Getting Started with the Google Workspace Security Investigation Tool
Data breaches and security threats are increasing, and so are their financial impacts. In 2023, the average global cost of a data breach was $4.45 million, according to IBM. In the United States, this figure soared to an alarming $9.48 million, surpassing all other countries. Beyond the financial aspect, data breaches result in reputational harm, erosion of customer trust, and legal liabilities.
To combat this rise in risk, IT, Security, and Compliance teams are turning to the Google Workspace Security Investigation Tool (GSIT). In this post, we’ll explore how to use the GSIT specifically related to Google Drive. Administrators can leverage the power of the tool to initiate searches related to Drive log events and then take actions based on the search results. Here’s how to do it:
How to run a search for Google Drive log events
- In the Admin console, go to “Menu” > “Security” > “Security center” > “Investigation tool.”
- From the Data source menu, click “Drive log events.”
- Click “Add Condition.”
- Click “Attribute,” and select an option. For a complete list of attributes, visit here.
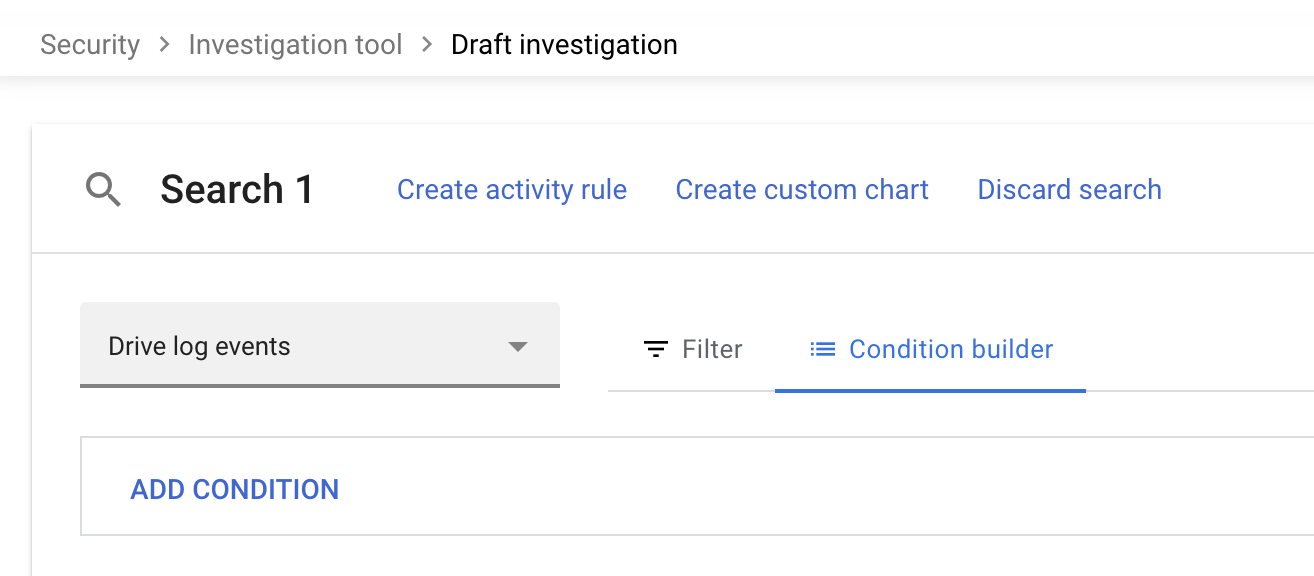
- Click “Contains” and select an operator.
- Enter a value, or select a value from the drop-down list.
- You can add more search conditions by repeating steps 3–6.
- Click “Search.”
- You can also group your results by different attributes. Click “Group results,” then choose your attribute, such as “Date” or “Actor,” from the drop-down menu.
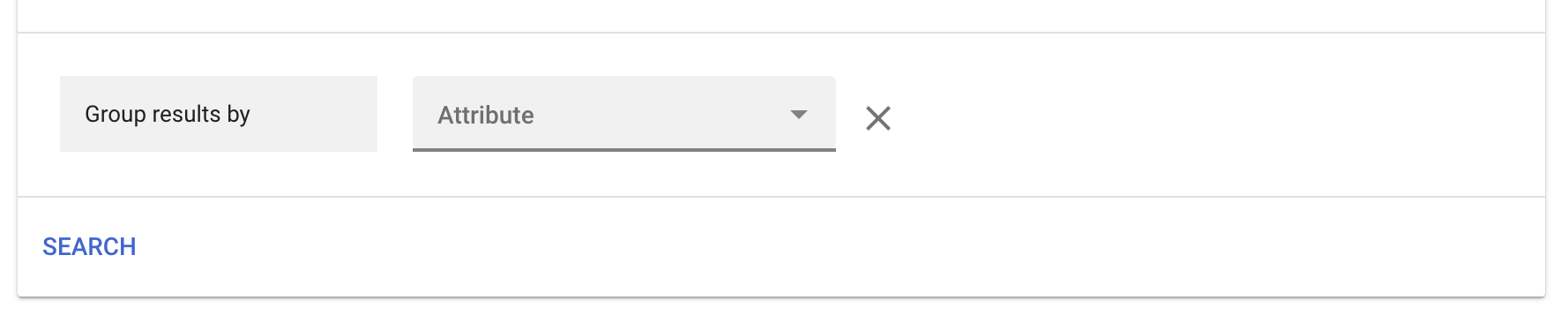
- To save your investigation, click “Save” > enter a title and description > click “Save.”
How to view files shared externally
Administrators can take the following steps to see files that are shared externally:
- In the Admin console, go to “Menu” > “Security” > “Security center” > “Investigation tool.”
- From the Data source menu, click “Drive log events.”
- Click “Add Condition.”
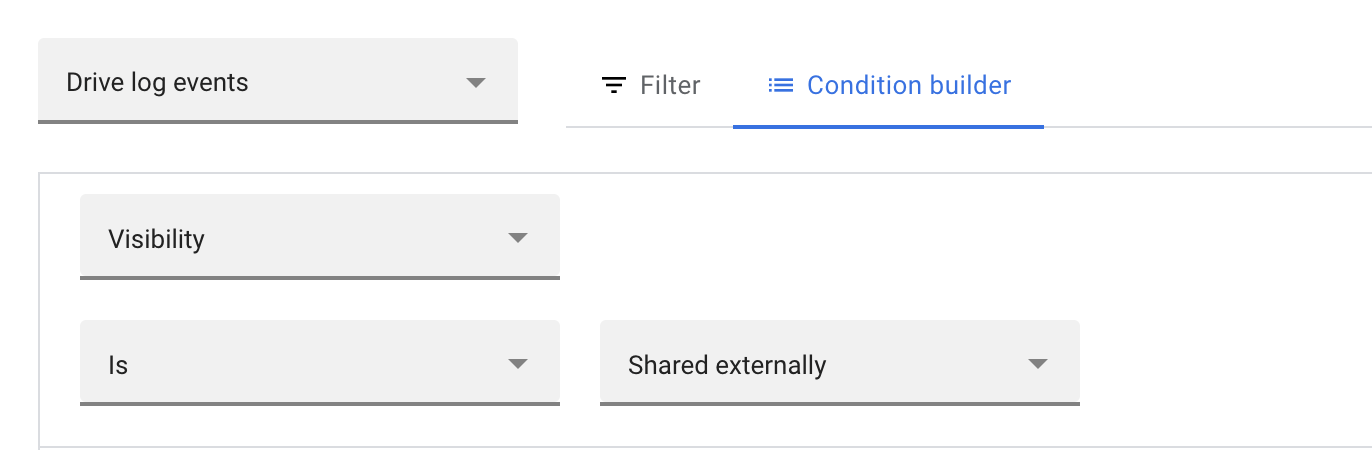
- Click “Attribute,” and select “Visibility.”
- Click “Contains” and then select “Is.”
- Click “Visibility” and then select “Shared externally.”
- Click “Search.”
How to start a file-sharing investigation
Administrators may need to search for a sensitive document that’s been shared externally, or shared too broadly. In this section, we’ll go over how to investigate a file that’s been shared externally by a specific user in your organization. First, we’ll look at how to conduct the search, and then show how to view and export those search results.
- In the Admin console, go to “Menu” > “Security” > “Security center” > “Investigation tool.”.
- From the Data source menu, click “Drive log events.”
- Click “Add Condition.”
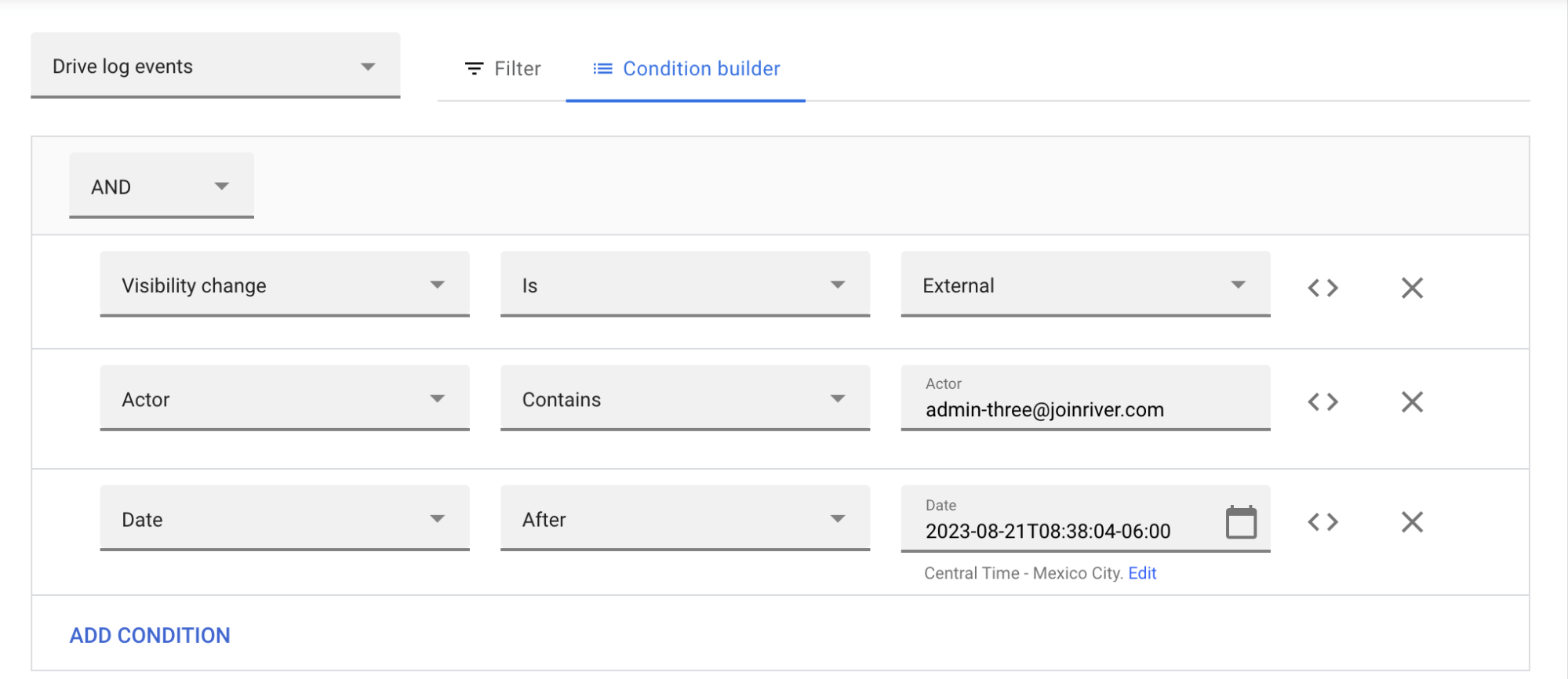
- From the Condition menu, click “Visibility change.”
- Make sure the condition is set to “External.”
- Click “Add Condition.”
- From the Condition menu, click “Actor.”
- In the User field, enter the username of the user who shared the file—for example, user@example.com.
- Click “Add Condition.”
- From the Condition menu, click “Date.”
- Change the condition to “After.”
- In the Date field, enter the earliest date and time when the file may have been shared externally.
- Click “Search.”
How to view and export search results
After finishing the above steps, the search results are displayed in a table at the bottom of the page. The table displays the date and time the file was shared externally, the document ID, document type, visibility, the title, the event type (for example, Change user access), the actor’s username, and the owner of the document. To save these search results to your My Drive folder, click the “Export all” button at the top of the table.
These examples show administrators how to use the condition builder to choose various attributes and operators when performing a search. For more information on the condition builder, visit here.
Since its debut in 2018, Google Workspace’s Security Investigation Tool has become a crucial security solution for companies using Google Workspace. Tailored to empower administrators and security analysts, GSIT plays a vital role in identifying, evaluating, and mitigating potential threats. Its functionality spans across multiple Google services, assisting IT, Security, and Compliance teams in securing their company’s data.
By revealing user activities and strengthening access permissions, the GSIT sheds light on investigations in Google Workspace, providing administrators with a toolkit to enhance security measures. For a complete guide on how to use the tool, visit here.

