What is an Access Control System, and Why Do You Need It?
If you’re a business owner or IT manager, external security is always top of mind. But have you thought about the importance of access control for your company documents?
The majority of cybersecurity threats come from outside your business, but internal problems can cause devastating security breaches.
Employees rely heavily on mobile and cloud-based storage as we’ve increasingly shifted to remote work. With sensitive and personal data living in the cloud, it’s become much easier to expose data.
While tech that enables cloud-based collaboration isn’t necessarily a threat, problems arise when people copy sensitive data from a company account to their personal accounts. Unfortunately, this happens more often than we think, with over 45% of employees admitting to taking documents from former employers.
Do you know who can access your company documents?
When people think about document access issues, malicious intent often springs to mind. But the reality is that many access problems are not on purpose. For example, 52% of people have accidentally added their personal accounts to company documents.
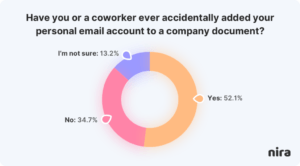
Typical day-to-day collaboration leads to accidental access issues. Documents get shared with and created by personal accounts, old vendors can still access documents they shouldn’t, and too many documents have public links that anyone on the internet can view.
Vendor access is an afterthought at most companies; 60% of companies don’t consistently remove a vendor’s access once they stop working with them.
Setting up documents with public links has become the norm to share documents quickly. In a rush, people even add public links to confidential documents. As a result, companies end up with tens of thousands of documents with public links just floating around.
The majority of companies ignore their document access problems or never have enough visibility into who has access in the first place. This ignorance leads to leaks, breaches, and lawsuits.
So how can an access control system help? What are the benefits, and why do you need one?
What is an access control system?
When we talk about access control, we usually mean one of two types: physical or logical. Physical access control is just as it sounds: the level of access given to a company’s physical space or physical assets. In computing, we deal more with logical access control.
A logical access control system is an automated system that controls an individual’s ability to access one or more computer system resources.
Why is an access control system so important?
It’s becoming critical to have a proper access control system in place as cyberattacks cost businesses millions each year.
An Interpol report found that the costs associated with insider threat breaches reached an average of $7.68 million in 2020. Unfortunately, this number continues to rise, and with the increase of people working from home, companies’ security vulnerabilities have spiked.
An access control system controls who can view or use any given resource. This can translate to who can access and edit a particular file, what kinds of equipment can be used, or who can access specific devices in an IT security setting.
Access control systems are crucial for business owners.
The ultimate goal of an access control system is to provide a level of security that reduces risk to a company. Your business centers on data: from employee onboarding and offboarding to product plans, financial documents, and customer details. Every company must pay close attention to how they store, access, and protect their assets.
Without proper access control, companies leave their staff and customers vulnerable to cyberattacks, data theft, or breach of privacy and data protection laws.
The benefits of having an access control system
Here are the benefits of implementing robust access control in your organization:
- Monitor and protect your most important documents, assets, and resources.
- Easily offboard employees by removing access to each of their accounts, including personal accounts, that were added to documents.
- Have complete peace of mind knowing that your data is secure and can only be accessed by assigned people.
- Gain total visibility: always know who is accessing your data and when.
- Modify user permissions and block unauthorized permissions quickly and efficiently.
- Improve regulatory compliance and compliance with data privacy laws. Avoid fines, revoked licenses, and, in worst-case scenarios, criminal liability.
- Enhance security to keep your business, employees, and assets secure from cyberattacks.
How do access control systems work?
There are three essential ingredients to all access control system setups:
- Identify who is accessing the secured company information, areas, or assets.
- Verify the individual to ensure they have the correct permissions to grant or deny access, whether for a particular file, document, or resource.
- Authenticate and grant access to the individual—this can be done by using a password, PIN, encryption, smartcard, or fingerprints.
Access control systems identify users by verifying various login credentials, including usernames and passwords, biometric scans, and security tokens. Once a user is verified, the access control system then authorizes the appropriate access level and allows actions associated with that user’s credentials and IP address.
How can I implement a real-time access control system for my business?
Any business that wants to improve its overall IT security and reduce risk should have an access control system.
At Nira, we take the security of your sensitive data seriously. We are SOC 2 Type 2 certified and are audited annually.
Security is our highest priority and integral to how we operate.
Our setup takes two minutes, and within 48 hours, Nira will give you complete visibility into the state of your Google Drive with no further configuration required. Tasks that used to take hours now take a few minutes.
Why should you use Nira?
Protect critical documents
- Monitor and protect your most important documents, folders, and shared drives, such as sensitive documents owned by the finance team, board meeting decks, and IPO materials.
- Protect documents owned by company executives and receive alerts when access to those documents falls outside of company policies.
Identify public links
- Quickly identify all documents with public links, assess their risk, and remediate any issues.
- Find and close all public links on documents that haven’t been modified for more than a year.
Streamline offboarding
- Fully offboard employees by removing access on each of their accounts, including personal accounts, and transferring documents ownership to new accounts.
Uphold document retention policies
- Delete all documents that fall outside of granular document retention policies.
Conduct investigations
- Deep dive into document-related incidents and conduct instant remediation without having to jump between tools.
Automate alerts
- Remediate the riskiest document access issues based on notifications from Nira.
Remove risky personal accounts
- Identify all personal accounts with access to company documents, assess their risk, and remove unnecessary access.
- Identify all current and former employees with personal account access and remove their access to company documents.
- Identify documents owned by current and former employees’ personal accounts and transfer ownership to the company.
Set up automations
- Automatically remediate document access issues based on company policies.
Manage third parties/vendors
- Identify all vendors and third parties with access to company documents, assess their risk, and remove unnecessary access.
- Fully offboard vendors by removing access for all of their accounts and transfer ownership of those accounts.
- Identify public links and unauthorized access on confidential documents owned by vendors.
How to protect your documents today
When it comes to access control systems, the main points to remember are:
- An access control system is essential and should be incorporated into your overall IT security plans.
- Access control systems protect against breaches of privacy, cyberattacks, and data theft.
- Access control can be used to monitor who or what can view or use any given document, asset, or resource.
- The biggest goal of an access control system is to provide a level of security that minimizes risk to any business.
Need help reviewing your current setup or implementing new access controls for the data you already have? Contact us for a demo.
Nira currently works with Google Workspace, with more integrations coming soon.

