Top Cybersecurity Companies of 2022
Cyber events have been growing in number and magnitude. Most companies, including large enterprises, do not have the IT staffing to guarantee protection against imminent cyber threats. Even with sufficient IT staff, cyber threats are becoming increasingly sophisticated and harder to spot.
For this reason, many businesses choose to outsource part or most of their cybersecurity needs. These companies have proved instrumental in securing businesses against common threats, including malware, phishing attacks, brute-force attacks, social engineering, and human error. In addition, cybersecurity companies invest heavily in cutting-edge technology to secure critical data, allowing businesses to expand their digital presence safely.
Cybersecurity is a broad niche, with crucial sub-sectors dedicated to important countermeasures such as threat intelligence, digital forensics and incident response, and endpoint protection. This porous landscape makes it challenging to identify specific security companies to outsource. This review looks at the six best cybersecurity companies of 2022, including their areas of expertise.
McAfee Corp.
McAfee Corp, formerly known as McAfee Associates, was founded in 1987. McAfee initially focused on client-based antivirus software. But, its offerings increased dramatically following the acquisition of the Canadian company FSA Corporation. As a result, McAfee’s product lines grew to include public key infrastructure, file encryption, and firewall cybersecurity products.
Today, McAfee has a vast cybersecurity product and services portfolio, spanning:
- Network Security
- Cloud Security
- Database Security
- Data Protection
- Endpoint protection
- Security Analytics
- Web Security
- Server Security
- Security Management
- SIEM
- Data Protection
McAfee has a market cap of $4.79 billion in 2022. One of the company’s most popular products is the McAfee Total Protection. The premium antivirus software has advanced cybersecurity features, including a personal firewall, cryptocurrency protection, safe web browsing, ID protection, and VPN. The product costs $104.99 per year.
McAfee products are among the best for personal protection, with over 500 million customers worldwide. Some of the company’s recent accolades include multiple awards from the 2021 Cybersecurity Global Excellence Award.
Cisco Systems, Inc.
Cisco Systems, Inc., another longtime American technology player, was founded in 1984. The tech giant is perhaps better known for its networking gear. But Cisco offers terrific cybersecurity tools targeting enterprise customers. Cisco already provides cybersecurity solutions to more than 840,000 networks, 61 million endpoints, and 300,000 customers.
The company is also hoping to increase its security market share. Cisco generated $3.4 billion from its security products in 2021. But, it hopes to grow this figure to $80 billion by 2025 (Source). Cisco’s cybersecurity solutions include:
- Advanced Malware Protection
- Firewalls
- Email Security
- Security Management
- Web Security
- VPN and Endpoint Security
One of the company’s notable products is Cisco Secure X. The cloud-native platform offers enterprise users a unified platform to enjoy Cisco’s expansive security portfolio. Cisco Secure X connects customers’ security infrastructure with Cisco’s integrated security portfolio.
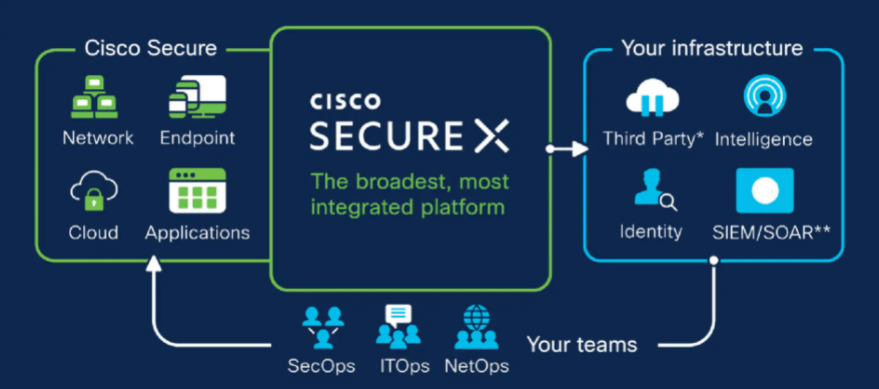
Users can enjoy:
- Unified visibility
- Fast time to value
- Managed threat hunting
- Playbooks
- Automation
- Threat response
- Device insights
This product allows users to handle cybersecurity from a unified platform rather than relying on disconnected vendors and products. It is available to all Cisco Secure customers.
Cisco has also won numerous recent awards, including:
- Industrial IOT Innovation of the Year – IoT breakthrough Awards 2020
- TrustRadius Tech Cares Award 2020
- Product of the Year for Hyperconverged Infrastructure – CRN Awards 2019
- 2018 Global Market Leader – Frost and Sullivan, 2018
Palo Alto Networks, Inc.
Palo Alto Networks, Inc. is yet another noteworthy American cybersecurity company headquartered in Santa Clara, California. The company was founded in 2005 and has since gained a reputation for its advanced firewalls and cloud-based cybersecurity products.
Palo Alto Networks serves more than 70,000 companies in over 150 countries. In addition, more than 80 of the Fortune 100 companies rely on Palo Alto Networks for their cybersecurity solutions.
The company is best known for its intelligent threat protection systems. Its products help identify and manage threats instead of merely blocking access. For example, legacy firewalls only identify traffic based on protocols and ports. This design leaves them vulnerable to clever attacks delivered using port-hopping.
Palo Alto firewalls enable applications regardless of SSL encryption, evasive tactics, port, or protocol. This design gives you more control over next-generation applications, infrastructures, and users.
The company also has a vast cybersecurity solutions portfolio, covering:
- Next-Generation Firewalls
- DNS Security
- Threat Prevention
- Data Loss Prevention
- Threat Intelligence
- Uniform Resource Locator Filtering
- SaaS Security API
- Internet of Things Security
- Cyber Security
- Security Analytics and Automation
- Laptop and Mobile Device Protection
The cybersecurity vendor also serves government entities and service providers. While Palo Alto has a robust cybersecurity solutions portfolio, it is perhaps best loved for its next-generation firewalls. The company offers a range of secure firewall solutions, including cloud-delivered firewalls and physical appliances.
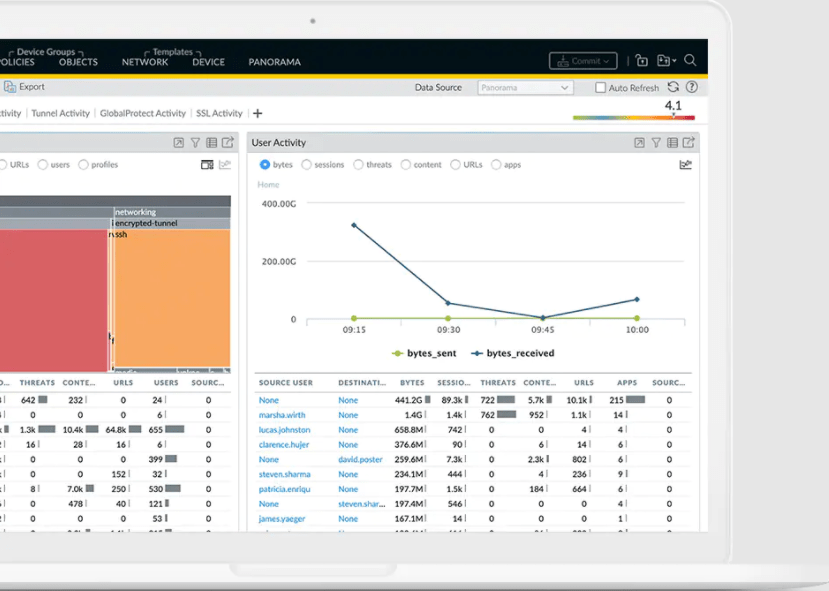
Users can also manage multiple Palo Alto firewalls from a centralized management system known as Panorama. The web-based interface allows users to view device-specific or aggregate data for applications, content, and users that pass through the firewall.
CrowdStrike Holdings, Inc.
CrowdStrike Holdings, Inc. is an American cybersecurity company founded in 2011. The company is headquartered in Sunnyvale, California, and provides threat intelligence, endpoint security, cloud workload, and cyber-attack response services. CrowdStrike has been involved in several high-profile cyberattack investigations, including the infamous Sony Pictures hack.
CrowdStrike unifies endpoint protection with its flagship Falcon Platform. Endpoints refer to physical or virtual devices such as laptops, desktops, mobiles, or virtual machine images.
- CrowdStrike’s Falcon platform is available on a subscription-based model. The subscription options include:
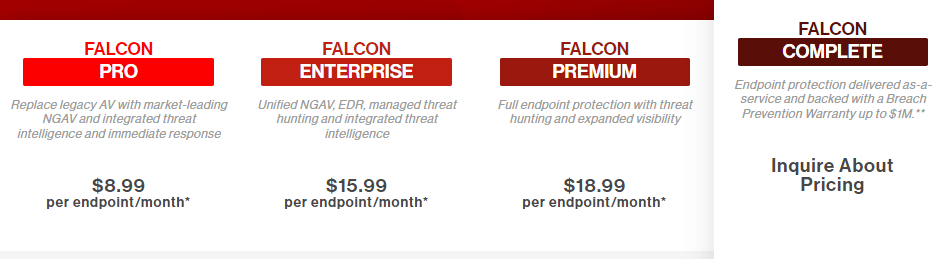
Falcon Pro – Costs $8.99 per endpoint per month. This package includes next-generation Antivirus protection with machine learning capabilities. - Falcon Enterprise – Costs $15.99 per endpoint per month. This package includes Endpoint Detection & Response in addition to the next-generation Antivirus protection.
- Falcon Premium – Costs $18.99 per endpoint per month. You get everything in the Enterprise package with IT Hygiene added to your subscription.
- Falcon Complete – Is delivered as-a-service. You’ll need to contact CrowdStrike for custom pricing.
The Falcon Platform also features individual product bundles. You can add these bundles to any of the subscription options mentioned above at an extra cost. Some of these bundles include:
- Falcon Prevent – This is a next-generation Antivirus program. The software features artificial intelligence and machine learning. This feature allows it to detect both known and unknown ransomware and malware. The program even provides full context for each attack, so you know exactly what the cybercriminals are trying to do.
- Falcon Firewall Management – This allows you to manage your firewalls from a centralized interface. You can create, manage, and enforce firewall rules and policies.
- Falcon X – This Threat Intelligence program automatically investigates incidents, so you don’t have to do so manually.
- Falcon Insight – Gives you a 360-degree view of what’s happening at every endpoint. This software helps to spot and prevent stealth attacks. It also automatically detects suspicious activities.
- Falcon Overwatch – Constantly crawls your data to hunt for signs of intrusion in real-time.
CrowdStrike is the ultimate endpoint security partner for businesses that heavily rely on the cloud.
IBM
International Business Machines Corporation (IBM) is a long-time technology company founded in 1911. The company has been behind some of the most notable technology inventions, including the floppy disk, automated teller machine (ATM), SQL programming language, magnetic stripe card, dynamic random-access memory (DRAM), and relational database. In addition, IBM holds the record for the most annual U.S. patents for 28 years in a row.
IBM is arguably better known for its hardware products. But, the company offers multiple cybersecurity software products covering:
- Data Privacy
- Data Protection Platform
- Encryption and Cryptography
- Identity and Access Management
- Cloud Data Security
- SaaS Solutions
- Zero-trust Security Solutions
- Mainframe Security
- Data Resilience
- SIEM
- Advanced Fraud Protection
- Data Security Services
IBM also specializes in managed security services for enterprise clients that prefer a more hands-off approach to cybersecurity. These services cover multi-cloud, on-premises, and hybrid environments. In this case, IBM manages day-to-day data protection, threat management, and compliance requirements.
Additionally, enterprises can benefit from holistic data security, encompassing malware, intrusion and exfiltration attempts, and other cybersecurity incidents in a single program. For instance, IBM’s managed cybersecurity services cover:
- Threat Management
- Managed Cloud Security
- Managed Detection and Response
- Managed Identity
- Managed Endpoint Security
Many companies don’t have the in-house competence to deal with sophisticated cyberattacks. So, IBM offers critical security solutions to businesses in this category.
Secureworks Inc.
Secureworks Inc. was founded in 1998 and has been a Dell Technologies subsidiary since its acquisition in 2011. The company is active in more than 50 countries and has more than 4,000 clients. These clients also include fortune 100 companies.
Secureworks specializes in Threat Detection and Response (TDR). The company uses a combination of third-party integrations, machine learning, and threat intelligence to produce world-class cybersecurity solutions. Secureworks also offers managed cybersecurity services.
The company’s cybersecurity product portfolio includes:
- Extended Detection and Response
- Managed Detection and Response
- Vulnerability Management
TAEGIS™ XDR is one of Secureworks’ most popular products. The software unifies threat detection, prevention, and response on a single platform. It uses comprehensive threat intelligence, machine learning-driven analytics, and automation to offer robust cybersecurity across cloud, network, and endpoint.
The product offers high-fidelity alerts to reduce noise and make the security team’s job easier. The software also provides specific and actionable intelligence to help you manage and remediate events quickly.
Secureworks is the ultimate cybersecurity solutions partner for businesses looking to improve mean time to respond, increase automation tasks, and improve advanced threat detection. Secureworks products feature custom pricing depending on the specific cybersecurity services you need.
How to Pick Your Cybersecurity Company
Cybersecurity can be difficult to handle alone, even for businesses with dedicated IT staff. As such, a good cybersecurity provider goes a long way to protecting your business from imminent cyber threats.
However, choosing the right provider can pose some challenges. There are many companies to choose from, each with its strengths and weaknesses.
The best strategy is to conduct a thorough cybersecurity risk assessment. This assessment will help you pinpoint exactly what you need from your security provider. Then, it’s easy to match with the cybersecurity company that fits your profile.
Step 1 – Standardize Your Data Asset Valuation
The typical organization collects, stores, and shares different types of data. This information may include customer contracts, research and development documents, source code, Personally Identifiable Information (PII), financial reports, and so on. But it is impossible to apply the appropriate security measure for each type of data without first determining its value.
For example, data types such as financial data, pricing, and product design can be more expensive to lose than PII information. (Source) This fact isn’t always obvious and may lead you to undervalue protecting certain kinds of data.
Therefore, create a standard template for determining the importance of your business data assets. You can use criteria such as the asset’s business importance, value, and legal standing to determine its value. Some of the questions that may help you determine the value of an asset include:
- How valuable is this data to competitors?
- Are there legal or financial ramifications of losing or exposing this data?
- Would losing this data affect profitability or revenue?
- What does it take to recreate this information from scratch?
- Could the business still function if we lost this data?
- Would losing this information impact our reputation?
This information will help you classify assets into categories such as Critical, Major, or Minor.
Step 2 – Catalog Critical Information Assets
This process involves listing all valuable business assets. It’s worth involving senior management, compliance officers, marketing, human resources, and other stakeholders to ensure you don’t miss anything. This point is crucial since defining important data assets can be somewhat subjective. For example, Marketing, IT, and Human Resources may have very different ideas about critical data.
Valuable data assets, in this case, may include:
- Sensitive partner documents
- IT servers, networks, systems, and communication
- Contact information
- Personally Identifiable Information (PII)
- Commercial transactions and interactions
- Intellectual property
- Financial information
- Trade secrets
Don’t forget to include information assets from your third-party vendors. Finally, use the template you created in the previous step to catalog your assets based on value.
Step 3 – Identify Imminent Cybersecurity Threats
Next, consider the types of threats that might put your assets at risk. The most common cybersecurity threats include:
- Malware
- Ransomware
- Social engineering
- Human error
- System failure
- Intentional or unintentional data leakage
- Unauthorized access
- Data loss
- Misuse of information by authorized users
You’ll be another step closer to finding the right cybersecurity partner once you’ve identified common cybersecurity threats. You’ll also have a better idea of how to protect your data and which vendor is most likely to fit your needs.
Step 4 – Identify Potential Vulnerabilities
It’s worth noting that a vulnerability is different from a threat. Vulnerabilities refer to specific system flaws that may increase the chances of a cyberattack. In addition, these vulnerabilities exist within your network, while a threat may be internal or external.
There are various ways to determine vulnerabilities, including penetration testing, audit reports, vulnerability analysis, or information security test and evaluation (ST&E) procedures. Common examples of cybersecurity vulnerabilities include:
- Unpatched or out-of-date software
- Hidden backdoor programs
- Weak firewall
- System misconfigurations
- Poor authorization and credentials management
- Missing data encryption
- Bugs
- Weak passwords
- Unrestricted uploads of dangerous file types
- You can also use these examples to gauge the vulnerability of your network and system
Step 5 – Choose Your Cybersecurity Partner
You can now collate all this information to articulate your cybersecurity needs. You may be surprised to find that your needs are different from what you’d thought initially. For example, you may find that you require a cybersecurity company to manage your firewall in addition to providing identity and access management.
Be specific about what you need your cybersecurity company to provide. Use all the information you collected in previous steps to identify your needs. The essential services may include:
- Endpoint security
- Network security
- Anti-virus
- Access control management
- Device and data storage protection
- Malware and phishing protection
Finally, you can vet different cybersecurity vendors and gauge their capability in relation to your security needs. We’ve already broken down the top six cybersecurity companies and their expertise for your convenience.

