Best Vulnerability Management Software of 2022
Wise organization leaders understand that vulnerability management should be front and center in network security. In a nutshell, vulnerability management involves identifying, evaluating, remediating, and reporting weaknesses in network systems and infrastructure. But it is virtually impossible to perform all these actions manually, even with dedicated IT and security teams.
This is where vulnerability management software comes to the rescue. These tools help take the guesswork out of boosting network security and control, visibility and reporting, and operations by scanning networks for weaknesses. Then the software identifies all potential weaknesses, groups them in order of urgency, and even suggests fixes for known vulnerabilities.
However, you’ll be bombarded with options once you hit the market. Each software claims to be better and more advanced, making it hard to decide which one you should adopt. We’ve put together this review of the five best vulnerability management software currently on the market to make your job a little easier.
Rapid7 InsightVM – Best Software for Automating Vulnerability Management
Rapid7 has been in the technology business for over 20 years and released one of the early commercial vulnerability scanners known as Nexpose. For its part, Rapid7 InsightVM does everything you need a good vulnerability management software to do. The cloud-based platform automatically scans your local, containerized, virtual, cloud, and remote infrastructure to detect and assess vulnerabilities.
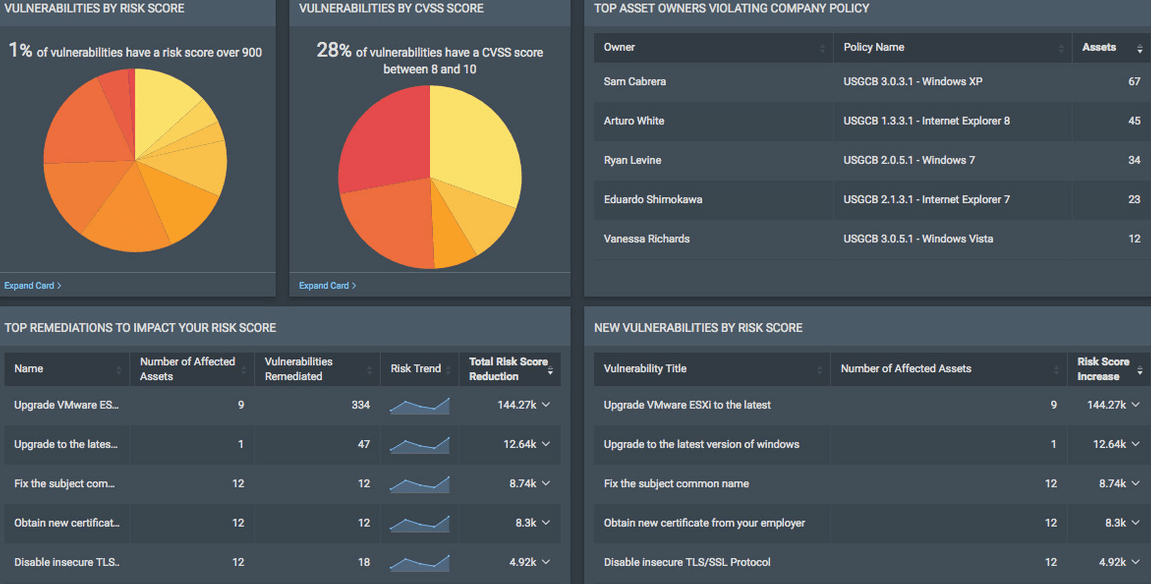
Mere vulnerability scanning is useless if you can’t act on the information. And this is where Rapid7 InsightVM truly shines. The platform provides tremendous value for security teams, including generating CVSS-based risk scores to help prioritize the most significant threats. The software even automatically generates tickets in ServiceNow or Jira based on its findings.
InsightVM is lightweight and isn’t too demanding on your network resources. The platform also shines with its automation features. For instance, admins can automate remediation steps and leave the software to collect vital information and retrieve solutions for known vulnerabilities. The software will even automatically patch weaknesses once approved by the system admin.
Similarly, InsightVM allows you to automate containment for vulnerabilities with no immediate solution. You can even automate asset discovery, including when an asset disappears and reappears on your network.
Rapid7 uses the software-as-a-service (SaaS) model to deliver this product. You pay $2.08 per asset per month for 250 assets. You also get volume-based discounts. For example, the price goes down to $1.84 per month per asset for 500 assets. This pricing model works well since you are guaranteed all of the software’s features regardless of how much you pay for the service. You also get a free trial of all its features.
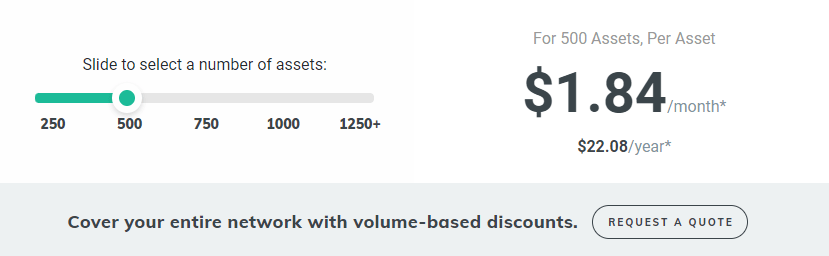
However, Rapid7 InsightVM has its downsides. The most glaring one is the lack of a unified dashboard. Admittedly, the software offers deep insights into your network vulnerability. But, these insights are spread out across multiple dashboards. For instance, you’ll need to toggle between dashboards to view Vulnerabilities by Severity and Newly Discovered Assets. It would be great to have all this information on a unified dashboard.
Otherwise, Rapid7 InsightVM is a terrific vulnerability management software, especially if you want to automate more repetitive vulnerability management tasks. It is also an excellent product for teams that require advanced reporting.
Tenable.io – Best Vulnerability Management Software for Enterprises
Tenable.io is an advanced vulnerability management software that allows you to monitor your entire attack surface. The software gives you visibility across all your assets, whether cloud, IT, or container-based. It uses a combination of active scanning, passive monitoring, cloud connectors, and agents to monitor your assets continuously.
The software also allows you to prioritize which vulnerabilities to address first. Here, Tenable.io relies on data science, threat intelligence, and exposure data to give you accurate risk ratings and scores. It covers more than 67,000 vulnerabilities to keep your network and systems safe. Furthermore, the platform’s dashboards are highly customizable and intuitive. These dashboards offer graphical summaries of system activity, scans, and scan results to improve your team’s Mean Time to Respond (MTTR).
The software is also notable for its advanced analytics. For example, analysis pages offer users deep insights into cyber exposure risk, known and unknown assets on the network, vulnerabilities, and even recommended solutions for identified vulnerabilities.
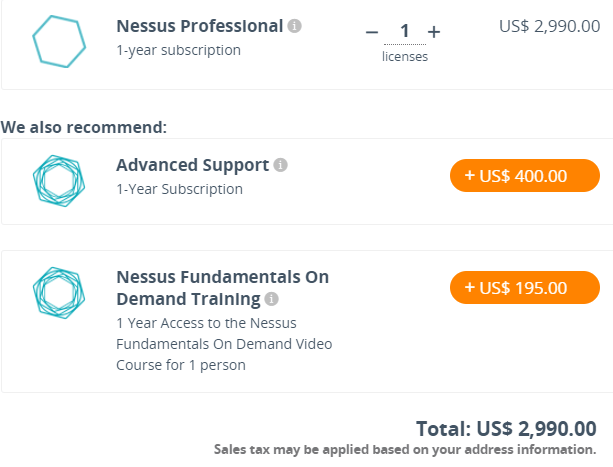
The software licenses start from $2,990 per year. You can also tack on extra features like advanced support and on-demand training at an additional cost.
The software features pre-built integrations that developers can use to automate scans, export scan results as a PDF, import third-party data, and much more. This flexibility is beneficial for enterprises looking to integrate Tenable.io into existing security infrastructure seamlessly.
This software isn’t without its faults. For one, this product targets enterprise users. It can be too cumbersome and expensive for small and medium-sized businesses despite being one of the best VMS out there. You also need to enter credentials every time you create a new scan, which can unnecessarily add input time.
Still, Teneble.io is exceptional software for enterprise users interested in CICD security features like container scanning. It’s also great for users looking for seamless integrations with existing cybersecurity infrastructure.
Qualys VMDR – Best All-in-One Vulnerability Management Software
Qualys VMDR is a robust software encompassing vulnerability management, detection, and response. The software runs vulnerability checks across your network, including cloud environments and virtual machines. More than that, Qualys VMDR also handles asset discovery, reporting, and patch management. So, you don’t need to maintain disparate tools to manage different aspects of the vulnerability lifecycle.
The software also boasts unrivaled accuracy. The tool claims it can detect vulnerabilities with 99.9% accuracy, making it an excellent tool for teams that hate dealing with constant false positives.
It is not always possible or practical to run active scans on your entire network. This is where the Qualys Cloud Agent steps in. Simply install the lightweight app in your systems, and it will run in the background. Then, the app updates the central Qualys platform with snapshots of new changes and information.
Qualys also offers useful automation features. For example, the software can generate and assign remediation tickets automatically as vulnerabilities are detected. You can even integrate the software with third-party ticketing systems if you prefer to maintain your current tool.
You can also generate custom reports on-demand or set an automatic schedule. These customized reports are convenient when briefing disparate teams, such as executives and security teams.
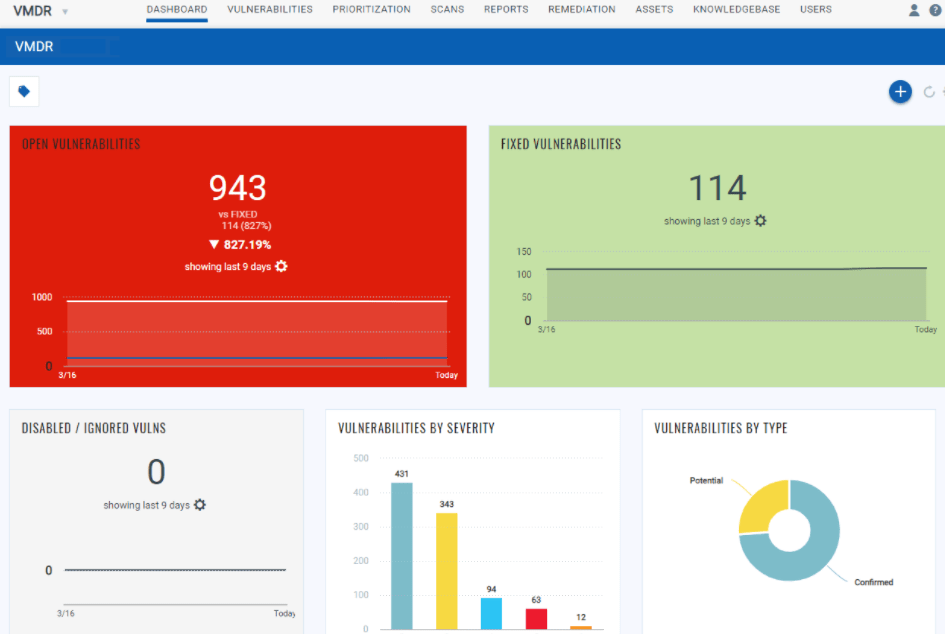
The dashboard is equally customizable. You can create multiple dashboards and toggle between them to view different asset information. Each dashboard also comes with widgets for the asset data you’d like to view. You even get a graphical host map to understand your vulnerability posture in real-time visually.
Qualys VDMR pricing depends on the number of user licenses, web applications, and IPs you choose. But prices start at $199 per asset. You also get a 60-day free trial.
The main downside is that Qualys VMDR doesn’t offer automatic patching for most vulnerabilities. Instead, there is a manual element to mitigation that enterprise users may find unnecessarily time-consuming.
Other than that, Qualys VMDR is an excellent tool for small to medium-sized business deploying their first vulnerability management software. It covers the entire vulnerability lifecycle, is affordable, and is easy to deploy and use. The cloud agent is also an excellent addition for SMEs without the network resource to handle continuous deep scans.
Tripwire IP360 – Best Software for Prioritizing Vulnerabilities
Vulnerability prioritization is a must-have feature for VMS. However, some software does this better than others. If your organization’s primary focus is prioritizing vulnerabilities, then Tripwire IP360 is the tool for the job.
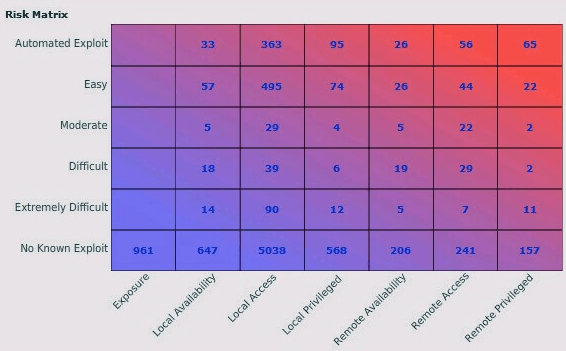
The software offers the standard CVSS-based vulnerability score for scanned assets. But, you also get a Tripwire score based on the software’s proprietary algorithm. This way, you are sure that you are first handling the most critical vulnerabilities. Furthermore, Tripwire IP360 offers comprehensive reports and suggestions for patching and remediation.
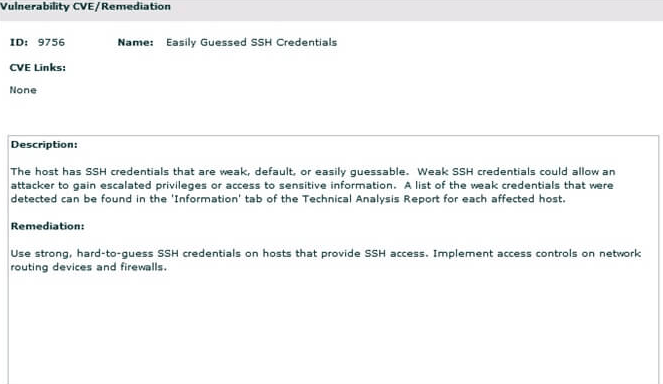
IP360 also has an impressive heat map feature that you don’t always get with these types of software. As a result, you get a clear overview of vulnerabilities with existing exploitations. The software also provides detailed reporting down to individual hosts and associated vulnerabilities.
The software also uses agent and agentless scans. So, you get complete visibility of your assets, whether cloud, on-premise, or container-based. This visibility also extends to previously undiscovered assets. You get plenty of flexibility when configuring scans. For example, you can set up automated scans based on scan types and schedules.
Tripwire IP360 offers custom pricing which is its major downside. It’s always good to know how much you’ll be paying upfront. This makes price-shopping easier. Nevertheless, Tripwire IP360 is an incredible tool for organizations most concerned with accurate vulnerability assessment, detailed remediation instructions, and efficient vulnerability prioritization.
GFI LanGuard – Best Feature-Rich Vulnerability Management Software
Most VMS appeal to novice users. But, more experienced security experts may want a robust tool with all the bells and whistles. GFI LanGuard answers the call by providing some of the most extensive vulnerability management features available on the market.
The software provides the essential functions you require for vulnerability management. These include automatically detecting assets and actively monitoring them for vulnerabilities. You also get a host of additional functionality, such as searching networks for missing patches and automatically deploying patches.
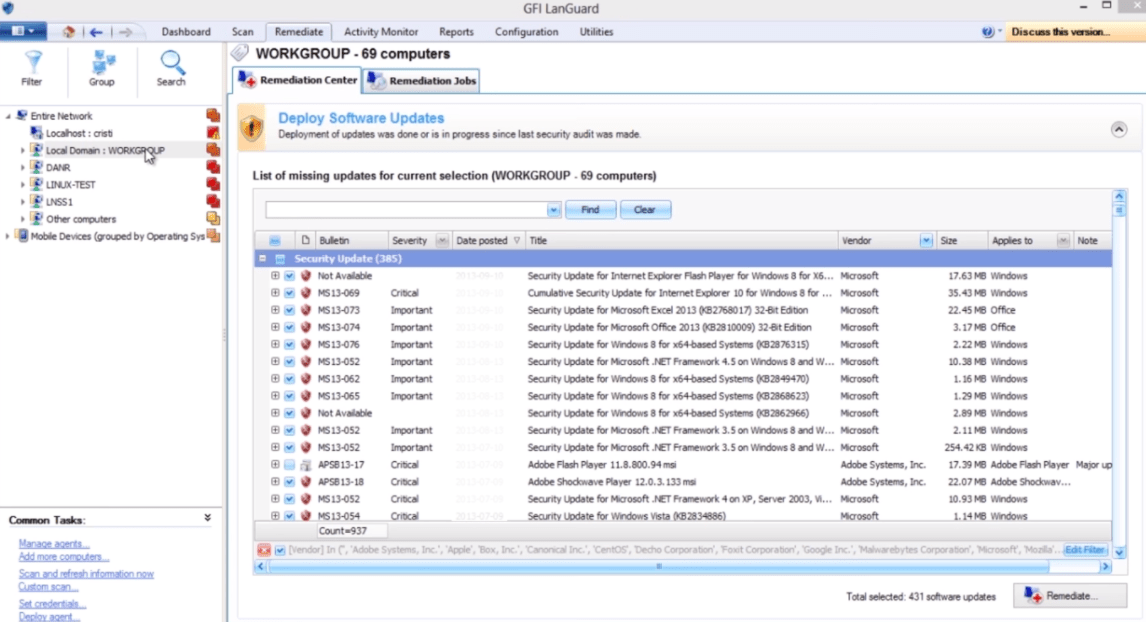
You can even deploy automatic patches for supported third-party applications, such as Mozilla Firefox, Adobe Flash Player, Java, and Apple QuickTime. In addition, GFI LanGuard allows you to roll back to previous states when deploying custom software and scripts on remote computers. This capability is invaluable in case there’s an issue with updates.
The software also allows you to manage vulnerabilities in the truest sense. You can group devices and even distribute management to various teams. All the while, you can monitor everything from a centralized dashboard. Moreover, you get equally valuable reporting. For instance, you can automatically generate compliance-related reports, including SOX, HIPPA, and PCI DSS requirements.
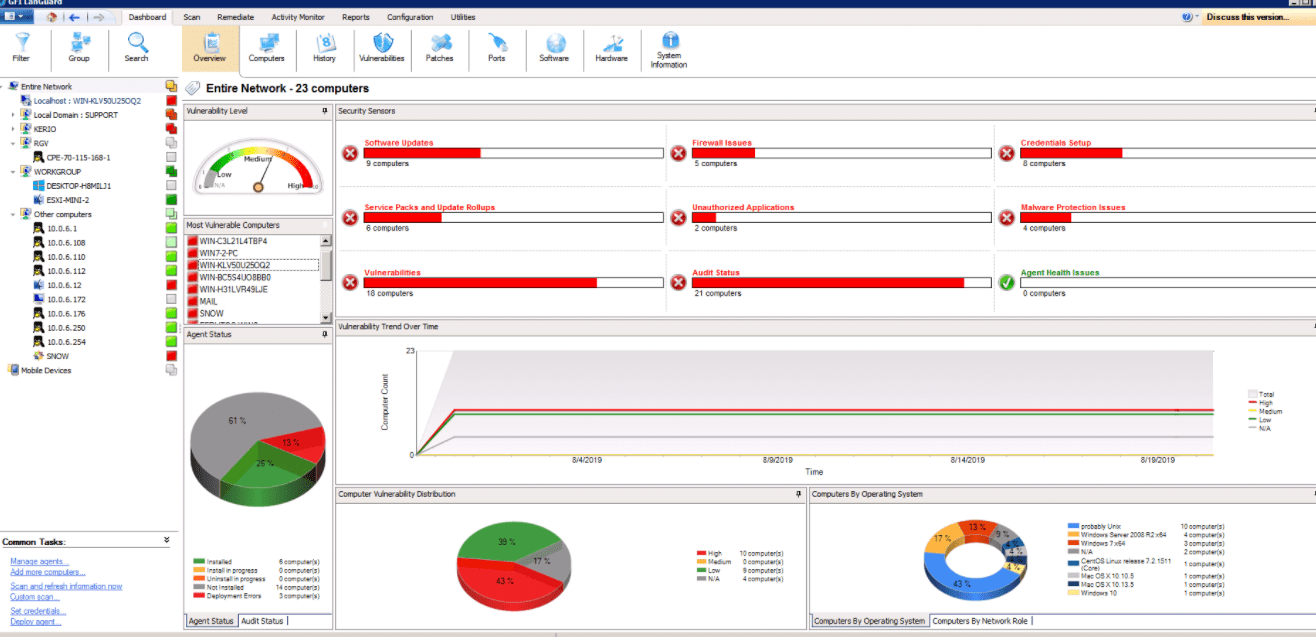
LanGuard also offers a premium package that includes GFI Unlimited. This option comes with additional components such as GFI MailEssentials, HelpDesk, Archiver, and Kerio Control. For instance, GFI Archiver lets you store, secure, and retrieve sensitive electronic communication, including email, file history, and calendar. On the other hand, Kerio Control is a unified threat management firewall with content filtering, bandwidth management, activity reporting, and intrusion prevention.

Finally, GFI LanGuard integrates seamlessly with more than 4,000 security applications, including a backup client, firewall, disk encryption, device access control, anti-phishing, anti-spyware, and antivirus.
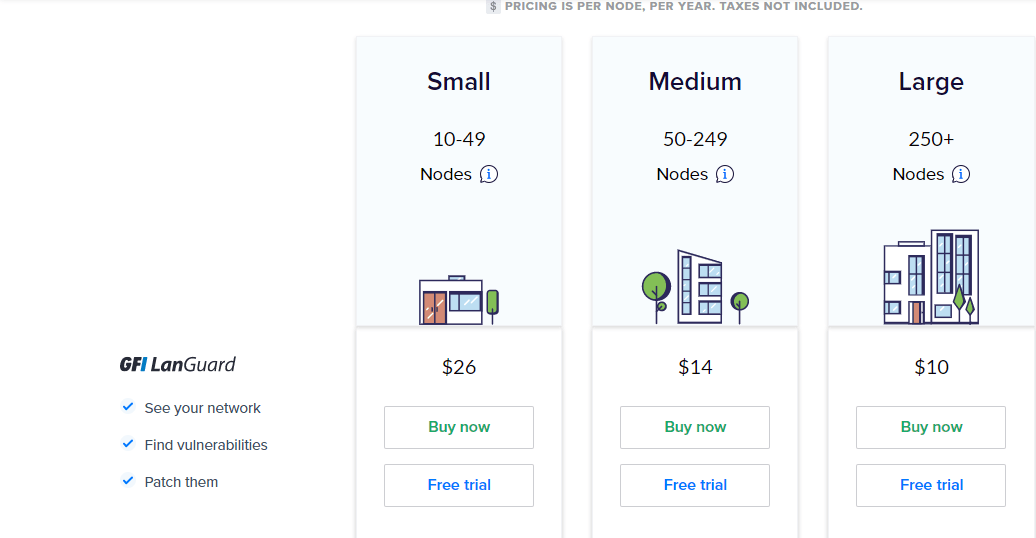
GFI LanGuard pricing depends on the number of nodes or assets covered. The packages include:
- Small – This option costs $26 per year per node for 10-49 nodes.
- Medium – Covers 50-249 nodes and costs $14 per node per year.
- Large – Scans 250+ nodes and costs $10 per node per year.
The most notable downside of this software is its hard-to-read on-screen formatting. Even so, GFI Languard outshines its competitors in patch management, automation, and in-depth reporting.
How to Pick Your Vulnerability Management Software
You’ll soon discover that there is no such thing as perfect vulnerability management software. Instead, each option has its strong suits and drawbacks. So, the idea is to match your organization’s needs to software that can satisfy them accurately. Work through the four steps below to select the right tool for your needs.
Step 1 – Assign Vulnerability Management Roles
It is often the case that vulnerability management software is underutilized. Plus, critical tasks can get passed around if there’s no clear structure. Such incidents can increase the average time to respond and leave your systems and infrastructure open to attack.
Ideally, you should have a team of people with specified roles. Of course, this team may look different for each organization. But some of the employees to consider for the positions include:
- Security officer: Responsible for designing and implementing the vulnerability management process.
- Vulnerability engineer: Tasked with configuring and setting up the vulnerability management software. They are also responsible for scheduling vulnerability scans.
- Asset owner: Takes charge of managing IT assets once they are scanned. The role may include delegating remediation tasks and following up on vulnerabilities.
- IT system engineer: Responsible for remediating identified vulnerabilities.
Again, the crucial part is assigning specific vulnerability management roles so everyone knows exactly what they should be doing. It is also good to inform the entire organization about your new measures. Rolling out the software may disrupt workflow, so getting employee buy-in before implementation is critical.
Step 2 – Decide Your Must-Have Vulnerability Management Features
Call a team meeting with your vulnerability management team. The main agenda is to discuss the areas you struggle with the most. Then, you can prioritize must-have features based on your known pitfalls.
For example, some organizations struggle with prioritizing threats. In this case, you’ll want software with advanced prioritization metrics and low false positives like Tenable.io. Other organizations struggle with poor structure within IT teams. A tool like GFI LanGuard that gives you granular control of categorizing assets and teams may be more suitable in this instance.
As a rule of thumb, the software should cover the entire vulnerability management lifecycle, including:
- Assessing your assets
- Prioritizing vulnerabilities
- Remediation
- Reassessing remediation actions
- Documentation and reporting
All the products featured in this review capture the entire lifecycle. We’ve also identified each software’s best use case for your convenience. After prioritizing your must-have features, you’ll have a clearer picture of the best software for your needs.
Step 3 – Sign Up For a Free Trial
You should have identified at least two prospective VMS by now. And most of this software comes with a free trial. So sign up for at least two options and test them independently for a month or more. Some of the things to look out for during the trial period include:
- Contextual insight – Exposing vulnerabilities in your system is well and good. But, the data can be overwhelming, especially when conducting your first vulnerability assessment. Good software will contextualize the data for you, including the likelihood of a vulnerability being exploited and its potential impact. Also, consider if the data is easily digestible, such as using heat maps and other visual tools.
- Collaboration with the existing IT environment – You probably have current software stacks such as third-party scanners and asset management databases. These tools aren’t always obsolete once you start using vulnerability management software. For example, you may want to retain your ticketing system, such as JIRA. Observe how well the VMS works with your existing environment and infrastructure before making the final purchase decision.
- Centralized risk management – Good software will allow you to manage your entire IT environment on a unified interface. For example, can you easily monitor remote, private and public cloud, and on-site assets from one dashboard?
Get a good feel of the software, its features and functionality, and its accuracy before purchasing the license. Then, finally, choose the software that makes the most sense for your organization.
Step 4 – Train Your Core Vulnerability Management Team
Be sure to train your core team on vulnerability management software best practices. The software already comes with documentation, so ensure that the team is briefed and prepared appropriately. Some software providers offer formal training for their products. This way, they’ll be able to make the most of the software.
Lastly, vulnerability management extends beyond the core team. Everyone with computer access at your organization should play a role in protecting your systems and infrastructure. It’s worth considering enrolling in a comprehensive data security program for all your employees.

