Phishing Statistics 2022
Phishing attacks represent a highly effective means for hackers to access your computers. When you fall victim to a phishing attack, you could lose critical personal or company information and financial resources.
To help you understand how phishing attacks occur and how you can protect your organization or business, we’ve dug deep into the statistics behind phishing attacks.
What Are Phishing Statistics Anyway?
Many private entities and governmental departments collect data about phishing. These phishing statistics are essential for helping law enforcement understand the methods hackers are currently using to try to steal information. Phishing stats also give cybersecurity companies the information they need to craft the most efficient types of defense.
Security departments at businesses use phishing statistics to figure out the best way to educate employees and network users about ways to protect themselves and the business’ data.
What Is Phishing?
During a phishing attack, a hacker will attempt to fool someone into giving up sensitive information by posing it as a legitimate request. Preventing phishing is a key means of deploying employee data security.
A phishing attack may involve a hacker sending you an email requesting banking information, passwords, or a Social Security number. The attacker may try to entice you to share this information through threats, the promise of a reward, or by simulating a legitimate request from someone you trust.
The phishing email may have a fake website link included in it. When you click this link, you move to a fake website made to look like a legitimate website. When you enter your information on the fake website, the hacker steals it.
Phishing attacks can cause a number of problems for individuals and businesses, including tricking people into revealing:
- Banking information
- Credit card information
- Social Security numbers and other personal information
- Passwords and usernames
Hackers can then use this information to commit identity theft or steal money from you. At a business, a phishing attack may give the hacker the ability to upload malware or viruses to the company network, giving the hacker illegitimate access to the network.
15 Most Important Phishing Statistics
Now that you understand phishing attacks and why it is important to protect yourself and your business, we uncovered the most interesting and vital phishing statistics during our research.
1. Phishing Attacks Occur Quite Frequently
According to research from Proofpoint, if your business or organization hasn’t recently experienced a phishing attack that worked, you’re in the minority.
In 2020, 57% of businesses and organizations worldwide reported seeing a successful phishing attack that they had to try to overcome. That’s an increase from the 55% that Proofpoint reported in 2019.
For American-based businesses, the numbers are far worse. About 74% of US-based businesses and organizations reported being victims of a successful phishing attempt.
The most common type of phishing attack involved sending the same email message to multiple users in the organization, hoping at least one person falls for the scam.
2. Reported Cybercrime Complaints Often Involve Phishing
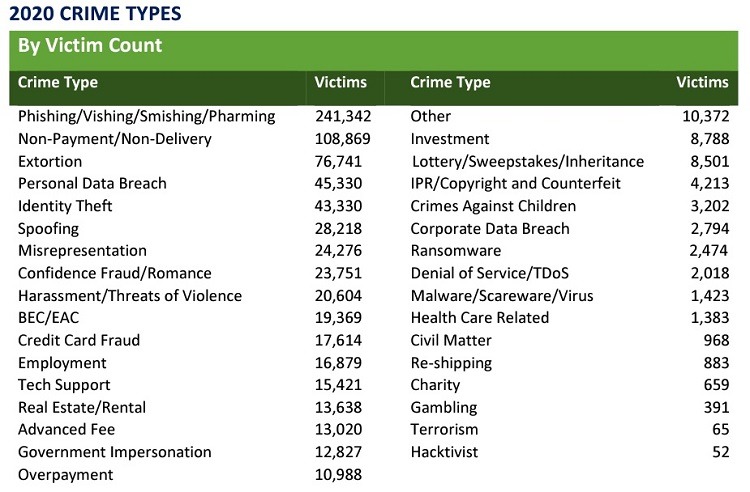
The FBI received 12 times more victim complaints regarding cybercrimes involving phishing attacks in 2020 versus 2016.
Phishing attacks climbed significantly year over year as well. The FBI reported more than 241,000 complaints regarding phishing in 2020 versus almost 115,000 phishing attack complaints in 2019.
3. Most Common Types of Data Compromised in a Phishing Attack
According to Verizon, certain types of data fall into the wrong hands through phishing attacks more often than with other types of attacks, including:
- Health insurance identifying numbers
- Insurance claim numbers
- Name and address
- Passwords
- PINs
- Usernames
4. Most Common Results From Successful Phishing Attacks
Proofpoint reports that successful phishing attacks globally result in a loss of data 60% of the time. A compromise of account credentials for the organization’s network occurs in about 52% of phishing attacks that work.
Financial loss only occurs in 18% of successful phishing attacks. However, organizations and businesses may suffer financial loss through a ransomware attack that originates with a phishing scheme, as organizations report that 47% of phishing attacks that end up being successful result in an infection on the network with ransomware.
5. Understanding of What Phishing Entails

Security professionals agree that the best defense against phishing attacks in a business or organization involves educating team members and employees about what to expect. According to Proofpoint, employees around the world can accurately describe phishing 63% of the time.
However, employees in the United States tend to have less of an understanding of phishing than counterparts elsewhere in the world. Based on location, employees who successfully described phishing in a survey question included:
- 69% of United Kingdom workers
- 66% of Australian workers
- 66% of Japanese workers
- 64% of German workers
- 63% of French workers
- 63% of Spanish workers
- 52% of American workers
6. Prevalence of Training for Cybersecurity and Phishing
Proofpoint reports that businesses use a wide range of educational techniques to try to give employees the training they need to understand and to avoid phishing attacks and other cyberattacks.
When developing training programs for security awareness, 98% of organizations report that they have this type of program in place. However, the level of effectiveness of these programs varies widely.
- Formal training: About 64% of companies report conducting formal training that involves either an in-person class or a computer-based training program.
- Simulated attacks: About 30% of companies report using simulated phishing attacks as the only means of training for employees. (The other 6% of companies report using various other techniques.)
In cybersecurity training sessions, 74% of companies report spending time on email-based phishing attacks, which is more than any other type of cyberattack. For example, only 44% of companies include training on best practices for password creation, and only 48% discuss the security of mobile devices.
Organizations also deploy significantly different means of deciding which members of the organization should have cybersecurity and phishing training.
- Company-wide: About 52% of companies report providing training to all team members.
- Department-focused: About 36% of companies report providing training only to specific departments.
- Individual-focused: About 11% of companies report only training specific individuals in the organization who have access to the most sensitive information.
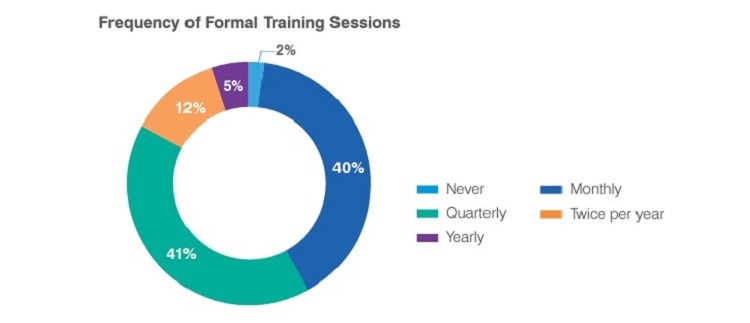
Finally, organizations report widely varying frequencies for holding training sessions. While only 2% of companies report that they have no formal training procedures in place, among the companies that perform training, there is no clear majority on how often the training should take place.
- Monthly: 40%
- Quarterly: 41%
- Twice a year: 12%
- Yearly: 5%
- None: 2%
7. Common Reasons Employees Fall for Phishing Email Attacks
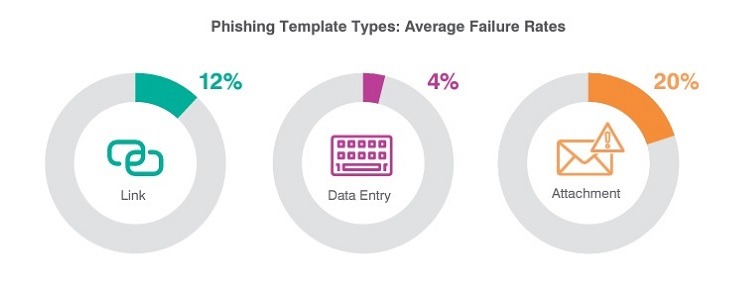
Through testing scenarios of the vulnerability of certain networks, Terranova Security and Proofpoint report that team members in businesses and organizations will click on a fake attachment in a phishing email message about 20% of the time. If the email contains a fake link to a website, about 12% of employees will click on it.
Only about 4% of employees will actually enter data in a phishing attack. (This means of the 12% of employees who will click the phishing link in the email to open a fake website, about one-third of them will enter data into that site, which equals 4% of all employees participating in the test.)
Overall, according to Proofpoint’s tests, 11% of employees failed a phishing test in 2020, which is a slight drop from the 12% who failed the test in 2019.
Some of the most successful subject lines and email content that will entice employees to click on the phishing link include:
- Alert about attempted fraudulent login to the employee’s social media account
- Incoming payment waiting for verification
- Suspended financial account because of missing personal information
- Secure update needed for software
- Compromised health information
- Zoom meeting invitation available
8. Employees Struggle To Recognize Phishing Attacks
A Proofpoint testing procedure in 2020 attempted to determine whether employees and team members recognized potential phishing attacks.
During the test, organizations asked their team members to report suspected phishing emails. Proofpoint measured the number of reports of suspected phishing versus the actual number of phishing emails sent during the test. Proofpoint also measured the number of failures during the trial, where an employee clicked on a fake link or downloaded a fake attachment in a phishing message.
As mentioned earlier, employees failed the phishing test 11% of the time in 2020. Almost more disappointingly, employees only were able to successfully report 13% of the phishing emails. This means they almost fell for as many phishing schemes during the testing procedure as they spotted and reported phishing attempts.
9. Phishing Attacks Can Be Costly
According to a data breach report from IBM, businesses that suffer a data breach experience a number of different initial attack vectors that create the breach. When phishing serves as the initial attack vector, it often results in a significant financial loss.
Phishing attacks that fit into this category have an average loss of $4.65 million per attack, which is the second most costly type of attack that leads to a data breach. Phishing only trails compromised email attacks that result in data breaches. These cost $5.01 million per attack on average.
When phishing is the initial attack vector for the data breach, the average cost to deal with the breach is more costly than attacks that originate with a malicious insider, a software vulnerability, or a compromise in the physical security of a location.
10. Phishing Attempts That Lead to Ransomware Attacks Often Lead to a Payout
As mentioned earlier, phishing attacks sometimes result in a hacker being able to install ransomware on the network.
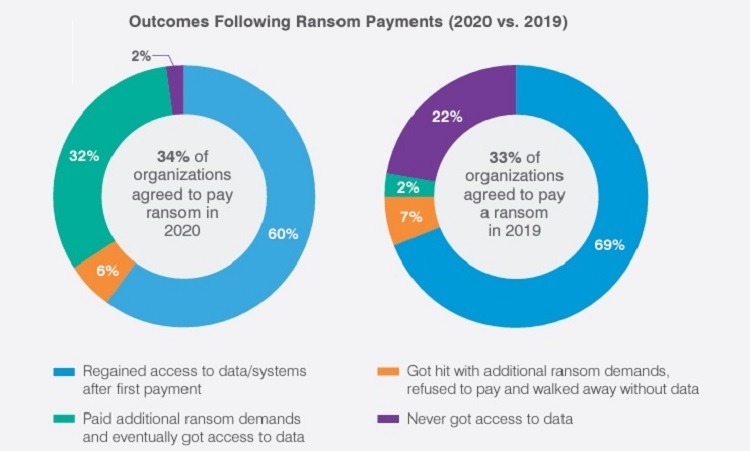
Among all companies in the global Proofpoint survey, 34% of them paid some sort of ransom in 2020, which is slightly higher than the 33% who paid in 2019. In 2020, 32% of companies worldwide experienced some sort of ransomware infection but chose not to pay. Another 34% of companies globally did not experience a ransomware infection in 2020.
Of the 34% of companies that agreed to pay the ransom, only 60% received access to their data after the first payment in 2020. Another 32% of companies paid additional ransom demands before receiving the data. And 8% of companies that made at least one payment for a ransomware attack did not regain access to their data.
11. Phishing Attacks are Difficult to Contain
According to IBM’s data breach report, when phishing represents the initial attack vector, companies report needing an average of 213 days from the date of the attack to the date of discovery.
Phishing attacks are also difficult to bring under control after the organization discovers the problem. Businesses report needing an average of 80 days to bring the damage under control that the phishing attack caused.
As an example, if a phishing attack succeeds on Jan. 1, it requires an average of 293 days, or until Oct. 21, to discover and take care of the problem. This is longer than attacks involving a third-party software vulnerability or a compromise of a location’s physical security.
According to IBM, the majority of data breach attacks against a business or organization require between 285 and 305 days to resolve.
12. Phishing Attacks Spiked During the Early Days of the COVID Pandemic
According to Barracuda, in March and April of 2020 when businesses were scrambling to give employees an opportunity to begin working from home in a secure manner, phishing attacks spiked.
Barracuda Sentinel reported measuring nearly 500,000 phishing attacks via email in March 2020 alone. In January 2020, Barracuda measured about 218,000 phishing email attacks over email.
13. Hackers Attacking Via Phishing Emails Take Steps to Cover Their Tracks
Barracuda worked with Columbia University to study the originating location for phishing email attacks. The researchers studied more than 2 billion emails sent during January 2020, of which about 10% served as phishing attacks.
The phishing emails frequently originated from Eastern Europe, the Middle East, Africa, and Central America.
Those sending the phishing email messages commonly sent the messages through far more server locations than a typical email message. Roughly 85% of legitimate emails traveled through servers in only one or two countries. Almost 40% of emails involving phishing attacks traveled through at least three countries.
14. Phishing Replacing Malware As a Primary Threat
According to Google Safe Browsing, which measures the safety of websites globally, the number of sites marked as phishing sites in January 2021 totaled more than 2.1 million sites. This represents an increase of about 27% from January 2020.
Phishing sites now dwarf the number of malware sites that Google Safe Browsing measures. Malware sites existed in far greater numbers than phishing sites until 2016, when Google measured about 500,000 of each kind of site. Since then, phishing sites have undergone an increase of more than four times, while malware sites now total only about 25,000.
15. Unclear Consequences for Employees Repeatedly Falling for Phishing Attacks
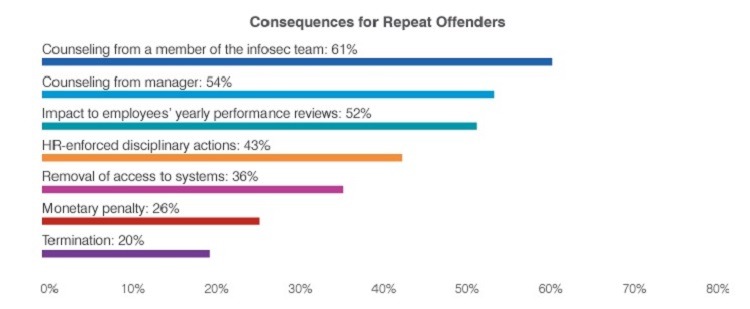
When employees fall for phishing attacks, Proofpoint reports that organizations struggle to determine the appropriate level of punishment or consequences.
Organizations use consequences ranging from counseling and additional education to disciplinary actions and monetary penalties. Some companies use termination as a consequence, although only 20% of companies report using this extremely severe punishment.
Companies also vary in how quickly they begin assigning consequences after holding a training session. About 46% of companies begin deploying consequences immediately to 6 months after the training session. About 44% wait between 6 and 12 months to start giving employees consequences for errors. The other 10% of companies wait at least 1 year to begin handing out consequences.

