The Ultimate Manual To Spoofing Attack Types
Even the most diligent employees and IT teams can fail to quickly identify a spoofing attack. But the stronger our awareness of spoofing in all its forms, even as it rapidly evolves, the easier it is to proactively protect against it—so let’s take a look at the state of spoofing today.
What Is a Spoofing Attack Anyway?
The term “spoof” basically means to mimic something or trick someone. A spoofing attack is a category of cyberattack in which the attacker takes on a false identity—that of another device or a trusted source—to appear as safe, in an attempt to steal money, collect sensitive data, hack systems, or spread malware. Spoofing is often just the first step in large-scale cyberattacks.
How Spoofing Attacks Work
There are many ways cybercriminals can spoof both companies and individuals, as I’ll cover below. Whatever the strategy, spoofing relies on two types of vulnerabilities to be successful:
- Network vulnerabilities. These days, organizations must take proactive steps to guard against network vulnerabilities—or flaws in software, hardware, or organizational processes—to ensure the security of their customers’ data.
- Human vulnerabilities. Spoofing attacks leverage social engineering, which refers to the manifold methods of deceiving us into doing something dangerous, like divulging confidential information or installing malware onto our devices.
Sometimes all it takes is for an attacker to simply invoke the name of a trusted organization for us to click something we shouldn’t. But spoofing attacks can be so sophisticated that they play on powerful human emotions like excitement, fear, and empathy without us even realizing it.
Here are some of the most common examples of different types of spoofing attacks to look out for and how they work, from the relatively simple to more advanced.
Example #1: Email Spoofing
We’ve all seen these in our spam folders. Email spoofing means making an email appear as if it came from a trusted source, like a big company, coworker, or friend. Attackers can do this by:
- Using a fake sender that looks similar to the original except for a few characters—for example, using a zero (0) in place of the letter O (known as a homograph attack)
- Disguising the from field to match the sender name or address of one of your contacts
- Addressing you by name and with personalized language (known as spear phishing)
- In the case of imitating a company, using its logo, colors, font, buttons, and other familiar branding elements
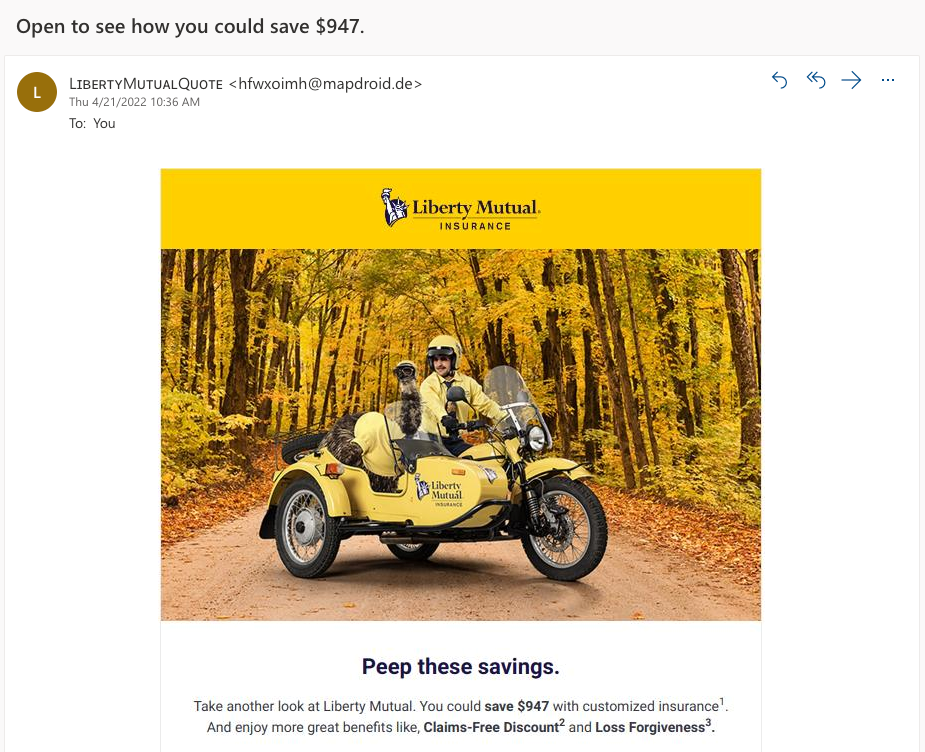
Email spoofing is often used as part of a phishing attack. The goal is to trick you into clicking a malicious link or attachment designed to infect your computer with malware or steal money or your sensitive information.
A famous example of this is known as the “grandparent scam,” when the attacker exploits the elderly by pretending to be a grandchild in need of money. Or a spoofed email from “PayPal” or “Amazon” might inquire about purchases you never made, making you concerned enough about your account’s security to click through.
Example #2: Website Spoofing
Website (also known as URL or domain) spoofing means making a malicious website look like a legitimate one. It’s common for attackers to spoof multiple points of contact, and website spoofing is generally used in conjunction with a spoofed email that links to the website.
The goal is usually to obtain the visitor’s sensitive information. For example, attackers will spoof the login page of a familiar website to have you attempt to log into your account, at which point the attacker can harvest, use, and/or sell your login credentials (aka login spoofing) or drop malware onto your computer (known as a drive-by download).
Similar to email spoofing, fake websites commonly feature legitimate branding, as well as a URL or domain name that’s almost identical to the real site except for a few characters. What’s missing is the green padlock, which represents the SSL certificate and used to be a big giveaway that a website isn’t legit. But SSL certificates are now free and easy to obtain. One security researcher found that today it’s possible to create a fake website that appears to have a secure connection and shows the correct URL.
Example #3: Caller ID Spoofing
Using a VoIP (Voice over Internet Protocol) phone service, anyone can create a phone number or caller ID name of their choice. Companies legitimately spoof business caller IDs to appear more professional.
But spoofed spam calls are also on the rise. Attackers use caller ID spoofing to make an incoming call appear to come from somewhere it isn’t. Often scammers will use a phone number with your area code to make it seem like the call is local because they’ve learned that people are more likely to answer a local number.
Once you answer the phone, the attacker will try to convince you to divulge sensitive information. They might pose as a customer service agent who needs personal information like your SSN, date of birth, or password to complete a transaction. More advanced spoofers can reroute a call to a long-distance carrier, causing you to rack up expensive fees.
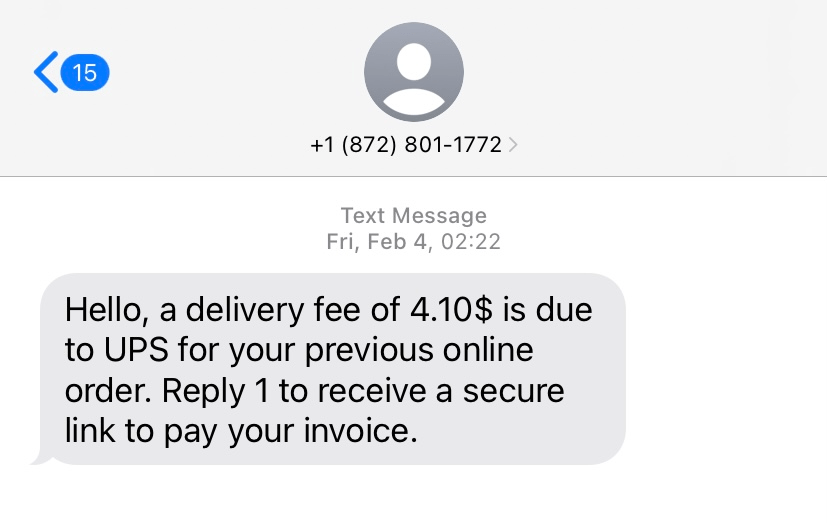
Example #4: Text Message (or SMS) Spoofing
Text message spoofing is similar to caller ID spoofing, only here the attacker sends a text or SMS with someone else’s phone number or hides behind an Alphanumeric Sender ID. Again, legitimate organizations use Alphanumeric Sender IDs to replace their phone number with a short and easy-to-remember ID, like a brand name, in marketing and communication with customers.
In spoofing attacks, the scammer might pose as a legit organization. For example, they’ll take advantage of people signing up for text tracking alerts by posing as a staffing agency or shipping company with an update to a job application or shipment. But the message will include links or text that leads to malware downloads or SMS phishing sites (smishing).
Example #5: IP Spoofing
Now we’re getting into the most advanced forms of spoofing. In simple terms, IP spoofing is altering an IP address to hide the location from which you are sending or requesting data online.
As with other types of spoofing, IP spoofing has legitimate applications. VPN services use it to protect your privacy, and IT teams create multiple spoofed IP addresses to perform load balancing or testing. But IP spoofing is also a type of cyberattack commonly used to:
- Keep authorities from finding out the true identity of an attacker
- Bypass security services that would have otherwise blocked the attacker
- Prevent the compromised device from sending attack alerts to security services
You’ll see this play out in threats like distributed denial of service (DDoS) attacks, which prevent the targeted website from functioning properly by flooding it with traffic and limiting access for authentic users. One of the biggest factors for the recent growth in DDoS attacks was COVID-19, which drove a rapid shift online and gave hackers more targets than ever before.
Example #6: ARP Spoofing
ARP (Address Resolution Protocol) is the communication protocol that maps an (ever-changing) IP address to a (fixed) MAC address, to transmit data over a LAN. Computers learn when an IP address matches a MAC address, so that when a data packet arrives at a network gateway, the gateway machine can ask the ARP program to find a MAC address that matches the IP address in the data packet. If it’s a match, the data can move ahead.
In an ARP spoofing (also known as an ARP poisoning) attack, an attacker will link their own MAC address with the IP address of a legitimate computer or server on the network. They can then intercept data meant for the owner of that IP address, and steal or modify the data.
ARP spoofing is another method used in DDoS attacks, as well as man-in-the-middle attacks.
Example #7: Man-in-the-Middle (MitM) Attack
A man-in-the-middle (MitM) attack is akin to eavesdropping. It’s when an attacker (the middle man) infiltrates communication between two parties, a user and a web application. In doing so, the attacker can impersonate one party or alter the communication to reroute sensitive information to themselves—for example, login credentials they can change, or banking details they can use to transfer funds.
This is one of the risks of using free public wifi, for example. A man in the middle can either hack the wifi or set up a fake wifi network with the name of a nearby business. Once you connect, the attacker can monitor your activity and intercept your login credentials, credit card details, and whatever else you happen to enter.
Example #8: DNS Spoofing
Besides email spoofing, another way to route users to malicious websites is through Domain Name System (DNS) spoofing. DNS spoofing, also known as cache poisoning, is an attack that alters Domain Name records to redirect traffic to a malicious site.
In other words, the attacker replaces the IP addresses stored in a legitimate DNS server with IP addresses of a server under their control, so that when you click a link to what you think is your bank’s website, for example, you end up on the malicious site instead. In one real-life example in 2018 involving health insurance provider Humana, hackers used DNS spoofing to steal the complete medical records of at least 500 people.
Example #9: GPS Spoofing
GPS spoofing means tricking a device’s GPS into thinking you’re in one location or time zone when you’re actually in another—another type of spoofing that has relatively innocent uses. You might know it from Pokemon GO when players use GPS spoofing to catch Pokemon all over the country without ever leaving their house. Some people spoof their own devices to protect their privacy or personal data from being tracked.
More nefarious reasons for GPS spoofing might include hacking the navigation system of a truck to reroute cargo to a destination where it can be stolen, or luring an individual toward dangerous destinations or online connections with malicious intent. Anyone that relies on GPS-enabled devices or location data could be a target.
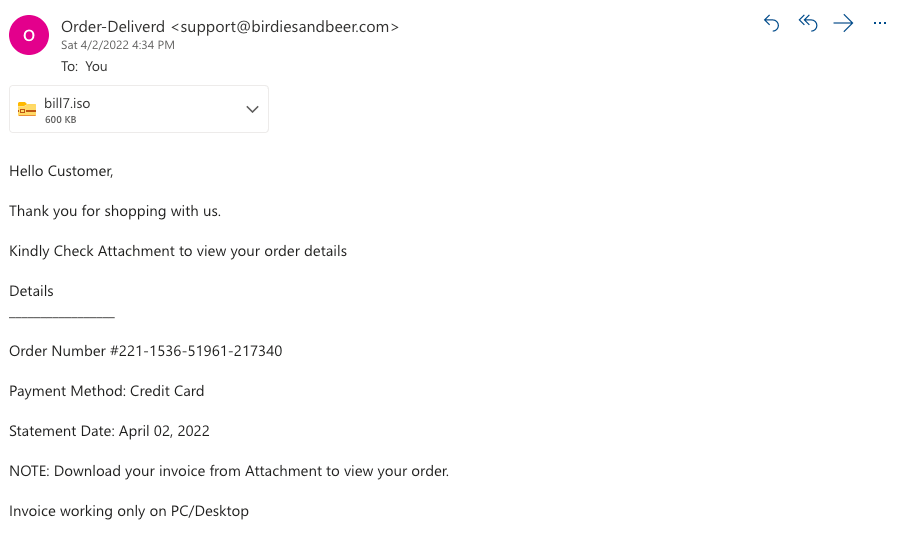
Example #10: Extension Spoofing
Extension spoofing means spoofing the extension name of a file—in this case, a malicious file, to disguise it as legitimate.
One common trick is to disguise malware as a text file using a file name like filename.txt.exe. Attackers know that file extensions are hidden by default in Windows, so Windows users will only see the filename.txt and think they’re opening a text document, which actually runs a malicious program.
Example #11: Facial Spoofing
Facial recognition is an emerging technology, making it particularly vulnerable. Research has found that it’s possible to build 3D models from photos available on social media and use them to unlock a phone using Face ID.
In other famous examples, we’ve seen how it’s possible to create fake news videos and embarrassing content featuring the voices and likeness of high-profile people, with implications varying from extortion to swaying political campaigns. Researchers have used deepfake technology to produce fake video footage of former President Barack Obama that perfectly matches real audio, and attackers once used AI to use a CEO’s voice to extort money.
Right now, the real-world applications for facial recognition are fairly limited—we use it to unlock our devices and not much else. But the risk of facial spoofing will only increase as we find ourselves using our faces to make payments, sign documents, and more.
How to Protect Against Spoofing Attacks
Start with the Basics
Here are a few basic precautions individuals can take right now to reduce their chances of falling victim to an attack:
- Switch on your spam filter to prevent most spoofed emails from reaching your inbox
- Use Google or another Password Manager to create strong passwords, autofill your login credentials, and alert you to compromised passwords
- Enable two-factor authentication on online accounts for websites that support it, for another layer of protection
- Get into the habit of hovering over links before clicking to check for unusual URLs
Know the Signs
Be aware of the common indicators of spoofing. For example:
- Unicode or other strange characters in a sender’s address or ID
- Emails from random email addresses using a business name as their sender name
- Typos or bad grammar in messages that appear to be from a legitimate business
- Links and attachments from unknown senders
- Calls or texts from unknown numbers
- Websites that aren’t secured or encrypted, represented by the green padlock or https:// at the beginning of the URL (not necessarily a spoof, but proceed with caution)
- Fields that don’t autofill your login credentials
- Someone asking you for sensitive information without verifying they’re a trusted source
- Messages or web pages with content that seems too good to be true
Invest in Security
Good antivirus software is the average person’s front-line defense in protecting against cyber threats. It’s worth the peace of mind. If you do click on a bad link or attachment, antivirus software can alert you to the threat and stop the download.
For businesses, security measures are more advanced and may be specific to certain types of spoofing attacks. For example, GPS security involves obscuring your GPS antennas. Remote service solutions must be properly patched and configured. Teams must be properly educated about security risks. Be sure to consult security solutions and best practices in your business area or industry.
Report Anything Suspicious
When you get a message that’s unexpected, seems too good to be true, or looks suspicious in any way, always do your research.
Double-check the address of the sender or website and whether it matches real information. Don’t be afraid to contact the real sender or owner directly to verify that they indeed sent the message, or Google the phone number, address, or contents of the message to see if it’s a known scam. If the message asks you to log in to your account and take some kind of action, instead of clicking the link, open a new tab or window and navigate to the site directly.
If it turns out you might have been spoofed: block the sender, delete the message, and report it to the FCC or the real company’s security team.

