The Complete Guide to Oracle Cloud Security
Spinning up and spinning down infrastructure is wildly easy today. Securing it is not.
The truth is that most companies today are operating with unknown cloud vulnerabilities. Over the next five years, 99 percent of cloud security failures will be the customers fault, according to Gartner.
Oracle Cloud Security provides the tools for companies to create, control, and protect the most complex enterprise IT environments. The suite enables multiple layers of defense at each level of your stack: from bare metal cloud to APIs on edge devices.
With Oracle Cloud Security, you can lock down your entire environment and make sure that users are prevented from doing anything that would jeopardize network integrity.
It doesn’t matter where they are or what device they’re on—Oracle Cloud Security allows employees and customers to access exactly what they need, and nothing else.
Overview of Oracle Cloud Security
Like all cloud service providers, Oracle Cloud Security is based on a shared responsibility model. Customers can build and share whatever they want in the cloud, but they are responsible for making sure it is secure.
In other words, Oracle provides tools that are safe to use, and customers are in charge of using them safely.
The customer’s responsibility varies according to the amount of control they have in each service.
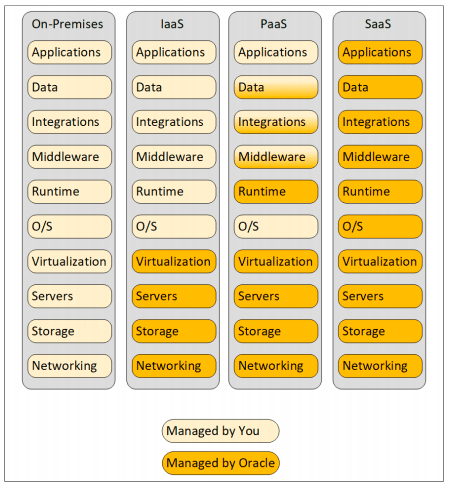
In the cloud, Oracle is responsible for the underlying infrastructure up to the virtualization layer. For PaaS and SaaS services, Oracle manages upper layers, as the customer requires less control.
First, we’ll look at how the design of Oracle’s second-generation cloud infrastructure keeps customers safe by default. Then, we’ll look at the suite of tools that come with Oracle Cloud Security and how they help customers harden their entire perimeter.
Oracle Cloud Security Architecture
Oracle has complete control over how their infrastructure is designed: hardware, firmware, and software. They saw how early iterations of shared-tenancy in the public cloud had serious vulnerabilities and developed something better.
Customers love the lower price of sharing space on the same infrastructure. But in much of today’s public cloud, hackers can still find ways to move laterally, breaching the virtual barriers that are supposed to protect the different tenants. Sensitive data is stolen, held for ransom, or worse.
In a 2020 report, the National Security Agency detailed several attacks where the hypervisor was compromised, putting all tenants on the same host at high risk.
To protect against these and other novel types of attacks, Oracle Cloud Security begins on a second-generation foundation: isolated network virtualization.
Instead of letting the hypervisor handle server and network virtualization, this responsibility is kicked down to a highly customized hardware and software layer:
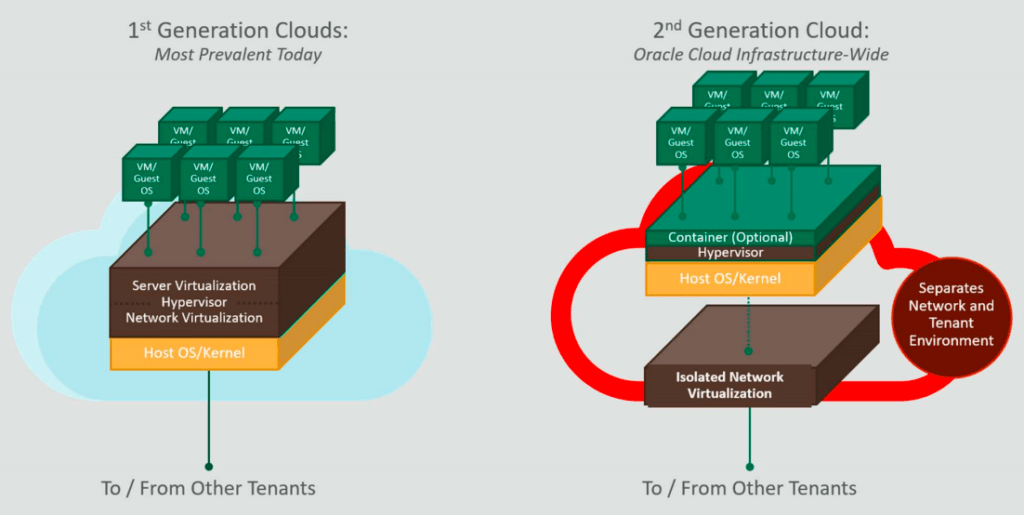
Should an attack successfully gain access to one VM instance, they would be unable to “break out” and threaten the assets of other tenants.
Isolated network virtualization is default across Oracle Cloud Infrastructure. Should a business require further isolation, Oracle offers bare metal cloud.
The data centers and physical networks that support the second-gen cloud are, of course, incredibly secure and state of the art. Oracle has been trusted by governments, banks, and telecommunications companies for decades, because their technology consistently outpaces that of bad actors.
Firmware attacks, for example, are becoming increasingly common. With Oracle Cloud Security, a hardware root of trust returns all servers to their factory state every time they are provisioned to ensure that no malicious firmware is left behind.
Another nice capability is Oracle Autonomous Linux. This automates the process of patching vulnerabilities to operating systems installed on IaaS resources. Given that something like one in three breaches are caused by unpatched vulnerabilities, this time-saving service can be a huge boost to security.
Oracle Cloud Security Features
From this firm foundation, customers can safely scale out any type of cloud deployment.
Oracle’s security portfolio is thick with solutions for data protection, identity and access management, secure configuration, and threat prevention. No matter how much there is to oversee, Oracle Cloud Security provides control from a single pane of glass via three interrelated tools:
- Oracle Cloud Guard
- Oracle Maximum Security Zones
- Oracle Security Advisor
Oracle Cloud Guard
Oracle Cloud Guard is the central hub for security operations across your entire environment. The interface is clean, easy to navigate, and delivers real time information about your overall security posture.
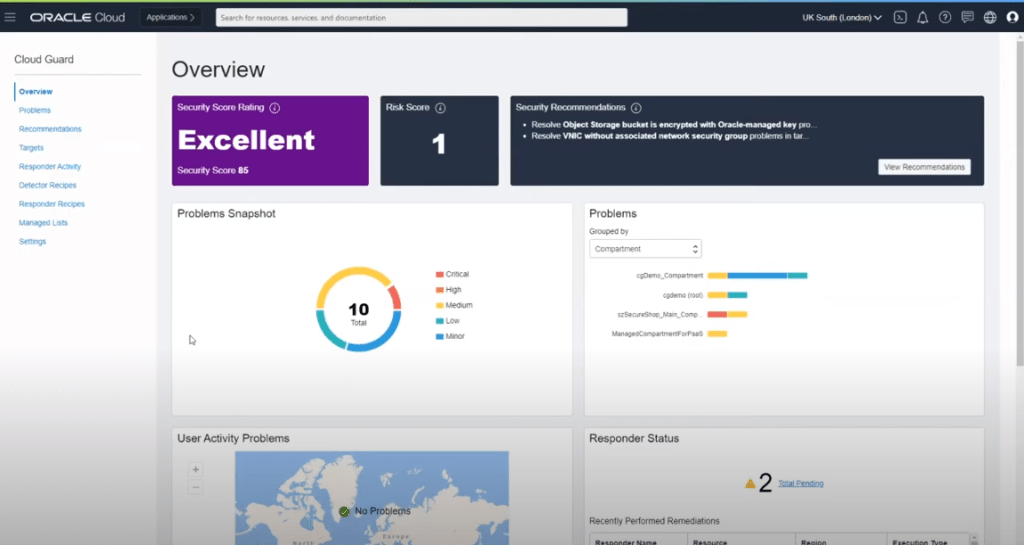
On the main dashboard, Cloud Guard displays prominent scores for your security and risk, which is based on data culled from all of your infrastructure services. Essentially, it aggregates logs and events from compute, networking, storage, and assesses them for potential security threats. These are then translated into clear security and risk scores.
IT administrators using Cloud Guard can see exactly how the scores were derived, as well as a prioritized list of actionable security recommendations. There are simple tools to set up automated remediation for many of the vulnerabilities you detect. You can also use the CLI, APIs, and SDKs within the console to capture and act on customized events.
It’s an excellent balance of built-in and customizable functionality that improves visibility and simplifies security tooling.
Oracle Maximum Security Zones
Resources in Oracle are divided into regions by the company based on the location of data centers. Regional resources are divided into compartments and subcompartments by the customer.
Using Security Zones, customers can ensure that all resources within a specific compartment (compute, database, networking, object storage, etc.) are compliant with security best practices.
Security Zones are based on recipes, which are collections of policies that prevent users from unintentionally creating security vulnerabilities, such as public buckets or misconfigurations.
Currently, there is a Maximum Security Zone, which is pre-configured by Oracle and cannot be changed. They have plans to offer other tiers of Security Zones in the future.
Oracle Security Advisor
Once Cloud Guard or Security Zones detect an issue, Oracle Security Advisor walks customers through the changes they need to make. What’s nice about this capability is that it can help users and administrators alike.
Security Advisor works within the Cloud Guard Console to guide admins in addressing misconfigurations, analyzing suspicious network activity, and enforcing strong identity and access management.
It also provides this service to users who are trying to work within Maximum Security Zones or other areas with strict policies. In the demo example below, a user was prevented from creating a bucket without a customer-managed encryption key.
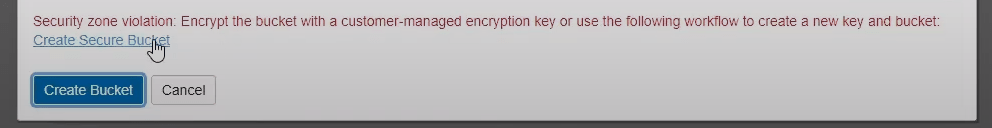
Instead of having to reach out to IT or their manager, they can click the link, which puts them in a set-up wizard. Security Advisor then guides the person, step-by-step, through accomplishing their goals in a secure fashion:
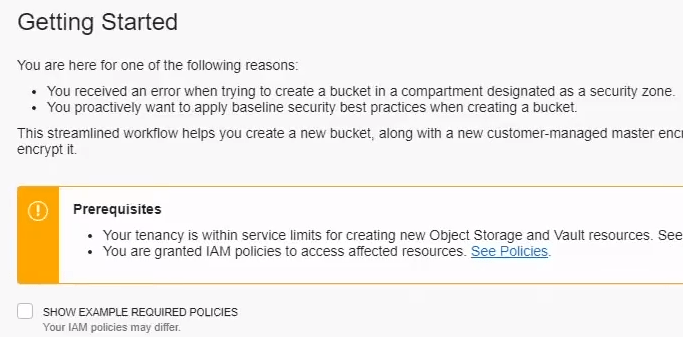
Security Advisor explains what went wrong and why it needs to be fixed. This streamlines the process of hardening your environment, and helps users learn best practices.
Along with Security Zones and Security Advisor, Cloud Guard ties into all of the other foundational Oracle Cloud Security services, which include:
Oracle CASB
Oracle Cloud Access Security Broker (CASB) provides complete visibility into cloud application use across the company. This includes SaaS, products from app-marketplaces, and services installed on top of PaaS and IaaS.
Beyond discovering shadow IT and helping you manage it, Oracle CASB monitors activity, configurations, and transactions across your cloud app environment to identify suspicious behavior.
Oracle Cloud Infrastructure IAM
Oracle Cloud Infrastructure Identity and Access Management (IAM) gives complete oversight of user activity and resource use. Only users or groups with privileges can access cloud assets, and you can control the type of authentication required for different types of resources.
Oracle’s IAM works across all of your cloud services, as well as other IdPs to enhance existing security.
Oracle Data Safe
Oracle Data Safe is a free service that centralizes control of all your Oracle Databases into a single cloud-based console. From there, non-specialists can employ administrative, data-driven, detective, and preventive controls.
This makes data classification and compliance, which is always the customer’s responsibility, much easier to get right.
Oracle WAF
Their web application firewall heads off many types of cyberattacks, and helps you identify bot traffic. It’s Payment Card Industry compliant, and works for enterprises with global, multi-cloud deployments and other hybrid cloud security concerns.
What differentiates Oracle from other cloud security solutions?
Mature tools run the risk of sprawling for the obvious reason that they have to solve more problems every year. In the case of cloud security, new problems emerge every day.
The result is that IT teams are overwhelmed precisely because the detection tools have become so sensitive and the policy rules are so highly configurable.
In the words of Paul Toal, a cybersecurity solution engineer with Oracle, “it is not good enough to build the latest and greatest security software alone. It must be easy to use.”
Powerful tools can quickly become unmanageable, leaving teams with less visibility than they had before. Toal continues:
“As vendors, we must take the burden away from IT Security teams and users of security tools, so that a company’s security posture is more secure by default, problems are identified and fixed automatically, and there are a smaller number of usable tools, not hundreds of different, siloed, complex ones.”
Oracle has been helping companies move to the cloud for as long as there has been a cloud. They understand the realistic long-term dangers of a bloated cybersecurity apparatus. Cloud Guard and Security Zones drastically reduce the number of tools in play without sacrificing visibility.
It’s a step in the right direction, and it is only possible because Oracle has built their cloud from the servers up through application-layer protections. Without the native integration of all the moving parts, customers would be back to relying on an ever-changing slew of third-party fixes.
The other major differentiator between Oracle and the major cloud players is that they haven’t really expanded their buyer persona. Though companies of all sizes are taking advantage of the cloud, Oracle continues to focus on security solutions with enterprise needs and problems in mind.
They don’t have as many tools as AWS Security, for example, but those they offer are deep enough to satisfy the most complex regulatory and compliance requirements.
Oracle CASB, for instance, provides a complete audit trail. Even across unmanaged devices, security teams can quickly trace attacks to the source.
For a large enough company, it may actually cost less to implement a simpler, more secure system via Oracle than would be possible with AWS.
Partnering with a cloud service provider is best when both parties get what they want. At this point, Oracle knows who benefits from their products and will buy-in for the long haul.
Who should consider Oracle Cloud Security?
If you have the need for on-premises or hybrid cloud security, Oracle is an extremely dependable option moving forward. This is especially true of companies that have experience maintaining their own infrastructure. Oracle will help you do exactly what you need to do with fewer tools to manage.
For smaller businesses looking to grow, Oracle might be a good long-term investment. Their enterprise-grade technology can give SMB clients the functionality they need to streamline security operations.
Oracle Autonomous Database, for example, simplifies database management and protection. The self-driving, self-securing, self-repairing databases dramatically reduce IT overhead and provide deep analytic insight.
For large companies, especially those with global compliance concerns, Oracle Cloud Security should be on your shortlist. With a relatively trim suite of tools, you can completely manage cybersecurity across branch offices, stay compliant in different countries, and keep data safe no matter where it travels.

