State of IT: Cloud Collaboration Risk

Cloud collaboration is increasing, and with it, the risk of unauthorized access to company data. Employees, vendors, and contractors can cause damage, whether their actions are intentional or not.
As organizations strive to make cloud collaboration more secure, we wanted to know where they view the most substantial risks, and what characteristics they search for in potential solutions.
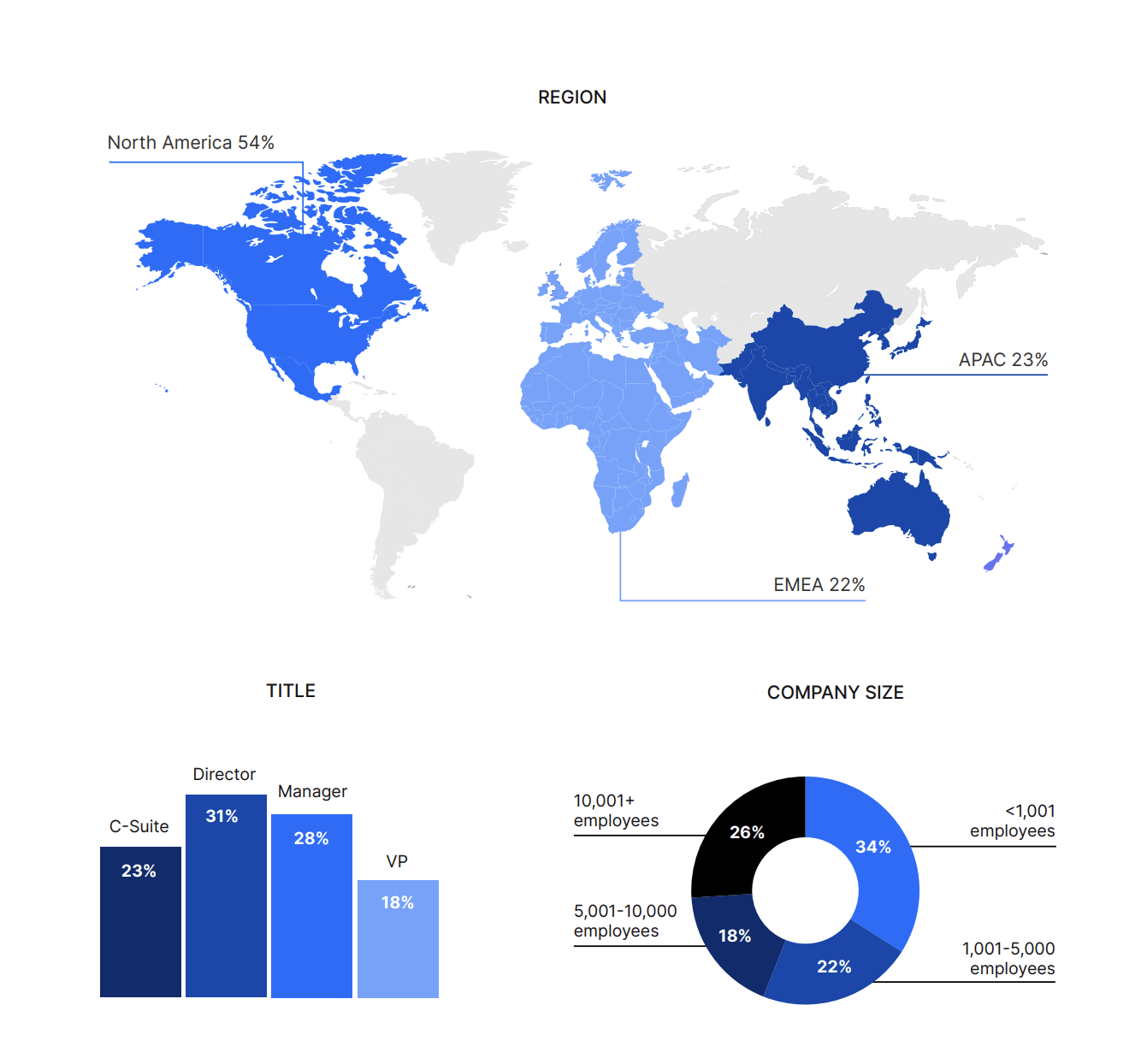
Nira utilized Gartner Peer Insights to survey 570 IT and Security leaders to better understand their top priorities, goals, and concerns about risk when managing and administering their cloud collaboration tools.
Here’s what we learned:
Across IT budgets of all sizes, organizations are expecting to embrace more cloud collaboration tools, despite the risks
Just under half of the respondents (47%) have annual IT budgets of $1M or less, while the other half (53%) have budgets ranging from over $1M to over $5M.
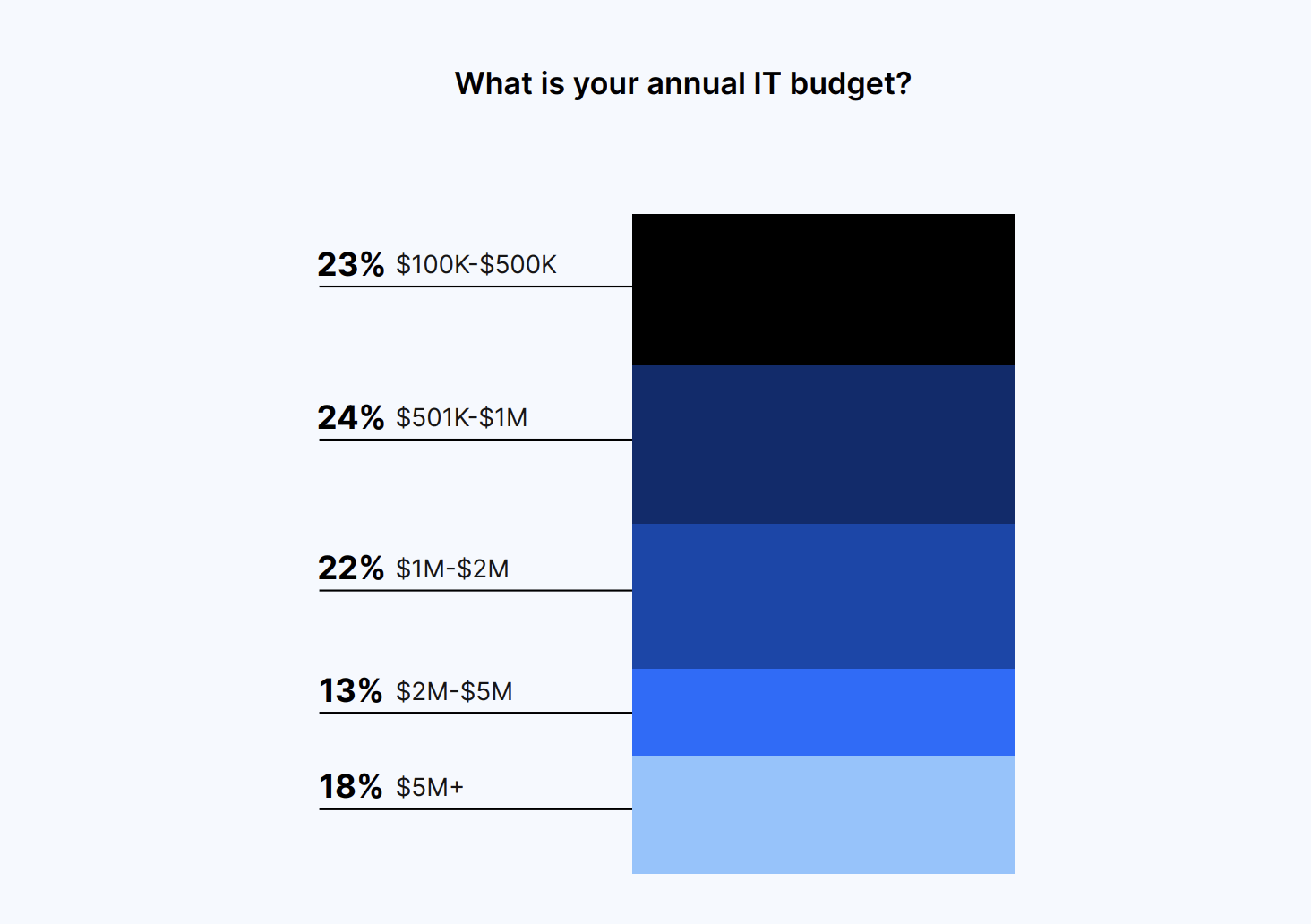
Microsoft 365 is the primary cloud collaboration tool used by the majority (74%) of organizations. In comparison, 25% of leaders cite Google Workspace as their organization’s primary tool.
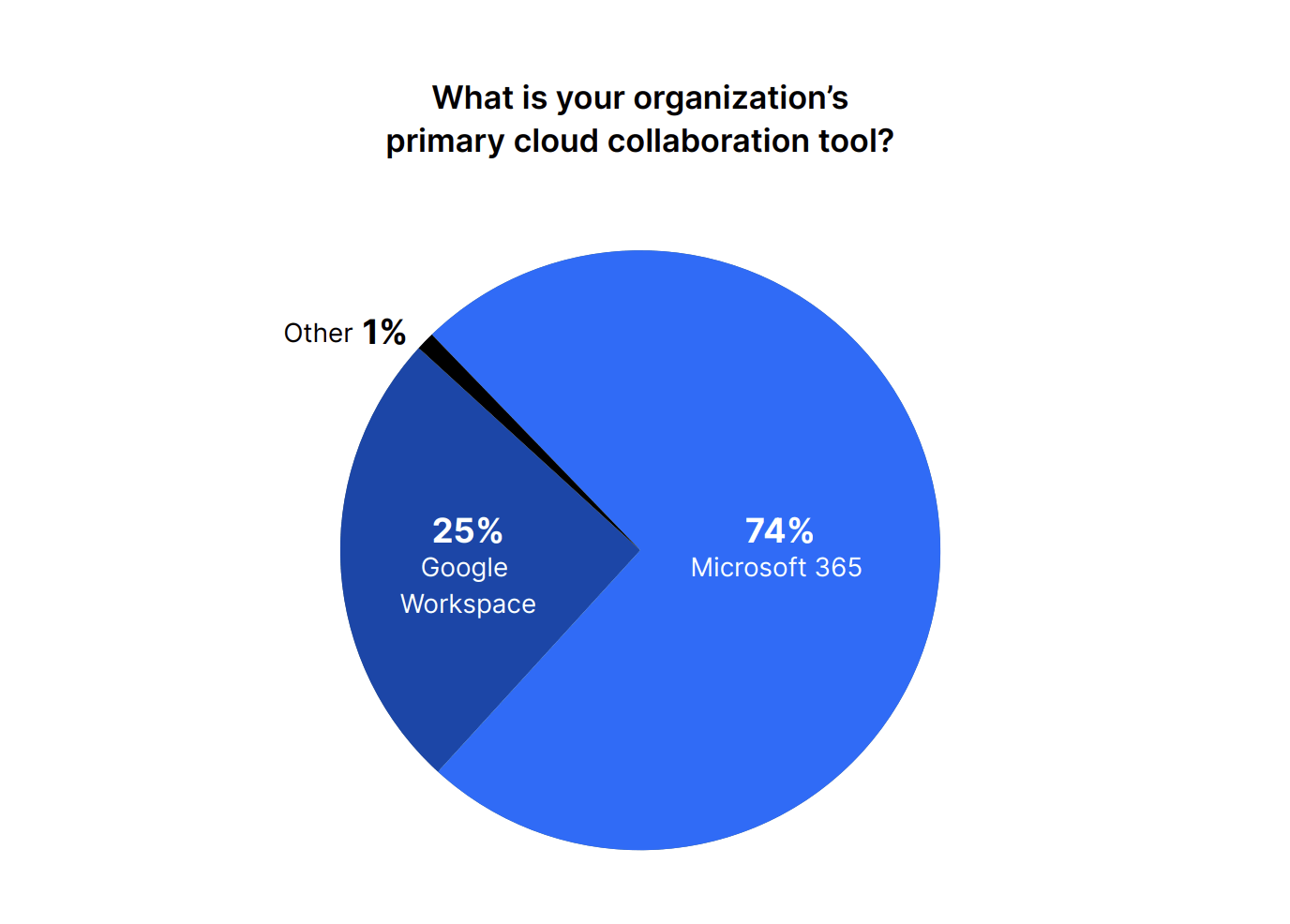
We found that over the last 24 months, a whopping 83% of organizations have increased their adoption of cloud collaboration tools. Twelve percent said that their adoption of cloud collaboration tools has stayed the same, while 5% said it decreased. This tracks with the idea that employees need to collaborate more than ever with internal and external parties due to the rise of remote and distributed work.
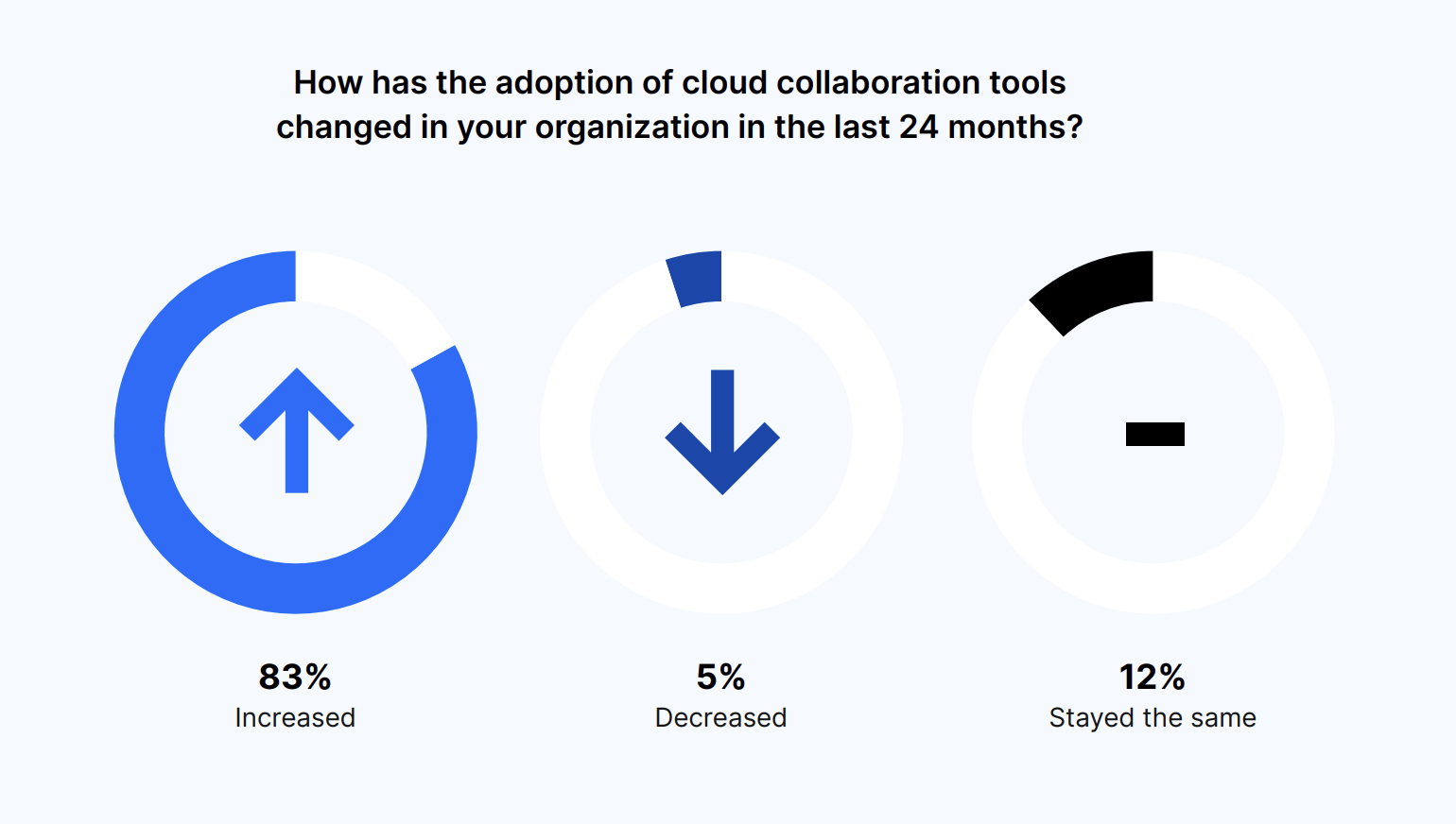
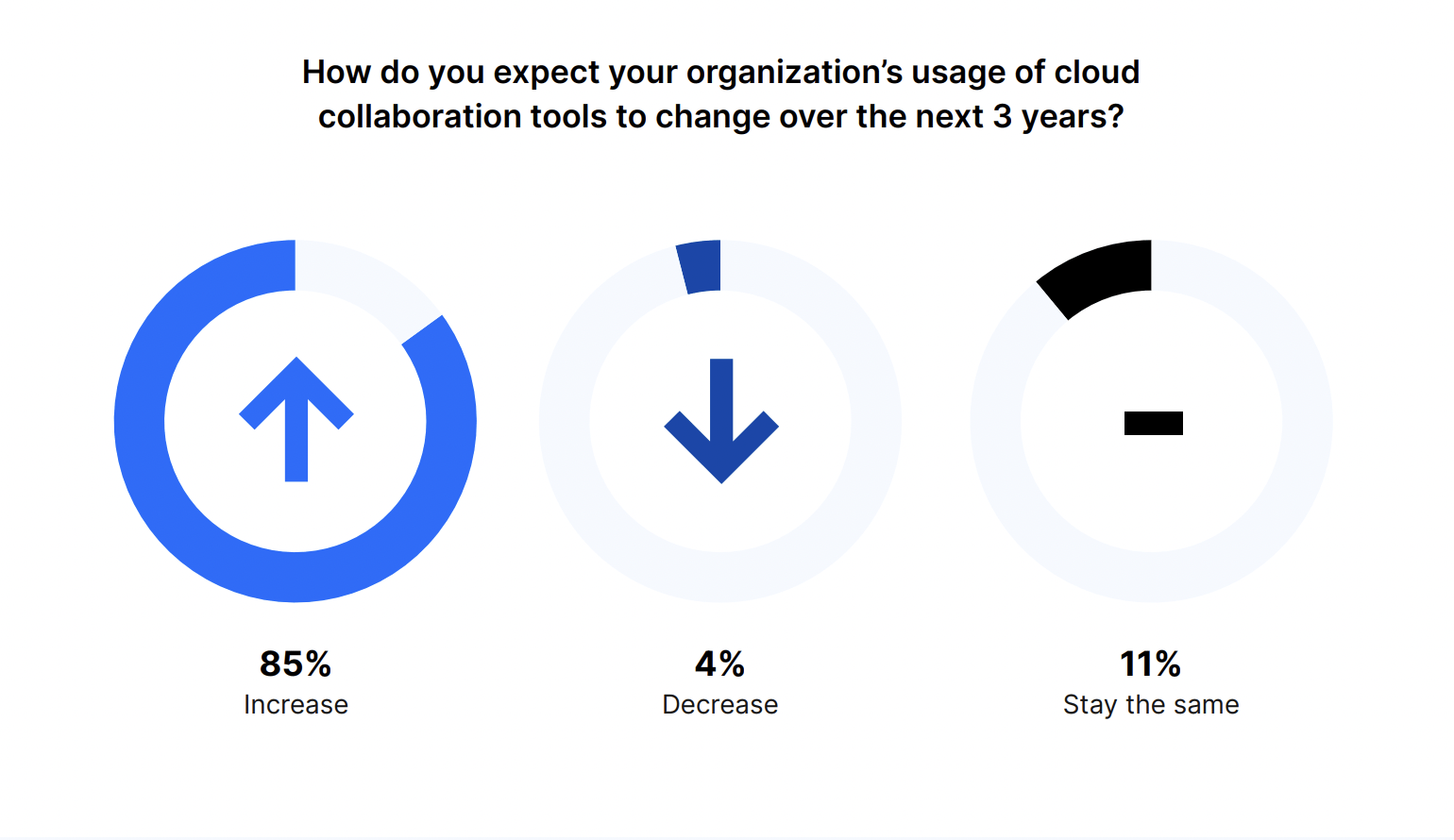
And this trend will only continue. Eighty-five percent of respondents expect their organization’s usage of cloud collaboration tools to increase over the next three years. Similar to the last question, 11% expect usage to stay the same and 4% said it will decrease.
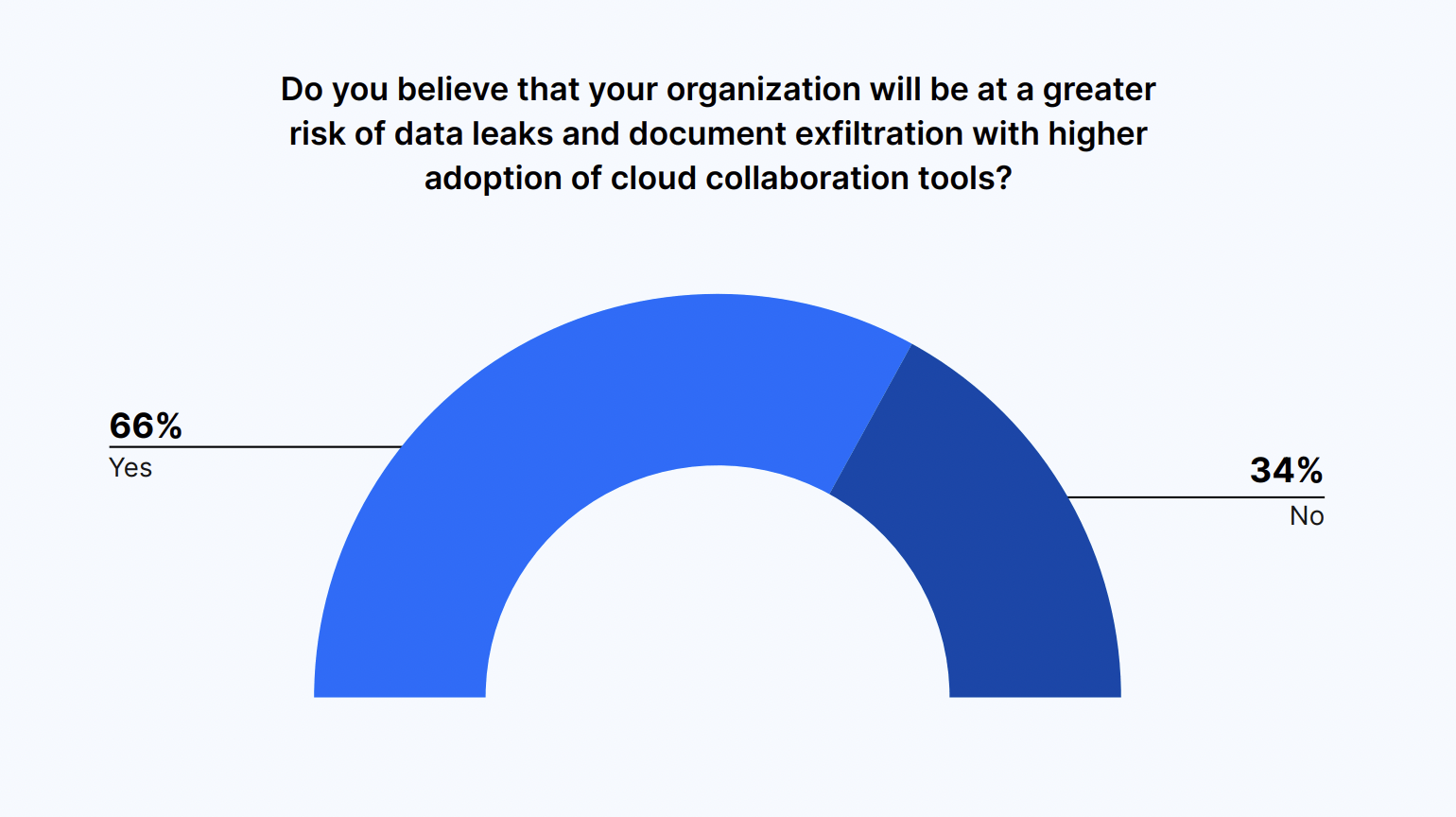
With wider adoption of cloud-based collaboration tools, comes a higher risk of vulnerabilities. Two-thirds of IT and security leaders (66%) say their organization will be at greater risk of data leaks and document exfiltration as their organization’s adoption of cloud collaboration tools grows.
Unauthorized access caused by employee and vendor mistakes keeps IT and Security professionals up at night, as it can result in litigation or compliance issues
Employees are often the first line of defense when it comes to securing cloud collaboration tools. And according to research, the majority see themselves as responsible for securing access to sensitive company files.
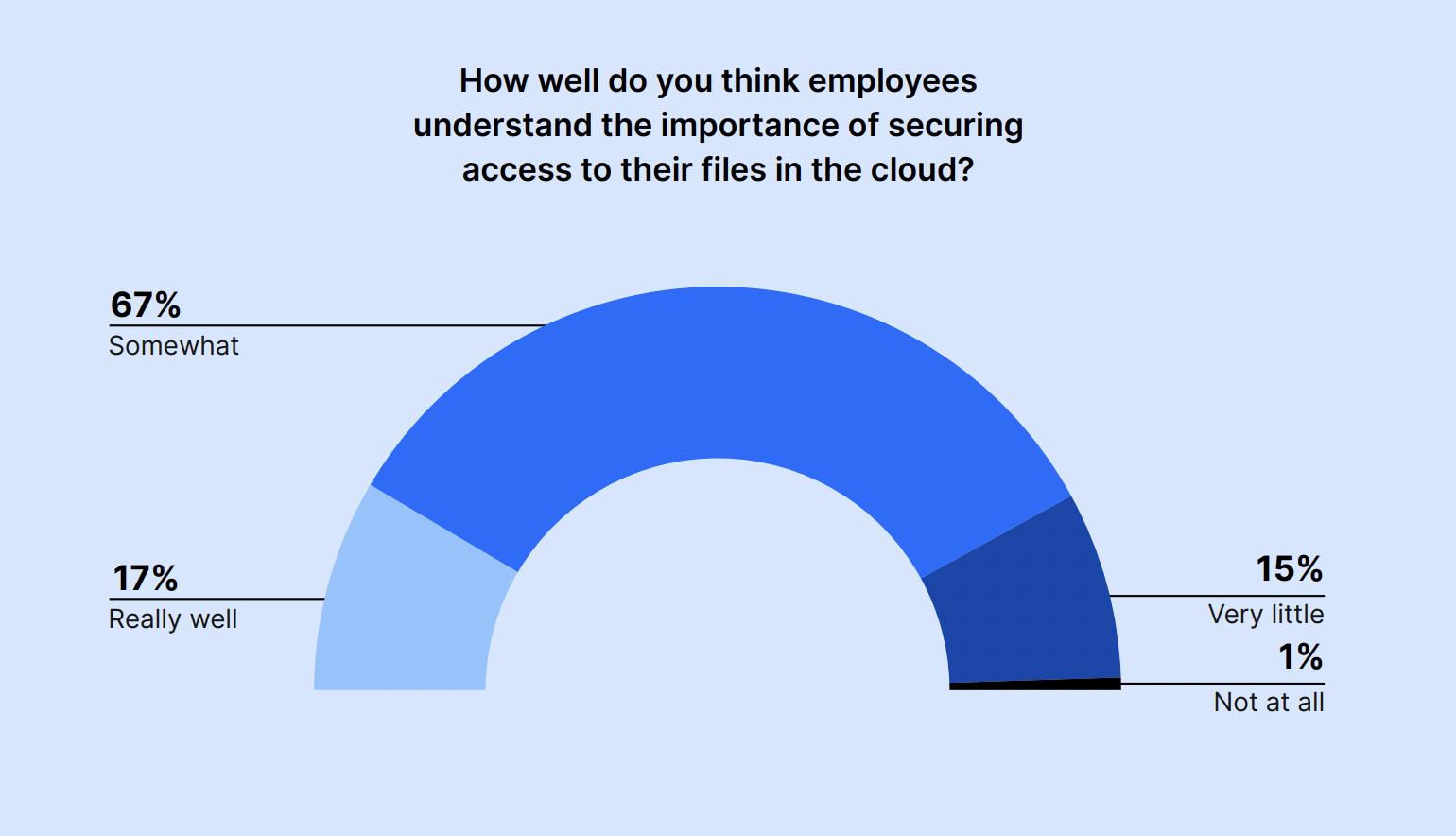
However, only 17% of IT and security leaders believe their employees understand the importance of securing access to their files in the cloud “really well.” The majority – 67% – said employees somewhat understand the importance, while 15% said they understand it “very little.”
If employees don’t fully understand the importance of security access to cloud-based files, they are more likely to make mistakes that put the company at risk. And this is likely why IT and Security leaders are more concerned about employee mistakes and malicious behavior than that of external parties.
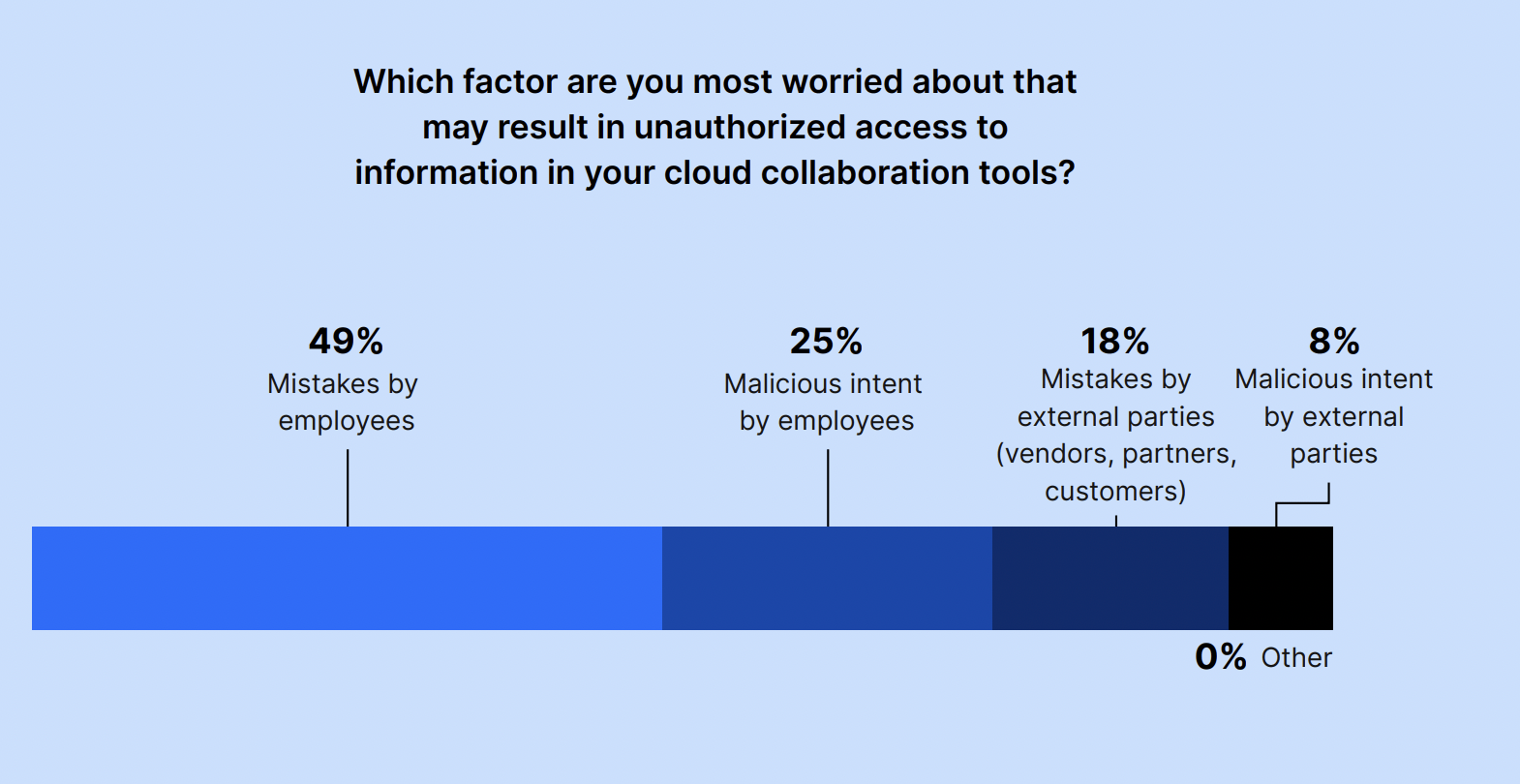
We asked IT and security leaders: Which factor are you most worried about that may result in unauthorized access to information in your cloud collaboration tools?
The majority of respondents are concerned about employees (74%), versus those who are concerned about external parties like vendors, partners, and customers (26%).
The factor they’re most worried about is mistakes by employees, with 49% of respondents choosing this option, followed by malicious intent by employees, at 25%. Less than a quarter of respondents (18%) were most concerned about mistakes by external parties, while 8% were most concerned about malicious intent by external parties.
While most data breaches are not malicious, mistakes and errors by end users can still cause harm. The survey responses echoed this fact: Sixty-seven percent of leaders are most worried about mistakes in general, either by employees or external parties. In contrast, only 33% are most worried about malicious intent by employees or external parties.
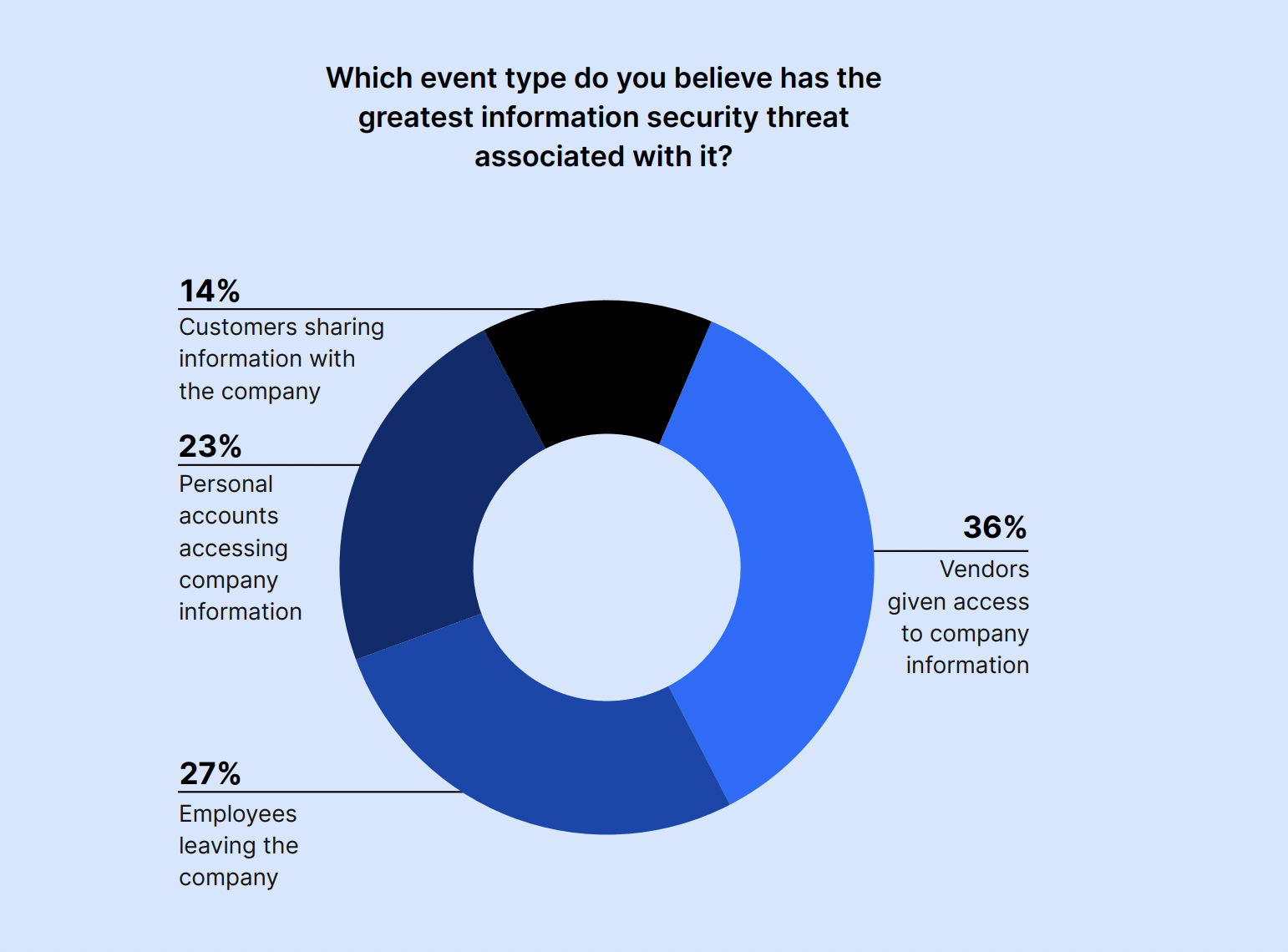
Vendors being given access to company information is the event that respondents said poses the greatest information security threat, with 36% of IT and Security professionals choosing it. Meanwhile, employees leaving the company came in second at 27%, and personal account access came in third at 23%.
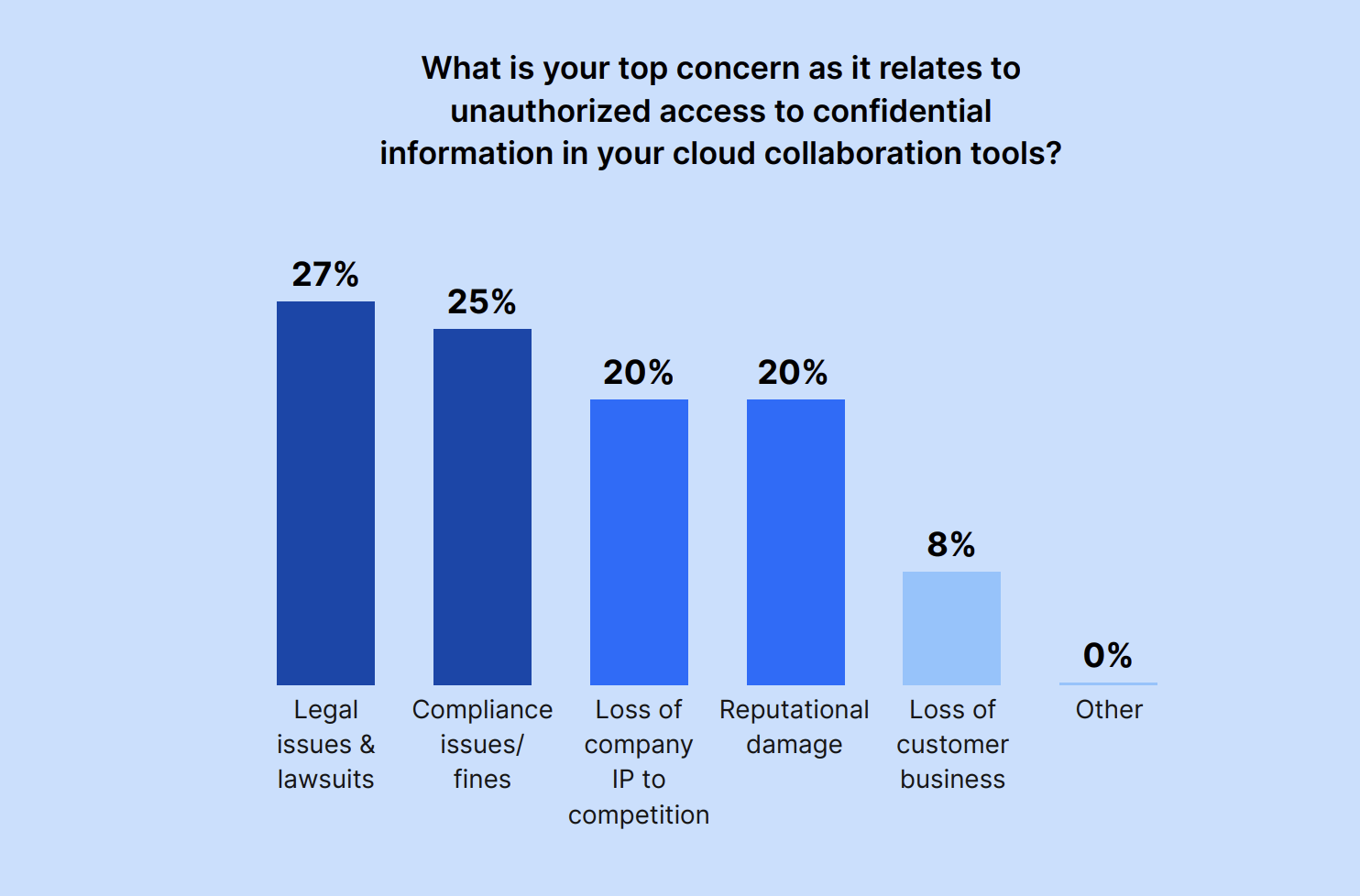
When asked about their top concern about unauthorized access to confidential information in cloud collaboration tools, the majority of leaders are most worried about legal issues or compliance issues and fines; over half (52%) cite them as their top unauthorized access concern.
Other IT and Security professionals are concerned about the loss of company IP to competition (20%) or damage to the company’s reputation (20%).
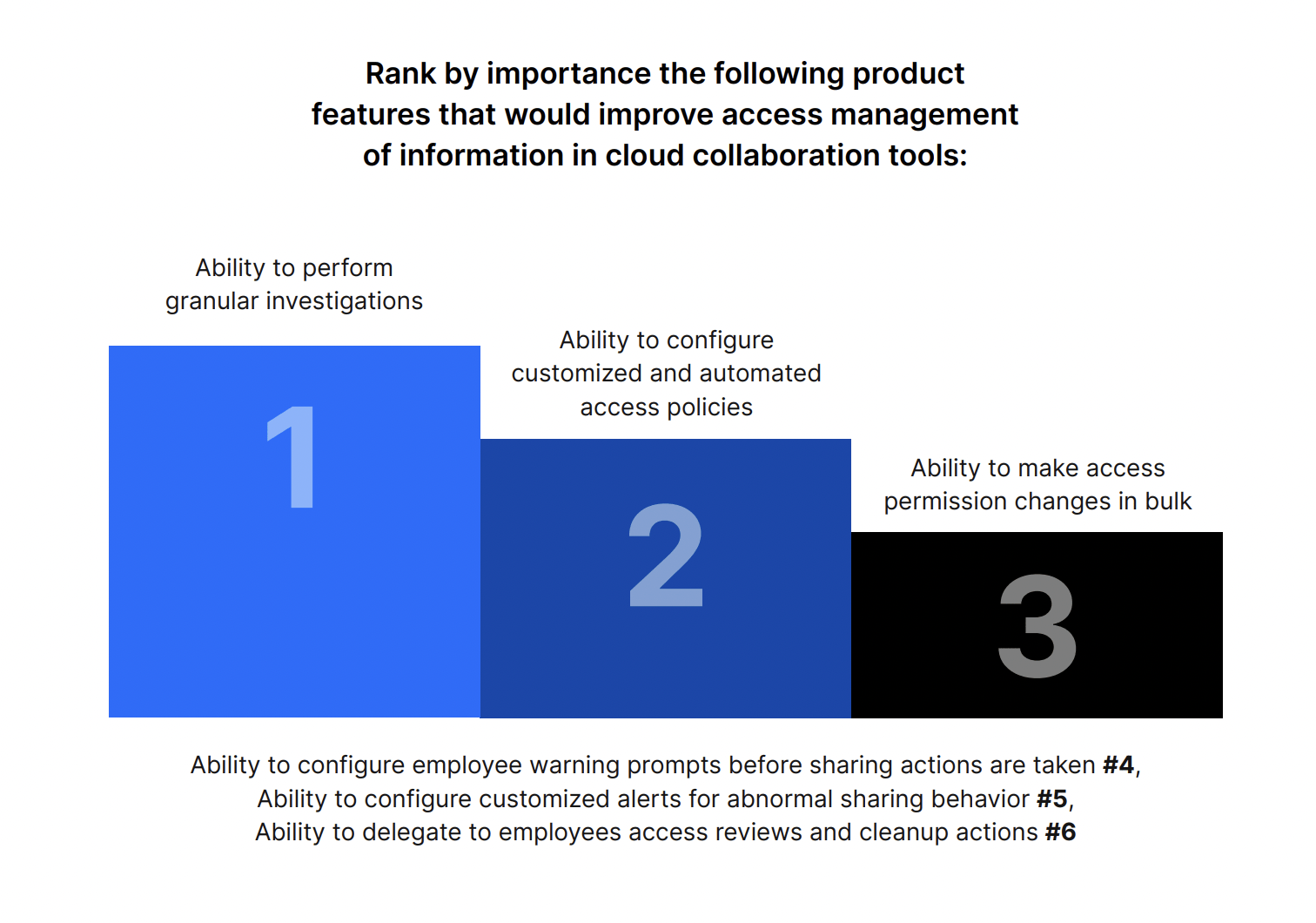
Decision-makers want the ability to perform granular investigations and automate policy enforcement while expecting quick time to value and easy tool onboarding and UI
Respondents ranked the ability to perform granular investigations as the top feature that will improve access management of information in cloud collaboration tools.
They also see value in the ability to configure customized and automated access policies, and they want the capability to change access permissions in bulk.
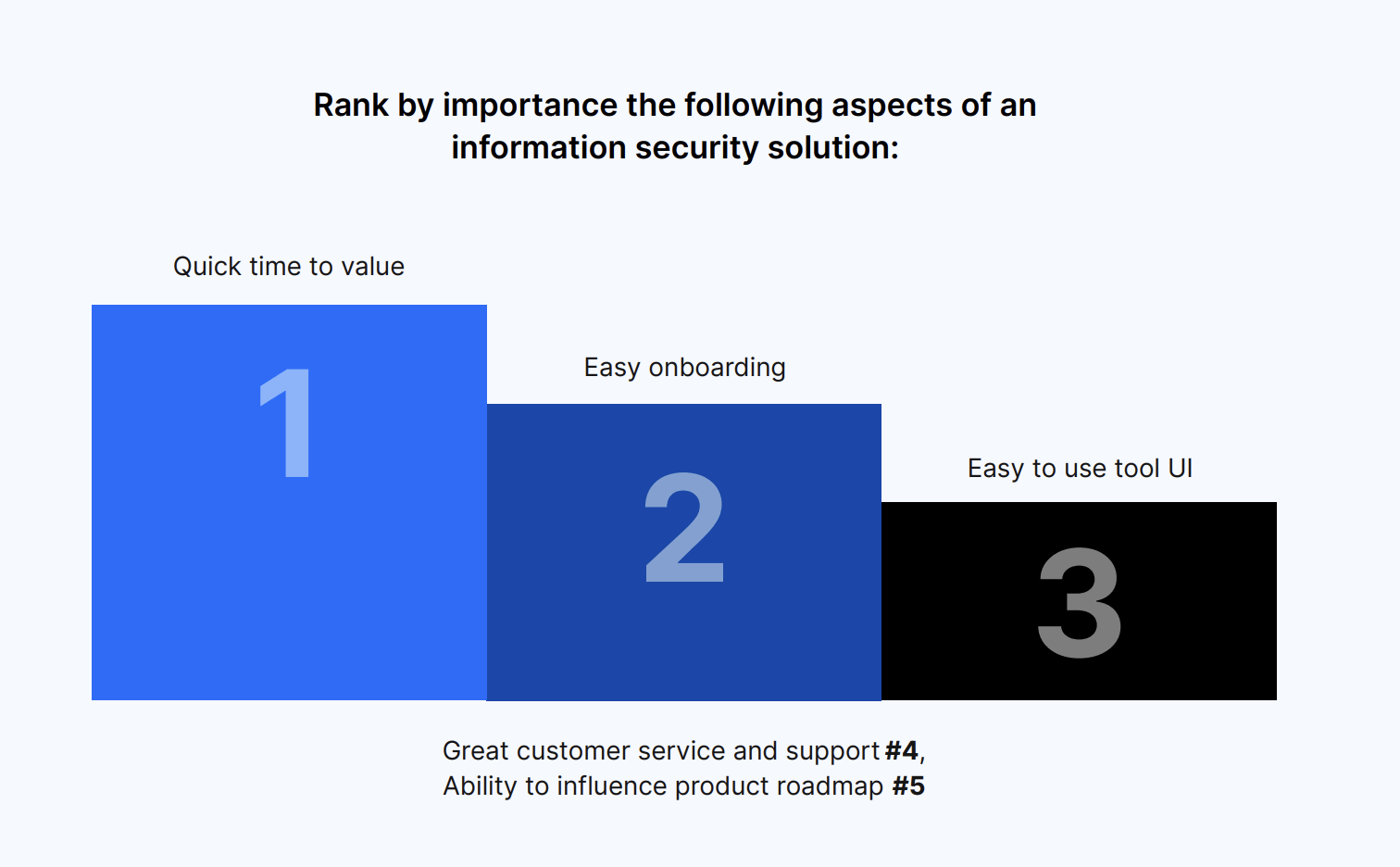
When it comes to an information security solution, decision-makers rank quick time to value as the most important aspect. An easy onboarding process and an easy-to-use user interface are also key.
IT and Security leaders are concerned about the information security risks associated with cloud collaboration tools. But this hasn’t stopped them from increasing the usage of cloud-collaboration tools in their organization, a trend that will only grow over the next three years.
To mitigate risk and keep their workspaces secure, IT and Security leaders want tools that allow them to perform granular investigations of potential issues, automate and customize access policies, and change access permissions in bulk. They also prioritize tools with quick time to value, easy onboarding, and intuitive UI.
While human error or even malicious intent remains a concern, IT and Security professionals are willing to work through the challenges of cloud collaboration. Rather than lock down all workflows or outlaw cloud collaboration entirely, leaders are seeking solutions to keep their vital company and customer data safe.
About Nira
Nira is a real-time Data Access Governance system that provides complete visibility and management over who has access to your company documents in Google Workspace and more. Nira provides a single, comprehensive view of who has access to valuable cloud-based company data. It allows you to easily find and identify risks, quickly control access and fix issues, and efficiently automate the process through policy enforcement and remediation delegation. Nira also enables employees to manage and control who has access to their information, without needing technical expertise.