What is a Cloud Security Gateway?
Cloud security gateway refers to an emerging product category that consolidates several critical security services within a single platform.
The exact services merged depend on the vendor, but all cloud security gateways function as a safeguard for all enterprise traffic, sitting between users and the internet, cloud applications, and company resources. The best cloud security gateways:
- Provide employees with safe, frictionless access to everything they need, wherever they are.
- Give security teams complete ability to monitor traffic, apply policy controls, and respond to threats anywhere in their environment.
In this post, we’ll go through the full range of capabilities expected with cloud security gateways, and review three of the most popular products today.
Why Cloud Security Gateways are Becoming More Popular
Gartner defines cloud security gateways as “security policy enforcement points placed between cloud service consumers and cloud service providers to interject enterprise security policies as the cloud-based resources are accessed.”
These can be deployed on-premises or in the cloud, and gradually replace the enterprise data center as the primary means of authentication, authorization, encryption and so on.
The move from datacenter to cloud security gateways is happening, according to Gartner, because current trends have turned the enterprise network “inside out”. Massive Saas, IaaS, and other cloud-based service adoption has “inverted historical patterns,” leading to a new normal, characterized by:
- More user work performed off of the enterprise network than on the enterprise network
- More workloads running in IaaS than running in the enterprise data center
- More applications consumed via SaaS than consumed from enterprise infrastructure
- More sensitive data located outside of the enterprise data center in cloud services than inside
- More user traffic destined for public cloud services than to the enterprise data center
- More traffic from branch offices heading to public clouds than to the enterprise data center
Whether or not you believe the enterprise data center will be phased out in a few decades, as Gartner contends, a cloud security gateway can help businesses secure digital assets now.
As you peruse your options, you’ll discover that vendors enact these “security policy enforcement points” differently, and don’t always consolidate the same types of policy enforcement.
In other words, no one set of services constitutes a cloud security gateway.
The ambiguity here is a reflection of the simple fact that the cloud expands a company’s IT perimeter in ways that are being redefined each year. Just as next-generation firewalls quickly became a distinguishable product category, cloud security gateways are headed the same direction.
Understanding the variation between the cloud security gateways on the market today will help you find the product with the right suite of capabilities to serve your company.
The Key Features of a Cloud Security Gateway
The key capabilities of cloud security gateways formerly existed as separate products or services, including:
- CASB: A cloud access security broker sits between users and cloud service providers, giving administrators visibility and control over company cloud application use. A CASB can discover and monitor all connected SaaS, PaaS, and IaaS resources, centralizing policy enforcement based on application risk or compliance needs.
- DLP: Data loss prevention is a set of tools and processes that protect sensitive data at-rest, in-transit, in-use, and on endpoints. DLP solutions let you discover, classify, encrypt, mask, and tokenize your most sensitive data to prevent loss and theft.
- RBI: Remote browser isolation uses virtualization to isolate a user’s web browsing activity from their endpoint device and other company resources. This protects users from malicious sites and prevents attacks from spreading.
- SWG: A secure web gateway inspects and filters internet traffic in real time. It enforces policies set by administrators to prevent data leakage and insecure access. Remote employees have a protected connection no matter where they are.
- ZTNA: Zero trust network access is a set of tools and policies that protect all traffic, in and outside the perimeter, by assuming it is hostile. Traffic is continually re-authenticated and reauthorized, across any type of environment.
Defense is streamlined through the merged tools. Implement DLP solutions for users, endpoints, and applications within a single console, such as Forcepoint Cloud Security Gateway:
It’s much easier to maintain consistent, up-to-date policies with cloud security gateway than a patchwork of different tools. You don’t have to worry about what kind of network your employees are trying to connect from, and neither do they.
If an attack does happen, you can trace it back regardless of which environments it moved through. The rich audit trails possible with a cloud security gateway can be integrated with your SIEM, and provide critical information to your security team. In the long run, the increased visibility leads to a better architected perimeter.
Additional threat protection is built into each capability as vendors leverage security intelligence from thousands of other users. New malicious tactics identified in one network quickly result in patches and strategies that are shared across the platform. The best cloud security gateways are continually updated based on the latest threats.
Perhaps the most important feature of a cloud security gateway is that it is purpose-built for the new mission of protecting an ever-expanding perimeter. As a unified tool, each service works closely with the others to offer threat insight and response capabilities that would be impossible with any individual service.
Because many of the features of cloud security gateways already exist, people using AWS, Azure, Google Cloud, and other platforms can potentially use the in-house cloud security solutions instead.
It’s possible to build out a hybrid “cloud security gateway” in AWS, provided your team has the cloud security certifications and experience to get it right.
The best cloud security gateways, on the other hand, are ready out-of-the-box to secure the complicated relationships between home office, data center, and cloud.
Popular Cloud Security Gateway Solutions
- Forcepoint Cloud Security Gateway
- Zscaler Internet Access
- Netskope Cloud Security Platform
It’s a testament to these products that most are partnered with Amazon, Microsoft, Google and other big cloud players. Forcepoint, for example, integrates with Azure Sentinel, one of the marquee Microsoft cloud security products, delivering high-powered investigative and response capabilities.
Likewise, Zscaler has deep integration with AWS, Google Cloud and Azure Security, and NetSkope connects to virtually anything.
In short, all of these products are trusted by the major cloud service providers and cybersecurity vendors. They are highly extensible, integrating with other leading technologies to protect edge locations, IoT, and unmanaged devices.
As work from home and cloud collaboration become the norm, companies can use these widely-vetted cloud security gateways to consolidate the oversight of the emerging IT environment.
Forcepoint Cloud Security Gateway
Cloud Security Gateway from Forcepoint is not a bundle of related products, rather its a converged cloud security service that unifies several key cybersecurity capabilities.
Convergence, for Forcepoint, “means merging web security, network security, and cloud application security, delivered in a single, easy-to-consume service.”
Essentially, it combines the functions that used to be split between the company’s DLP, CASB, SWG, and RBI to create a multidimensional gateway that stands between users and the cloud resources they use.
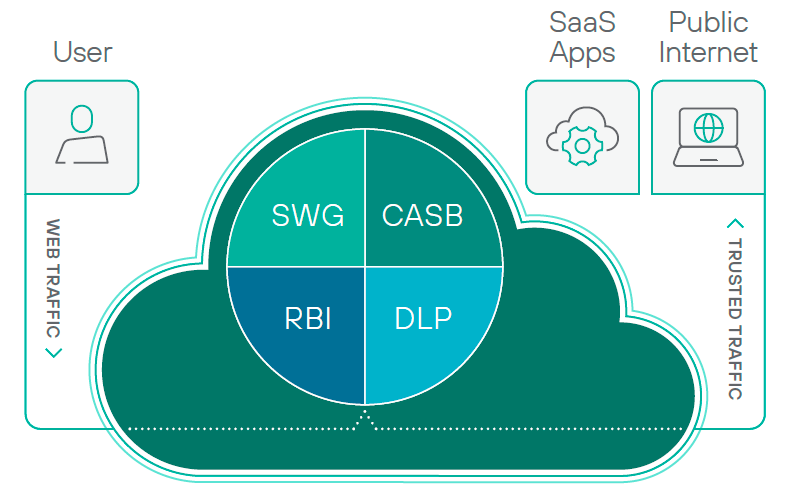
By bringing these functions under one roof, Forcepoint has created something that helps IT and users.
Security teams have visibility into many of the threats that plague users at home and on-the-go: malicious applications, shadow IT, data loss, and so on. They can monitor and resolve threats from all of these vectors within the Cloud Security Gateway console.
For users, they know that their data is safe. Their work data is better protected because they are prohibited from transferring it inappropriately or unsafely. Plus, they’re blocked from accidentally sending their personal banking traffic in the other direction. They have true security in the home office.
Zscaler Internet Access
Zscaler Internet Access (ZIA) is a truly cloud-native option that has become incredibly popular with companies who want to leave 1990s hardware-driven network defense in the past.
Zscaler offers the full security stack as a service. This means an end to appliances and the entire hub-and-spoke model that required all traffic to be backhauled through the enterprise data center. With Zscaler, direct-to-cloud access is always protected wherever users go.

All traffic is routed through Zscaler cloud, where it is filtered and policies are automatically enforced. Zscaler Internet Access is easy to deploy, delivering a unified SWG, CASB, DLP, intrusion prevention system (IPS), and RBI, though the company calls it Cloud Browser Isolation.
The services you get depend on your ZIA subscription, or they can be purchased à la carte. Either way, all of the capabilities function together to provide granular policy control and continuous security.
Premium capabilities include zero-day threat protection via cloud sandboxing and full inline inspection of all SSL traffic.
Netskope Security Cloud Platform
Netskope offers a full range of cloud security products that are built to scale. Netskope Cloud Security Platform unifies a number of these best-in-class options to provide a cloud security gateway flexible enough to accommodate any type of deployment.
From a single UI, you can manage policies across web, SaaS, IaaS, on-premises. Netskope Cloud Security Platform makes it easy to enforce access control and data protection consistently for all users and devices.
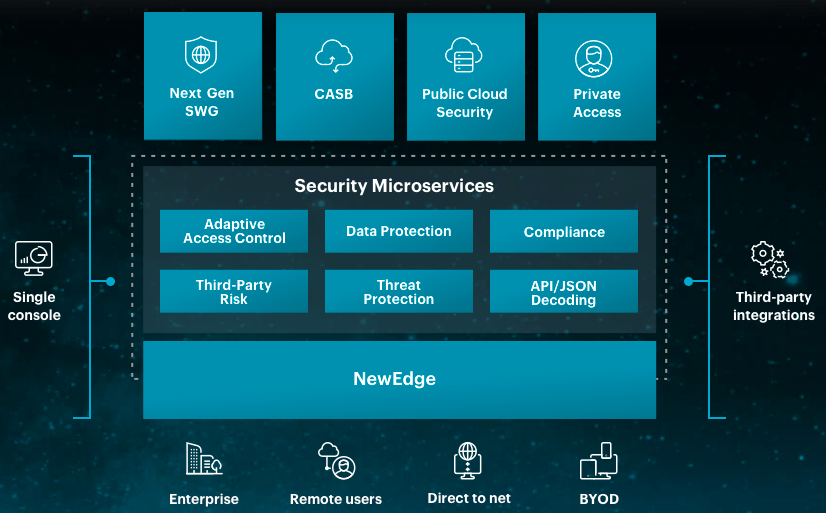
The core tools that comprise the platform are Netskope’s Next-Generation SWG, CASB, and Private Access (ZTNA), Public Cloud Security (ATP & DLP). Together, these tools enable the safe and seamless remote access to company resources.
For security teams , Netskope Cloud Security Platform is more than the sum of its parts.
Real-time analytics from across their entire environment help teams visualize problems. The integrated advanced threat protection can be applied to data at rest, as well as web and cloud traffic. When problems are discovered, configurations for microservices can quickly be shared enterprise wide.
Beyond the core tools comprise the platform, which can be enhanced with other Netskope services and a host of third-party integrations. This includes Microsoft 365, AWS, Azure, and other cloud security companies like CrowdStrike for EDR
Netskope will ingest rich information about user activities and data use in these integrated services, giving you much better insight and control over SaaS.
One thing that sets Netskope apart is that ZTNA comes as part of its cloud security gateway. With Forcepoint and Zscaler, you have to purchase separate Private Access services.
More trusted cloud security gateways
Other leaders in the cloud security gateway market include:
Umbrella, from Cisco Cloud Security is an excellent cloud security gateway, though it’s not marketed as such. Yet.
As people continue to find success with cloud security gateways, expect to see more companies put forward a dedicated offering in this product category.

