STIG Vs. CIS: Side-by-Side Comparison
Enterprise hardware and software assets come with default settings for easy use and quick deployment. However, these default configurations introduce security risks to the organization’s network. For example, open ports, unnecessary applications, and services provide hackers with potential attack vectors.
Creating configuration standards from scratch is a tough sell for most organizations. So instead, they rely on publicly available third-party configuration baselines to secure their assets. The two most common baselines include Security Technical Implementation Guide (STIG) and Center for Internet Security (CIS) Benchmarks.
This guide is dedicated to helping you choose the best configuration standards for your organization.
Our Recommendation = Use CIS Benchmarks
For most organizations, it makes sense to implement CIS Benchmarks over the STIG framework. The benchmarks cover all common assets, including network devices, mobile devices, operating systems, applications, and cloud hosting services. Whatever the asset, you are guaranteed the industry’s best configuration settings for hardening your systems.
CIS Benchmarks also tie into major regulatory frameworks such as PCI DSS, ISO 27000, HIPPA, SWIFT, and NIST CSF. For example, PCI DSS standards recommend using benchmarking tools. Given the CIS Benchmarks are consensus-driven and internationally recognized, it makes sense to implement them as a first step toward mandatory regulatory compliance.
Furthermore, CIS Benchmarks are more widely used than the STIG Framework. The Center for Internet Security comprises a consortium of subject matter experts drawn from the private sector, manufacturing, vendors, government, research, and academia. Therefore, there is plenty of supporting material to complement the CIS Benchmarks.
By contrast, the STIG Framework was developed by the Defense Information Systems Agency (DISA). As a result, additional supporting information, research, resources, and tools may be more challenging to come by. This limitation is a natural consequence of the limited scope of parties involved in developing the framework, particularly compared to the CIS.
Finally, the STIG Framework is designed primarily for the Department of Defense (DoD) and its affiliates. The Framework is still freely available to the private sector. However, you can tell from the documentation and jargon that it is geared toward U.S Government use. The terminology may be difficult and borderline frustrating to translate for private businesses that don’t require STIG compliance.
The CIS caters to a broader target audience, including government institutions, private businesses, and organizations of all sizes and industries. The terminology is simple and universal and easy to cross-reference with other known standards and regulatory frameworks.
When To Use STIGs Instead
Again, the STIGs were developed for the Department of Defense. So STIG is the defacto configuration framework for DoD agencies. So, it makes sense for a Federal IT professional within the DoD to comply with STIGs over CIS Benchmarks.
However, all organizations that are part of the Department of Defense Information Networks (DoDIN) are legally and contractually required to comply with STIGs. This category includes contractors that connect to DoD systems and networks. So, a defense contractor may want to focus on meeting STIG compliance before deploying the CIS Benchmarks.
STIG compliance is also a requirement for software and hardware operating on DoD systems and networks. So, vendors whose products are meant for use in the Defense Information Networks should focus on complying with STIG cybersecurity requirements.
Finally, organizations that require high-level security configurations may opt for STIGs. These requirements are more stringent than CIS Benchmarks. However, it makes sense since they are developed for the Department of Defense, which works with highly sensitive and classified data. STIGs are also updated every 90 days, so you’re always guaranteed the most current standards.
Pricing – Is STIG or CIS the Better Deal?
We won’t attempt to compare the cost of implementing STIG vs. CIS Benchmarks, because the cost of deploying these baseline controls varies widely between organizations. Instead, we’ll compare the price of the documentation and supporting tools.
The Security Technical Implementation Guides (STIGs) are free to download. By default, the guidelines are available in XML format. You can visit the DoD Cyber Exchange website to download the relevant STIGs for your device and operating system.
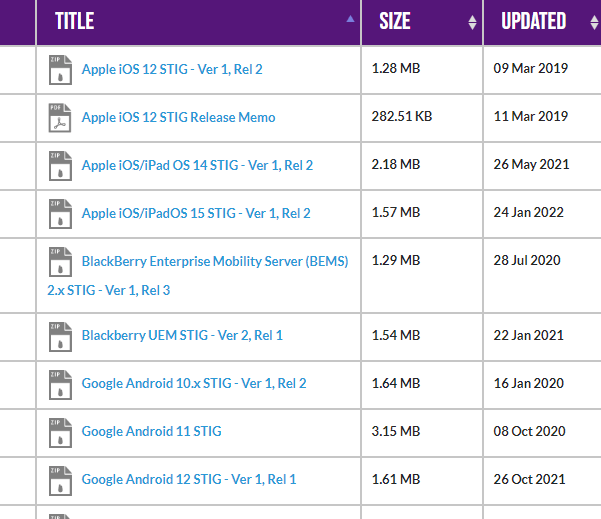
The CIS Benchmarks are also free to download in PDF format. However, you’ll need to sign up for an account to download the benchmarks. Signing up for the account is free.
STIG vs. CIS – File Formats
The file format may not be a deal-breaker for most people. However, it’s still worth investigating. STIGs are available in XML format, precisely the XCCDF format. Unfortunately, the format is notoriously difficult to read. But you can overcome this problem by parsing the document with an XCCDF viewer.
The CIS Benchmarks are available in PDF format. It’s a more accessible choice for most people. You can also convert the benchmarks into XCCDF files with the paid version of the CIS-CAT. We go into more details about the CIS-CAT in a different section of this post.
SITG vs. CIS – Commercial Adoption
Winner = CIS
Both STIG and CIS see extensive commercial adoption. However, STIGs are often used by government agencies and private sector businesses that work within the national supply chain. Still, STIGs are publicly available for commercial adoption.
It’s no surprise that the CIS Benchmarks enjoy broader adoption in the private sector. The benchmarks are heavily peer-reviewed and consensus-driven. STIGs tend to use government-mandated language, which might be unpopular for organizations that aren’t required to comply with the standards.
STIG vs. CIS – Ease of Implementation
Winner = CIS
Both STIGs and CIS Benchmarks are relatively easy to implement. This ease is primarily thanks to the documents’ clear structure.
For instance, STIG categorizes its controls based on risk level. There are three main categories, including:
CAT 1 – This is the most severe risk level. The controls in this category help neutralize direct threats to system availability and data integrity.
CAT 2 – The vulnerabilities are less severe than CAT 1 but still open to exploitation. There is a lower risk of compromised system availability and data integrity. However, these vulnerabilities are serious and should be addressed quickly.
CAT 3 – These vulnerabilities do not pose an immediate risk of system failure or cybersecurity incidents. However, the vulnerabilities may still affect an organization’s overall security posture.
Similarly, the CIS Benchmarks categorize recommendations based on the potential impact of the recommendation. These categories are called profiles and include:
Level 1 Profile – This level focuses on surface-level recommendations to remediate the most common cybersecurity vulnerabilities. The recommendations in this profile can be implemented quickly and with little or no disruption to normal operations.
Level 2 Profiles – This level features more complex recommendations that deal with high-level threats. These recommendations benefit organizations that prioritize cybersecurity or are accountable to cybersecurity regulations and compliance. However, implementing recommendations in this category may cause some disruption to normal operations.
In short, STIG and CIS standards offer a simple and straightforward framework for configuring networks. However, the CIS uses more concise language and might be easier to implement.
STIG vs. CIS – Implementation and Compliance Tools
Security control frameworks often feature hundreds of recommendations. The extensive documentation helps provide organizations with actionable recommendations for system hardening. However, manually applying each recommendation is tedious, if not impossible. Implementation tools help to automate the process and reduce incidents of human error.
STIG Implementation and Tools
Winner = CIS
STIG offers handy tools to help you automate recommendations, implementation, and compliance.
The most popular tool is the STIG Viewer. You can download the JAR file for free at the DoD Public Cyber Exchange website. The tool allows you to view the STIGs XML file in OVAL or XCCDF format, depending on your use case.
Additionally, the STIG Viewer allows you to create a STIG checklist. Simply import the STIG file you downloaded to the STIG Viewer. Then, select the relevant STIG, and the tool will create a checklist for you to follow during implementation.
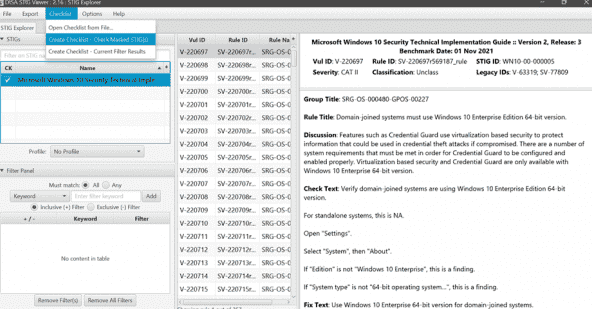
It’s worth noting that the STIG Viewer is designed to simplify the recommendations. The tool doesn’t automate implementation or compliance. It also doesn’t scan your system for compliance.
Still, it’s a valuable tool for managing compliance. It provides all STIGs in a central place. You can also select specific rules for your organization and get in-depth information about each control.
For example, each selected STIG rule explains why the item is essential. It also guides how to check for compliance with the specific STIG rule. Finally, the STIG Viewer provides specific action steps for complying with the selected rules.
SCAP Compliance Checker (SCC)
The Secure Content Automation Protocol (SCAP) checker is a helpful tool for assessing compliance. It’s more robust than the STIG Viewer and, therefore, worth deploying. It’s available for free at the DoD Cyber Exchange Website.
The SCAP Checker displays all available STIG benchmarks when you launch the tool. Then, you can select specific criteria and scan a local or remote system. You’ll receive checklist files with the scan results, which you can import into the STIG Viewer.
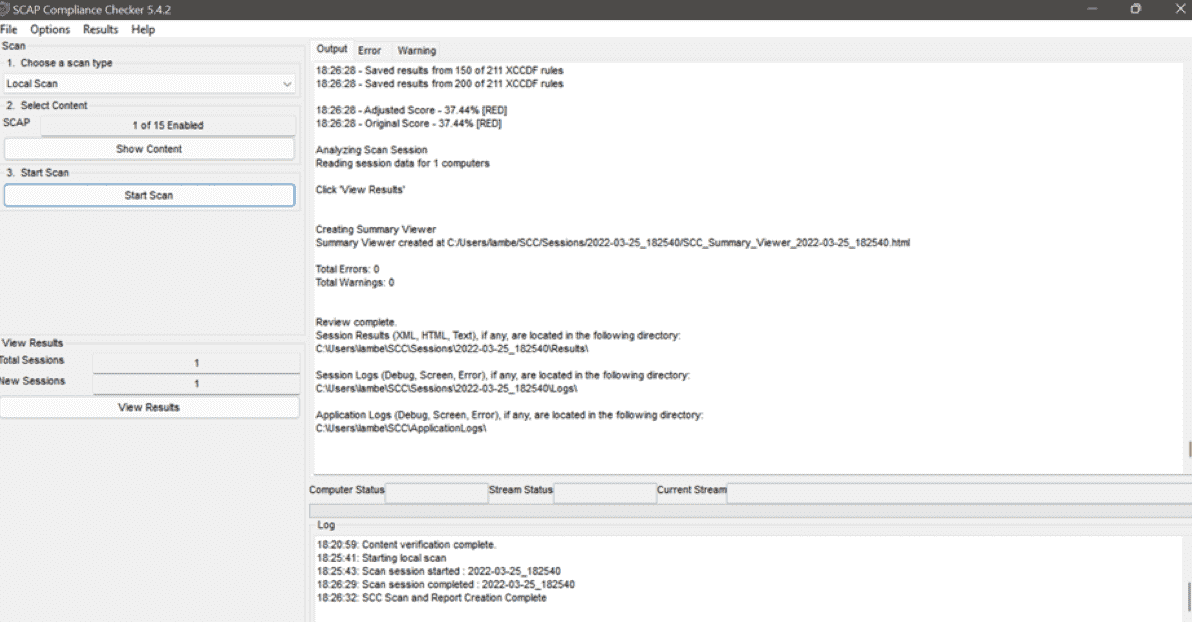
Again, this tool doesn’t automatically remediate non-compliant items. However, it’s still helpful in determining your compliance posture. You can then use the STIG Viewer for the action steps to remediate non-compliant items.
Overall, STIG offers limited tools to automate compliance. You’ll have to rely on third-party tools such as PowerSTIG to automate the implementation. Specifically, PowerSTIG is an open-source project that lets you create Desired State Configurations based on STIG guidelines.
CIS Implementation and Compliance Tools
The Center for Internet Security offers a tool similar to the SCAP Compliance Checker. It’s known as the CIS-CAT Benchmark Assessment Tool and is slightly more robust than the STIG tool.
For example, you can track CIS compliance over time, assign user roles, and collaborate across teams. You can also upload supporting documentation and monitor compliance with additional benchmarks such as PCI, HIPPA, and FISMA. This is much more than you get with the SCAP SCC.
The version of the tool is the CIS-CAT Lite. It is available for free download. This version lets you scan CIS Benchmarks compliance for Google Chrome, Ubuntu, and Windows 10. You’ll receive a compliance score from 1-100. You’ll also receive specific remediation steps to ensure compliance.
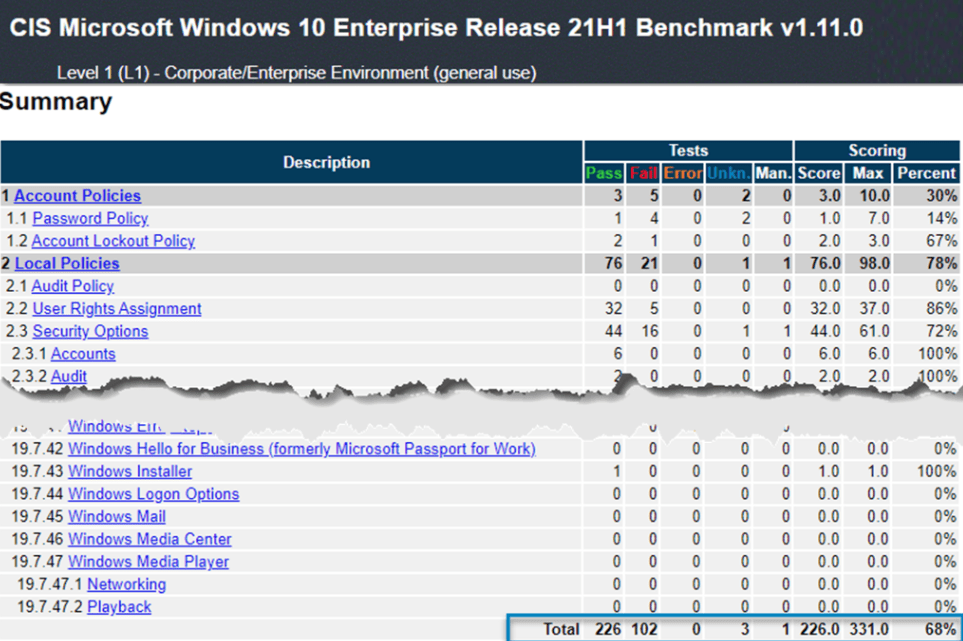
The CIS-CAT Pro version offers more features. For instance, you can scan for more than 80 CIS Benchmarks, unlike the Light version, which is limited to selected benchmarks. This version also supports more operating systems and applications. In addition, you can customize the benchmark contents and view assessment results directly from the CIS-CAT Pro dashboard.
However, you’ll need a paid CIS Membership to access the CIS-CAT Pro. The membership price starts at $1 452 per year. Discounts are available if you opt for a two or three-year membership.
Additionally, CIS Members get access to CIS Build Kits. These are available as Group Policy Objects (GPOs) for Windows and shell scripts for Linux. However, you can download and test a sample Build Kit for free before you decide if it is worth the membership.
The Build Kits also come with detailed deployment instructions for the specific system. In addition, they help to automate the implementation of many of the CIS Benchmarks.
STIG vs. CIS – Applications and Operating System Coverage
Winner = Draw
SITGs and CIS benchmarks offer impressive coverage for the most commonly used operating systems and applications. In addition, you’ll find coverage for most modern operating systems, including multiple versions of Windows, macOS, Microsoft Windows Server, Red Hat Enterprise Linux, Amazon Linux, Ubuntu, and CentOS.
The standards cover popular infrastructure software and platforms such as VMware and Cisco. However, the instances where STIG covers specific systems while CIS doesn’t and vice versa.
For example, STIGs do not cover Microsoft Azure, GCP, and AWS. Instead, you’ll need to rely on the DISA Security Requirements Guide (SRG), whose recommendations are more generic than STIGs. Similarly, CIS doesn’t have specific benchmarks for Red Hat JBoss F5 BigIP and IBM Websphere (zip). But you can find STIGs for these environments.
Overall, both STIGs and CIS Benchmarks offer sufficient coverage for most people. However, the choice may come from the specific environment and systems you’re working with. You can simply implement the available standards in this case.

