The Complete Guide to Symantec Cloud Security
Since its acquisition by Broadcom, Symantec cloud security has been developing tools to serve the needs of Global 2000 organizations.
The consumer portion of Symantec is now a separate entity (Norton LifeLock), leaving the company free to focus on scalable security solutions with rich compliance and governance capabilities.
By reorienting the company in this way, Broadcom is trying to leverage Symantec’s deep product portfolio and name recognition to corner their piece of the booming enterprise cloud market.
But how good is Symantec cloud security? And how does it compare with the other top cloud security solutions on the market?
In this post, we’ll walk through Symantec’s cybersecurity offerings, differentiate them from other leading providers, and close by considering which organizations will benefit most from Symantec cloud security.
Overview of Symantec Cloud Security
As companies add tools to their arsenal to defend against the ever-growing number of new threats, it gets harder and harder to keep track of what’s happening in their environment. This is only more true for hybrid, multi-cloud, and global deployments.
There are thousands or millions of users who expect always-available cloud resources. These could be employees, customers, or partners who all need different levels of access. With so much control over policies and so many signals being detected, it’s easy for teams to get overwhelmed.
And, if your teams are trying to accomplish this impossible task with tools from a variety of vendors, the problem compounds in unseen ways. With information coming in from multiple vectors, warnings go unnoticed, patches aren’t distributed, and encryption keys aren’t maintained.
The all too common story is that the many “fixes” create new vulnerabilities because it’s impossible to implement patchwork security perimeter properly.
In refocusing Symantec cloud security on enterprise needs and trimming back on everything else, Broadcom believes they can offer clients a simpler and more effective overall cybersecurity solution. By providing a relatively small number of potent products, companies can better monitor and improve security posture across an organization.
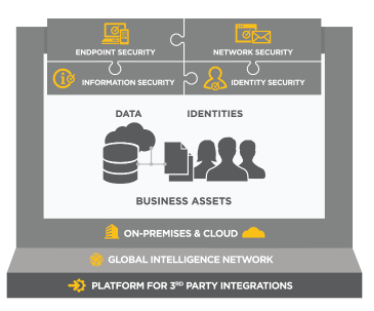
Symantec groups their cybersecurity tools under four general areas:
- Endpoint security
- Identity Security
- Information Security
- Network Security
All of these tools can be managed from Symantec Integrated Cyber Defense Platform, which can be deployed on-premises, cloud or hybrid.
Their products may also be purchased separately, though they work best together. The capabilities of one tool enhance those of another. For instance, you can use Symantec Endpoint Security to resolve an issue flagged by Privileged Access Management.
Semantec’s cloud security products interlock, providing total visibility and a gapless perimeter. Let’s go through the key tools from each area.
Symantec endpoint security tools
Endpoint Security is a single agent-based solution that works for on-premises, cloud, and hybrid deployments. From a single platform, you can manage traditional and mobile endpoint devices, creating interlocking defenses at the device, network, and application level.
Symantec Endpoint Security gives IT teams the ability to visualize and respond to threats targeting endpoints in a simple, intuitive console. It integrates with your other Symantec cloud security services to enable rich control over all endpoint devices.
Server Security lets companies protect workloads in public, private, and hybrid cloud deployments. You can use Symantec Data Center Security, Symantec Cloud Workload Protection, and Symantec Storage Protection to harden any type of environment you need to enable your business.
Endpoint Management simplifies software and OS deployment, update, and migration. Automate the process of distributing patches at scale, even to remote and roaming endpoints. Symantec Endpoint Management streamlines the oversight of third-party and Symantec cloud security integrations on your devices, ensuring they are healthy and up-to-date.
Symantec identity security tools
Privileged Access Management (PAM) minimizes the risk that an attacker can compromise accounts with administrative credentials. Symantec PAM is easy to deploy and monitors privileged account activity across all IT resources from core to edge. Many of the emerging compliance requirements for data privacy can be addressed with PAM.
Site Minder is a unified access management platform with single sign-on and identity federation that enables users to safely access cloud, mobile, and web apps. It monitors the entire user session, and gives you the ability to enforce security policies for sensitive data.
VIP is a scalable authentication solution that protects customer, employee and partner access to your mobile and web apps. There are a range of authentication options available with Symantec VIP, all of which are designed with a hassle-free end-user experience in mind. Protect customer accounts from being hijacked and new account fraud with zero-trust access.
IGA is an identity governance and administration tool meant for businesses that need to manage and store millions of user identities.
Symantec IGA ensures that the company has oversight for compliance and to protect against breaches, and automates many of the review processes associated with user privileges and entitlements. It also gives end-users a large range of self-service capabilities, like resetting passwords, which decreases the strain on your helpdesk.
Directory is a next-generation version directory server that is built to scale and perform in a distributed environment. Symantec Directory is an always-available and service that works consistently across on-premise, cloud, and mobile applications.
Advanced Authentication combines automated risk-assessment with two-factor authentication (2FA) to provide extra layers of intelligent security. Symantec Advanced Authentication uses information about user behavior, device identification, geolocation, and other factors in order to screen for inappropriate access without disrupting the end-user experience.
Symantec information security tools
CloudSOC CASB is a cloud access security broker that gives companies visibility and control over the application-usage and shadow IT. As a CASB, it is as robust as any on the market, leading the cloud security gateway category in a recent report from Forrester.
Integrations with the other Symantec cloud security tools extend CloudSOC CASB to function as a complete security operation center. Administrators can monitor and respond to incidents in real time with granular control over policies and permissions across their total IT environment.
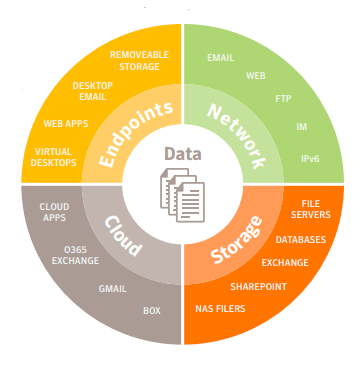
Data Loss Prevention (DLP) tools included with Symantec make it easy for companies to discover, monitor, and safeguard their data from theft or inappropriate access. Whether data is on endpoints, in-transit, at rest, or in the cloud, all encryption and data loss policies can be managed from a single pane of glass in the Symantec DLP Enforce Platform.
Secure Access Cloud creates a software defined perimeter (SDP) that uses zero trust access principles to provide point-to-point connectivity at the application level. It’s an easy-to-deploy, agentless solution that eliminates inbound connections to your network, effectively cloaking corporate applications and services from attackers.
Encryption is easy to manage in Symantec cloud security. Whether you need to secure data on endpoints, files and folders, email, or implement secure socket layer (SSL) encryption, Symantec has cost-effective, intuitive solutions.
Control Compliance Suite allows you to automate the IT assessment of complex, hybrid, and multi-cloud deployments. Discover your entire infrastructure (web, cloud, mobile, virtual, and IoT), identify vulnerabilities or misconfigurations, and automate remediation processes to ensure continued compliance across your organization.
Symantec network security tools
Secure Web Gateway functions as a proxy between users and the internet that terminates traffic, allowing for its inspection and filtering before releasing data to the user. This prevents advanced threats from ever reaching the network, and protects users while they browse.
Messaging Gateway provides multi-layered protection for email. It automatically stops many of the most common phishing and spam attempts. Symantec Messaging Gateway also detects malicious URLs and attachments in emails, removing them for isolation and sending a cleaned version of the email to the end user.
Encrypted Traffic Management is powered by the Symantec SSL Visibility Appliance, which supports TLS 1.3 (RFC 8446). It gives you visibility and the ability to manage encrypted traffic without having to re-architecture your existing network infrastructure.
Advanced Threat Protection (ATP) integrates with all of your other Symantec cloud security services to provide content and malware analysis across your entire environment. With Symantec ATP, you can leverage insight from the company’s Global Intelligence Network to surface and respond to threats faster.
What differentiates Symantec from other cloud security solutions?
Many vendors offer a centralized platform to oversee the security posture of your “entire” environment. This stretches the truth, though, especially if you have widely distributed assets, users, and devices, or the need for continued on-premises security.
With Symantec cloud security, you have visibility and control at every layer of every stack, from core to edge. No exceptions. This holds true for the most complex deployments with the most rigorous requirements.
There are two reasons why Symantec cloud security works as an overarching solution.
One, each of the tools that come with Symantec Integrated Cyber Defense Platform are feature-rich. Their DLP solution, for instance, gives you 360-degree visibility into the safety and compliance of sensitive information, no matter where or how it is stored.
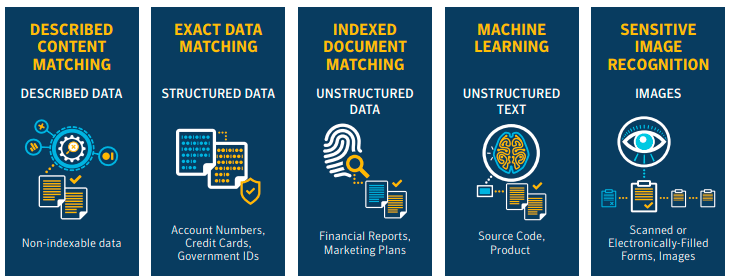
The detection capabilities of Symantec DLP are extremely well-developed, using advanced machine learning, fingerprinting, image recognition and other technologies to accurately classify data. This streamlines the task of locating sensitive information in any location or file format.
All of the tools in Symantec cloud security, like their DLP, are mature products that have been refined over the years. You have a tremendous amount of control, yet the interface remains simple.
Along with the depth of their products, the second reason that Symantec works well for complex deployments is that every layer of your stack is covered. Many of the newer, cloud-native security solutions can help you transition unidirectionally toward a total cloud environment, but cannot help you leverage or upgrade your existing infrastructure.
With Symantec, your “cloud first” model doesn’t have to mean “cloud always.”
They have services and tools that can build out your on-premises resources or safely connect them to other public clouds. You’re not locked in to choosing any one direction with Symantec, no matter how you scale, and you don’t have to split your security operations center among multiple programs.
Symantec Integrated Cyber Defense Exchange (ICDx), which is free for existing customers, is an intuitive software layer that brings all of your Symantec and partner security solutions together in a single console. This gives your teams an actual, real-time view of the whole environment while drastically reducing administrative complexity.
Who should consider Symantec cloud security?
For companies with less complex IT infrastructure requirements, there are other solutions that may work very well. Products from Zscaler, Crowdstrike, and other cloud security companies may be easier to implement than Symantec, though they don’t provide the range of services.
If you are constantly finding vulnerabilities with your existing cyber defenses, having trouble scaling out policy enforcement, or simply tired of trying to fill gaps with yet another tool, Symantec cloud security may be what you need.
It’s an excellent choice for companies that are continuing to invest in their on-premise infrastructure. Like Cisco Cloud Security and IBM Cloud Security, Symantec is happy to let company’s transition to the cloud at their own pace.
Because it integrates with a large number of third-party applications and services, Symantec cloud security is a safe bet for companies with complex multi-cloud deployments. Products like Amazon Cloud Security work well to secure AWS resources, but what if you are using other public clouds, or Microsoft 365 as your productivity suite?
With the deep Symantec cloud security toolkit and the ability to oversee partner solutions with Symantec ICDx, the process of protecting a complex hybrid cloud perimeter comes within reach.

