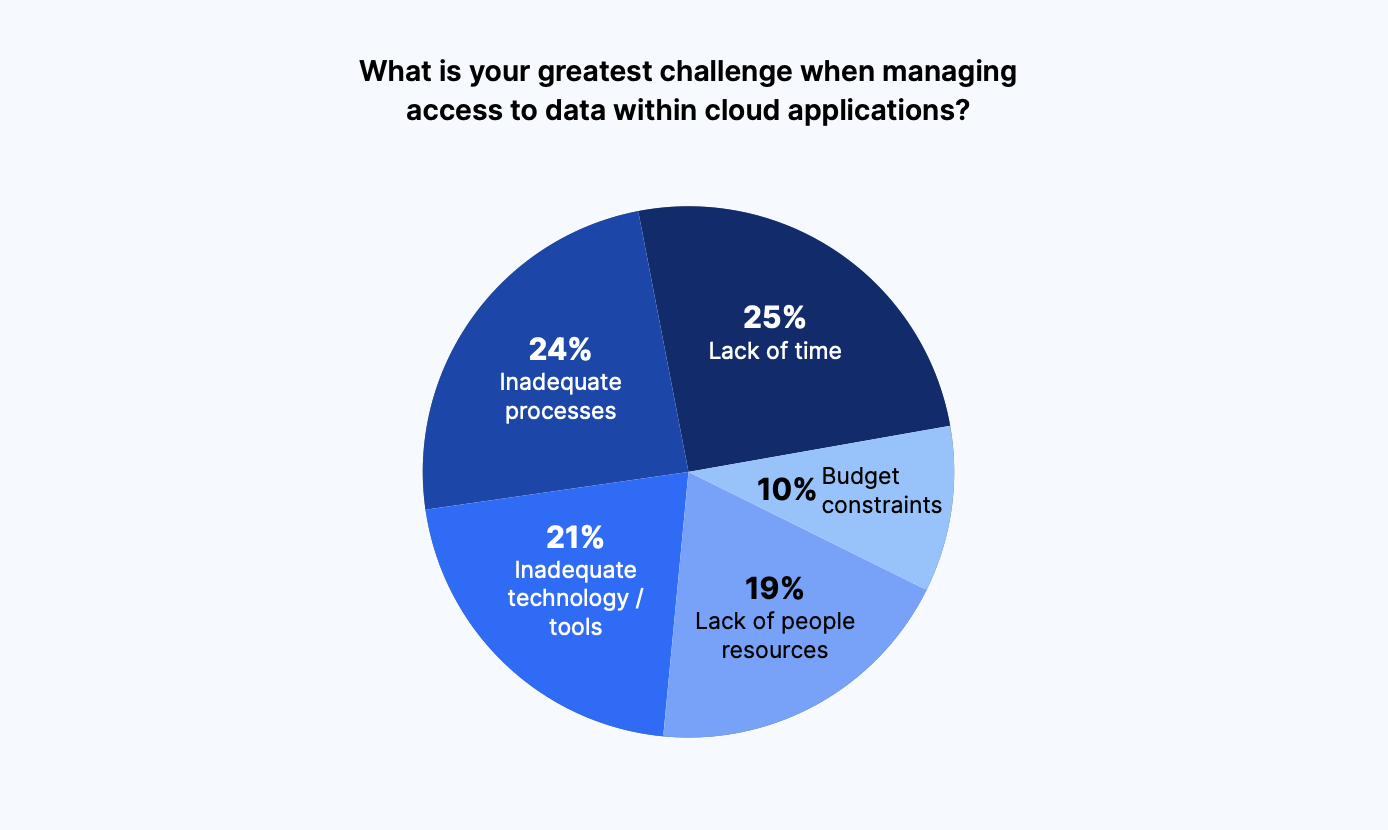
Lack of time (25%) was the greatest challenge faced by leaders when managing access to data within cloud applications, followed by inadequate processes (24%).
Inadequate technology/ tools (21%) and lack of people resources (19%) were close behind, and budget constraints came in at 10%.
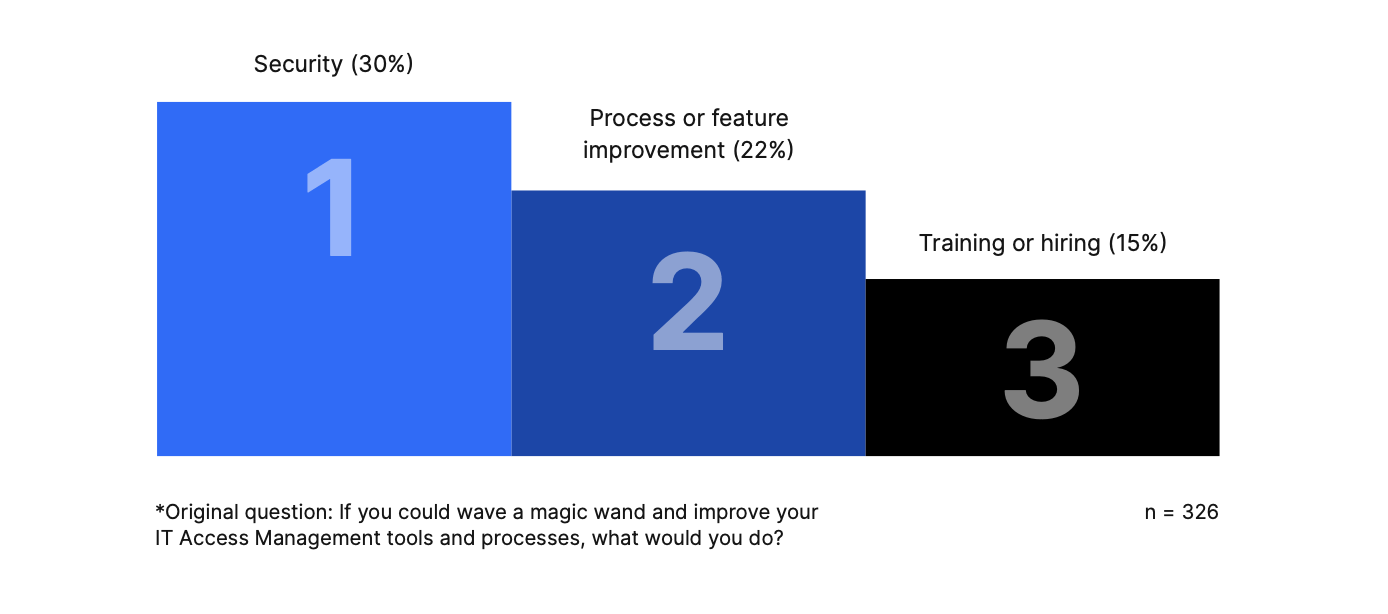
When asked “If you could wave a magic wand and improve your IT Access Management tools and processes, what would you do?”, the most common responses were to improve 1.) security, 2.) processes or feature improvements, and 3.) training or hiring:
Respondents said:
“Increase visibility to all data across the world if services are out there. We have no easy way of discovering data out there that IT has not been involved in the setup of.”
– Manager, Healthcare, EMEA, 201 – 500 employees
“Review the entire process and tooling. Oftentimes we are patching a known process to make it work with changing needs. That’s a business reality but if I had a magic wand, I would take the time to look at everything top to bottom and change what’s needed.”
– Manager, Telecommunications, North America, 10,000+ employees
“Have more people and configure every application, system and SaaS platform to utilize centralized authentication and authorization.”
– Director, Manufacturing, North America, 1,001 – 5,000 employees
IT and Security teams are swamped. They don’t have time to waste on manual processes when dealing with IT Access Management.
As a result, many organizations are seeking automated solutions to help manage and secure their data, which can provide more efficient and effective protection against potential risks.
By relieving some of the administrative burdens on their teams, IT and Security leaders can allow them to focus on risks that truly matter, and even improve overall efficiency throughout the business.
To ensure the protection of vital company and customer data, organizations must take a proactive approach to IT Access Management. This includes having complete visibility into potential risks, and the ability to quickly and efficiently address them. Solutions that can manage and secure access to a wide range of cloud-based applications and environments are essential for IT and Security teams.
Overall, IT Access Management is a continuous process that requires a proactive mindset, regular monitoring, and constant updates to safeguard sensitive information.
About Nira
Nira is a Cloud Document Security system that provides complete visibility and management over who has access to your company documents in Google Workspace and more. Nira provides a single, comprehensive view of who has access to valuable cloud-based company data. It allows you to easily find and identify risks, quickly control access and fix issues, and efficiently automate the process through policy enforcement and remediation delegation. Nira also enables employees to manage and control who has access to their information, without needing technical expertise.
Respondent Breakdown