The State of Information Security: Tools, Budgets, and Bandwidth
As information security risks increase, so do the rising pressures felt by IT and Security leaders. Despite solutions and teams tasked with addressing these threats, a lack of bandwidth is placing immense stress on organizations of all sizes.
Nira utilized Gartner Peer Insights to sample 500 IT decision-makers and understand their perspective on information security risks. The following report covers the current state of the tools, budgets, and bandwidth needed to tackle the information security challenges that companies face today.
Information security risks are increasing, along with IT workloads and budgets
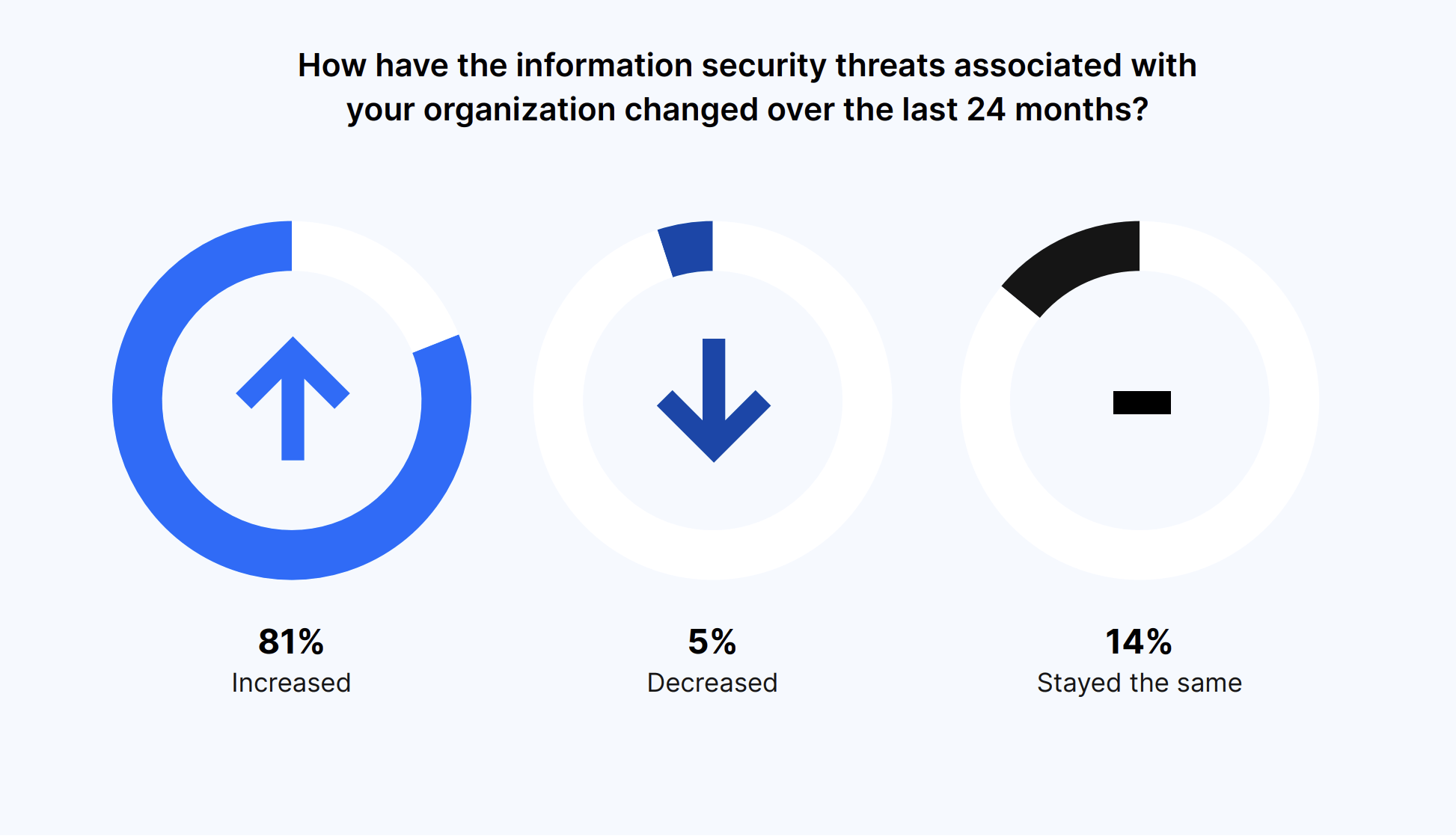
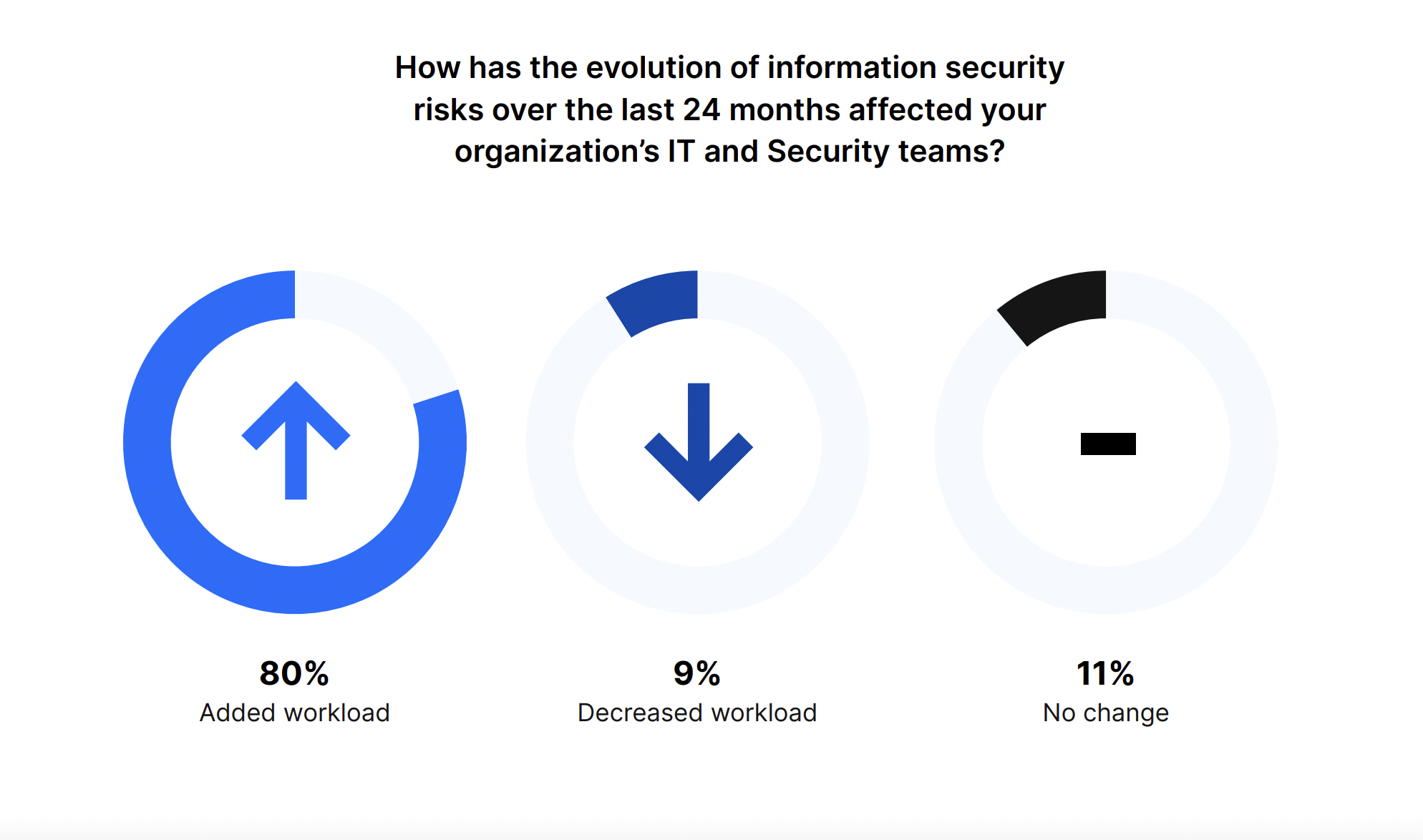
The majority of organizations (81%) saw a rise in information security threats over the past 24 months, which highlights the ongoing need for thorough cybersecurity measures. And 80% of IT and Security teams had to deal with a greater workload thanks to these growing threats.
IT and Security teams are overwhelmed with a large number of competing priorities. And economic challenges, as well as the increasing risks and workloads, are only exacerbating the situation.
Despite a slowdown in the current economic climate, 36% of decision-makers are still hiring cybersecurity professionals. Only 8% are planning to reduce their team size, while over half (56%) will keep their same team but stop hiring for now.
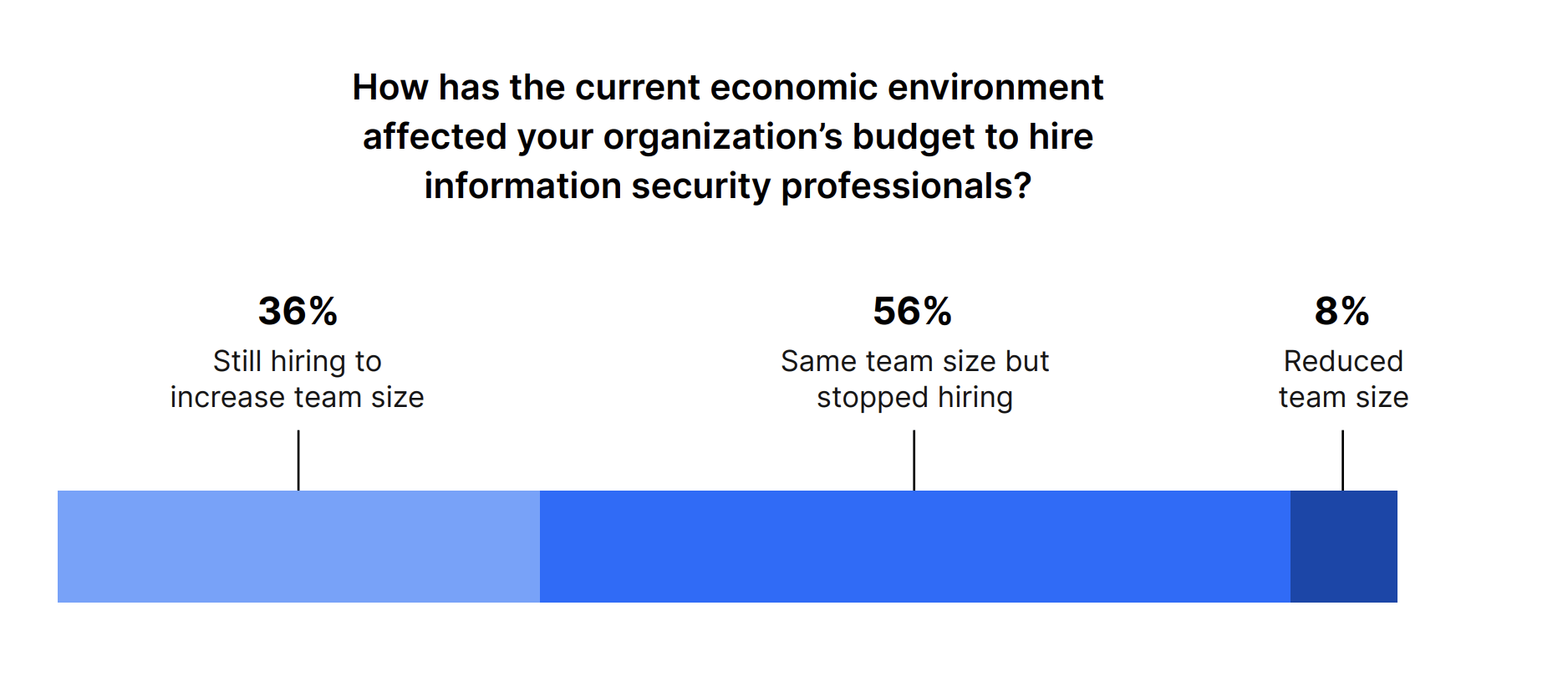
IT and Security leaders remain resolute in investing in cybersecurity initiatives, determined to stay a step ahead of potential breaches and attacks.
There has been a surge in budgets allocated to information security tools, underscoring the growing importance of safeguarding digital assets. A surprising 68% of respondents reported a notable increase in budget, reflecting a commitment to fortifying information security measures.
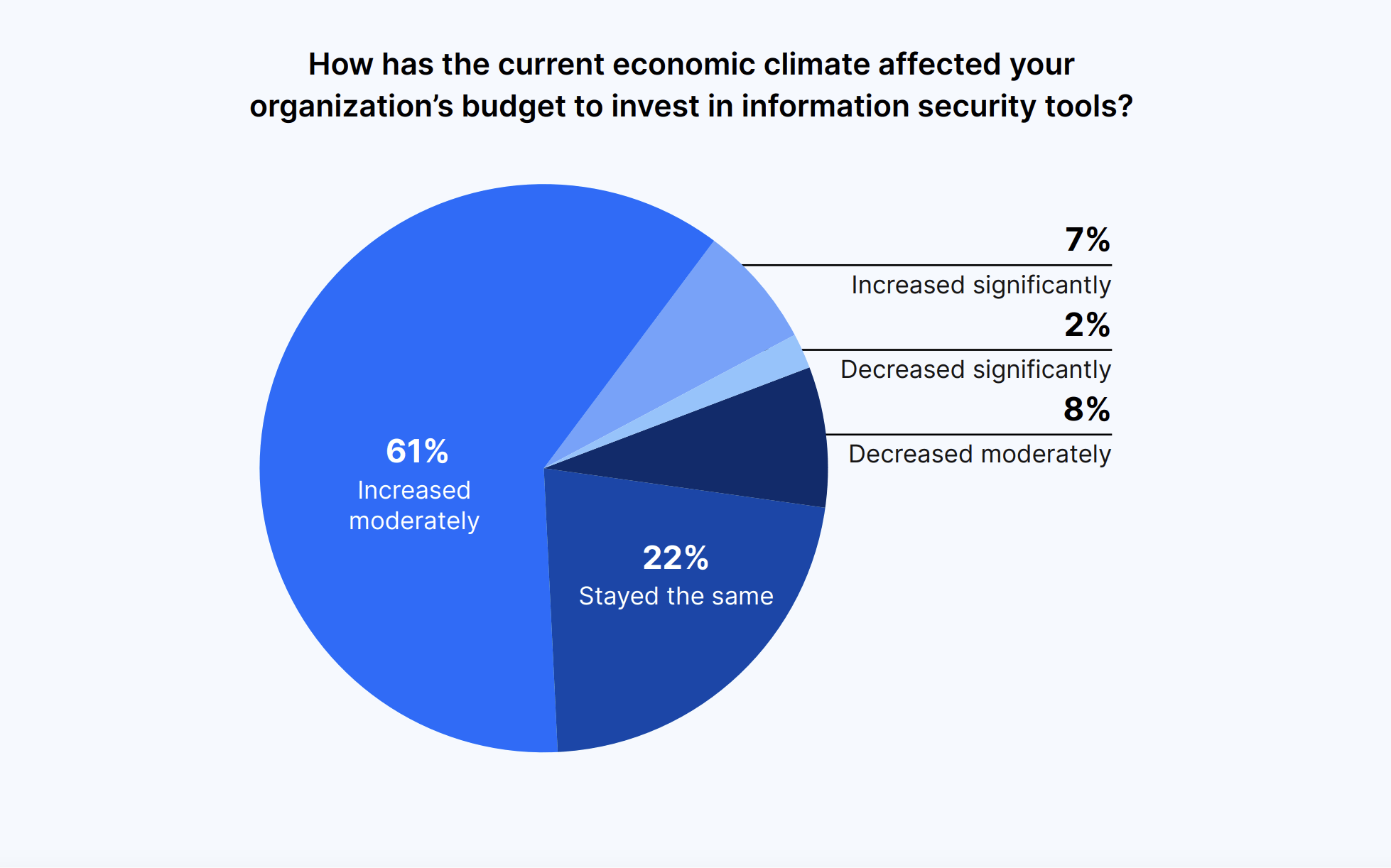
This increased investment not only demonstrates a proactive stance against threats but also signifies a shift in organizational priorities toward data protection. By allocating resources to information security, IT and Security leaders are actively working toward creating a security landscape that can withstand the substantial increase in risks.
Managing risks and manual work take up valuable IT and Security time
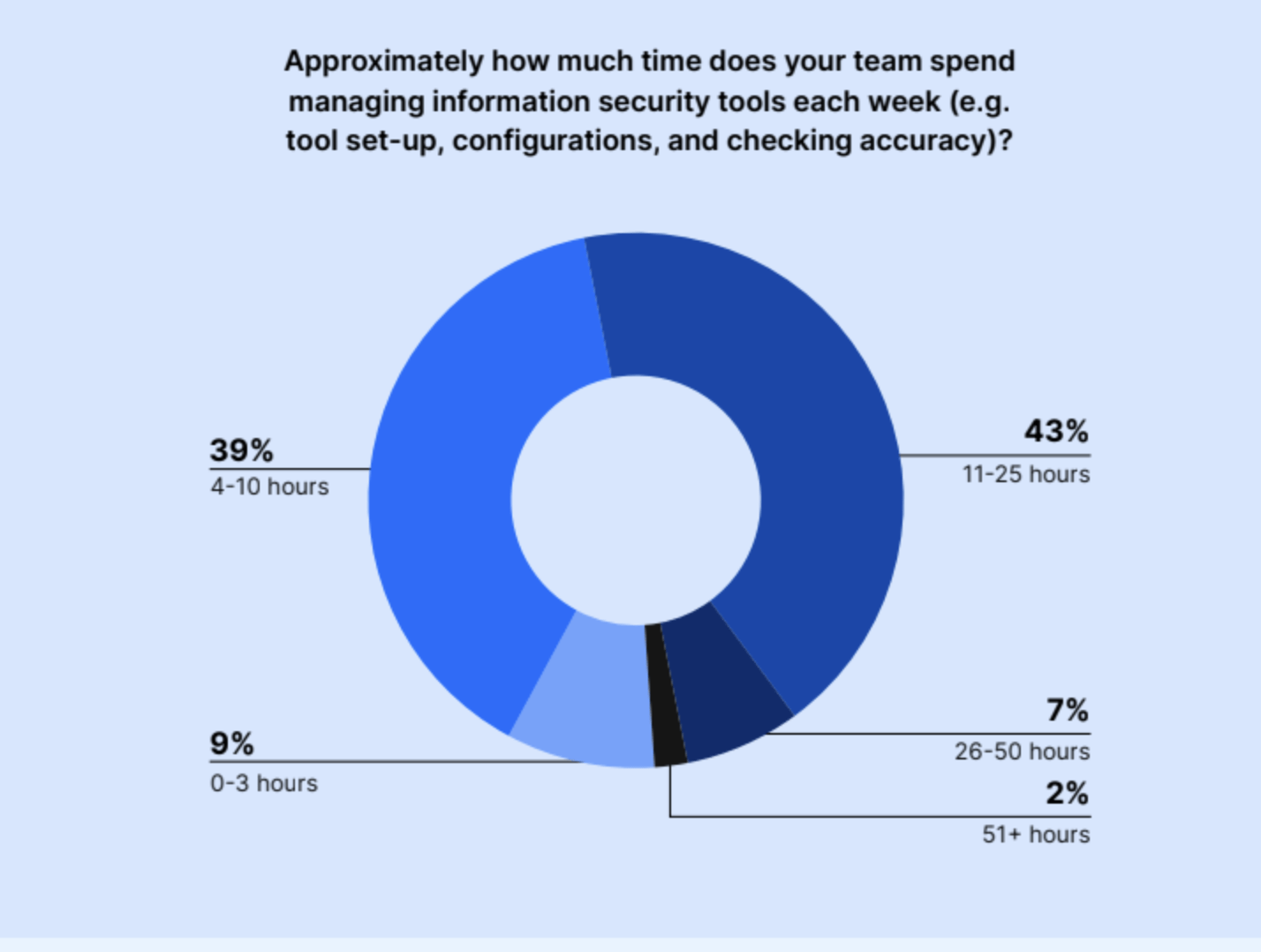
IT and Security teams’ time is consumed by managing risks and manual work; 43% of respondents reported their team dedicates between 11 and 25 hours per week to the management of information security tools. Thirty-nine percent said they spent four to 10 hours, while 7% spent 26-50 hours, and 2% spent over 51 hours.
The rest (9%) said their teams are spending 0 to three hours managing information security tools each week. This means that a whopping 91% of teams are spending four or more hours (upwards of 50+!) per week managing information security tools.
Manual work isn’t just cumbersome and time-consuming, it also affects other security and business needs. Teams can only focus on so many priorities, and manual work pulls time away from what matters most.
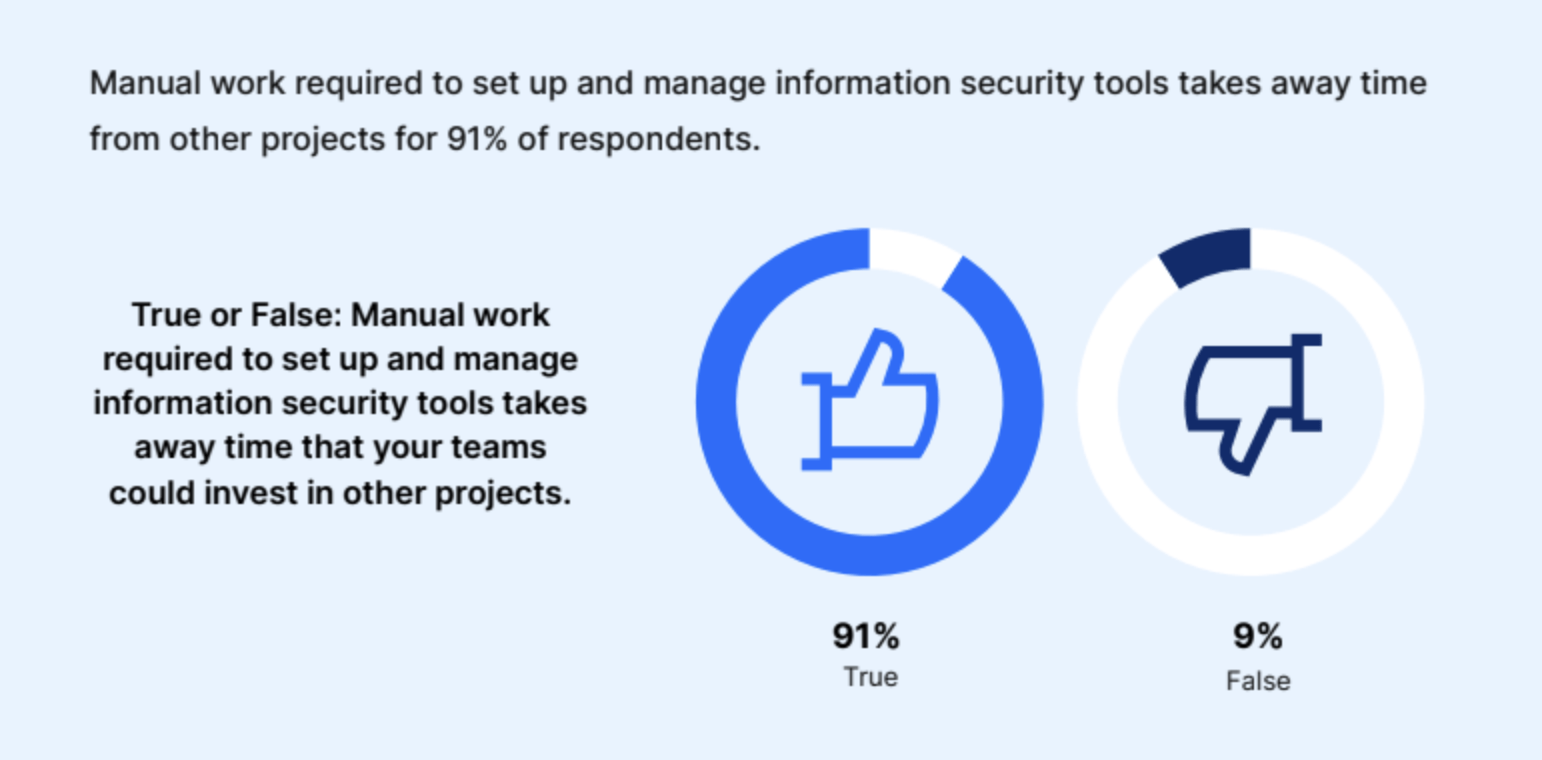
According to a whopping 91% of the respondents, the manual work required to set up and manage information security tools takes away time that teams could invest in other projects.
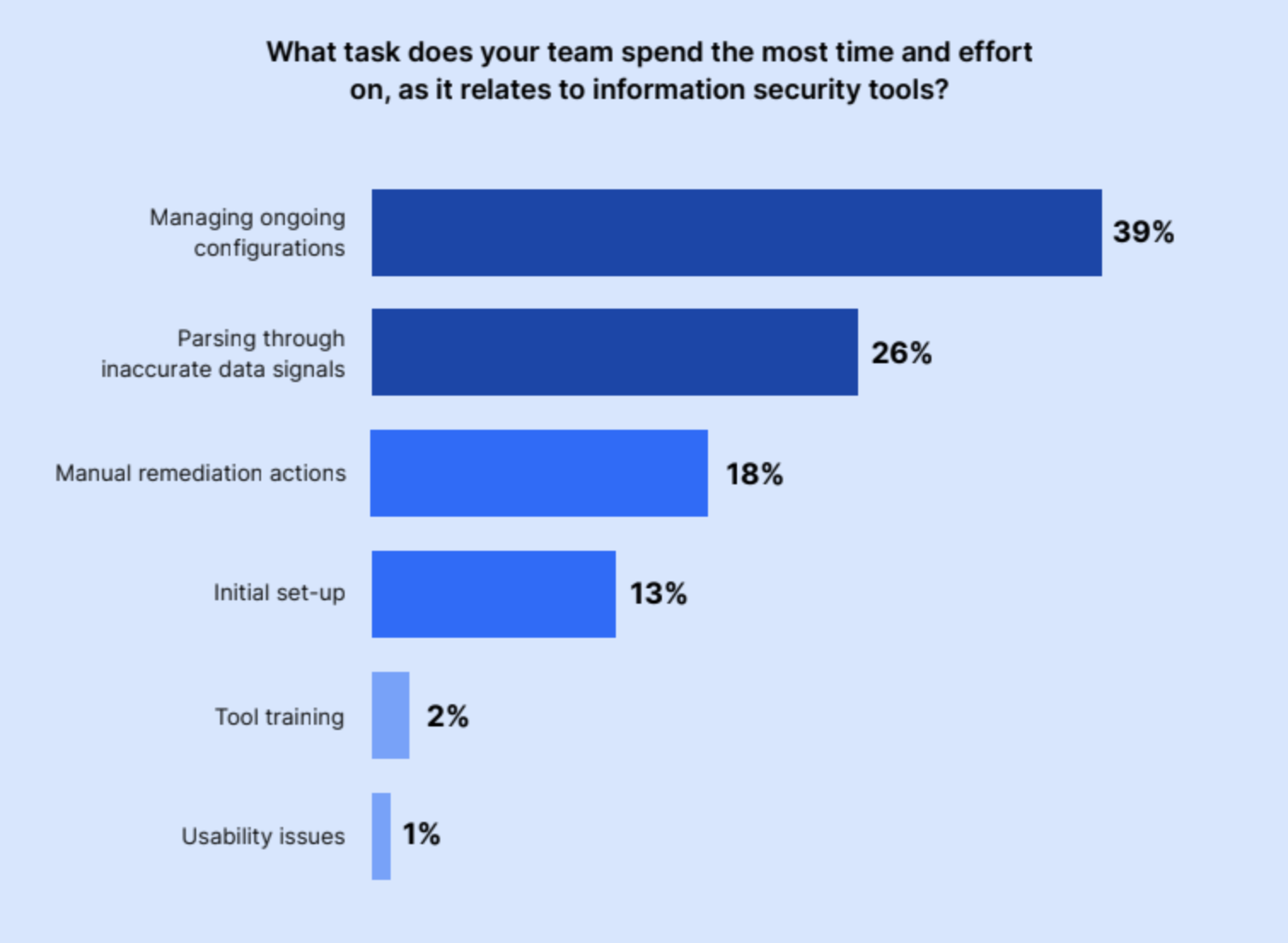
But what sort of manual work are IT and Security teams doing as it relates to information security tools? The majority of respondents spend the most time managing ongoing configurations (39%) and parsing through inaccurate data signals (26%). Others deal with taking manual remediation actions (18%) or the initial set-up of tools (13%).
Meanwhile, only 2% spend an excessive amount of time on training and only 1% on solving usability issues. It turns out that maintaining the information security tools companies use is quite time-consuming and tedious work.
This is a running theme in our conversations at Nira. IT and Security teams spend an increasing amount of time sifting through false positives and unreliable alerts—often from solutions like data loss prevention tools. In a separate Nira-Gartner survey on the state of DLP, 25% of survey participants cited false positives as their biggest challenge with DLP.
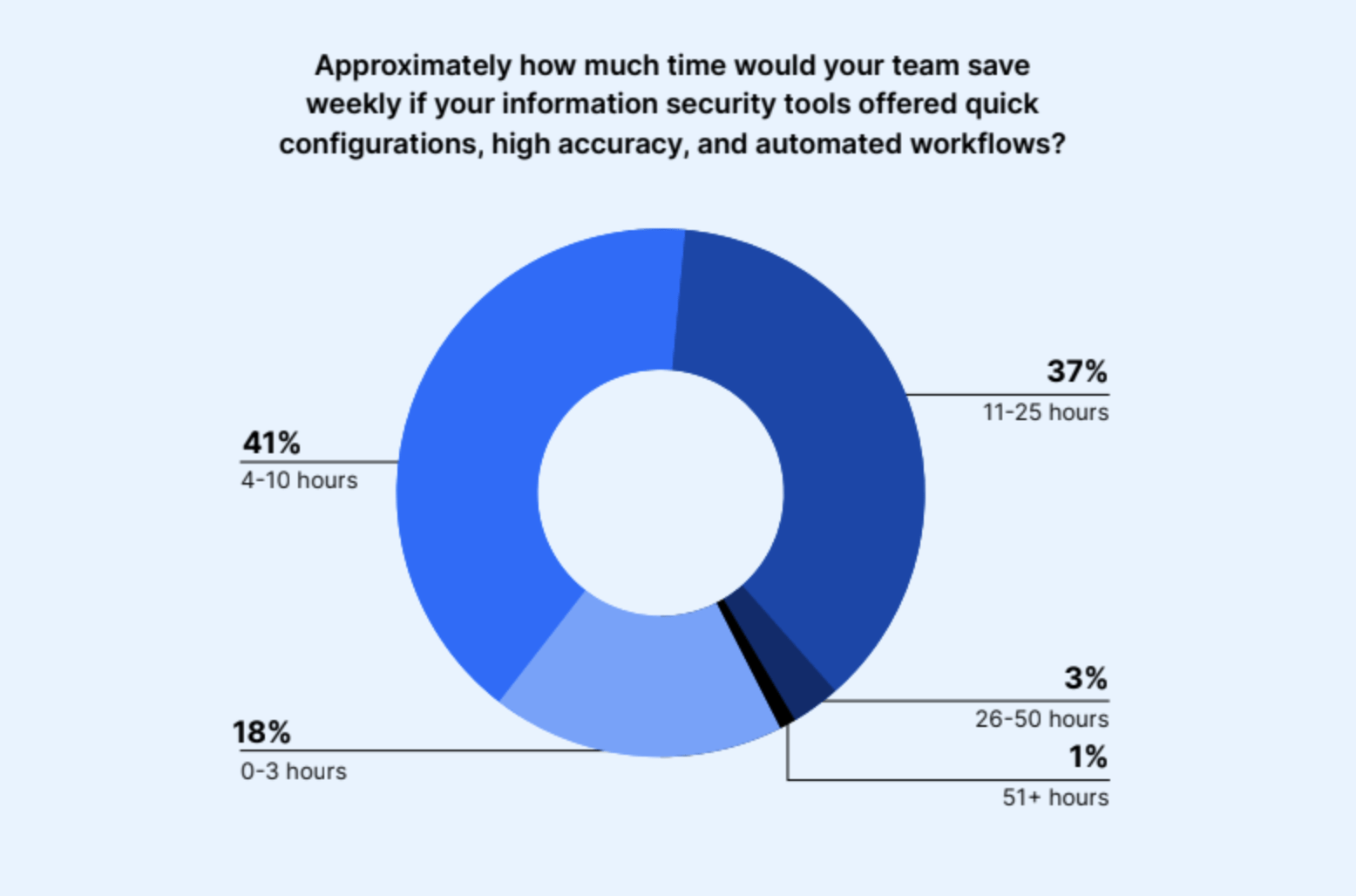
To solve these problems, security professionals are seeking quick configurations, high accuracy, and automated workflows. Forty-one percent of decision-makers believe this would save their teams four to 10 hours per week; while 37% say it would save up to 25 hours per week for their teams.
Leaders want accuracy and automation in their information security solutions
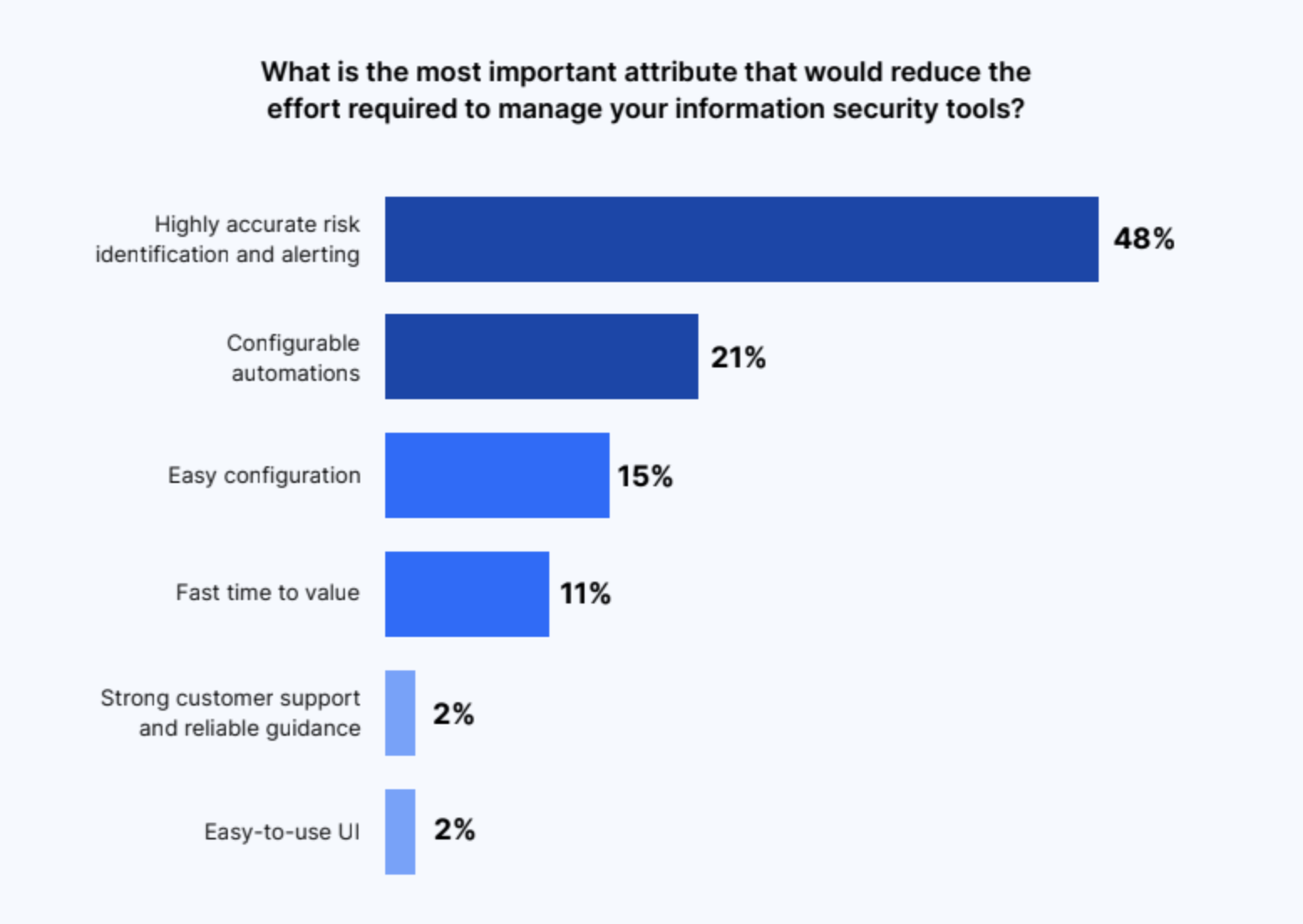
IT and Security leaders agree there are vast benefits from automation and increased accuracy in information security solutions. Highly accurate risk identification and alerting (48%) is the most important attribute that IT and Security leaders say would reduce the effort required to manage information security tools. This follows closely with what we at Nira call “alert fatigue,” where teams are receiving more alerts than they can handle, many of which are false alarms.
Second place goes to configurable automations, at 21%. IT and Security teams want to be able to automate tasks quickly and easily. Other desired attributes are easy configuration at 15%, and fast time to value at 12%.
Accurate risk identification and automated solutions are highly sought after by IT and Security professionals. With an ever-evolving threat landscape, the need for efficient and reliable tools has become paramount. By harnessing the power of automation, leaders can streamline their workflows, enhance accuracy, and ensure more consistent results.
Challenges exist, including the high cost of the required features and tools
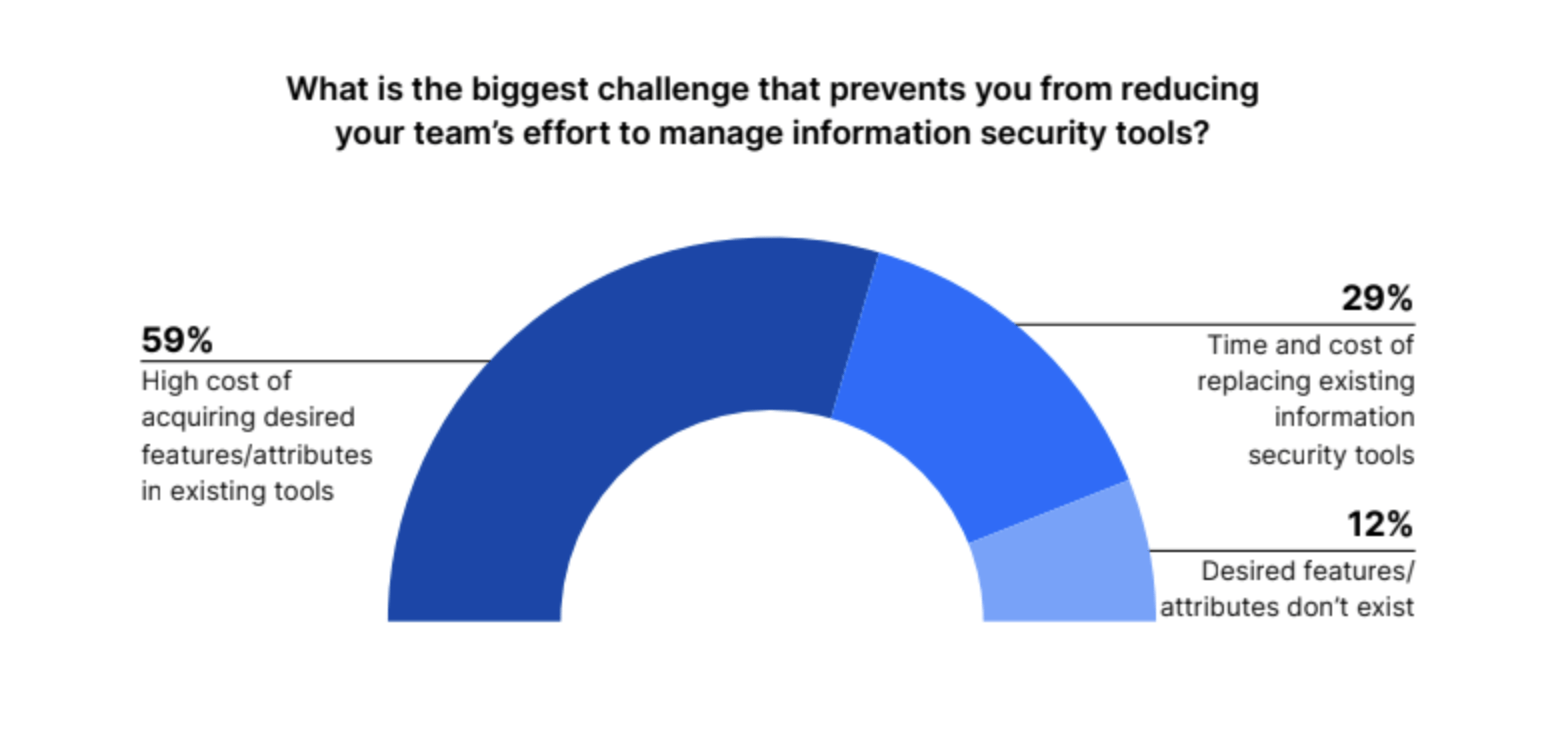
Managing information security tools is still a challenge. Despite a reported increase in security budgets, the high cost of acquiring the right features and tools is the primary obstacle for more than half (59%) of IT leaders who want to reduce their team’s effort to manage information security tools.
Other respondents said the time and cost of replacing existing tools (29%) was their biggest issue, while 12% said the desired features and attributes did not yet exist.
AI and automation, easy integration and usability, and high security and accuracy are ideal
The three most commonly requested features in an ideal solution include artificial intelligence and automation; easy integration and usability; and high security and accuracy.
IT and Security leaders said they want to be able to accurately monitor for risks, without taking up too much of their teams’ time. Time management is a major factor for respondents, and they want to avoid sifting through false positives and signals as much as possible.
Respondents would also like to automate more security tasks and get advanced reporting and analytics capabilities that they can view on a single dashboard. The ability to easily integrate with other security tools and vendors is also highly desirable.
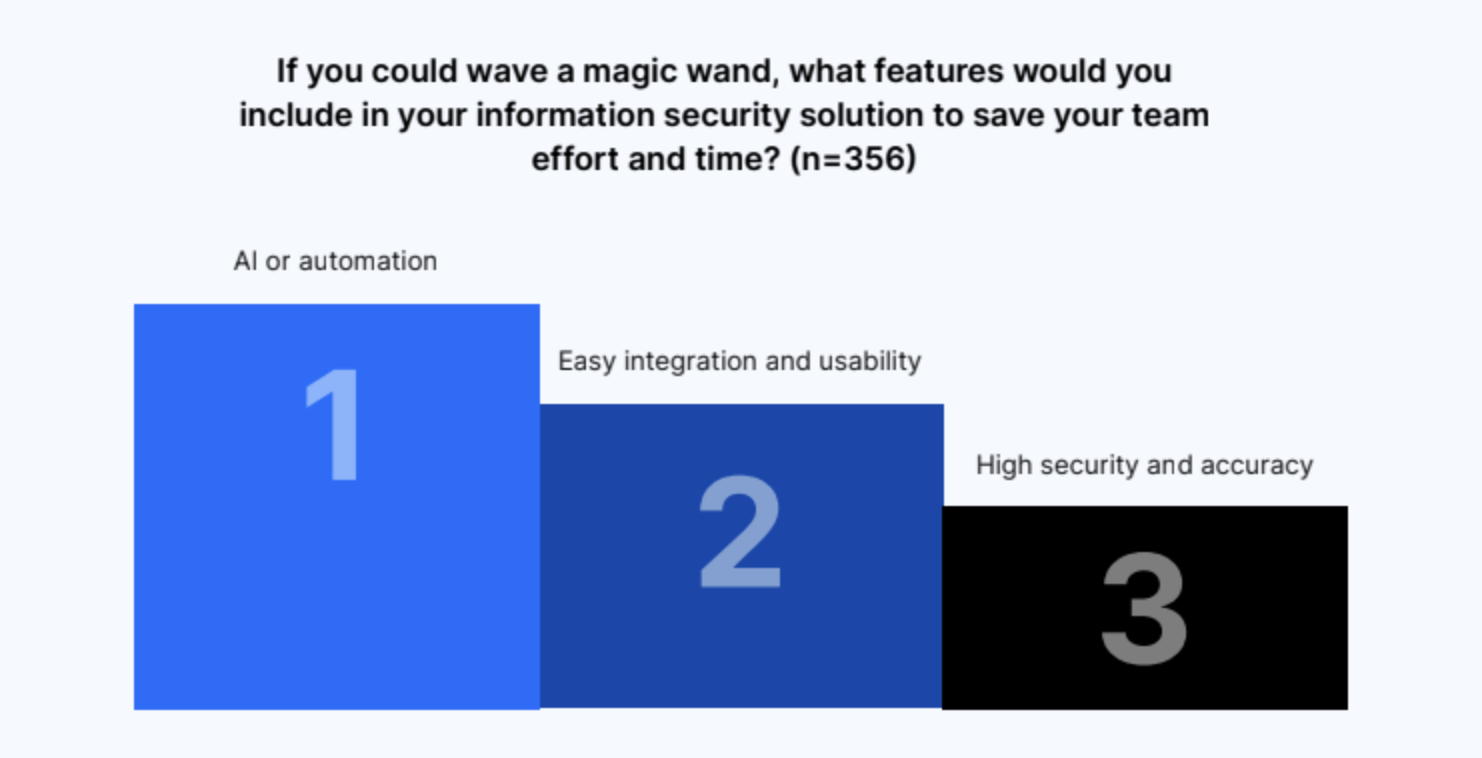
Here’s what several IT and Security leaders said when surveyed about the features they would include in an information security solution to save their team effort and time:
“ACCURATELY monitoring for risks that require little to no time on people. The biggest issue we have is wading through false signals. This is manually intensive and prone to mistakes that could be costly.”
– Director, North America, Professional Services, 5,001-10,000 employees
“I would love it if it included the automation of security tasks, centralized management, integration with other security tools, offered threat intelligence, and provided enhanced reporting and analytics on one unified dashboard.”
-Director, APAC, Professional Services, 10,000+ employees
“I will design an information security tool which will have ML ability to configure itself and send alerts for any unknown attacks and filter them in a smart way. It will generate reports like what SOC and SIEM teams do to take predictive measures & decisions for further configuration and settings.”
– C Suite, APAC, Educational Services, 51-200 employees
“Tools that we use must have integration capabilities with other vendor solutions and use of them must be relatively easy and understandable. Time management is the key factor for us.”
– Manager, EMEA, Professional Services, 501 – 1,000.
The landscape of information security is constantly evolving, and organizations face increasing risks in protecting their valuable data. This is further exacerbated by the growing IT workloads and budgets required to keep up with expanding threats.
Managing these risks and the manual work associated with them can consume a significant amount of IT time, making it necessary to find solutions that streamline and automate security processes.
IT and Security leaders are seeking information security solutions that offer automation and accuracy to effectively combat the rising risks. They understand the importance of leveraging technology to enhance their security posture and minimize human error.
Despite the challenges, organizations recognize the need for advanced tools that can seamlessly integrate with existing systems and provide high levels of security and accuracy.
By addressing these priorities, organizations can better protect their data and mitigate evolving risks in today’s information security landscape.
About Nira
Nira is a Data Access Governance system that provides complete visibility and management over who has access to company documents in Google Workspace, Microsoft OneDrive, and more. It provides a single, comprehensive view of who has access to critical cloud-based company data.
Companies can comply with their data retention policies using Nira, which allows admins to delete or archive files that are outside of retention periods. Documents can be targeted with precision, with filters such as keywords, organizational units, or when a document was last modified. Employees can also set archive exceptions for items that should not be archived.
In-depth security investigations and remediations are also powered by Nira. With real-time monitoring, advanced filtering, and contextual reporting, it becomes possible to quickly identify and remediate suspicious activities, unauthorized access, and potential data breaches.
Nira allows IT and Security administrators to easily find and identify risks, quickly control access and fix issues in bulk, and efficiently automate the process through policy enforcement and remediation delegation. It also empowers employees to manage and control who has access to their information through its Employee Security Portal.
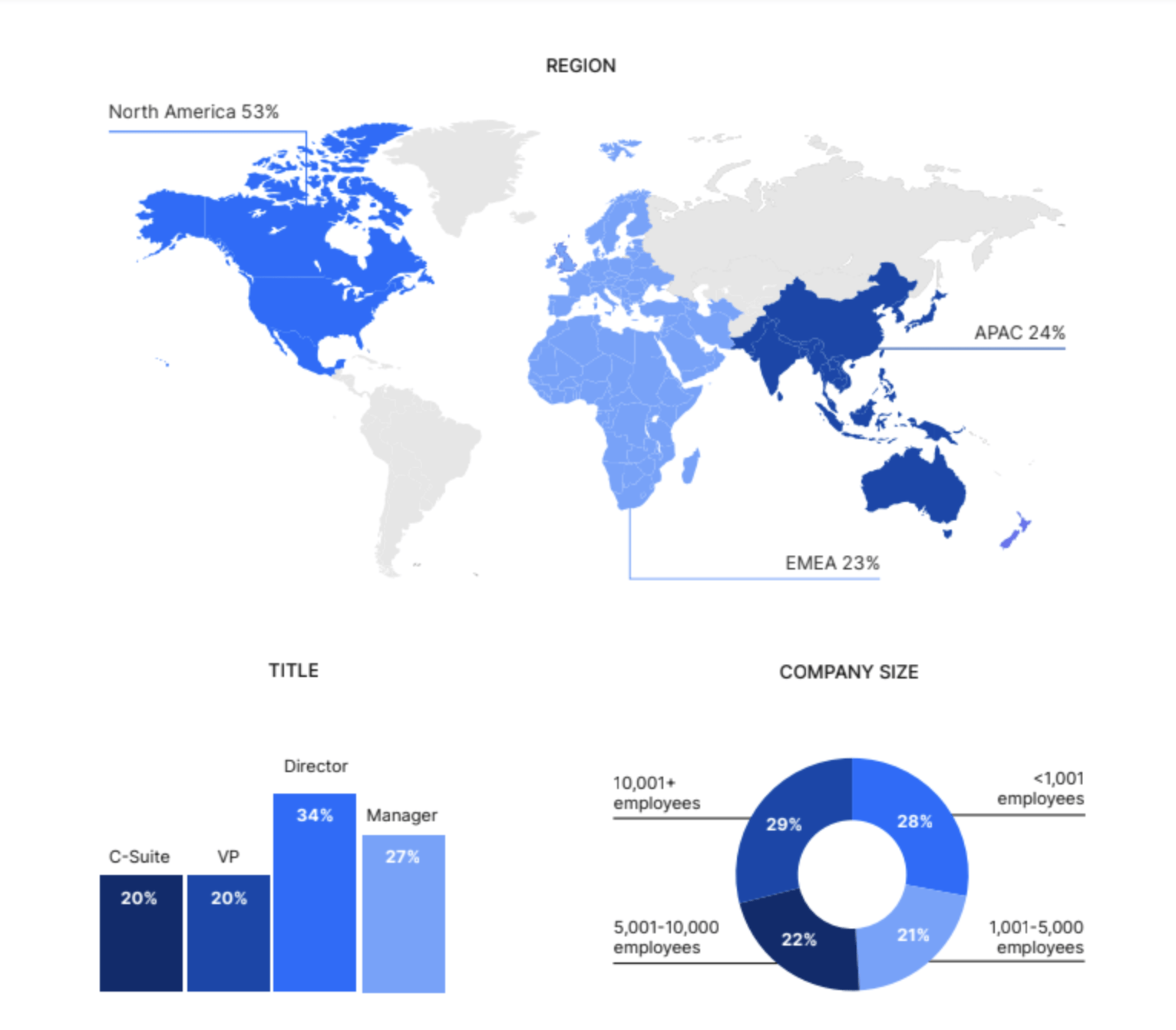
Respondent Breakdown