The State of Offboarding Security For Remote Work
Employees are often granted access to sensitive company data, documents, and software. When an employee leaves an organization, offboarding processes serve as a way to protect the organization from intentional or accidental data breaches which can cost companies millions in revenue and reputational damages.
However, the coronavirus pandemic resulted in a rapid switch to a distributed, remote workforce which caused new challenges and security risks.
What’s the state of offboarding processes during COVID-19?
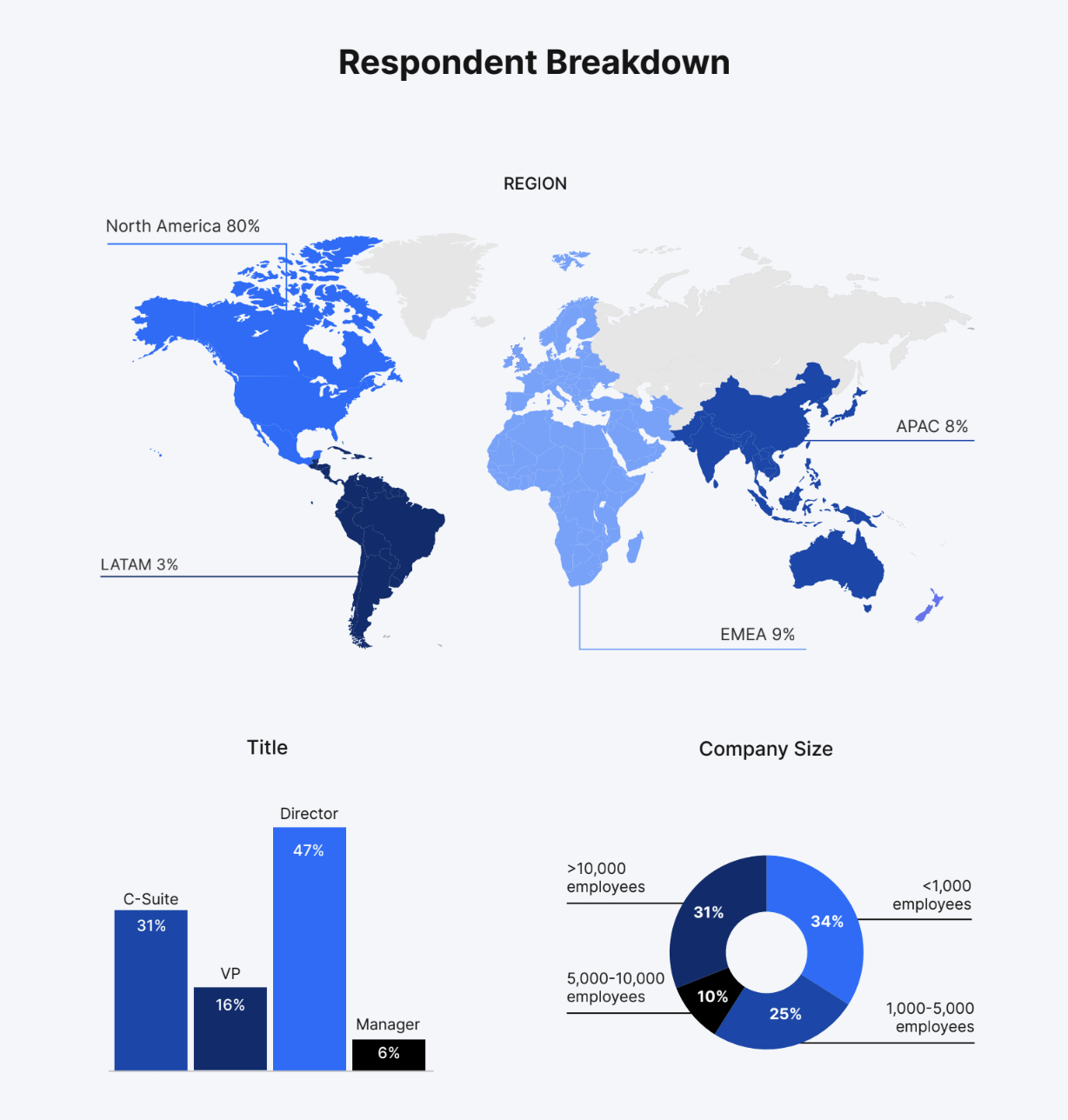
Nira utilized Gartner Peer Insights and asked over 100 IT executives across a range of industries about:
- How offboarding was affected by the switch to a remote workforce
- Their biggest offboarding security threats and if they have sufficient protocols to manage them
- What their priorities are for offboarding going forward
Offboarding processes have changed because of COVID-19 and become more challenging
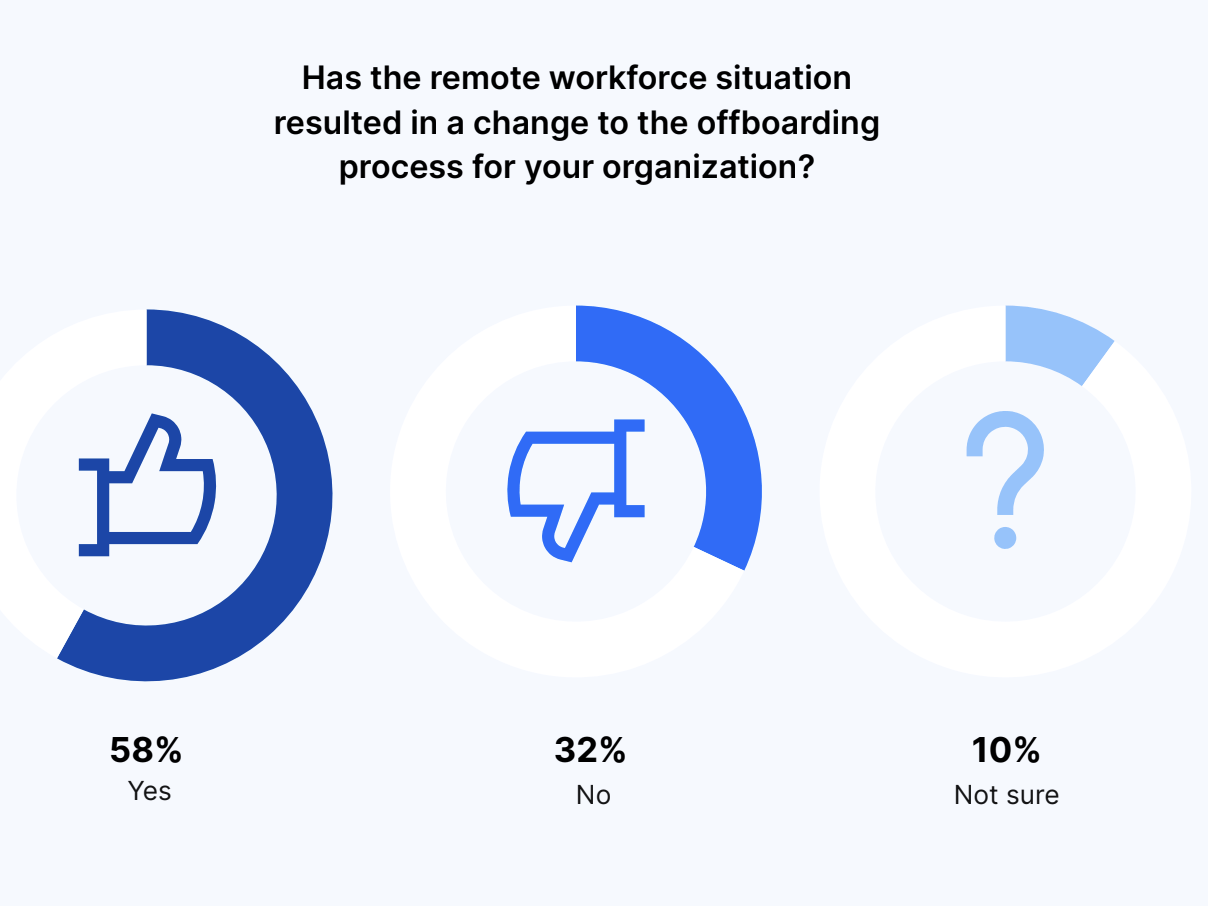
Fifty-eight percent of executives reported that offboarding processes have changed as a result of an enforced remote workforce while 10% were unsure.
Has the remote workforce situation resulted in a change to the offboarding process for your organization?
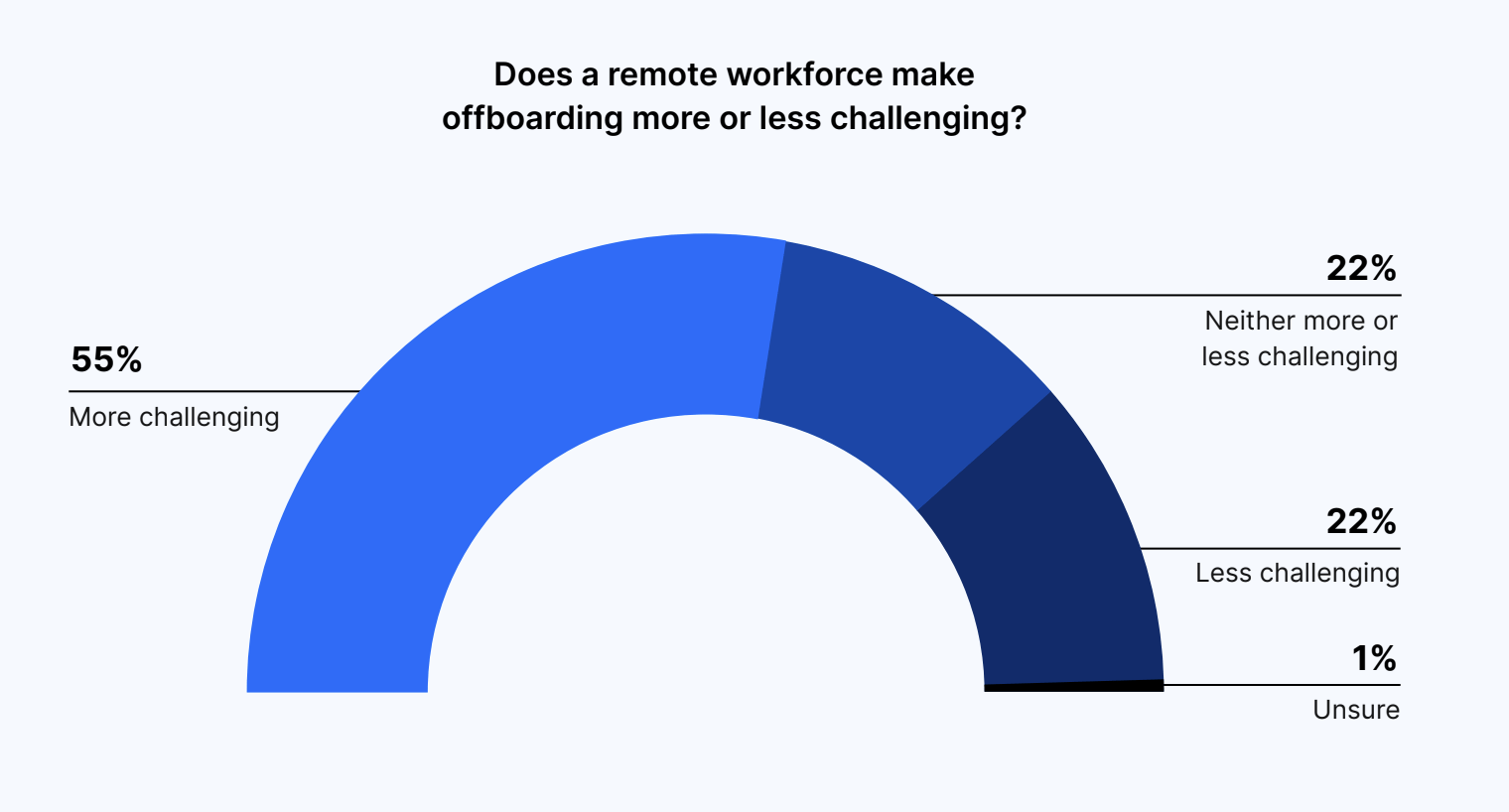
And 55% of IT and security leaders described this remote offboarding process as more challenging.
Does a remote workforce make offboarding more or less challenging?
Offboarding is a significant security threat—with access privileges being the biggest concern
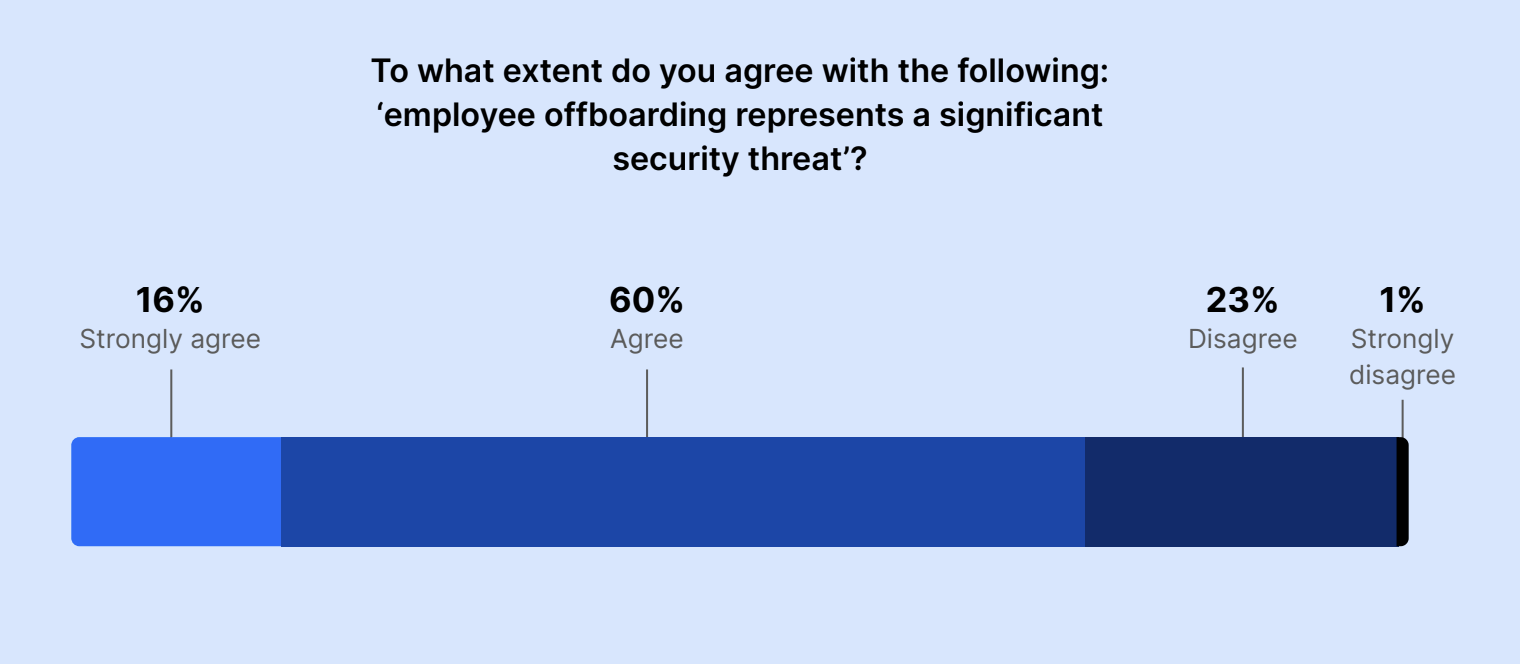
Overall, 76% of executives agreed that employee offboarding represents a significant security threat.
To what extent do you agree with the following: “employee offboarding represents a significant security threat?”
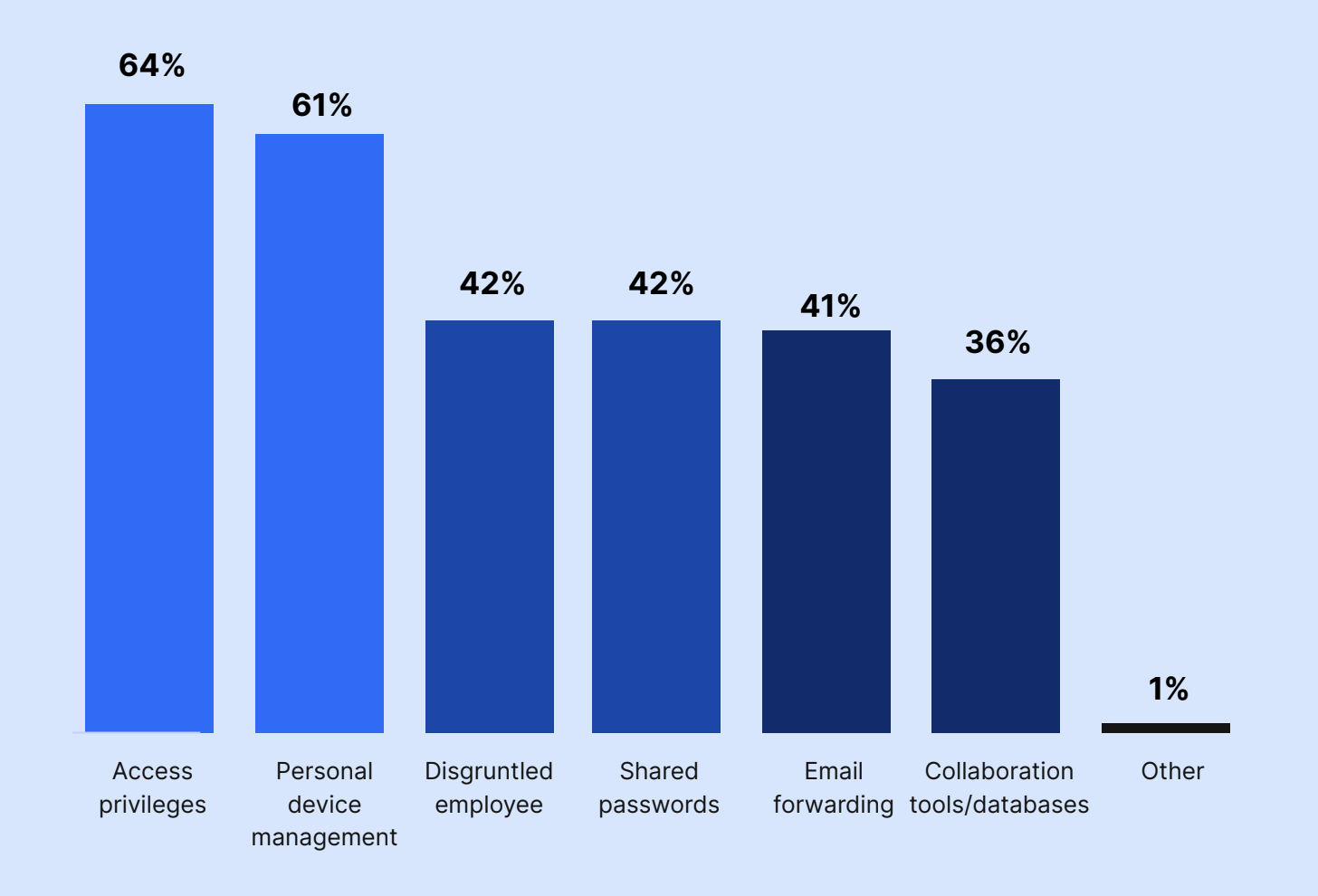
Access privileges (64%) followed by personal device management (61%) presented the biggest offboarding security threats.
Other executives were worried about shared passwords (42%), disgruntled employees (42%), email forwarding (42%), and collaboration tools and databases (36%).
What do you think are the biggest security threats with the offboarding process?
Two-thirds (67%) of executives believed that employees exiting the organization are more likely to cause security breaches by accident, rather than intentionally. This complements research from Nira that says 80% of access-risk incidents are not malicious.
Are you more concerned about accidental or intentional security breaches by employees that are leaving the organization?

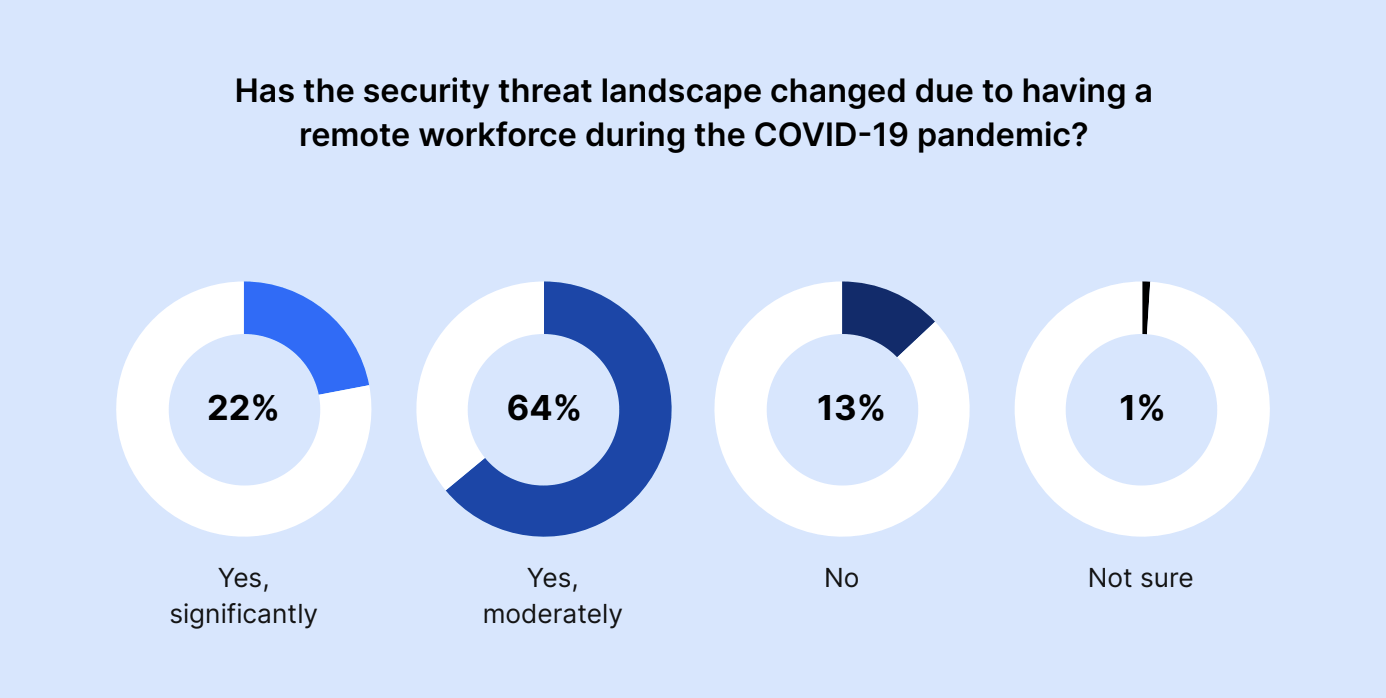
Overall, 86% of IT and security experts believe that security threats have changed due to a remote workforce being in place during COVID-19.
Has the security threat landscape changed due to having a remote workforce during the COVID 19 pandemic?
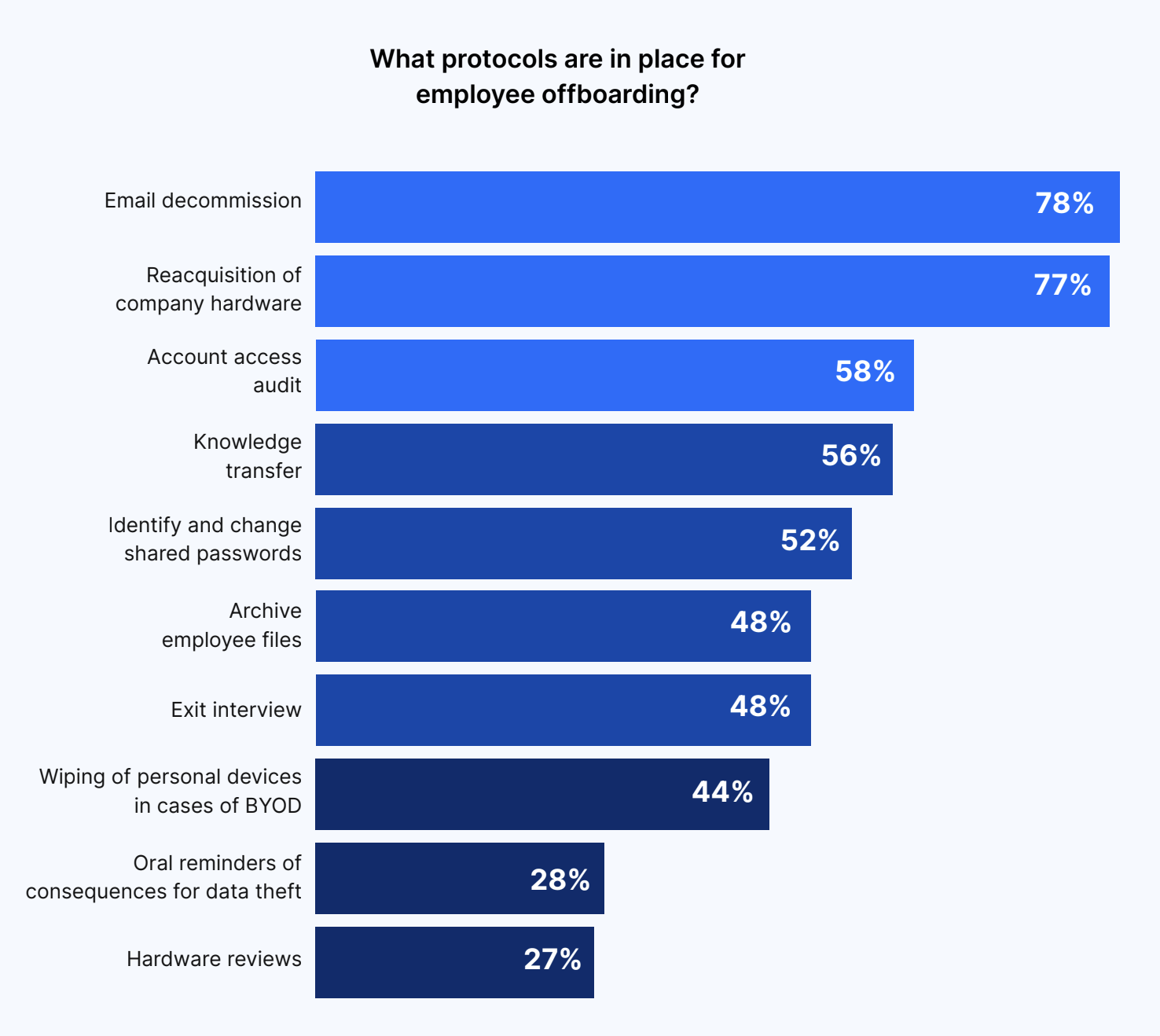
Email decommission and return of company hardware were the top protocols during the offboarding process—and two-thirds now use software to guide offboarding
Email decommission (78%) and reacquisition of company hardware (77%) were the most common offboarding protocols for employees.
Other protocols included an account access audit (58%), knowledge transfer (56%), and identifying and changing passwords (52%).
Companies also noted archiving employee files (48%), conducting an exit interview (48%), and wiping personal devices in cases of Bring Your Own Device policies (44%).
Less common offboarding measures were oral reminders of the consequences of data theft (28%) and hardware reviews (27%).
What protocols are in place for employee offboarding?
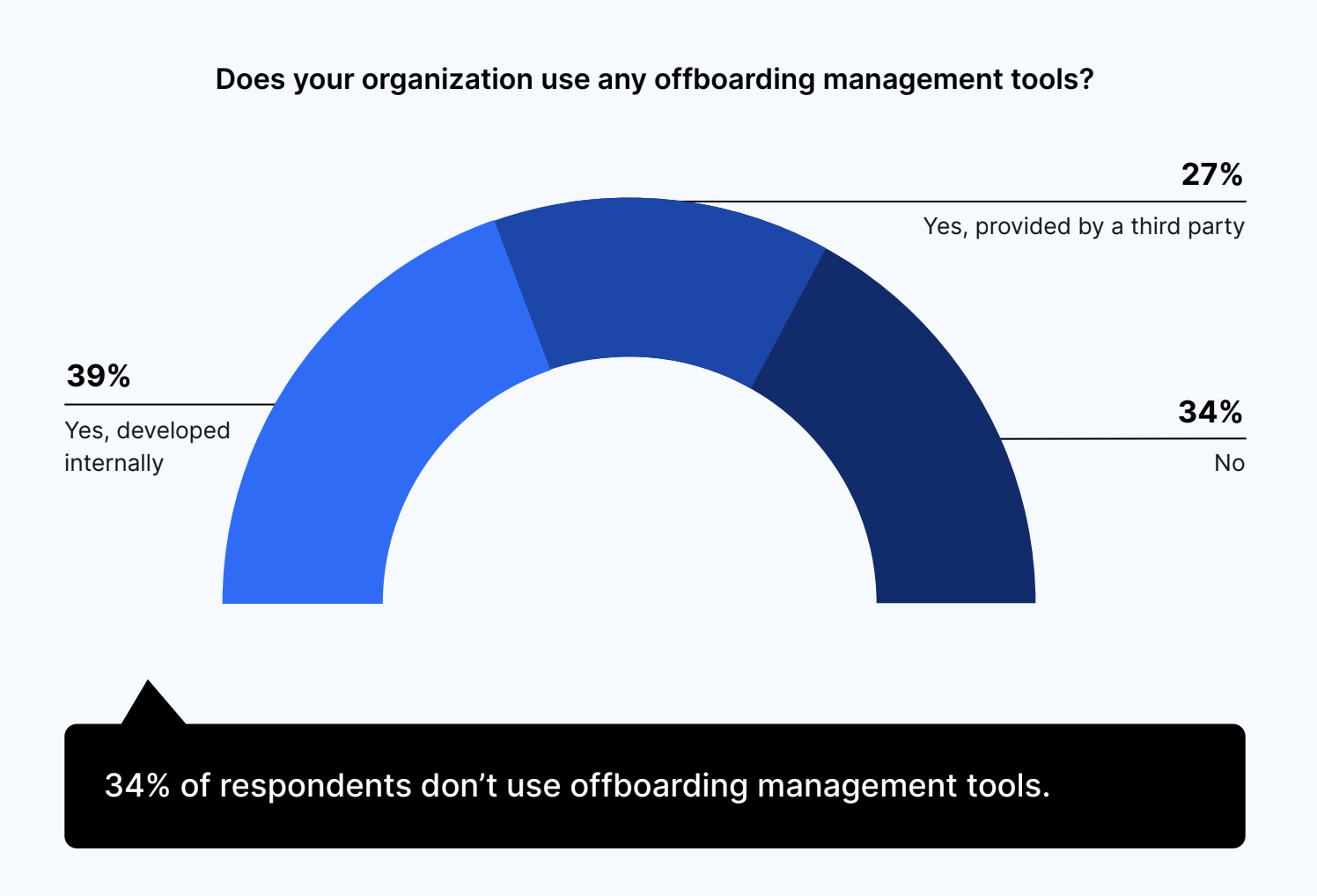
Two-thirds of companies use offboarding management tools, with 39% implementing internal tools and 27% using third-party tools.
Meanwhile, 34% of respondents don’t use offboarding management tools at all.
Does your organization use any offboarding management tools?
Most IT and security leaders believe offboarding protocols are sufficient, but access management remains a priority
Overall, 77% of IT and security leaders believed that their offboarding protocols provided adequate security measures.
To what extent do you agree with the following: “my organization’s offboarding protocols are sufficient with regard to security?”
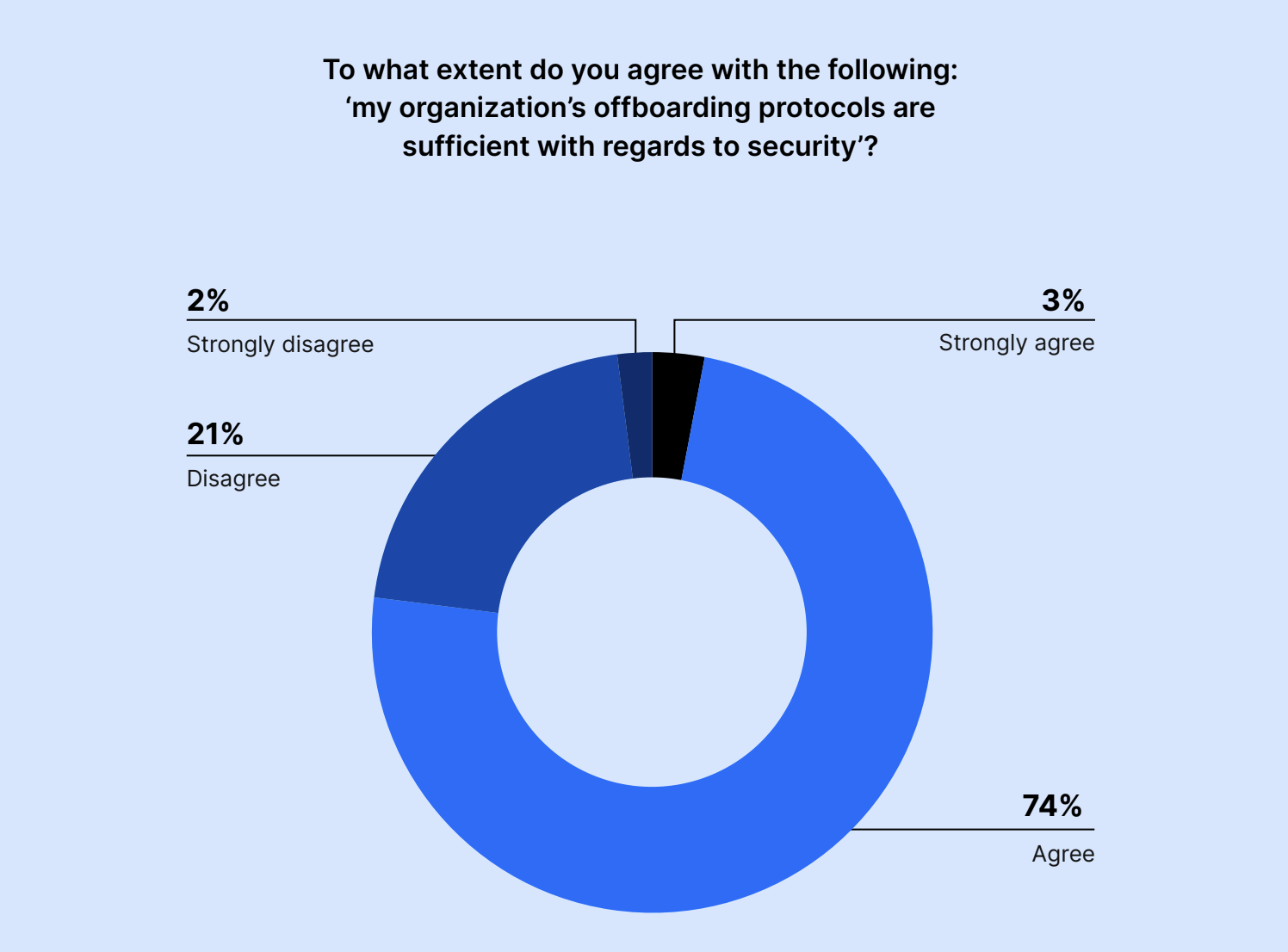
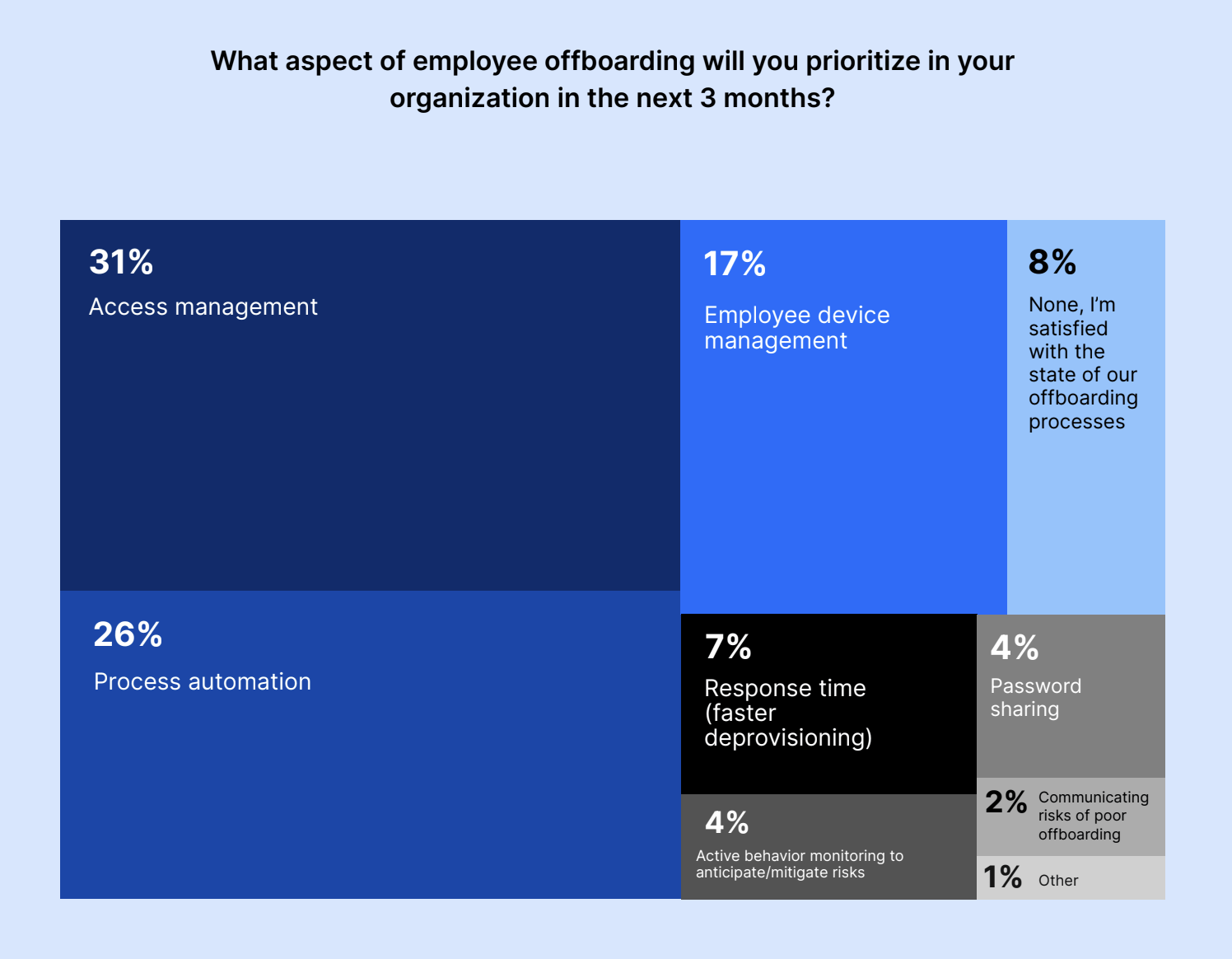
Executives were targeting access management (31%) over the next quarter, followed by process automation (26%). Seventeen percent were interested in employee device management while 8% had no plans to prioritize employee security in the next three months.
What aspect of employee offboarding will you prioritize in your organization in the next 3 months?
Offboarding remains a challenge in a remote, hybrid environment. Traditionally, removing an employee’s access to company documents relied on deactivating the employee’s account. However, this method doesn’t factor in the possibility of employees having access to company data through their personal accounts, either accidentally or on purpose. This access can persist for years after an employee leaves an organization.
Companies should be able to view access from personal or archived accounts, and then take swift action on restricting or removing document access permissions on multiple documents and multiple personal accounts. Companies can help mitigate these risks through the use of a Cloud Document Security system. Learn how to do this quickly and efficiently here.
About Nira
Nira is a real-time Cloud Document Security system that provides complete visibility and control over who has access to your cloud-based company information. Nira provides a single, comprehensive view of who has access to valuable company data.
It allows you to easily identify risks, quickly control access, and efficiently automate policy enforcement and remediation.
Nira also enables employees to manage who has access to their information, without needing technical expertise.
This content, which provides opinions and points of view expressed by users, does not represent the views of Gartner; Gartner neither endorses it nor makes any warranties about its accuracy or completeness.
Source: Gartner Peer Insights, Onboarding Security for the Remote Workforce survey

