What is Hybrid Cloud Security?
Many companies today are using a mix of on-premises, private cloud, and public cloud resources. This allows them to access the best parts of all of these deployments: the security of on-premises, single tenancy of private cloud, and on-demand scalability of public cloud.
With a hybrid deployment, companies can reap the benefits of cloud computing without having to sacrifice the control.
But by spreading their resources between different environments (each of which require different protections) they’ve increased their attack surface and potentially introduced unknown vulnerabilities.
In order to make every part of their digital workplace safe for business, organizations need a robust hybrid cloud security strategy.
What is hybrid cloud security?
The first part of defining hybrid cloud security lies in defining hybrid cloud.
Traditionally, we think of a hybrid cloud as being made up of at least two of the following:
- A public cloud environment (AWS, Microsoft Azure, Google Cloud, etc.)
- A private cloud environment (on-premises, or hosted third-party)
The goals of using hybrid cloud is to leverage the benefits of both types of environments.
With public cloud infrastructure, companies rely on the cloud service provider for the hardware and underlying service fabric, which they share with other tenants, saving on IT overhead as they scale. Companies provision the resources they need on-demand, pay for what they use, and don’t have to worry about replacing hardware.
Private cloud infrastructure is dedicated to a single company, and may be hosted on premises or in a third-party data center. Companies have a greater degree of control over private cloud resources than with public cloud, making it ideal or necessary for companies with strict compliance requirements (government, healthcare, finance, and so on).
Under a hybrid cloud model, companies can store business-critical cloud assets in their private cloud, while taking advantage of the seamless scaling public cloud affords. They can avoid sudden, massive outlays to handle spikes in traffic, while keeping their most sensitive workloads completely private.
Key elements of hybrid cloud security
Companies that leverage both private and public cloud resources enjoy greater flexibility, but it comes with a larger attack surface. This includes the combined vulnerabilities of each different deployment, as well as novel security issues that come from their connection.
Any hybrid cloud security solution has to address:
- On-premises: You need staff to build, maintain, and monitor all of the hardware, firmware, and software that undergird your company’s on-site infrastructure.
- Private cloud: You need people working with a third-party data center to ensure that all of your cloud assets are safe.
- Public cloud: You will need in-house staff who understand how to leverage the security features CSPs provide, as well as the knowledge to employ additional tools as necessary.
- Endpoints: You will need to secure all of the devices that connect to your network, whether employees are bringing their own laptop, phones, tablets, etc.
- Applications: You will want a CASB to discover and sanction the thousands of SaaS apps your users access.
While it might seem like hybrid cloud security comes with extra headaches, if it’s thoughtfully implemented and managed well, the end result can be far more secure than a strictly on-prem or strictly cloud deployment.
Benefits of Hybrid Cloud Security over Cloud Security
Private and public clouds have different strengths and weaknesses. By being deliberate about how you architect your hybrid cloud, you leverage the traits of each environment to increase the security of your entire perimeter.
The exact setup will be unique to every company, but there are some fundamental ways to employ hybrid cloud security that are simply impossible with just cloud security. These include:
- Cloud bursting: Securely move private cloud apps to a public cloud deployment in response to usage spikes or increased demand.
- DR/COOP: Companies can leverage hybrid cloud for disaster recovery and continuity of operations by backing up on-prem assets in the cloud, providing redundancy and availability only a large CSP could provide.
- Edge security: Use multiple layers of on-prem and cloud network defenses to protect IoT and smart manufacturing devices.
- Minimize migrations: Avoid the huge costs and potential data leakage of massive cloud migrations by going hybrid. Keep your data and workloads safe with proven systems if you like, instead of having to move everything to the cloud.
- Scaling securely: Complement the on-demand availability of public and private clouds with the security of on-prem. Customize virtual and hardware firewalls to fit your organization’s specific needs and monitor all network traffic.
- Securely segment cloud resources: Allow remote users access to on-prem resources instead of having to migrate everything to the cloud. Allow developers to use private cloud for production, and public cloud for development and testing.
Downsides of Hybrid Cloud Security
Securing a hybrid cloud deployment is difficult for the common sense reason that you are on the hook for managing at least two separate environments that have different vulnerabilities.
On-prem IT requires dedicated staff and continuous capital expenditures to maintain. Keeping it secure is entirely on the company. It’s a lot of work, and of course no one wants manual maintenance done during business hours, so how dedicated is that IT staff?
Then you also have to address the security issues that come with working in a public cloud environment. AWS Security, Azure Security, and Google Cloud Security are all tremendous, but customers retain certain key security responsibilities. These require in-house staff that understand each service and how to make sure it is working as intended.
There are also the second-order problems created by the connection of these different environments. Moving information and applications between private and public clouds creates opportunities for attackers and accidents.
The daily movement of data between environments is a lot to manage safely, and cloud migrations for companies with big data are known for being complex and expensive.
If it sounds like a lot to manage, it is.
Done right, however, you can leverage the different characteristics of on-prem and cloud environments to improve one another.
In other words, the key to hybrid cloud security is to utilize the strengths of each environment to cancel out the cons of others.
Here’s how to get started.
4 Best Practices for Hybrid Cloud Security
1. Don’t rush to the cloud
Anyone with a credit card can spin up a massive amount of cloud infrastructure. If it’s architected poorly, disaster lies ahead.
Take time to build a proper foundation. Make sure those in charge of setting up cloud environments know how to use the built-in audit, governance, and security capabilities from day one. They need to understand how cloud security differs from on-premise security, and have a plan to execute strategies for both.
Don’t believe the hype about “seamless” or “effortless” migrations, even if you are only moving partial operations to the cloud. There is going to be a tremendous amount of work on your end, no matter what.
Vendors like AWS, for example, have done a lot to help make these transitions easier, but at the end of the day, the design and maintenance of these environments is on the customer. They’ve laid out how to secure the cloud according to the AWS Well-Architected Framework. It’s up to you to enact these principles according to your specific needs.
2. Understand shared responsibility for security
In order to safely use public cloud resources, especially if you are linking them to your on-premise infrastructure, you need to understand all relevant shared responsibility models.
Looking at IBM, for example, you can see that the level of responsibility generally varies with each type of service:
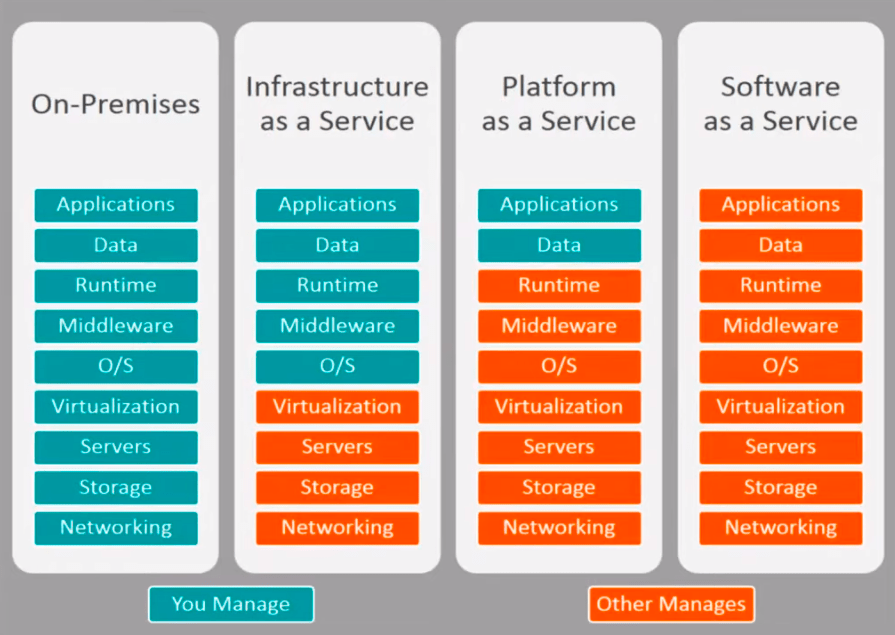
It’s critical to understand where the vendor’s responsibility ends and your begins. Many vendors provide tools and services to help you secure each layer. IBM Cloud Security can completely outfit an organization with everything they need, but it won’t be free.
Ensure that you have the tools to provide security across all of your environments. Because hybrid cloud security typically involves on-premises resources, you should have systems in place to protect bare metal on up.
3. Centralize cybersecurity ops
This is best practice, regardless of whether you are cloud, multi-cloud, or hybrid.
Your IT security team needs to have complete and legible information about everything that is happening. Even a small business has thousands of network events each day. For a large organization, this number jumps into the millions.
Be sure to leverage tools like Azure Security Center, which do a lot of the aggregation and analysis for you. At the same time, Azure Security Center may only cover your Azure deployments, and hybrid cloud security requires coverage for all of your public cloud and on-prem resources.
You may need additional tools to cover your entire perimeter, but you still want to be able to identify and address issues from a single console.
The best cloud security companies offer tools that centralize oversight across complex organizations. They tie into all of your services, on-premise or cloud, and deliver reports on key metrics, as well as high-fidelity, prioritized alerts about potentially dangerous activities.
4. Continually monitor and improve security posture
Once you have a centralized console to manage cybersecurity operations, you need to ensure that it is monitored 24/7/365. Much of the legwork can be accomplished through automation, but you will want to continually assess the performance of your hybrid cloud security.
Consider gamedays, penetration testing, faux-phishing attacks and other techniques to test each layer of your security.
As with any deployment, the human layer of your security is likely the most vulnerable. Make sure that employees understand the importance of identity and access management, as well as their role in ensuring the health of the overall IT ecosystem.

