What AWS Cloud Security Gives You (And What it Doesn’t)
Amazon Web Services (AWS) is the most used cloud infrastructure service provider today, with a larger market share than Microsoft Azure and Google Cloud combined.
The inherent availability of cloud infrastructure is convenient, but it comes with the potential for exploitation via cyberattack. AWS security is trusted by the highest-sensitivity organizations, like global banks, the U.S. military, and the Central Intelligence Agency.
So what makes AWS security so good?
In short: experience, resources, and the legendary Amazon drive to provide customers with everything they want and more. No other provider has as deep a set of tools as for keeping cloud assets secure.
As with other IaaS solutions, AWS customers are responsible for protecting what they store and build in the cloud. In this post, I’ll distinguish what Amazon provides from user responsibilities, and close with a list of AWS security best practices for hardening your environment.
AWS cloud security overview

AWS is composed of 175 feature-rich services—compute, storage, database, etc.—which provide customers with a unified and seamless set of customized web service solutions.
AWS security runs on a shared responsibility model. As the company describes in a recent AWS security whitepaper:
“AWS is responsible for securing the underlying infrastructure that supports the cloud, and you’re responsible for anything you put on the cloud or connect to the cloud.”
The goal is to maximize the control you have over your cloud infrastructure, while minimizing the operational overhead of securing it. Here’s a visualization that breaks down the shared responsibilities of AWS security:
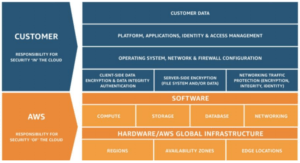
Understanding what AWS provides and what you are on the hook for is an important part of keeping your workloads and data safe in the cloud.
Let’s go through them one at a time.
AWS security: What’s available out of the box
Responsible for the security “of” the cloud, AWS maintains a state of the art global infrastructure. Every aspect of their data center’s physical and environmental security has been honed by years of experience. Access is tightly controlled, power systems are fully redundant, and all of the equipment is state of the art.
AWS data centers are built in clusters in different geographic regions. This gives customers the ability to keep instances and data within multiple regions, and in different availability zones within regions.
Within a single city, for example, a company could have instances in several availability zones, each of which relies on a data center that is fed by multiple power sources and backed by a generator.
By distributing workloads, customers can ensure continuity even when natural disasters, power outages, or other unforeseen system failures occur.
The AWS network infrastructure is extensively monitored 24/7/365. All of the software that supports AWS is updated routinely to ensure that the services they offer are secured against the latest threats.
Before you start building the next great application, however, you’ll want to take care of things on your end.
AWS security: What you should expect to do on your own
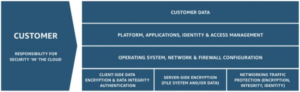
Responsible for security “in” the cloud, customers need to ensure that nothing they store or build on top of AWS leaves an open door to threats. With so many different services, each with their own security challenges, the task of protecting your AWS account is no small job.
Over the years, however, AWS has constantly improved, simplified, and streamlined the UI of their cloud security services based on customer feedback.
Today, users have access to more than 200 security, compliance, and governance tools that help people fortify and monitor their cloud assets. AWS Security Hub, for instance, provides a centralized view of performance and threats across all services.
The specific tools you use will depend on the cloud services you need, but regardless of what you choose, every account comes with core AWS security tools:
AWS credentials prevent unauthorized access to your account and resources. There are several types used by AWS to provide multiple layers of security. These include:
- Access keys
- Key pairs
- Multi-factor authentication (MFA)
- Passwords
- X.509 Certificates
AWS CloudTrail provides an event history of account activity that enables compliance, governance, risk auditing, and security analysis. You can record and store event logs of API calls, actions taken through command line tools, the AWS Management Console, software development kits (SDKs), and other services.
AWS Config continuously monitors and records changes to your resource configurations in order to make sure they are efficient, secure, up to date, and compliant. You can define the policies for your environment, receive notifications when resources deviate, and remediate vulnerabilities quickly.
AWS Identity and Access Management (IAM) provides centralized and comprehensive control over which users can access which resources and services.
AWS Trusted Advisor is a support service that helps you optimize your environment for performance, resilience, and security. It analyzes the environment and provides recommendations to help you close gaps in security.
As you add more tools and services, the burden of your shared responsibilities will grow. There are many advanced AWS security services available to make this task easier.

The services you need now may change by next year. You should constantly reassess the AWS resources you are using, how they are deployed, and find opportunities to make them more secure.
There may be no better platform to scale a web service on than AWS, but without attention to security, you risk catastrophe.
Best practices for securing AWS yourself
Security is one of the Five Pillars of the AWS Well-Architected Framework, a guide the company created to help businesses apply best practices for using their cloud infrastructure.
To keep workloads safe, AWS identifies seven design principles you should follow:
- Implement a strong identity foundation
- Enable traceability
- Apply security at all layers
- Automate security best practices
- Protect data in transit and at rest
- Keep people away from data
- Prepare for security events
Pursuing each of these principles is an ongoing task, as the threat landscape is always changing.
AWS is always improving the services that help you optimize your security posture. Under the shared responsibility model, you are in charge of making sure these resources are leveraged intelligently and consistently.
Here’s how to start applying AWS security best practices in accordance with each design principle:
- Implement a strong identity foundation
- Ensure users create strong passwords, and change them often, without re-using them.
- Download credential reports to monitor status of passwords, keys, and MFA devices.
- Grant permissions according to the principle of least privilege.
- Define permission sets based on groups and roles, rather than individuals.
- Use AWS permission boundaries to create delegated administrators with the freedom to create specific users and roles.
- Use temporary credentials instead of access keys.
- Enable identity federation to streamline and secure user access in AWS. Here’s how to automate the federation setup.
- Delete unused access keys and credentials. AWS credential files are the target of a recent cryptojacking campaign.
- Enable traceability
- Configure service and application logging with AWS CloudTrail, AWS Config, AWS GuardDuty, VPC Flow Logs, and others.
- Configure AWS Security Hub to aggregate and organize relevant findings.
- Receive security alerts via chat, not just email, to increase visibility.
- In light of threat modeling, attacks, and the latest threat intelligence, continually review the quality of the data you are logging, and your ability to analyze it quickly.
- Apply security at all layers
- Data classification is foundational for security.
- Segment resources into subnets based on routing requirements, i.e. use public subnets for external-facing resources, and private for internal.
- Use network ACLs as firewalls at the subnet level
- AWS services that don’t need internet access shouldn’t have it. For those that do, consider AWS WAF, a web application firewall, or a NAT gateway for instances with outbound traffic only.
- Consider AWS Transit Gateway for large, hybrid networks to maximize the traffic that remains on AWS private network.
- Protect security logs, which may contain sensitive information, by deleting unneeded data or storing it securely.
- Use Amazon Inspector to assess the applications you deploy on AWS.
- Automate security best practices
- Use AWS CloudFormation to automate detective controls in AWS CloudTrail, AWS Config, and AWS GuardDuty.
- Integrate the flow of security events from into a SEIM system or ticketing system.
- Set AWS Config rules to detect non-compliant configurations, and automate remediation based on rules.
- Protect data in transit and at rest
- Set default encryption protocols for all of your data at rest using AWS Key Management System for centralized management.
- HTTPS should be used instead of HTTP for data transmissions. All AWS services allow you to enable secure HTTPS communication, which uses TLS/SSL to encrypt HTTP requests and responses to prevent eavesdropping.
- Use AWS Certificate Manager to oversee TLS certificates you deploy.
- Automate detection of unusual activity recorded by AWS GuardDuty or VPC Flog Logs to receive alerts when data is being wrongfully altered, deleted, or moved.
- Keep people away from data
- Encrypt, mask, and tokenize sensitive data, isolating it in separate AWS accounts according to its security needs.
- Configure systems and permissions so that direct access to data is prohibited for all but select users. This involves different for each service, but you can streamline the process by using AWS Organizations.
- Use Amazon QuickSight to create business intelligence dashboards for business users or for internal use. That way, people can interact with the data without risk of corrupting it.
- Prepare for security events
- Link detection mechanisms with established processes to investigate and remediate issues once they have been flagged. Make these solutions safe to execute repeatedly.
- Continually engage in threat modeling and simulated game days in order to evaluate your ability to detect and respond to threats.
- Establish processes to quickly distinguish “insider” threats. These could be an accidental mistake caused by an employee that appears as an attack, or a disgruntled client planting a backdoor on their way out.
- Distribute data and instances across multiple availability zones to prevent single-point failure.
- Educate all AWS users about the threats posed by a lax security posture, even on the part of an individual.
It’s important, too, to stay up to date with AWS recommendations and threat intelligence. Their managed services update routinely, but you may need to take action within your account in order to stay protected from emerging threats.
Other ways to repel attacks include implementing up-to-date endpoint security software, taking steps to prevent social engineering, and keeping employees on guard for potential threats.
One way to beef up security is to invest in certifications, such as the AWS Certified Security Specialty, in order to upskill employees. There are also vendor-agnostic cloud security certifications that may be of value.
There is no perfect path toward total AWS security, but by following best practices and looking to harden your environment everyday, you will be as prepared as possible.

