How to Protect Your Online Privacy
Online privacy is top of mind for a lot of people after they hear about a friend losing financial information or suffering a password hack. Simply worrying about or thinking about the consequences isn’t quite enough, though.
Taking a few steps before the next time you begin using your favorite social media app or begin web browsing can give you a much better chance of protecting your online privacy.
1. Install Antivirus Software
The first step you should take is installing a good antivirus software package. Antivirus software protects your computer from malicious software that you may inadvertently download while using the web. Viruses can:
- Create popup ads
- Track and steal your personal information
- Delete software and files
- Reformat the hard drive
- Lock up the hard drive, holding the data for ransom
- Disrupt system performance
Although many viruses will destroy data or affect the way your computer runs, some viruses exist specifically to steal your personal information and monitor your online activity.
You can encounter viruses during many day-to-day activities you perform online. Chances are high that you won’t know when you inadvertently download a virus. It’ll just happen. Without antivirus software constantly monitoring for viruses, you may not know that the virus is running in the background and stealing your information.
Without antivirus monitoring, by the time you realize the presence of the virus, your information is long gone.
How to Use Antivirus Software
Quite a few pay versions of antivirus software exist, although there are some free versions that are strong performers too. Regardless of which software you select, the important thing is to install the antivirus software and keep it up to date.
Windows 10 or Windows 11 users will probably want to simply deploy the built-in security and antivirus measures included with the operating system. Windows Defender Antivirus automatically runs as part of the Windows 10/11 operating system, unless you turn it off.
If you are running another antivirus software package, you have the option of running Windows Defender Antivirus as a passive supplement to the third-party package.
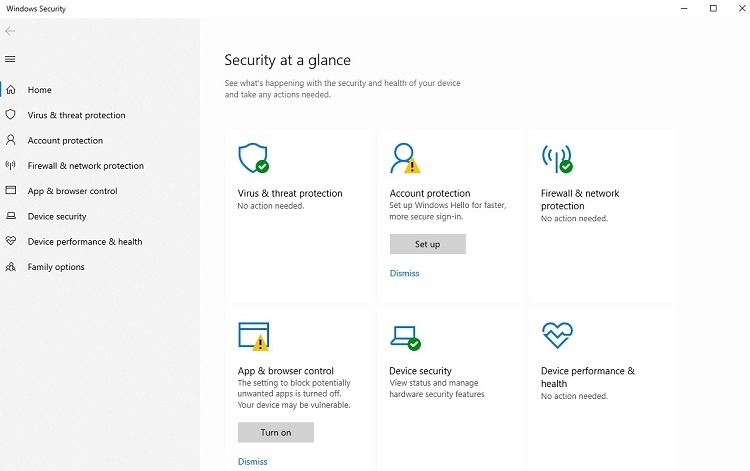
To determine the status of Windows Defender Antivirus on your computer, click the Start button and the Settings icon (marked with a gear). Click on Update & Security.
Click on Windows Security, followed by Open Windows Security. You can see the status of the computer’s antivirus protection in this window. Click on the Virus & Threat Protection icon to see more information about the status. You may be able to click on Microsoft Defender Antivirus options to make changes to the antivirus settings.
If you prefer to go with either a free or paid version of a third-party antivirus software package, some of the best options include:
- AVG Antivirus
- Bitdefender Antivirus
- Kaspersky Antivirus
- Malwarebytes Antivirus
- McAfee Total Protection
- Norton Antivirus Plus
- Trend Micro Antivirus
Mac users typically count on the antivirus capabilities built into the operating system. If you want a third-party software package, however, Malwarebytes has a strong Mac version of its antivirus software.
2. Hide Your Browsing History and Actions
When websites and other entities are tracking your browsing history and your actions online, your privacy disappears quickly. As these entities track everything you do over dozens and hundreds of online sessions and website visits, the growing amount of data reveals a significant amount of information about you and your habits.
Eventually, all of this information leads to targeted advertising and other actions that you may consider a violation of your privacy.
You can attempt to block both the collection of data about your online habits and the targeted ads through a few different steps. Use of a virtual private network, an incognito or private browser window, or a browser extension that blocks malware from collecting your internet usage data all can help protect your online privacy.
Use a Virtual Private Network
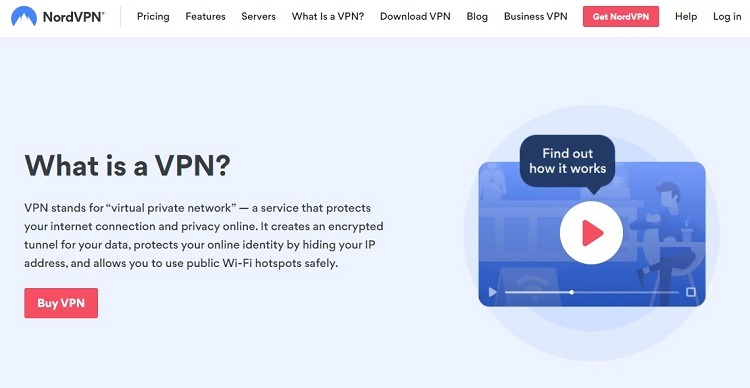
A virtual private network, or VPN, is software that allows you to use the internet anonymously. The use of a VPN is a vital component for those who want to take significant steps to protect their online privacy. The VPN delivers a number of benefits for you, including:
- Encrypting your traffic on the internet
- Spoofing the physical location of your device
- Hiding your IP address
- Blocking the tracking of your browsing and social media activity
If you regularly use a public WiFi access point, a hacker in the area may be able to monitor your internet traffic by running some hacking software at the hotspot. A VPN will prevent this from happening by encrypting your traffic.
Your internet provider could collect your browsing and usage data and sell it to advertisers. Running a VPN puts an end to this unscrupulous practice from an internet provider.
The best VPN tools carry a subscription price of around $5 to $10 per month, depending on the model you choose.
Use Anonymity in Your Browser
An incognito or private browsing window is a quick way to hide your identity from tracking software temporarily. It’s not as secure as a VPN, but it is useful for occasional deployment.
To open an incognito window in Google Chrome, click the three dots in the upper right corner of the Chrome window. Then click on New Incognito Window.
In Microsoft Edge, click the three dots in the upper right corner. Then click New InPrivate Window.
Some people will want to make use of a browser that operates in a private or incognito mode all of the time. For example, the Tor web browser hides your IP address, clears the browser’s cookies each time you close it, and blocks tracking software.
Use a Browser Extension
Another option for protecting your online privacy involves installing an extension for your web browser that blocks ads and tracking. An extension like Privacy Badger or Ghostery will provide ad-blocking and tracker blocking.
However, if you are using Google Chrome, some of these ad-blocking extensions will not work.
3. Use a Password Manager
Weak passwords are a serious problem for online privacy and account security. Once a hacker gains access to one of your accounts by stealing a password, you’re in trouble. And if you use the same password for all of your accounts, you could lose the vast majority of your personal information before you even realize what is happening.
Account and password hacking can significantly expose your personal information, jeopardizing your online privacy.
The best option to protect your account information, including the username and password, is to use password manager software. A password manager will store all of your account names and passwords in a highly secure location. The password manager software will encrypt your usernames and passwords, so even the software maker is unable to gain access to your data. Only you can access the information.
You can gain access to all of your information by using a single username and password in the password manager software. Trying to remember a few dozen passwords is far more difficult than remembering a single password.
With the password manager, you can make the passwords extremely complex, using a combination of uppercase letters, numbers, symbols, and lowercase letters. The password manager will even enter the username and password for you when you visit a website, automating the process.
How to Install a Password Manager
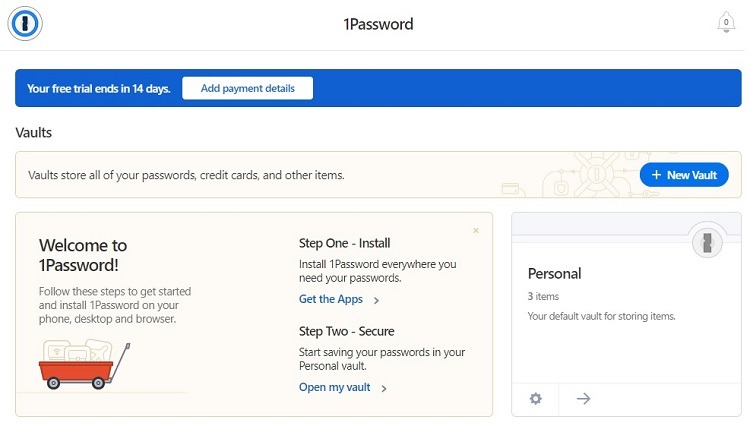
Our recommended password manager is 1Password, and we’ll use this software as an example for installing a password manager.
To install 1Password, visit the home page. Click on the Try 1Password Free button in the upper right corner of the home page to sign up for a free trial period. If you decide to continue using 1Password, you can migrate to a subscription version later without having to re-enter your information.
Select the pricing plan you believe you will want to use if you decide to keep the service. Enter your name and email address before clicking Create Account.
You’ll then need to enter a password to use with 1Password before entering your credit card information. Or, if you scroll down the page, you can choose to skip adding your credit card information for now. (You will need to add a credit card later if you decide to keep the subscription.)
Because the 1Password software encrypts all of your usernames and passwords, customer service people at 1Password cannot retrieve your stored passwords. If you run into problems, 1Password stores your recovery data in an Emergency Kit PDF document that is unique to your account. You’ll need to download this document before you can begin using 1Password.
You then can begin using 1Password. Click Get the Apps to download the 1Password app for all of your computers and mobile devices. Click Open My Vault to begin storing your passwords and other account data.
Individual users can subscribe to 1Password for about $3 to $5 per month. Business users have a few different pricing options, including $20 per month for up to 10 team members. Both businesses and individuals can try 1Password during a free trial period.
For those who would prefer a free password manager option, both Google Chrome and Microsoft Edge have free password management features built into the browsers. They aren’t quite as secure as a third-party package that specializes in password management, like 1Password, however.
4. Set Up Two-Factor Authentication
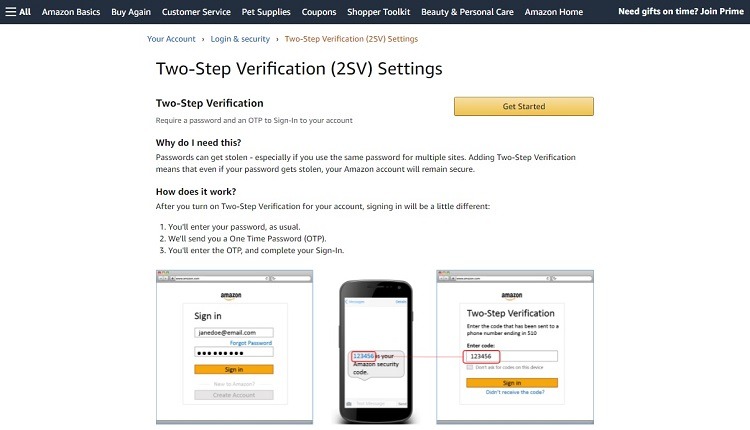
One of the best and easiest ways to protect online accounts and privacy is by setting up two-factor authentication (or 2FA). This is an efficient means of protecting your personal data stored in accounts.
A hacker who steals your username and password cannot gain access to the account without the second factor when you make use of 2FA. The second factor may involve the website sending you a text message or an email message containing a unique code after you enter your username and password.
The idea behind 2FA is that even if the hacker gains access to the first layer of security (your username and password), the hacker would not also have access to the second layer of security (your smartphone or email account). Without access to these items, the hacker would not know the unique code, meaning your account is safe.
How to Use 2FA
Companies like Amazon, Apple, Facebook, Google, Slack, Twitter, and many more offer 2FA. Although the number of online accounts offering 2FA is growing, not every account may offer this level of security.
If you are wondering whether you can set up 2FA for a particular account, find the Security settings for the account. If you see a link to two-factor authentication or two-step login, you should be able to begin using this option.
Oftentimes, setting up 2FA is as easy as turning it on with a slider button. You then would select the preferred method for receiving the code.
Once 2FA is ready to use, you’ll first enter your user name and password at the website. The site will either send you the code immediately, or it will give you a popup window where you can ask to have the code sent.
With the code in hand, enter it at the website, and you then can access your account. Most of these codes have a limited time period during which they’re valid, so you will need to enter the code within a few minutes of receiving it.
Common Problems When Protecting Your Online Privacy

Although you may feel like you are doing everything possible to protect your online privacy, a few things can slip through the cracks. Frequently, we will give up some of our privacy regarding our data because it makes apps and websites easier to use. But what seems like a harmless tradeoff now could place privacy and data at risk well into the future.
Here are some of the most common issues people struggle with when trying to protect their online privacy.
Problem 1: Allowing Cookies
When a website alerts you that it uses cookies and asks you to click the Accept button, you probably do it most of the time without thinking twice. However, these cookies may track your browsing history and collect the data for use with advertisers.
Legitimate cookies by themselves don’t track your highly sensitive personal data, such as financial account information. And cookies do have a benefit, as they can help you use a website that you visit often more efficiently by remembering some of your favorite settings.
However, having your personal browsing data available to advertisers can result in being the target of unwanted advertising campaigns. Certain campaigns may generate quite a bit of spam email, costing you time to have to deal with the extra messages. If a certain spam message sneaks through and if you click on something you shouldn’t, you could end up the victim of a phishing scam.
Problem 2: Allowing Location Tracking
When using apps on your smartphone or tablet, many apps will attempt to track your location. The apps may ask you at the time of installation whether they can track your location, and you may give them permission without thinking much about it.
Through the GPS chip inside the smartphone, the app knows your location at all times, which advertisers can use.
Certainly, some apps are almost worthless without being able to use the GPS chip to know where you are. The best solution is to only give those apps access to your location when you are actively using the apps.
If you are really looking to protect your online privacy, keep your location private from apps unless they are running.
Problem 3: Exposing Personal Information Without Thinking About It
People enjoy sharing information about their lives and activities on social media. After all, this is the point of social media. It’s supposed to be fun.
However, when you are using a website or app primarily for fun, you may let your guard down a little bit versus when you are online shopping, where you know you will be sharing financial information.
When you post your birthdate or a picture of your new driver’s license photo on Facebook, it may seem harmless. But you are exposing personal information that could affect your privacy if it falls into the wrong person’s hands.
Before you share something on social media, think twice about whether you really want this information exposed.

