The 18 CIS Critical Security Controls
The Center for Internet Security (CIS) developed a series of recommendations for preventing the most prevalent cyber-attacks. The 18 recommendations are collectively known as the CIS Critical Security Controls or CIS Controls. They are free for anyone to use and have been widely adopted by enterprises of all sizes.

First, the CIS identifies the most prevent cyber threats, including malware, ransomware, insider and privilege misuse, targeted intrusion, and application hacking. Therefore, the CIS Controls focus on these areas, providing critical recommendations for closing attack vectors and reducing the attack surface. Furthermore, the CIS Controls center on cost-effective cybersecurity activities that provide the highest value in the shortest time.
These controls are developed by a consortium of industry experts, including cyber analysts, policy-makers, government agencies, consultants, auditors, and academics. It’s worth noting that the CIS Controls do not replace other regulatory or compliance frameworks such as FISMA, HIPAA, and DSS. However, the controls align with established frameworks and provide a suitable starting point for compliance with these regulatory frameworks.
The 18 controls are spelled out in Version 8 of the CIS Controls. It’s slightly more condensed than Version 7. Version 8 is also updated to tackle the current changes to how businesses operate since the release of the previous version. These changes include outsourcing, cloud-based computing, changing attacker tactics, mobility, and work-from-home.
Below is a brief overview of each of the 18 CIS Critical Security Controls and what they entail:
Inventory and Control of Enterprise Assets
The first CIS Control deals with the active management of all enterprise assets. The main goal is to gain an accurate picture of all the enterprise’s assets. Then, you’ll be able to monitor and protect these assets actively. Successful implementation of this control also allows you to identify unmanaged and unauthorized assets for removal or remediation.
The CIS defines asset management as inventorying, tracking, and correcting all enterprise assets. Some things that can be categorized as assets include end-user devices, network devices, the Internet of Things (IoT), and servers. This control also covers all assets connected to the enterprise’s infrastructure, whether virtually, physically, via the cloud, or remotely.
The CIS also provides actionable steps for completing this control. These include using an active discovery tool, addressing unauthorized assets, and establishing and maintaining a detailed inventory of your enterprise assets. Finally, this control is critical for preventing external attacks that exploit unprotected, poorly configured, or patched assets.
Inventory and Control of Software Assets
It’s equally important to protect your software assets. Attackers often target outdated and unpatched software to access an enterprise’s system remotely. The best prevention measure is to update and patch vulnerable software. However, this measure is difficult to implement without a comprehensive inventory of your software assets.
Again, managing software assets includes the inventory, tracking, and correcting all assets. The main goal is to ensure that only authorized operating systems and applications can be installed and executed on the network. Furthermore, implementing this control helps block unauthorized and unmanaged software installation and execution.
Some of the recommended action steps for this control include:
- Creating and maintaining a complete inventory of software assets
- Using automated software inventory tools
- Addressing unauthorized software
- Creating allow lists for software, scripts, and libraries
This control is equally effective for authorized software for which patches are yet to be released. Your software inventory can help you identify vulnerable assets to protect until the patch is released. In addition, it’s an adequate safeguard against zero-day attacks that target this specific vulnerability.
Data Protection
Today’s enterprises access and store data in various locations, including within the enterprise, in the cloud, and on portable end-user devices. Furthermore, some of this data is sensitive and relates to customer data, intellectual property, and finances. So the third control calls for a robust data management plan.
This plan is simplified by focusing on the five W’s, including:
- What data does the enterprise handle and store?
- Who should access the data?
- Where is the data accessed and stored?
- When should the information be deleted?
- Why does the data need protection?
This step is crucial for enterprises covered by data privacy laws and regulations. Properly managing data throughout its lifecycle makes it difficult for attackers to extract sensitive information during a breach. Some of the suggested action steps in the CIS Data Protection Control include:
- Establishing and maintaining a comprehensive data management process
- Maintaining current data inventory
- Enforcing data retention measures
- Documenting data flows
- Securely disposing of data
- Encrypting sensitive data in transit and at rest
- Implementing data segmentation based on the sensitivity
- Logging sensitive data access
Specifically, data classification is crucial to a data management plan. The CIS suggests using common classification tags such as Sensitive, Confidential, and Public. However, this recommendation isn’t cast in stone, and enterprises can use custom tags that fit their purposes. Finally, the data classification should end in granular user permissions to minimize data exposure.
Secure Configuration of Enterprise Assets and Software
Most hardware and software come pre-configured out of the box. For example, a device or software may come with default passwords, older vulnerable protocols, or open ports and services. Most manufacturers prioritize ease of deployment with their default settings.
In light of this fact, the fourth CIS control recommends configuring your enterprise assets and software to adhere to your security policy. This configuration process isn’t ad-hoc. Instead, it is necessary to develop a consistent configuration management workflow. Organizations should also document this workflow for compliance, incident response, and audits.
Some of the recommended safeguards for this CIS Control include:
- Configuring automatic session locking on enterprise assets
- Installing firewalls on end-user devices and servers
- Disabling or uninstalling unnecessary services on software and enterprise assets
- Implementing remote wipe capabilities on end-user devices
- Applying automatic device lockout on end-user devices
- Managing default accounts on software and enterprise assets
This CIS Control also emphasizes multiple security layers. Firewalls are a great starting point, but you need more robust security to slow, delay, or stop potential threats.
Account Management
Threat actors don’t always gain access to the enterprise environment through hacking. Instead, it is relatively common for unauthorized users to gain access to an organization’s assets using valid user credentials. For example, cybercriminals can use malware to capture passwords and gain access to enterprise assets.
Highly privileged accounts, including administrator accounts, are particularly vulnerable to these attacks. Unauthorized access to a privileged account gives the attacker complete control, including the ability to make changes to the assets. These changes are typically designed to make the asset vulnerable to other malware attacks.
Therefore, the Account Management Control calls for complete visibility of user accounts in the enterprise environment. This visibility includes an intimate understanding of who owns credentials, how they are assigned, and how they are used.
An excellent place to start is with an inventory of all enterprise accounts. Tools such as Active Directories also help track account changes and detect anomalous behavior. Other account management best practices include not sharing accounts or using default passwords, implementing lockouts after multiple failed login attempts, and enforcing strong password policies.
Other suggested Account Management measures covered by this CIS control include:
- Using unique passwords
- Creating dedicated administrator accounts to limit user privileges
- Disabling dormant accounts
- Maintaining an inventory of service accounts
Access Control Management
The previous control deals with general account management. Access Control Management examines the type of access accounts should have. Organizations should follow the principle of least privilege. Here users are granted the lowest level of access required for their role.
Some of the granular recommendations for this Control include:
- Establishing processes for creating and revoking access
- Requiring multi-factor authentication (MFA) for administrative access, remote network access, and externally-exposed applications
- Centralizing access control
- Inventory of authentication and the relevant systems used for authentication
- Role-based access control
Successful implementation of this Control should result in a standardized and repeatable process for granting, refusing, and revoking access across the entire organization. There are also multiple tools that organizations can use to enforce and maintain access control policies.
Continuous Vulnerability Management
The seventh control offers basic guidelines for establishing a vulnerability management program. Vulnerability management is one of the oldest cybersecurity best practices. It allows organizations to create a plan for constantly assessing and tracking threats to enterprise assets. Successful vulnerability management also makes it more difficult for attackers to gain unauthorized access to the enterprise environment.
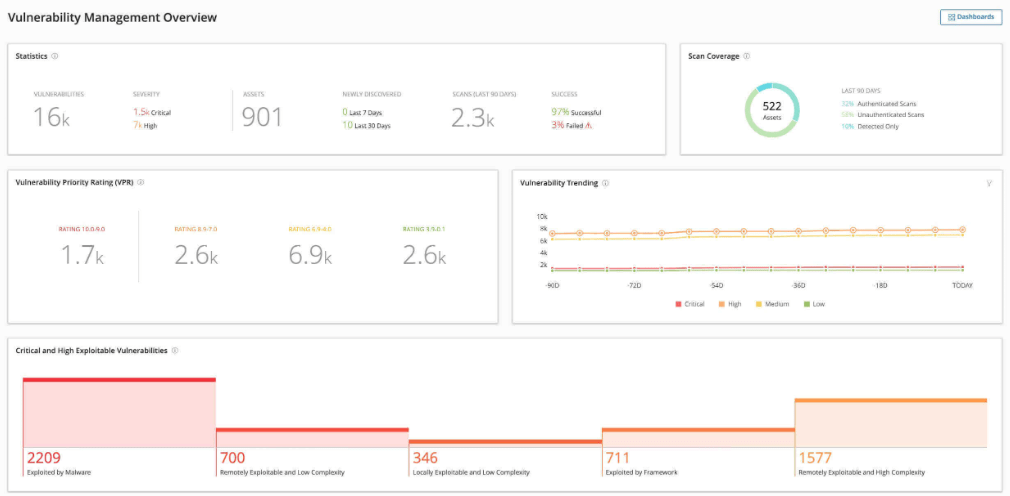
Attackers are constantly scanning enterprise networks for exploitable vulnerabilities. So timeliness is a critical part of a good vulnerability management program. Defenders must stay up-to-date with the latest threat bulletins, security advisories, software updates, and patches to identify threats before hackers do.
Some of the recommendations under the Continuous Vulnerability Management CIS Control include:
- Creating and implementing a comprehensive vulnerability management process
- Designing and implementing remediation processes
- Automating patch management for operating systems and applications
- Automating vulnerability scans for internal and externally-exposed assets
- Remediating identified vulnerabilities quickly
It’s worth noting that this CIS Control focuses more on known threats rather than remediation of zero-day attacks. Therefore, it emphasizes a repeatable and continuous process of discovering, prioritizing, and resolving vulnerabilities.
Audit Log Management
Audit Log Management is a critical CIS Control, covered by regulatory compliance such as HIPPA. Many organizations also already collect audit logs across enterprise assets to meet compliance requirements. However, it’s not always the case that organizations constantly monitor and analyze these logs.
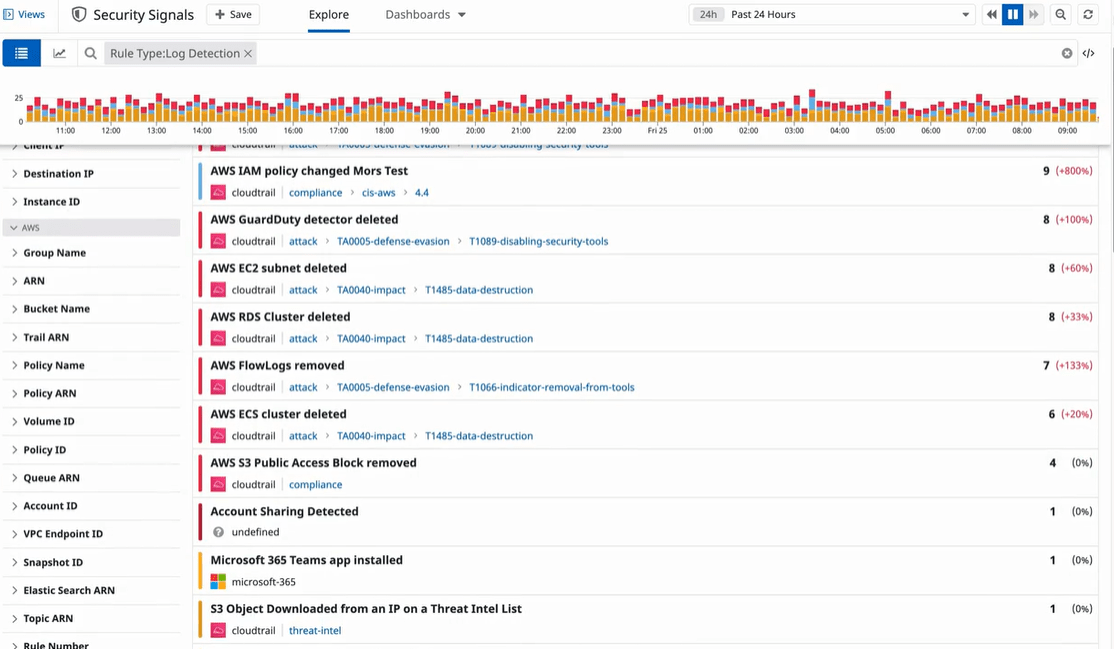
Therefore, the Audit Log Management CIS Control also covers regular audit log reviews to identify activity baselines and operational trends. This information is helpful for quickly detecting abnormal system activity that might indicate an attack.
Some of the recommendations under this control include:
- Establishing a standard audit log management process
- Collecting audit logs
- Reviewing audit logs
- Standardizing time synchronization
Audit logs aren’t just helpful in detecting an attack. They are equally valuable for incident response, such as assessing how an attack happened and understanding its full extent.
Email and Web Browser Protections
Email and web clients allow attackers to engage with enterprise users directly. In particular, social engineering attacks attempt to manipulate users into interacting with malicious content. As a result, users within the enterprise may unwittingly disclose sensitive information, expose credentials, or provide hackers with an entryway into the enterprise network.
The ninth CIS Control focuses on protecting web browsers and increasing email security. Some of the suggested safeguards include:
- Preferring fully supported email clients and web browser
- Enforcing DNS filters and network-based URL filters
- Restricting unauthorized and unnecessary email client and browser extensions
- Blocking unnecessary file types
- Implementing DMARC
- Deploying anti-malware protections on email servers
Email and web connect enterprise assets to external users and environments. Therefore, protecting these critical vectors is crucial for drastically reducing your attack surface.
Malware Defenses
Malware is one of the oldest and most pervasive internet threats. Attackers use malware for various malicious activities, including stealing data, destroying records, and capturing credentials. While most users understand the importance of anti-malware programs as a last line of defense, many still engage in risky end-user behaviors such as installing unapproved software and opening unknown attachments.
This CIS Control covers some of the rudimentary malware best practices. These include installing malware defenses on all possible entry points, automating updates, and centralizing anti-malware management. Other malware-related recommendations featured in this control include:
- Disabling auto-play and auto-run for removable media
- Automating anti-malware scanning
- Using behavior-based anti-malware solutions
- Enabling anti-exploitation features on enterprise assets and software
The Malware Defenses Control may seem like a no-brainer for IT professionals. However, it’s still worth reviewing the organization’s use of anti-malware technologies.
Data Recovery
Organizations can lose data under various circumstances, including malicious ransomware, accidental deletion, hardware failures, and natural disasters. Nevertheless, every organization needs a plan to recover lost data. Specifically, the main challenge is to restore the data to a known trusted state as quickly as possible.
This challenge is particularly pronounced during ransomware incidents. Malicious actors often tamper with configuration settings and trusted applications to make the system more vulnerable to attacks. Therefore, recent data backups are crucial for resuming normal operations.
This CIS Control offers specific guidelines for data recovery in the event of data loss. The necessary procedures include:
- Creating a data recovery process
- Automating backups
- Protecting recovery data using encryption or data separation
- Isolating recovery data
- Testing recovery data regularly
This control is one of the easier ones to implement, even for small organizations. For instance, isolating recovery data entails storing it offline where there are fewer chances for tampering. In addition, testing the recovery data regularly means that staff can count on the backups to restore data to the last trusted state in the event of a breach.
Network Infrastructure Management
The typical network infrastructure provides a broad attack surface for would-be hackers. Malicious actors have multiple potential entry points, including physical and virtual gateways, routers, switches, wireless access points, and firewalls. Most notably, pre-configured network devices provide attackers with viable entry points into the enterprise system.
Most manufacturers and vendors configure their devices and software for easy use and fast deployment. Unfortunately, often these default settings don’t prioritize network security. For example, a network device may have multiple potential vulnerabilities, including a weak default password, unnecessary pre-installed software, and open ports and services.
A threat actor can exploit these vulnerabilities to launch several potential attacks, including redirecting traffic, gaining access to the network, or intercepting sensitive data while in transmission.
The CIS Control 12 attempt to remediate the inherent security flaws in new hardware and software assets. Some of the recommendations for this control include:
- Updating the network infrastructure
- Securing the network architecture
- Centralizing Network Authentication, Authorization, and Auditing (AAA)
- Utilizing VPN for remote devices
- Connecting remote devices to the enterprise AAA
Central to this control is developing processes and procedures for securing the network infrastructure. Organizations should also continuously improve these processes to include new and emerging vulnerabilities.
Network Monitoring and Defense
Configuring the network infrastructure is only one part of securing the enterprise network. This CIS 13 Control takes a holistic approach to network security. It calls for organizations to implement processes and tools for monitoring and defending against internal and external threats.
Some of the key recommendations for network monitoring and defense include:
- Centralizing security event alerting
- Implementing network intrusion detection systems
- Using host-based intrusion detection and prevention technologies
- Managing access control for remote assets
- Capturing network traffic flow logs
- Filtering traffic between network segments
- Deploying port-level access control
This control also emphasizes the importance of humans in monitoring, detecting, and preventing malicious attacks. Over-reliance on detection and prevention systems may lead to false positives. Additionally, these technologies are only as good as their configuration.
Security Awareness and Skills Training
Even the best enterprise security program cannot be effective without a skilled and security-conscious workforce. Risky user behavior is the leading cause of enterprise data breaches. Therefore, the 14th CIS Control emphasizes the importance of security awareness programs for addressing human vulnerability.
This CIS Control recommends creating and implementing a comprehensive security awareness program. The program should empower employees to:
- Recognize social engineering attacks
- Use authentication best practices
- Handle data securely
- Understand the roots of unintentional data exposure
- Recognize and report security incidents
- Identify and report missing security updates
- Understand the dangers of connecting to insecure networks
Specifically, this CIS Control encourages role-based security awareness and skill training. For example, organizations may deploy separate training programs for their high-profile roles, IT professionals, and web application developers.
Service Provider Management
Most modern organizations work with third parties such as service providers, contractors, freelancers, and vendors. Unfortunately, these third parties also introduce security risks to the enterprise network. Therefore, it is crucial to audit external partners with access to IT platforms or processes and those that handle sensitive enterprise data.

The main recommendations under this CIS Control include:
- Creating a complete inventory of all service providers
- Developing a management policy for service providers
- Classifying service providers
- Including security requirements in service provider contracts
- Assessing and monitoring service providers
- Creating secure procedures for decommissioning service providers
It’s critical to create clear standards for evaluating and grading service providers. Service providers may also occasionally change their policies. Therefore, monitoring the policy changes and ensuring that it aligns with the enterprise security policy is essential.
Application Software Security
Numerous software applications make previously complex system functions like databases easier to handle. However, these applications may have inherent security vulnerabilities due to insufficient testing, weak authentication, coding mistakes, or insecure design. Nevertheless, securing these applications is vital since they provide an easy entry point for potential attackers.
The 16th CIS Control provides a clear framework for securing critical applications that control access to system resources or manage sensitive data. Some of the recommendations include:
- Establishing a secure application development process
- Creating an inventory of third-party software components
- Performing root cause analysis for security vulnerabilities
- Establishing procedures for remediating software vulnerabilities
- Implementing code-level security checks
- Separating production and non-product systems
- Training developers in secure coding and application security concepts
This control is beneficial for in-house developed and hosted software. The CIS also suggests implementing additional frameworks together with this control. For example, the NIST SP 800-218 provides detailed guidelines for developing a secure development process.
Incident Response Management
The CIS understands that security breaches are inevitable despite established processes for detecting and preventing threats. This control primarily deals with reducing the dwell time between the attack and appropriate response. Unfortunately, attackers continue to do more damage the longer they have access to the system network.
The control emphasizes documenting an incident response plan. This plan should cover critical response and recovery measures, such as specific investigation procedures, data collection, reporting, legal protocols, management responsibility, and communication. Additional safeguards under this control include:
- Having dedicated incident handling personnel
- Establishing processes for reporting incidents
- Assigning incident response roles and responsibilities
- Defining thresholds for security incidents
- Conducting regular incident response exercises
- Conducting post-incident reviews
Penetration Testing
The final CIS Control is concerned with identifying vulnerabilities within the enterprise network before the attackers do. Penetration tests are critical for this purpose. They help organizations identify weaknesses in their internal and external networks, devices, systems, and applications.
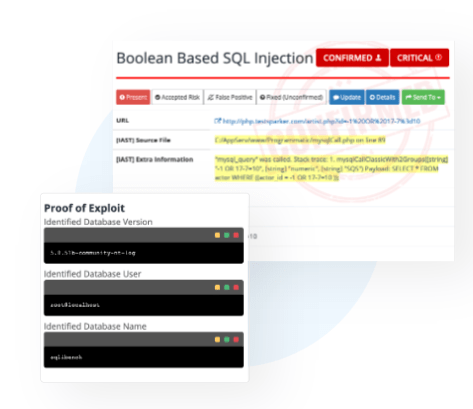
The benefits of penetration testing are threefold. The first benefit is validation. It allows the enterprise to confirm that its defenses are adequate. Secondly, penetration tests help identify security gaps and remediate vulnerabilities before hackers can exploit them. Finally, the results of a penetration test can be an excellent tool for convincing decision-makers of the importance of bolstering the system’s security.
This CIS Control recommends:
- Creating a penetration testing program
- Occasionally performing external penetration tests
- Remediating identified vulnerabilities
- Conducting regular internal penetration tests
It’s worth noting that this control is different from control 7, Vulnerability Testing. Vulnerability testing focuses on known treats, while penetration testing goes much deeper. For instance, the penetration test may uncover the potential impact of a successful attack. Lastly, vulnerability tests rely primarily on automated scans and technology, while penetration tests are more human-centric.

