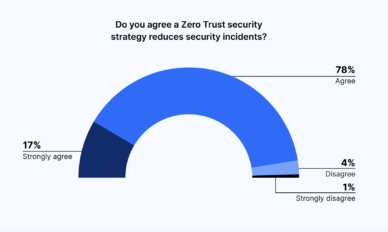
Are Personal Email Accounts Accessing Your Company Data?
Personal account access is one of the biggest data exfiltration risks a company faces—and one of the most hidden. The current state of personal account access is precarious and affects organizations of all sizes. Every person who interacts with a company using cloud collaboration tools like Google Workspace and Microsoft OneDrive could have added their… (more) Are Personal Email Accounts Accessing Your Company Data?