The State of Zero Trust Strategy Adoption
Zero Trust is the idea of blanket skepticism regarding network access—even from internal users—requiring verification at all entry points and never assuming access privileges. But while Zero Trust is gaining significant momentum as a strategic ideal, rearchitecting the network to achieve Zero Trust is not so straightforward.
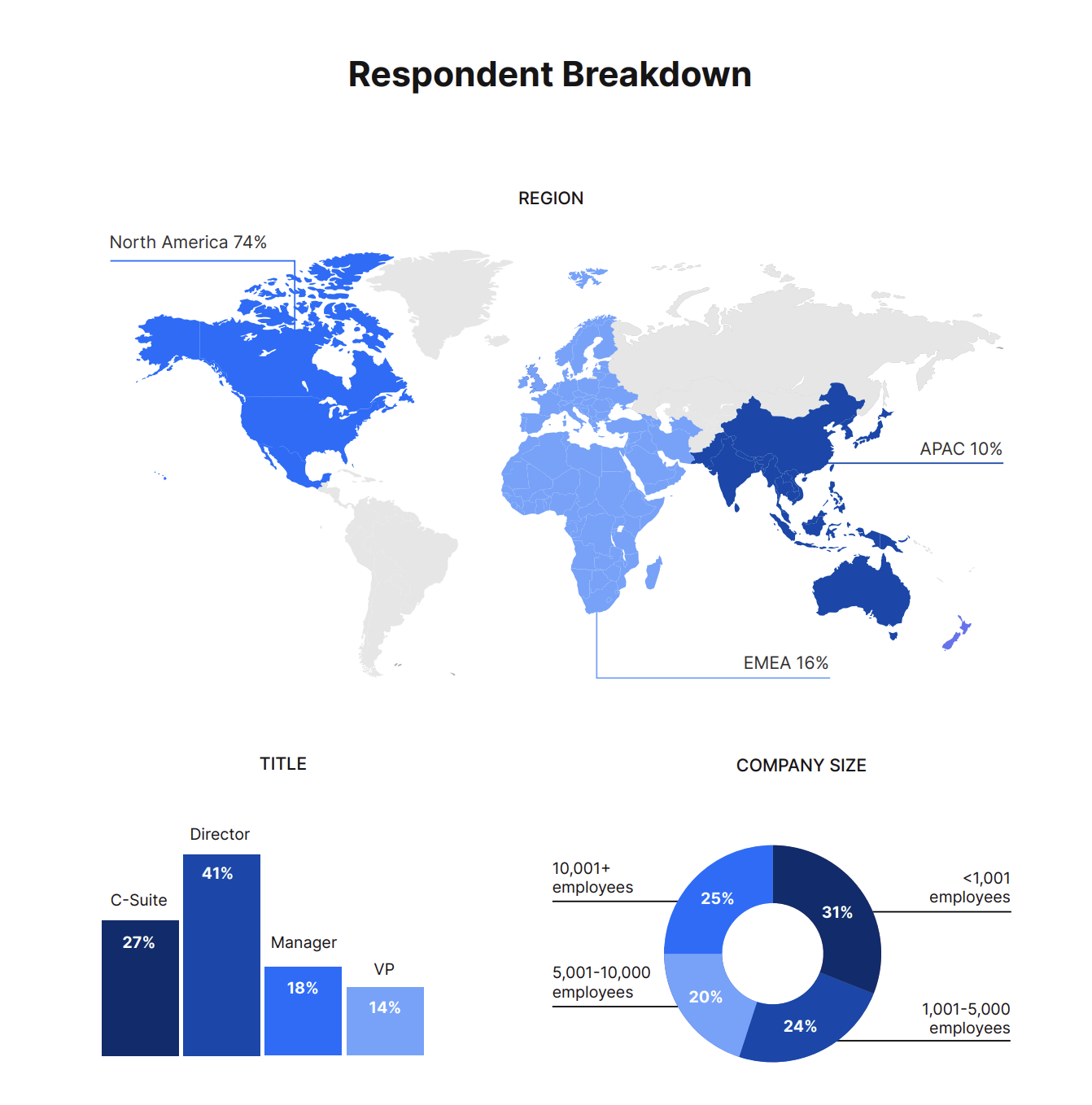
As more companies adapt to distributed work and headline-making cybersecurity incidents rise across industries, we wanted to know if decision-makers are adopting a Zero Trust security strategy.
Nira utilized Gartner Peer Insights and surveyed over 200 digital decision-makers to better understand:
- Levels of Zero Trust adoption and timelines for implementation
- Perceived benefits of Zero Trust, as well as barriers to adoption
- Essential components for Zero Trust and whether organizations have them in place.
Here’s what we learned:
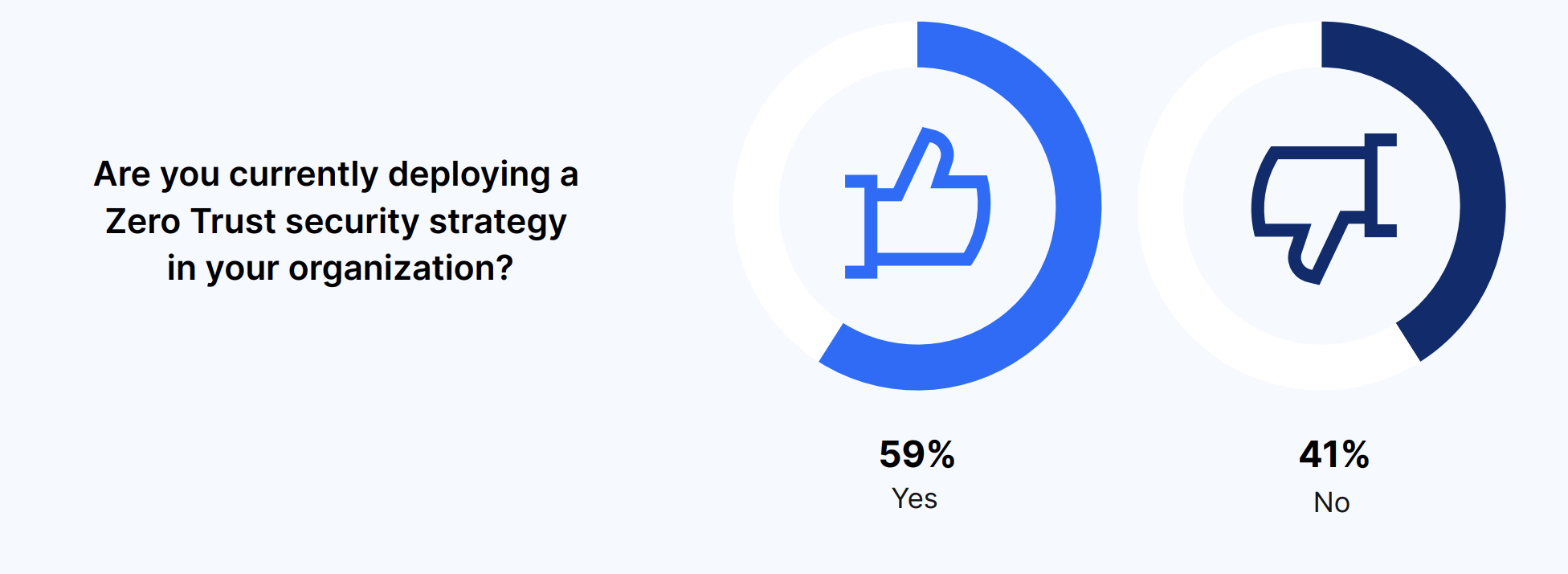
Just over half of IT leaders already have a Zero Trust security strategy—and others will eventually follow. Most decision-makers – 59% – are currently deploying a Zero Trust security strategy, but 41% have yet to.
“Zero Trust has transformed (for the better) many processes and our ability to protect our internal assets.”
—C-suite, small-medium business
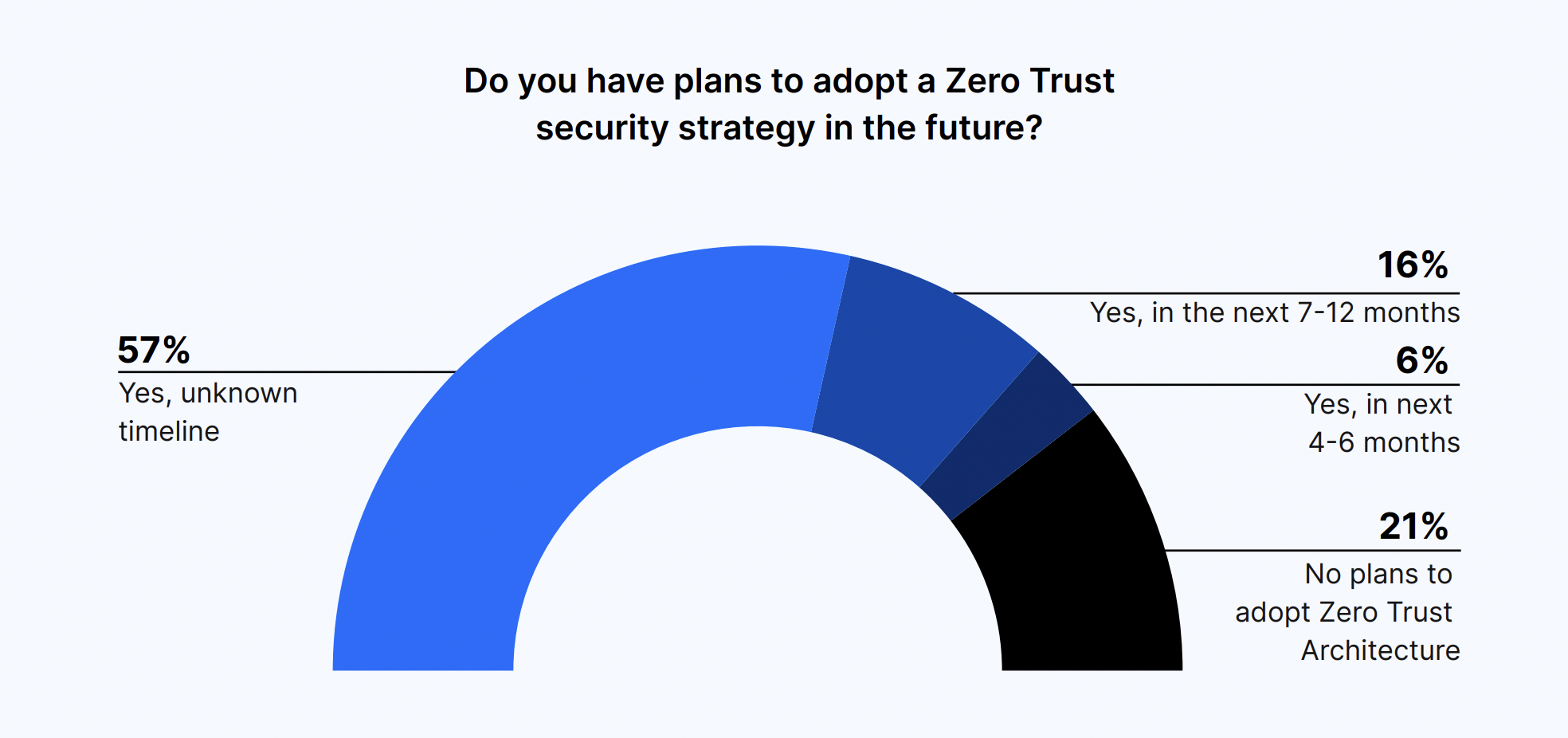
Of those who aren’t deploying a Zero Trust security strategy, 79% have plans for adoption in the future. Fifty-seven percent were unsure when that timeline would take place while 16% said within the next seven to 12 months, and 6% said four to six months. Meanwhile, 21% had zero plans to adopt Zero Trust architecture.
“I’m very interested in implementing [Zero Trust] at my organization, but we have such a complicated network architecture that I worry it might be impossible.”
—C-suite, public sector
Zero Trust adoption is driven by risk management and secure remote access—and protecting customer data is the top business case.
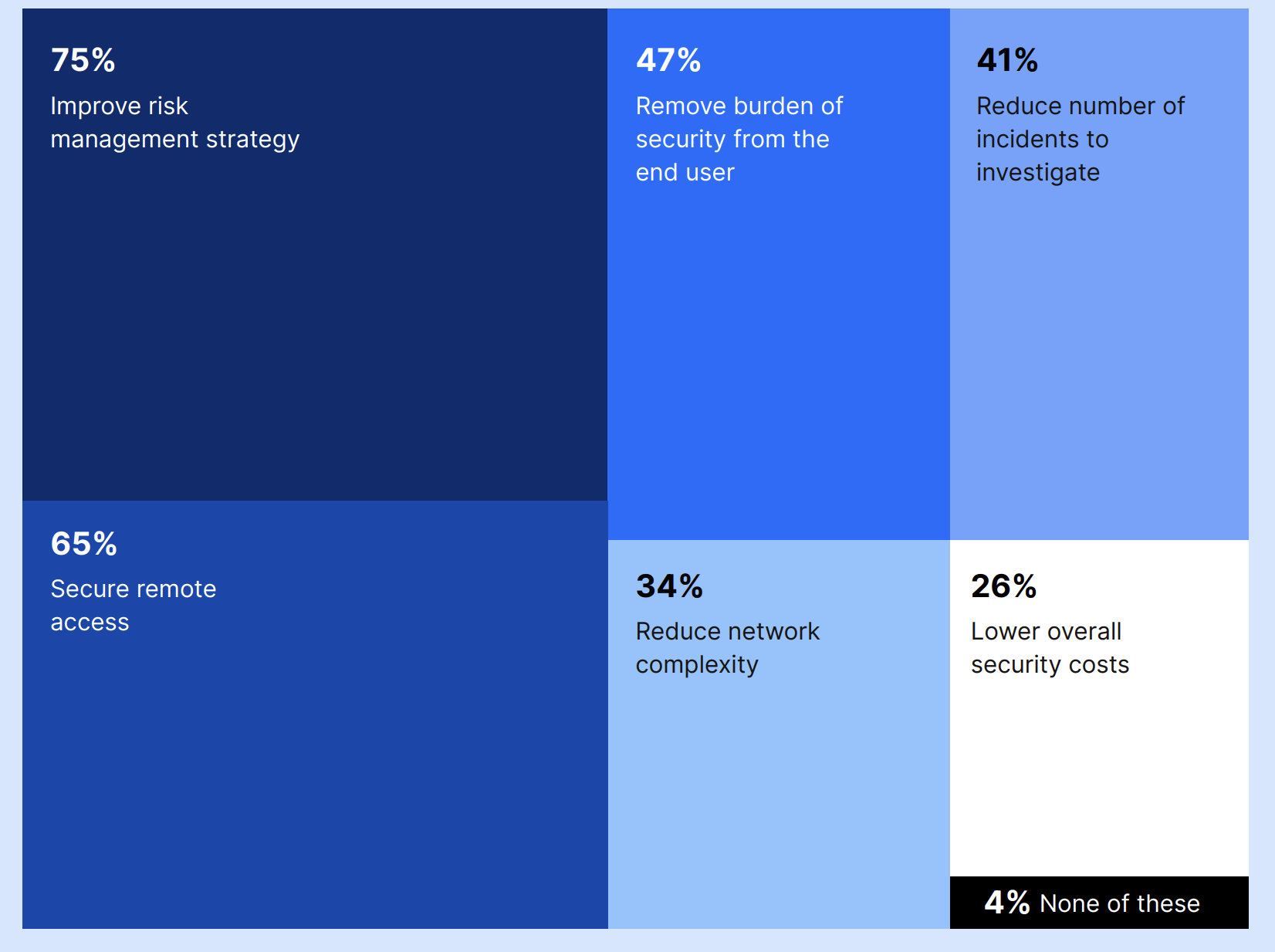
Improving risk management strategy (75%) and securing remote access (65%) were the top reasons to adopt a Zero Trust security strategy. Meanwhile, other leaders (47%) wanted to remove security burdens from end-users, and 41% aimed to reduce the number of incidents to investigate.
What are the main reasons to adopt a Zero Trust security strategy?
“Zero Trust is a business imperative driven by the explosive number of threat vectors and incidents. It is only a matter of time before every company is impacted. Zero Trust gives companies a fighting chance.”
—C-suite, startup
As for business cases, protecting customer data (63%) and a uniform security approach (51%) were the main drivers for Zero Trust adoption.
Other reasons included reducing accidental internal breaches (47%) and simplifying the security stack (47%). Forty-six percent of security leaders were concerned with maintaining compliance.
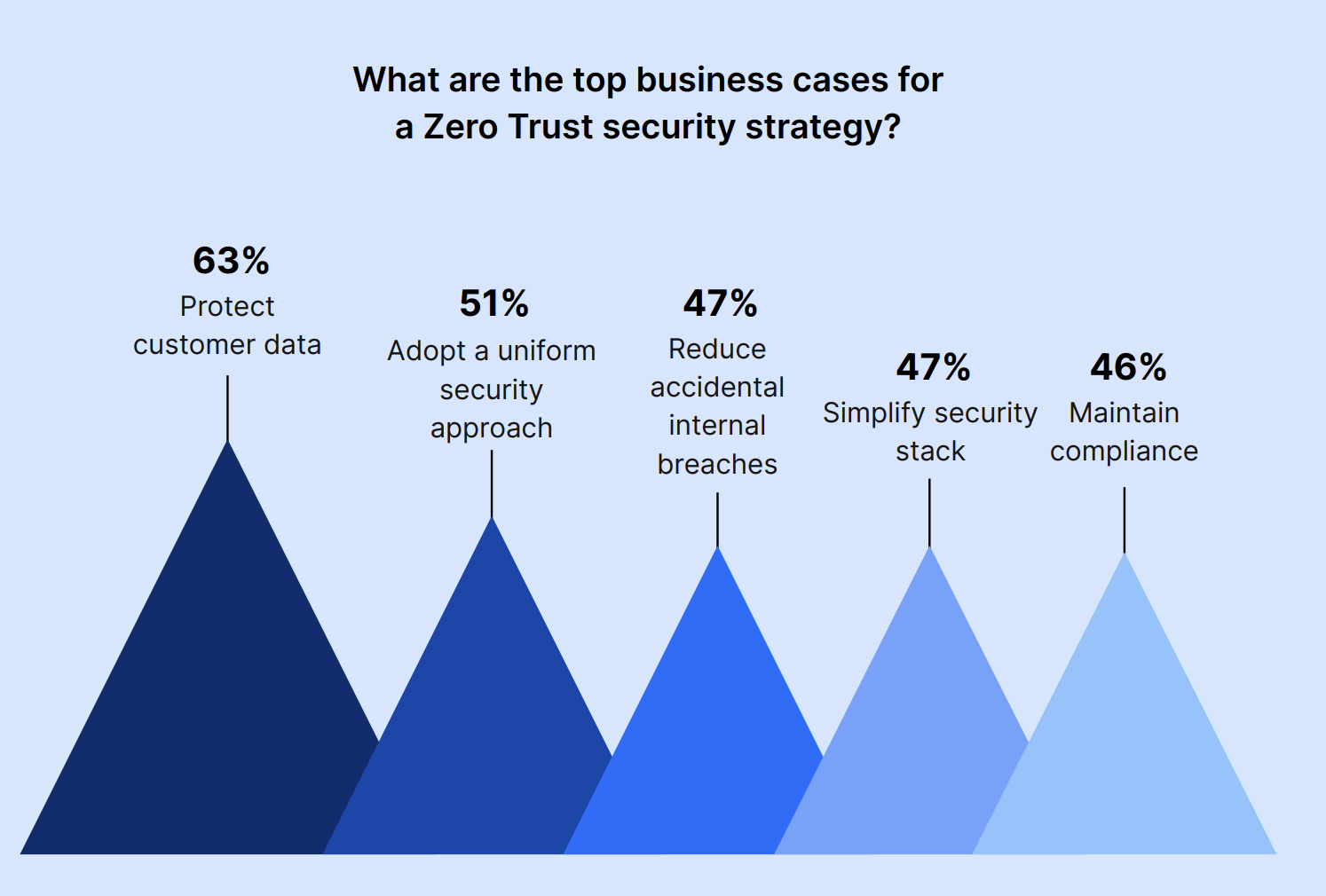
Other business cases included:
- Reducing malicious internal breaches (41%)
- Centralizing security oversight of public clouds (30%)
- Fostering business continuity (26%)
- Reducing costs (26%)
- Minimizing the need for highly skilled security professionals (21%)
“Zero Trust is a perfect fit in companies where data sets are highly protected and usage patterns are consistent.”
—C-suite, startup VP, large enterprise
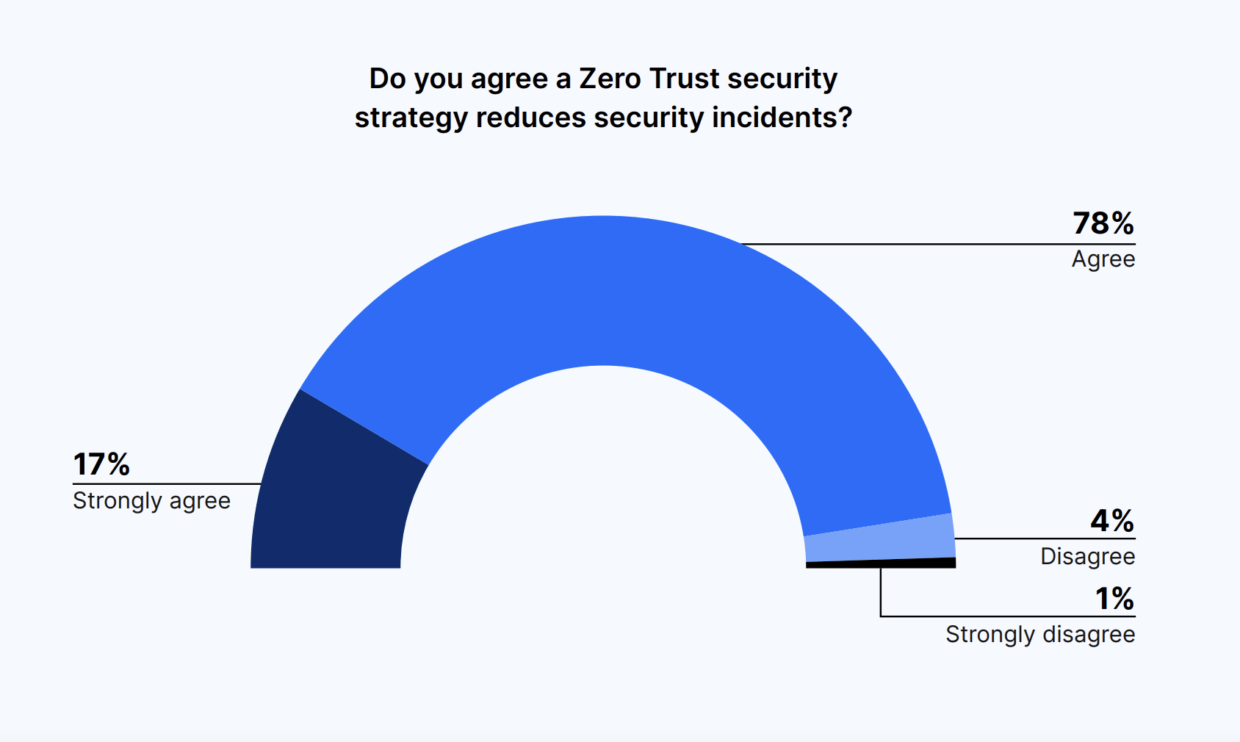
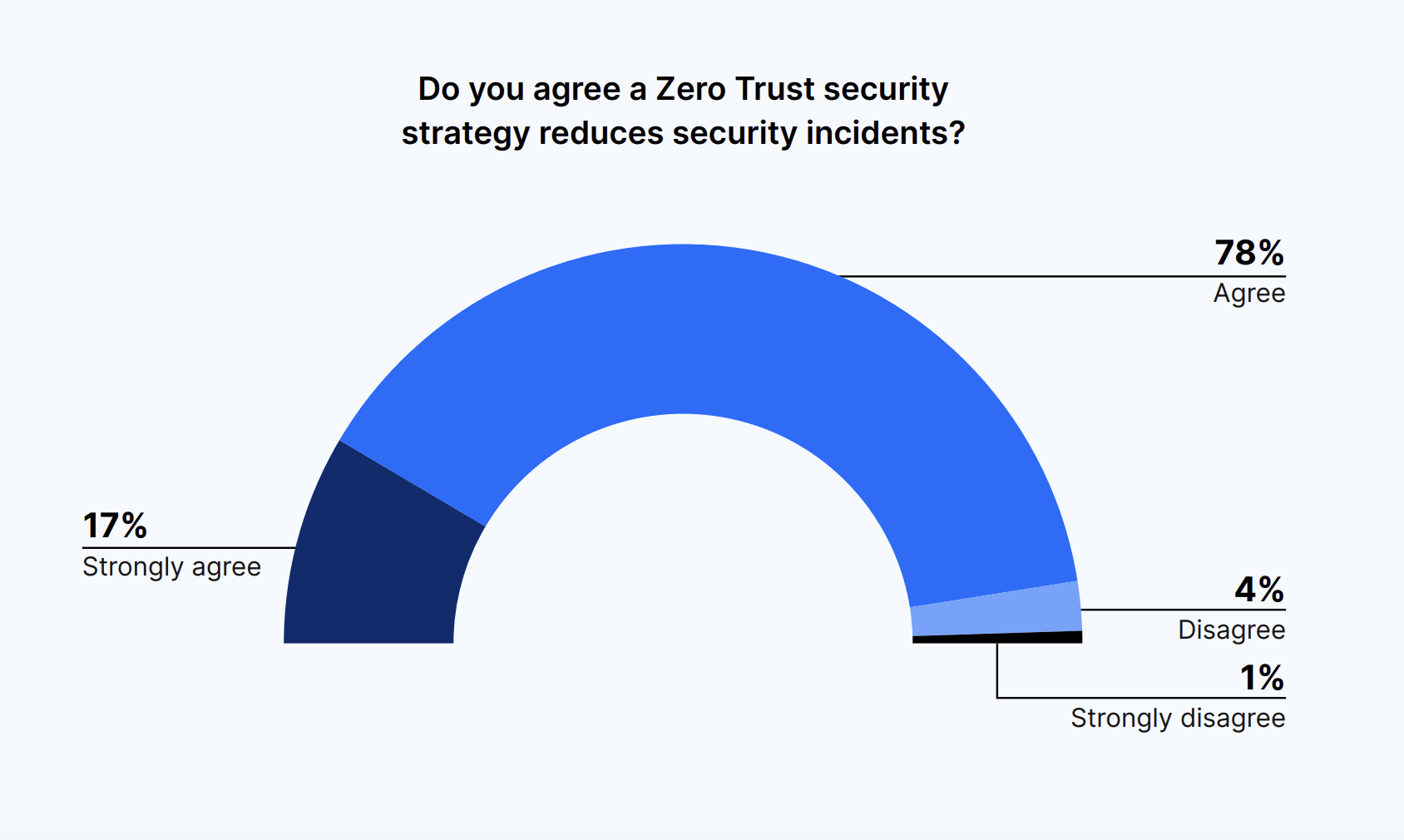
Most leaders agreed that a Zero Trust security strategy reduces security incidents, particularly data leakage and internal threats, and also simplifies security architecture. A strong 95% of decision-makers agreed that Zero Trust reduces security incidents.
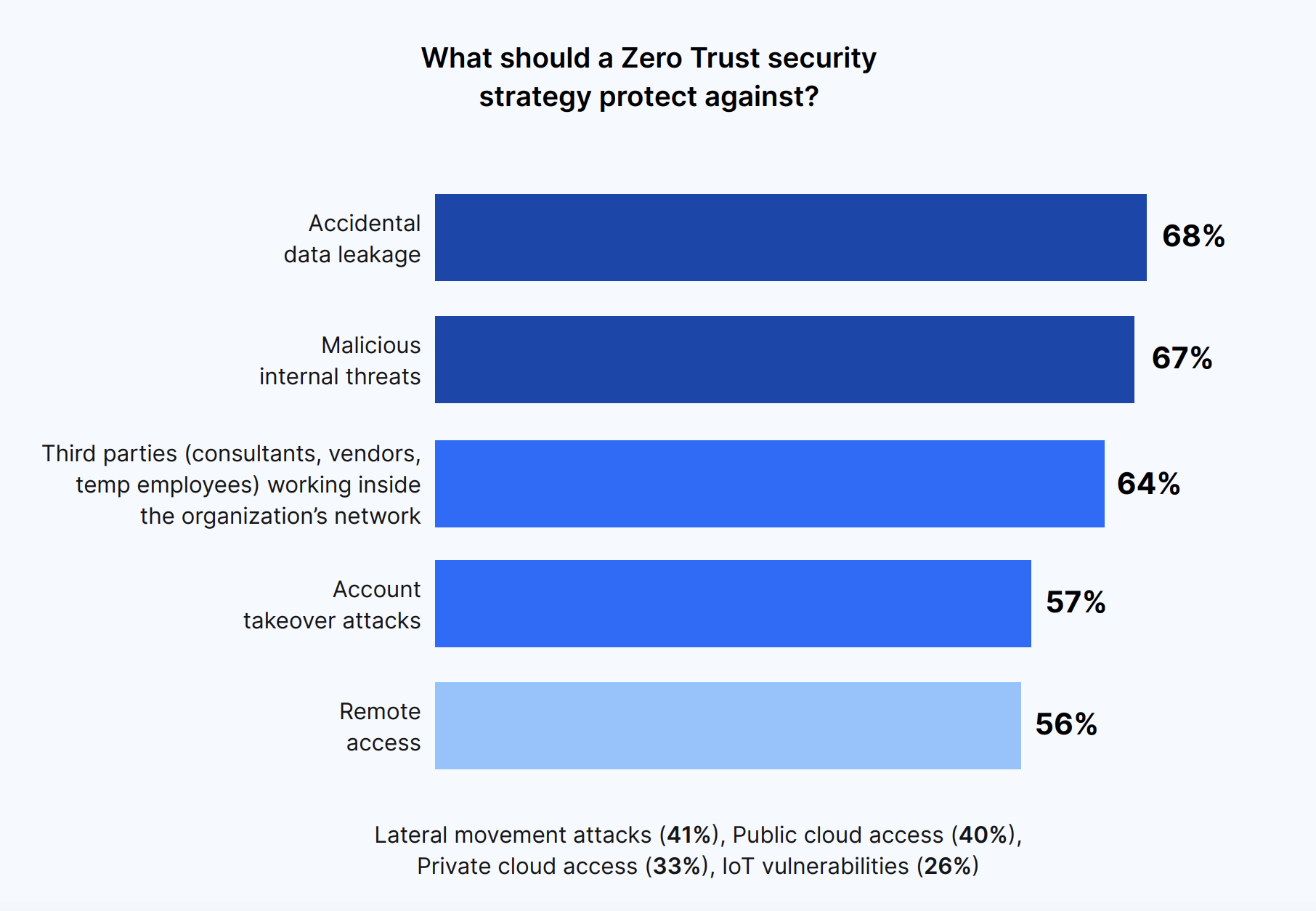
A Zero Trust security strategy should mostly protect against accidental data leakage (68%), followed by malicious internal threats (68%), and third parties working within the network (64%).
Eighty-seven percent of decision-makers believed that a Zero Trust security strategy will also simplify their organization’s security architecture. However, based on written feedback, some worried that they did not have adequate materials to convince non-technical executives of its importance.
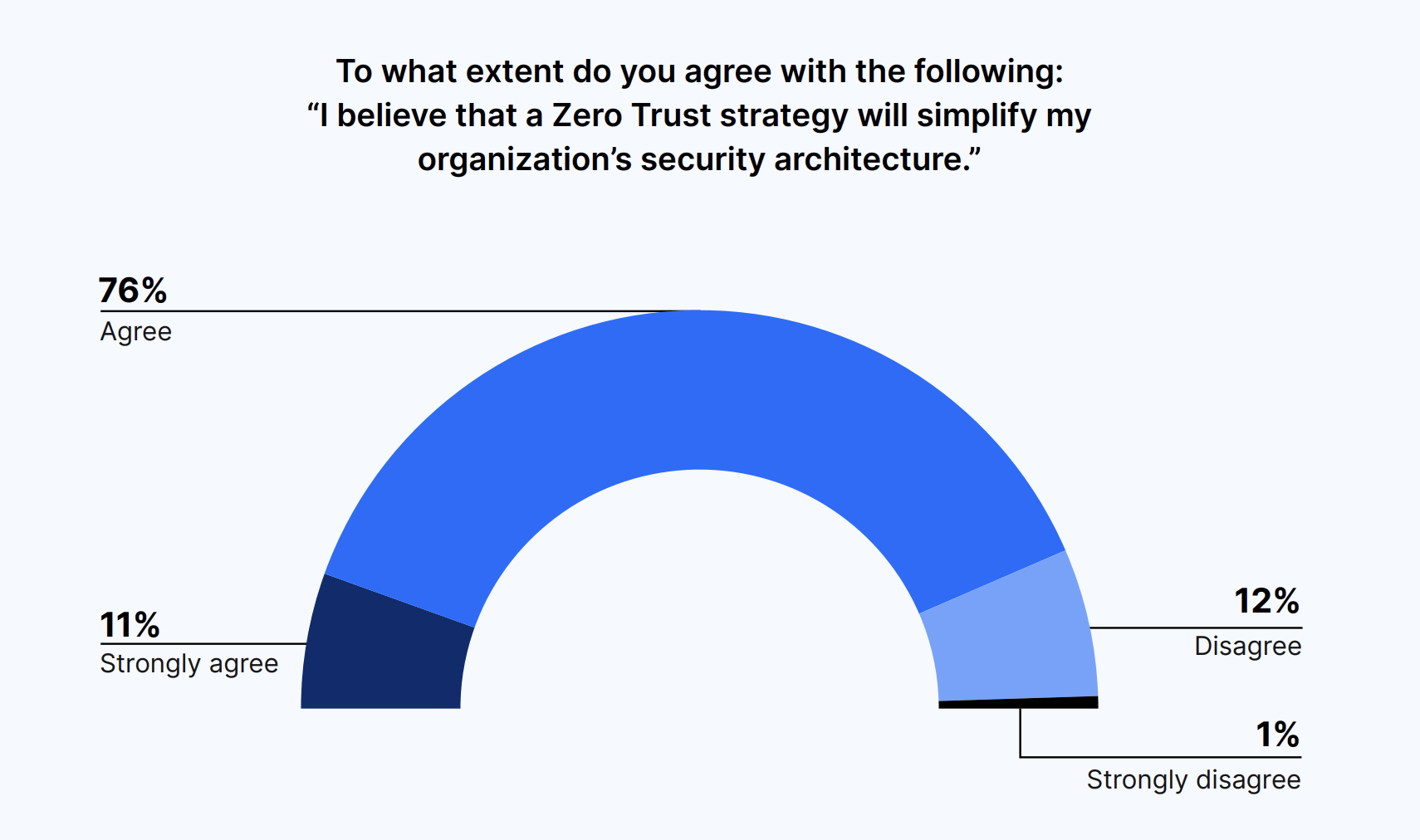
“I’m sold [on Zero Trust], the non-technical [leadership] isn’t. Key materials to help win the battle are few and far between.”
—Director, small-medium business
Most information security professionals already have the essential components to a Zero Trust strategy within their security stack—but costs and skills gaps are challenges to implementation.
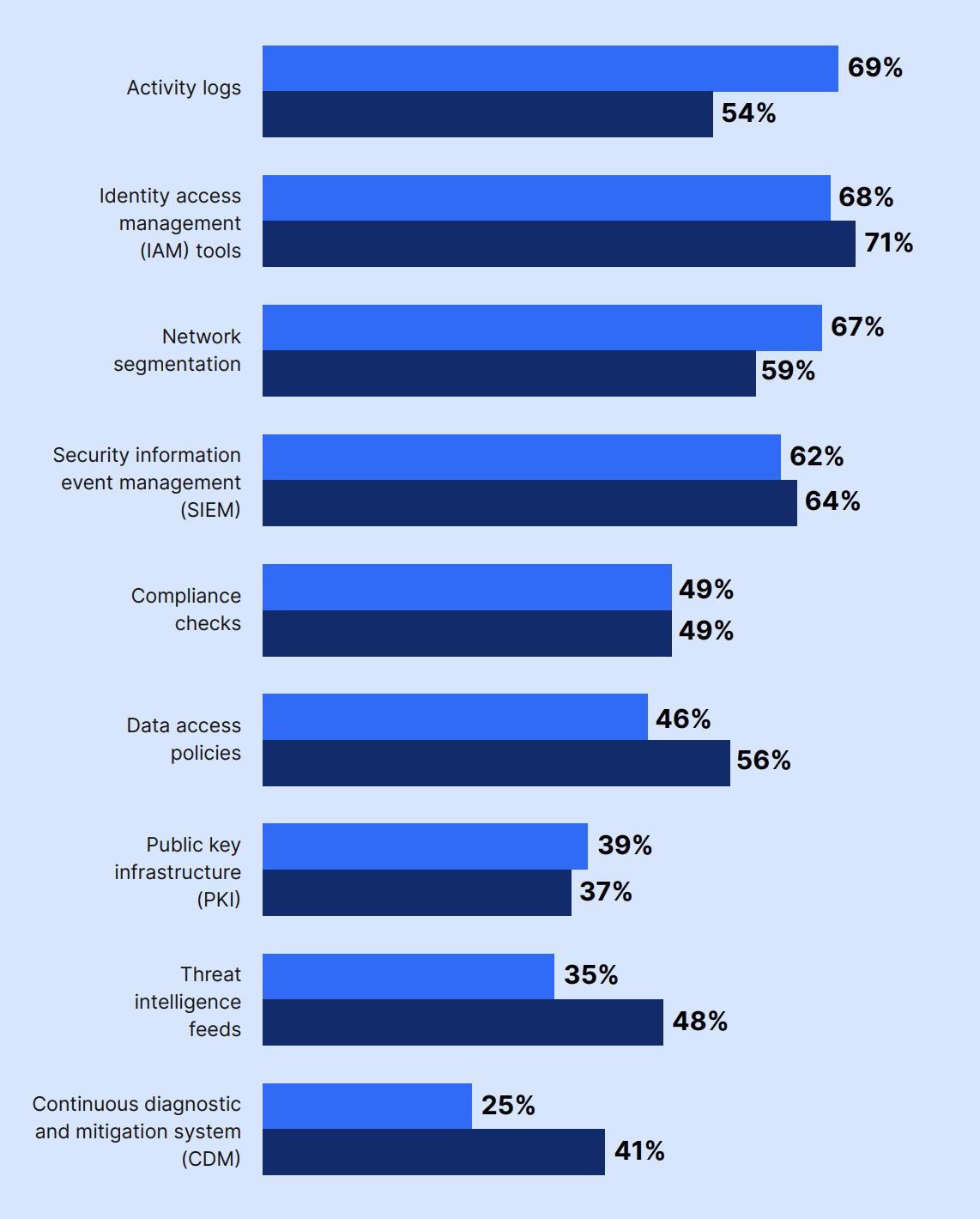
Security stack components included: activity logs (69%), identity and access management (IAM) tools (68%), network segmentation (67%), and security information and event management (SIEM) (62%).
From the same list, decision-makers highlighted IAM tools (71%), SIEM (64%), and network segmentation (59%) as the top essential components of a Zero Trust security strategy, meaning that many already have these components in place.

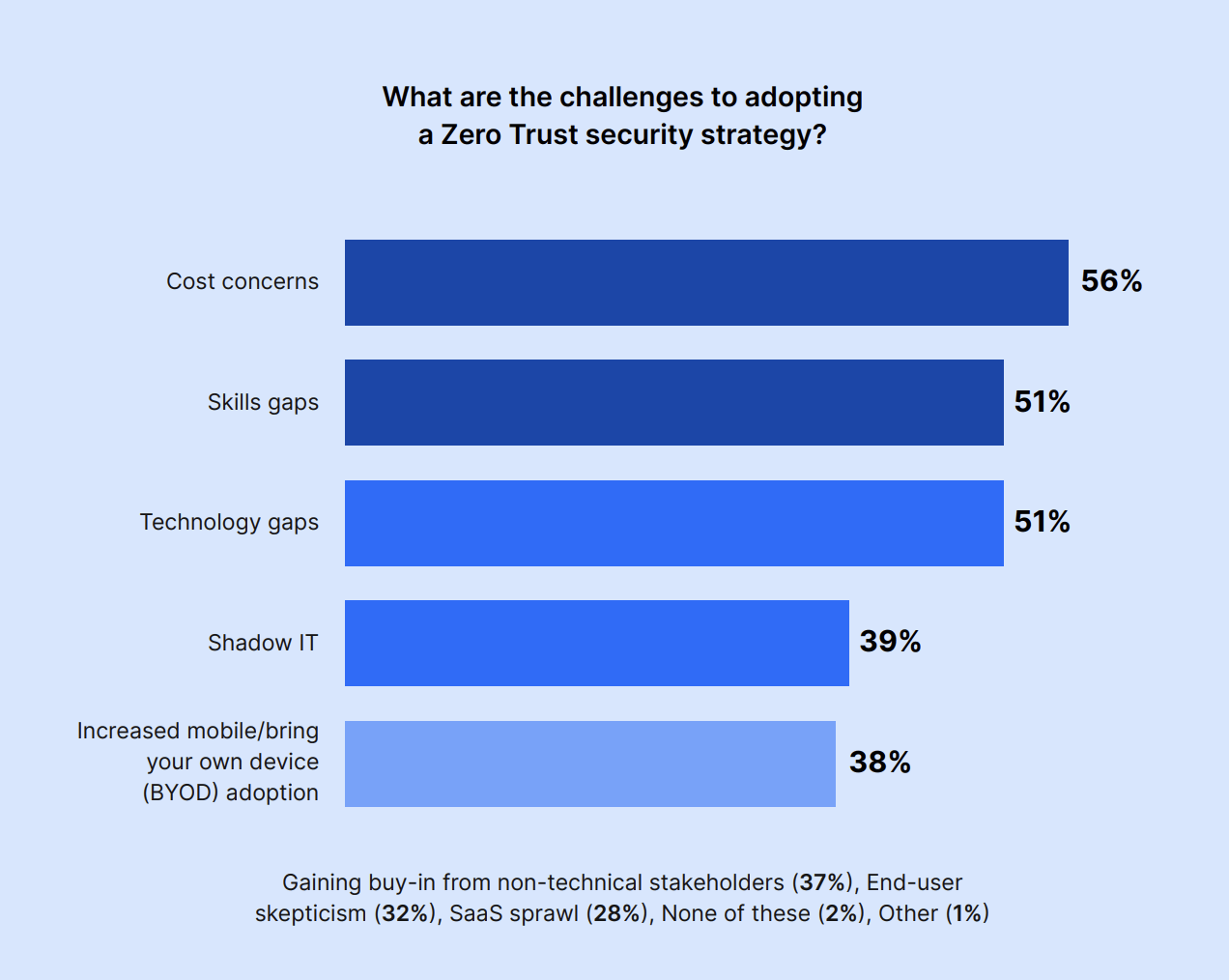
When it comes to adoption challenges, however, cost concerns ranked highest (56%), followed by skills gaps (51%) and technology gaps (51%.) Shadow IT (39%) and increased BYOD (Bring Your Own Device) adoption (38%) were also concerns.
“Changing the culture of our organization has been challenging. So many users have had access privileges that they think they need but don’t.”
—Director, small-medium business
Overall, Zero Trust architecture is a growing consideration for companies of all sizes and across industries. Over half of the companies surveyed already had some sort of strategy in place, and many more had plans to implement one in the future.
Despite the challenges, as well as convincing executive leadership of the business need, Zero Trust seems poised to stay in the conversation around security architecture as more organizations embrace adoption.
About Nira
Nira is a Cloud Document Security system that provides complete visibility and management over who has access to your company documents in Google Workspace and more. Nira provides a single, comprehensive view of who has access to valuable cloud-based company data. It allows you to easily find and identify risks, quickly control access and fix issues, and efficiently automate the process through policy enforcement and remediation delegation. Nira also enables employees to manage and control who has access to their information, without needing technical expertise.