The Complete Guide to Amazon Cloud Security
More companies are moving to the cloud with Amazon than any other vendor. Security is a big part of why.
Amazon Web Services (AWS) has a full set of tools built to help people conduct business safely across the most complex IT environments. As with any cloud service, security is a shared responsibility between provider and customer. Amazon has worked hard to make sure that this task is as easy as possible.
In this post, we’ll go through the arsenal of products that make up Amazon Cloud Security, and how they work together to optimize an organization’s security posture.
To close, we’ll look at what makes Amazon Cloud Security different and who should consider it as an option.
What is Amazon Cloud Security?
Amazon takes care of the underlying infrastructure that allows for cloud computing and communications, ensuring that company’s can build whatever they want on top of AWS without having to fear an attack from below.
This includes state-of-the-art Amazon data centers, whose traffic is monitored 24/7/365 by thousands of cybersecurity experts. Much of the malicious activity on the internet is filtered out automatically by Amazon and their partner cloud security companies.
To put it in plain language, the AWS infrastructure is incredibly secure. Ask the Central Intelligence Agency (CIA), who have been using AWS for years now.
Most of the successful attacks on AWS and other cloud service providers are the result of a customer mistake. It’s not that AWS is getting hacked. Rather, an AWS customer accidently leaves an open door or an AWS user account gets compromised.
This happens because Amazon doesn’t police what you build in their cloud. If someone accidentally makes private information public, for example, that’s on the customer.
In exchange for the privacy and control afforded by AWS, the customer assumes a shared responsibility for security:
- Amazon is responsible for the security of the cloud. They provide a firm platform to build on.
- Customers are responsible for security in the cloud. Companies need to make sure that what they build is secure, properly configured, and only accessible by the right people.
AWS has been around longer than any other provider. Over the years, they have refined a comprehensive set of security best practices and developed an unrivaled suite of Amazon Cloud Security tools.
Amazon Cloud Security Tools

AWS Security Hub is the seat of operations for Amazon Cloud Security. It aggregates, analyzes, prioritizes information from across your other AWS and third-party cloud resources.
In a single dashboard, you have visibility and over your entire cloud perimeter and the ability to drill down into any event. Security Hub combs through the data gathered by all of your other tools and provides alerts about suspicious user behavior, misconfigured devices, unpatched vulnerabilities, and so on.
You can run automated security checks to make sure your data, workloads, and other assets are compliant with industry standards, such as the Center for Internet Security (CIS) Payment Card Industry Data Security Standard (PCI-DSS).
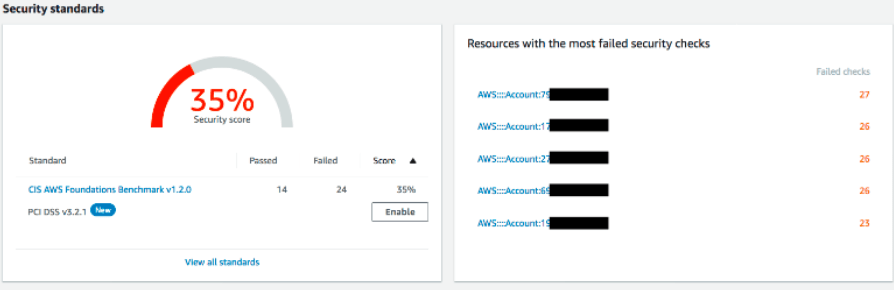
Security Hub generates a report with a clear overall score, flagging problematic assets for further inspection. The whole process is several clicks, and you can set security checks to run continuously.
Management is streamlined for many tasks in Security Hub, whether you are looking to track user behavior, configure firewalls, or investigate an ongoing attack. Security Hub can be integrated with your SIEM or SOAR so that critical events get the attention they need automatically.
AWS Security Hub ties into Amazon Cloud Security tools to address all key areas that customers are responsible for:
- Identity access and management
- Infrastructure protection
- Data protection
- Detection
- Incident Response
Identity access and management
![]()
AWS Identity & Access Management (IAM) lets you create roles and permissions that limit access to your cloud resources to the right people. It’s a fine-grained, IAM solution that lets you assign users individual and temporary security credentials to minimize the threat of compromised accounts.
You can integrate AWS IAM with your existing identity management solution (as long as it supports SAML 2.0), and enable MFA for privileged users.
AWS Single Sign-On (SSO) configures and manages all the necessary permissions for users across all their AWS accounts. It makes users’ lives easier—they can login once to access all of their resources.
AWS SSO also saves time for IT administrators. They can assign cross-organization permissions for specific job functions that meet your security and compliance needs.
Combined with built-in integrations to Salesforce, Microsoft 365, and other popular business apps, AWS SSO can eliminate gaps in security while improving employee ease-of-access.

Amazon Cognito is a secure directory that can scale out to millions of users. You can quickly add sign-up, sign-in, and access control to web and mobile apps. You can manage access for different users, and customize the frontend UI to ensure that the customer’s experience is aligned with your expectations.
Cognito supports the use of social and enterprise identity federation, so users can log in with Google, Facebook, or Amazon credentials.
![]()
AWS Resource Access Manager (RAM) simplifies the process of making sure that users have secure access to the assets they need across the cloud. Instead of having to create duplicate accounts, administrators can select a group of resources and associate it with identities and groups from AWS IAM.

AWS Organizations simplifies governance across an organization. You can automate account creation and management, share resources across AWS accounts, and create permission guardrails that prohibit users from jeopardizing network integrity.
By integrating with other tools like CloudTrail and Security Hub, AWS Organizations makes it easier to implement and enforce security, audit, and compliance policies.
Infrastructure protection

AWS Shield is a managed, always-on distributed denial of service (DDoS) protection service. AWS Shield Standard comes with all AWS accounts and defends against the most common network and transport layer attacks.
AWS Shield Advanced provides additional security for applications cloud development. The add-on feature integrates with AWS WAF to stave off large and sophisticated DDoS attacks.
![]()
AWS WAF is a web application firewall that is easy to deploy and maintain. It gives you near real-time visibility into web traffic and the ability to configure rules quickly. Inspect any aspect of web traffic according to your security needs or using managed rules that protect applications and APIs from common attacks.

AWS Firewall Manager centralizes the configuration and management of all of your firewalls. As new resources are added, AWS Firewall Manager will discover them and enforce the security policies you have set. When new threats are surfaced in AWS Security Hub, you can use Firewall Manager to quickly deploy updated protections across your network.
Data protection
![]()
Amazon Macie is a fully managed service that discovers and protects sensitive data across your AWS accounts. The automated service provides a complete inventory of all Amazon S3 buckets, applies machine learning and pattern matching to identify sensitive data from any bucket you select.
You can enable the service in a few clicks, and there is no custom-configuration required to scan for sensitive data types. Amazon Macie allows companies to scale operations without losing track of sensitive data, which is a massive security risk.
![]()
AWS Key Management Service (KMS) simplifies the oversight of all encryption keys. Along with centralized key management (key creation, importation, rotation, and deletion), AWS KMS ties into your other services to provide logs for regulatory and compliance needs.
![]()
AWS CloudHSM helps you create and manage the hardware storage modules (HSMs). HSMs are the hardware devices that generate and store keys. AWS CloudHSM handles many of the administrative tasks associated with maintaining an HSM, automatically patching software and provisioning hardware.

AWS Certificate Manager centralizes the oversight and automates the maintenance of all the Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates you use to secure network communications.
Many of the time-consuming steps associated with provisioning and deploying certificates are eliminated by AWS Certificate Manager, helping companies keep all traffic encrypted and meet compliance requirements.
![]()
AWS Secrets Manager protects the credentials you use for databases and other services. Instead of hardcoding your credentials in plaintext, secrets are retrieved with a call to Secrets Managers APIs. Within the console, you can oversee access to secrets using permissions and monitor the rotation of secrets across all cloud services.
Detection
AWS Security Hub is the primary detection tool for Amazon Cloud Security, but it relies on integrations with the following products to get the data it needs.

Amazon GuardDuty is a managed threat detection service that scans your entire cloud environment for suspicious user behavior, data access patterns, cryptojacking, and other advanced attacks. GuardDuty works with AWS Organizations and Amazon CloudWatch to integrate existing enterprise infrastructure and keep it secure.
![]()
Amazon Inspector is an automated security assessment service that helps organizations identify vulnerabilities in applications before they are deployed, and while they are running. With Inspector, developers can iterate quickly, securely, and work vulnerability assessments into the DevOps process.

AWS Config continuously monitors and records configuration changes of AWS resources. Config triggers alerts when relationships between resources deviate from the policies you have set, and lets you assess the impact of potential changes before making adjustments.
![]()
AWS CloudTrail records and stores log events and API calls, giving visibility into user and resource activity. In addition to the comprehensive history, which is critical for governance, compliance, and auditing, AWS CloudTrail can be automated to respond to common security vulnerabilities.
![]()
AWS IoT Device Defender is a managed service that continuously monitors IoT configurations to ensure they are operating according to best practices. IoT Device Defender helps you detect and respond to threats from this emerging attack vector.
Incident Response
![]()
Amazon Detective helps IT security teams respond to threats by aggregating key information from across your cloud environment to present a unified view of the incident. They can see user and resource interactions over time, with context, for quick investigation of the root cause.
Amazon Detective provides incident visualization without the need to configure queries or algorithms.
![]()
CloudEndure Disaster Recovery continuously replicates all your applications and databases to ensure business continuity. It is simple to implement, and can be used as a disaster recovery site for third-party public cloud resources.
What differentiates Amazon from other cloud security solutions?
The breadth of tools available with Amazon Cloud Security is the most comprehensive of any cloud service provider. This allows you to keep a larger share of your toolkit from a single provider, which decreases vulnerabilities, simplifies management, and speeds deployment of new updates.
In addition to the core Amazon Cloud Security portfolio, there are also a wide variety of services, add-ons, and ready-to-go software stacks available in the AWS Marketplace. All of these products have been tested, vetted, and found success. Some of them are free.
Those that use AWS benefit from the company’s size and the scope of its cloud operations. Because they control more than 30% of the cloud compute market, they see an outsized share of attacks. The threat intelligence that undergirds Amazon Cloud Security products comes from the careful analysis and protection of this massive attack surface.
Amazon has put a tremendous amount of thought and effort into giving customers information they need to enact a complete cloud security strategy. By following the AWS Well-Architected Framework, customers can employ Amazon Cloud Security tools to protect every layer of their entire network, from core to edge.
Who should consider Amazon Cloud Security?
If you are using AWS, the Amazon Cloud Security suite is wonderful, and basically unavoidable. Because they are a titan in the field, they have solutions for virtually every cloud security issue available already.
In the case of emerging security concerns, they have a reputation for developing features and fixes quickly. AWS may not be the first to market with a commercially available solution, but they won’t be far behind.
If you are using another cloud service provider, Amazon Cloud Security tools can be configured to work across multi-cloud deployments. They also work for hybrid deployments, though IBM Cloud Security and Oracle Cloud Security carry more appliances and solutions for the on-premises stack.
There is no one type of Amazon cloud customer, and the quality of their services make them a strong option for almost any type of business: small, midmarket, or enterprise.
The cost of AWS and Amazon Cloud Security depend on the services you use. Get in touch with sales to get an accurate price, and rest assured that you’ll have the capabilities you need to harden your entire perimeter.

