Offboarding Checklist for IT Teams

Employees have left companies in record numbers over the last few years due to layoffs, job changes, and new opportunities. In 2023, the tech sector alone faced more than 1,500 layoffs, affecting an average of 667 people per day.
Although IT and Security teams do not have extra time or resources, they often pick up the slack during offboarding procedures. These teams must ensure company intellectual property (IP), personally identifiable information (PII), and personal health information (PHI) are secure and protected.
Seventy-six percent of executives agreed employee offboarding represents a significant security threat, according to a Nira-Gartner Peer Insights report.
Offboarding creates risks, not only from malicious behavior but also from common mistakes. Concerns include company files owned by personal email accounts, unidentified public links accessible by anyone on the internet, and unsecured shared drives—to name a few.
This post provides a checklist for a smoother IT offboarding process, to reduce risk and keep your company’s confidential data secure.
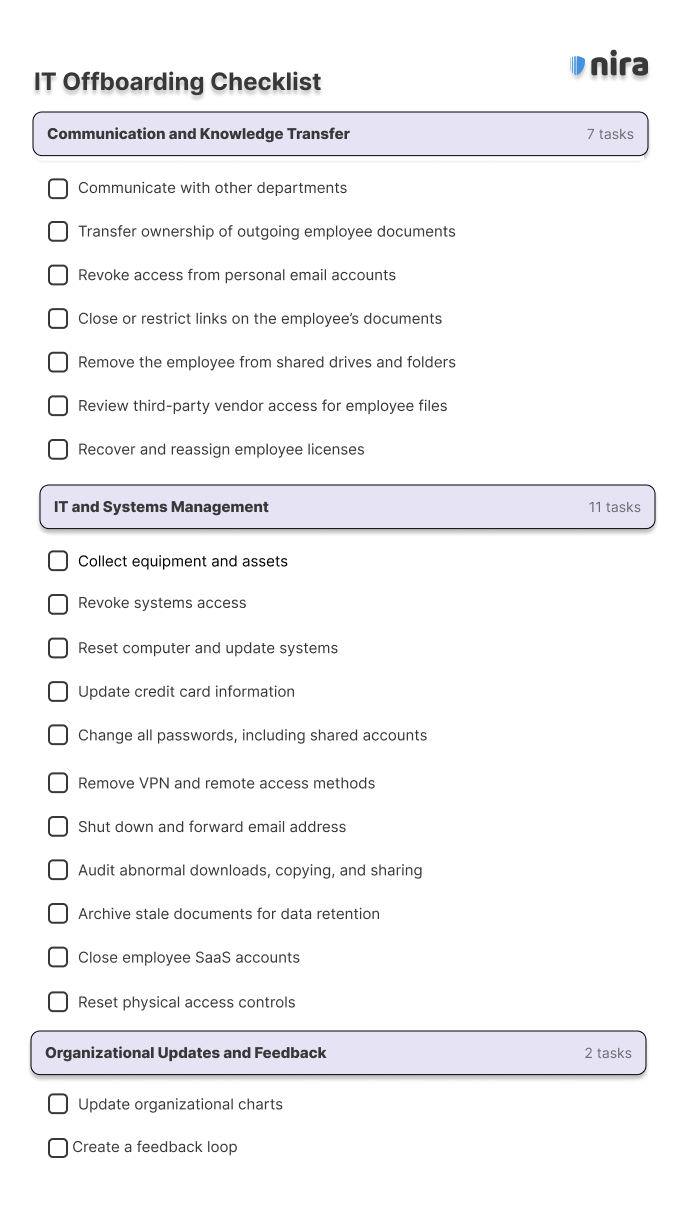
An effective IT offboarding checklist can be separated into three main categories:
- Communication and Knowledge Transfer
- IT and Systems Management
- Organizational Updates and Feedback
Communication and Knowledge Transfer
-
Communicate with other departments
The first step of any offboarding process is to understand timely information about the employee’s departure. This includes their last working day, their reason for departure, and any specific offboarding requirements set by your company.
Coordinate with other relevant departments including Human Resources and Compliance to ensure compliance measures and company policies are properly implemented as the employee leaves.
2. Transfer ownership of outgoing employee documents
The departing employee may still own company documents in cloud collaboration tools like Google Workspace and Microsoft OneDrive. These files could have sensitive information that should not be accessed by anyone outside the company, and where possible, document ownership should be transferred to the relevant team members.
This preserves critical information and ensures a smooth transition for ongoing projects. To learn how to securely transfer ownership of documents in Google Drive, visit here.
3. Revoke access from personal email accounts
Personal email account access is a hidden problem that most companies face. More than half (52%) of employees surveyed said they or a coworker had accidentally added their personal email to company files. What’s worse, after employees leave, their personal email accounts still have access to these sensitive documents.
It’s vital to understand how many personal email accounts have access to your company data and to revoke their permissions immediately. To learn how to do this quickly and efficiently, visit here.
4. Close or restrict links on the employee’s documents
When an employee leaves, shared links often remain on their cloud-based documents. These documents might be accessible to anyone in the company with the link, or even anyone on the internet with the link. Documents with Public and Company links are seldom stripped of access and are quickly forgotten.
To prevent unauthorized access, you should find and restrict all shared links on the departing employee’s documents. For more information, visit here.
5. Remove the employee from shared drives and folders
Many departing employees still have access to shared drives and folders in cloud collaboration tools like Google Workspace. Shared drive security is a concern because collaborators can accidentally add unauthorized people or documents to the shared drive, inadvertently sharing all documents and folders within it.
It’s important to understand who has access to which shared drives and to remove all access permissions from drives and folders after an employee leaves.
6. Review third-party vendor access for employee files
Third parties often have access to hundreds or thousands of company documents, many of which are confidential.
Typically, when an employee leaves, third-party access to their documents remains. That means third parties they were collaborating with continue to have access to the ex-employee’s files, often in perpetuity. In fact, 60% of employees said they never or sometimes remove vendor access once they are no longer working with third parties.
Make sure that all vendor and third-party access has been removed from the employee’s files and that vendors do not have Editor permissions unless necessary.
7. Recover and reassign employee licenses
It’s vital to be aware of any subscriptions or software licenses assigned to the departing employee. This helps prevent unnecessary costs and ensures compliance with licensing agreements and offboarding procedures.
You should transfer any vendor licenses associated with the outgoing employee to the appropriate team members, or close out the license and optionally have the former employee’s data deleted.
IT and Systems Management
8. Collect equipment and assets
Once you know their last working day, you can set the appropriate time to gather all company devices issued to the departing employee, including laptops, cell phones, and any other hardware. Once ready, you will ensure all relevant data on these devices is transferred as needed.
9. Revoke systems access
According to Intermedia, 89% of former employees still have access to at least one application from their former job. Ensure you disable or deactivate the departing employee’s access to various systems, networks, and applications to reduce risk and unneeded expenses.
10. Update credit card information
Your finance or HR team will probably be in charge of recovering the employee’s company credit cards. However, you should be aware of any IT subscriptions or services the employee may have been responsible for.
If applicable, update credit card information connected to the outgoing employee so services are not interrupted.
11. Reset computers and update systems
Once any relevant data has been downloaded or transferred, reset the departing employee’s computer to factory settings or perform a secure wipe. Ensure all systems are updated to reflect the changes in user access.
12. Change passwords
Change all passwords associated with the outgoing employee’s accounts, including shared accounts and access to databases. You should ensure that new passwords are strong and enable secure multi-factor authentication (MFA) methods as applicable.
For shared accounts, make sure relevant parties are aware of the changes.
13. Remove VPN and remote access methods
Revoke any VPN or remote access privileges that the departing employee had. It’s good practice to review remote access methods periodically to make sure employees do not still have ways to get into the network.
14. Shut down and forward email address
Disable the departing employee’s email account and set up forwarding to redirect emails to the appropriate team members. The former employee’s manager is usually the best person. This allows the manager to quickly follow up on any loose ends.
If the situation is sensitive for any reason, you can forward the email to someone in HR. After a few months, you should be able to turn off email forwarding entirely.
15. Audit abnormal downloads, copying, and sharing
Two-thirds (67%) of executives believe employees exiting the organization are more likely to cause security breaches by accident, rather than intentionally. However, suspicious activity does happen, and more than 45% of employees admit to taking documents from former employers.
Whether it be by accident or on purpose, it’s vital to understand what company material was downloaded, copied, or shared. Review and audit any unusual or abnormal activities related to downloads, copying, or sharing of data by the departing employee.
16. Archive stale documents for data retention purposes
Access to stale documents can create several issues for an organization. These documents haven’t been modified in years, yet they are still accessible by employees and external accounts, like personal email accounts and ex-vendors.
This can cause issues from a compliance and data retention perspective. You need full visibility into documents that should be archived based on data retention policies. For tooling that helps, visit here.
17. Close employee SaaS accounts
Close any Software as a Service (SaaS) accounts associated with the departing employee. Common accounts you’ll want to check include project management tools like Trello or Asana; document storage solutions like Dropbox or Box; communication tools including Slack or Zoom; and CRMs like Salesforce.
It’s helpful to keep a record of accounts that employees have access to. This makes it much easier to shut everything down when an employee leaves.
18. Reset physical access controls
If applicable, reset physical access controls such as keycards or entry codes to prevent unauthorized entry to company buildings. You can incorporate periodic security audits of the physical access control infrastructure if needed.
Organizational Updates and Feedback
19. Update your organizational charts
Update internal organizational charts and directories to reflect the employee’s departure and any changes in responsibilities.
Your company’s core documentation should be updated so the outgoing employee is no longer listed as an employee.
20. Create a feedback loop
Coordinate with relevant departments (for example, HR and Compliance) and establish a feedback loop to continuously refine offboarding procedures. This can identify areas for improvement and ensure the IT offboarding process remains effective.
Multiple security risks exist when offboarding employees. Insider threats pose a problem, but the majority of issues stem from common mistakes and accidental misconfigurations. Using an IT offboarding checklist helps ensure your bases are covered and nothing gets missed.
IT and Security teams may use powerful tooling to help with the offboarding process including bulk transfer of file ownership and securing company shared drives.
We recommend periodic security audits to ensure all company documents are successfully transferred and secured. You can set up your free audit here.

