NIST CSF Categories: The Ultimate Guide
To better understand the NIST cybersecurity framework, you need to get familiar with the different CSF categories. This guide explains everything you need to know about CSF categories, how they work, and how to get started using them.
What Are CSF Categories Anyway?
The National Institute of Standards and Technology (NIST) is a US government agency that creates non-regulatory standards to promote best practices, standards, and guidelines for cybersecurity management.
The NIST cybersecurity framework is segmented into three different components—the framework core, implementation tiers, and profiles.
The framework core contains sets of desired cybersecurity activities and outcomes. These are all organized into functions, categories, and subcategories.
There are 23 CSF categories split between five different functions. Those functions are:
- Identify
- Protect
- Detect
- Respond
- Recover
Here’s a visual representation of these functions and categories, taken directly from the NIST.gov website:
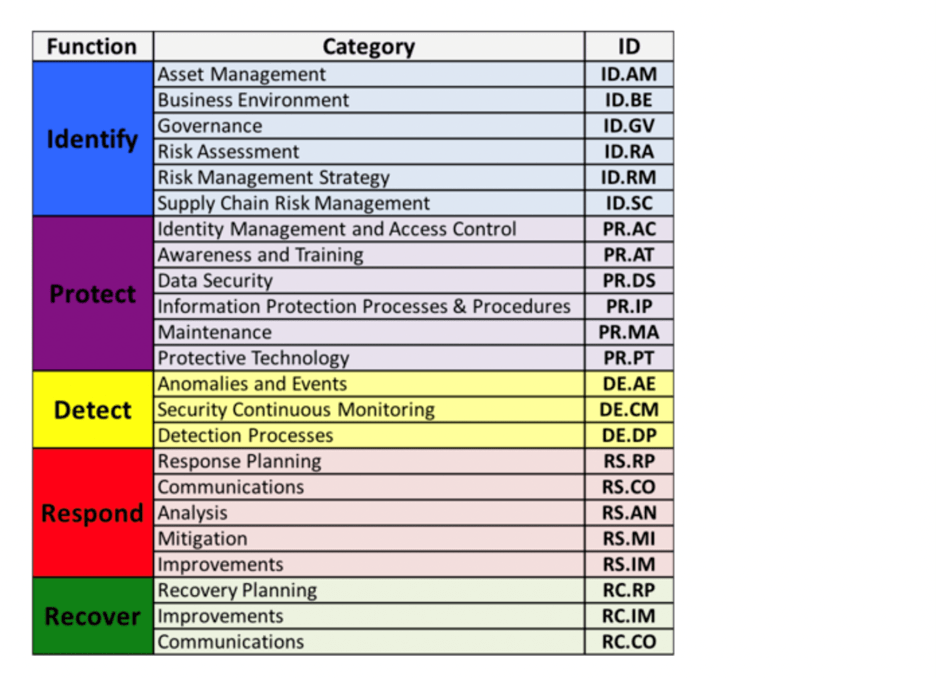
How CSF Categories Work
Functions are the highest-level part of the NIST framework. They’re designed to foster communication between stakeholders and technical users within an organization to improve, control, and manage cybersecurity functions.
The CSF framework does not explicitly dictate risk management strategies for cybersecurity. But the categories and subcategories provide organizations with enough information to implement cybersecurity protocols based on unique needs.
CSF categories are intended to cover all cybersecurity objectives for an organization. They are intentionally vague, without specific details, so each organization can apply the categories as needed.
The 23 categories cover topics that are focused on business outcomes across physical environments, cyber environments, and personnel.
There are 108 subcategories in the NIST cybersecurity framework. Subcategories are the third level of the NIST core framework—coming after functions and categories.
Each of the 23 categories has an ID. The subcategories have corresponding IDs with outcome-driven statements that are used to create or improve cybersecurity initiatives within the organization.
For example, “Business Environment” is a category within the “Identify” function. Its ID is ID.BE, and there are five subcategories that correspond as follows:
- ID.BE-1 — The organization’s role in the supply chain is identified and communicated.
- ID.BE-2 — The organization’s place in critical infrastructure and its industry sector is identified and communicated.
- ID.BE-3 — Priorities for the organization’s mission, objectives, and activities are established and communicated.
- ID.BE-4 — Dependencies and critical functions for delivery of critical services are established.
- IDE.B5 — Resilience requirements to support the delivery of critical services are established for all operating states.
Again, the CSF categories and subcategories are not mandates or prescriptive. They do not explain how an organization can achieve the desired outcomes. It’s up to the organization to figure out how these outcomes will be reached based on customized needs.
An organization may choose to use some, none, or all of the information resources within each subcategory to reach the desired outcomes.
Let’s take a closer look at 23 cybersecurity framework categories within the five core functions identified by the NIST. These real examples and explanations will help you better understand how this works:
Identify
The identify function encompasses risks to critical infrastructure, assets, data, people, and information systems. Organizations can use this function to develop proper organizational understandings across six categories:
- Asset Management (ID.AM) — Create an inventory to identify and manage all assets within the organization. This includes employees, stakeholders, and contractors. You can use this to assess the risk associated with things like BYOD.
- Business Environment (ID.BE) — Identify the organization’s mission and stakeholders. Understand why the company exists and how the core business objects get accomplished. This helps you understand where cybersecurity risks exist and also helps assess the total risk profile of the business environment.
- Governance (ID.GV) — Monitor and manage your organization by establishing a formal set of policies, processes, and procedures. Formal governance helps with operations, regulatory compliance, and highlights potential risks with communication channels.
- Risk Assessment (ID.RA) — Assess all risks in the organization, including risk management associated with technology, processes, and people. Break this down into each individual asset.
- Risk Management Strategy (ID.RM) — Determine how risk-averse your organization is. Assess how much risk you’re willing to tolerate, which will ultimately help you with operational risk remediation support.
- Supply Chain Risk Management (ID.SC) — Identify and assess third-party vendors, contracts, and other processes in your supply chain.
The identification stage is crucial as it sets the foundation for each of the remaining functions established by the NIST.
Protect
The protect function is designed to support the delivery of crucial services. It also established secure engineering of total information systems and SDLC (systems development lifecycle).
There are six categories within the protection function:
- Identity Management and Access Control (PR.AC) — This category helps you establish who has access to what assets and systems. Figure out why each person has access to specific things and what those people are doing with those assets. Identity management and access control help companies ensure that they have proper authorization for data and applications, typically supported through initiatives like multi-factor authorization, SSO, just-in-time access controls, and password policies.
- Awareness and Training (PR.AT) — Determine the effectiveness of user training for cybersecurity. This ensures your staff understands how to identify things like spoofing or phishing attacks. Determine how you’re going to effectively train your staff to make them aware of different cybersecurity risks.
- Data Security (PR.DS) — The data security category is segmented by integrity, availability, and confidentiality. Data should be encrypted when it’s at rest and in transit. You can protect data using rights management policies to verify the user identity before access gets granted to recipients.
- Information Protection Processes and Procedures (PR.IP) — Your processes and procedures should clearly identify roles, responsibilities, and coordination between different entities within the organization.
- Maintenance (PR.MA) — The maintenance subcategories all require constant updates to ensure the operations continue to run smoothly. Maintenance is key for continuous effectiveness when you’re protecting an organization from cyber risks.
- Protective Technology (PR.PT) — What technology, platforms, and software are you using to protect your people, assets, and systems? The answers are defined in this category.
The primary goal of the protection function is to reduce the impact of a potential cyber event. These categories ensure that business objectives and success can continue running smoothly.
Detect
As the name implies, this function helps detect cybersecurity events. There are three categories within the detect function:
- Anomalies and Events (DE.AE) — Any anomaly must be promptly identified so the potential impacts can be understood immediately.
- Security Continuous Monitoring (DE.CM) — All assets and systems must be continuously monitored. This will help identify events quickly and ensure proactive initiatives are being applied properly.
- Detection Processes (DE.DP) — There should be specific ways to detect and track events through functions like detection logs and event alerts. These should be set up to adapt and evolve as the threat landscape changes over time.
Fast detection is key to appropriate responses, which brings us to the next function.
Respond
The response function ensures that organizations take the appropriate actions for different cybersecurity events once they’ve been detected.
- Response Planning (RS.RP) — Establish a set of processes and procedures for different types of security events. This ensures that everyone knows exactly what to do and they follow the appropriate protocols after detection.
- Communications (RS.CO) — Define how everyone should communicate the response actions with team members, management, internal stakeholders, and external stakeholders.
- Analysis (RS.AN) — Run thorough tests on a regular basis to ensure that all of the response actions and recovery plans are working the way they should be.
- Mitigation (RS.MI) — Fast mitigation actions are crucial to stopping an event from spreading before it’s resolved. For example, if certain machines, assets, or user categories have been breached, how will you lock down the rest of your systems to mitigate the threats from advancing?
- Improvements (RS.IM) — No response plan is perfect. The plans should be evaluated on a regular basis to look for weaknesses and areas that need improvement.
All of these categories will help an organization respond appropriately if a cyber threat or event is detected.
Recover
The recovery function covers the plans and processes designed to restore impacted services and capabilities back to normal.
- Recovery Planning (RC.RP) — What plans and steps do you have in place to restore assets and information systems that have been impacted by a cyber threat, incident, or event?
- Improvements (RC.IM) — Always look at your recovery plans for improvement. This can help you restore everything faster or ensure that more information can be recovered without a loss.
- Communications (RC.CO) — Well-defined communication procedures and steps can ensure a swift and smooth recovery process.
Recovery categories lay the groundwork to ensure your organization stays resilient and functional after an incident.
How to Get Started With CSF Categories
With 23 categories and 108 subcategories to understand, getting started with the cybersecurity framework categories might seem intimidating or overwhelming. But this is much easier to implement when you have a proven blueprint to follow.
The steps below will help you get started with CSF categories through actionable tips and quick wins. Then you’ll be able to build momentum and scale your initiatives from here.
Step 1 — Understand the Framework Implementation Tiers
There are four CSF implementation tiers defined by the NIST. Each tier describes the degree to which an organization’s practices and policies exhibit the traits within the framework.
- Tier 1 — Partial
- Tier 2 — Risk-Informed
- Tier 3 — Repeatable
- Tier 4 — Adaptive
Anything on the first tier means that you have limited awareness or informal practices for the function. Nothing has been formalized from a risk management perspective, and everything is managed in a way that’s reactive or ad hoc. There is limited awareness of risks, and the organization does not communicate with other entities to understand the broader threats within the cyber landscape.
The second tier means that there is some high-level awareness within the organization. Management might have some practices in place for risk management, but it’s not well-managed or adopted organization-wide. There might be some collaboration with external sources, but it’s rarely used.
Formal policies are well-defined and implemented at the third tier. There is a formal approval and documented policy for risk management, and there is effective communication organization-wide. The organization has a solid understanding of where it stands against threats in the overall landscape.
The fourth tier is the highest level of implementation. Security is part of the organization’s culture at all levels, and there is active information sharing organization-wide. Cybersecurity practices are implemented, managed, and controlled as part of daily business operations.
Step 2 — Establish Your Framework Profiles
The NIST uses framework profiles as a way to help organizations define things like organizational requirements, risk appetite, and objectives for the categories within the CSF framework core.
Establishing framework profiles can help an organization improve its position for cybersecurity initiatives.
Start with your current framework profile. Look at each function and category and give yourself a rating.
You can break the categories down even further and map out the requirements and mission objectives for each of the 108 subcategories as well.
Then you can create a target profile that explains where you want these to be. Identify gaps between your current framework profile and target framework profile to see what needs to be done in order to reach your desired outcomes.
Step 3 — Prioritize Initiatives
Once you’ve defined gaps in your CSF categories, you need to prioritize them. All 108 subcategories are likely not going to be ultra-important for your particular organization.
So it’s your job to determine which ones are the most important based on your risk level or the gap significance.
Defining the priority using identifiers like high priority, moderate priority, and low priority is usually appropriate. You can also use the gap analysis to allocate budget resources to different initiatives. Then you can map out a plan for how you’ll address each category and subcategory.
For example, what will you do in the next year to close the gap in your recovery planning category? How much money will this cost you?
This forces you to establish clear corrective actions that will help you apply the desired framework that best serves your organization.

