The Ultimate Manual to Shared Google Drive Data Loss Prevention
Nearly 30,000 companies worldwide rely on Google Drive for storing, syncing, and collaborating on data. But, these collaborative cloud spaces bring up data privacy and security concerns. As a result, Google Workspace unrolled a data loss prevention feature to allow admins more control over data security on personal and shared Google Drives.
What is Shared Google Drive Data Loss Prevention Anyway?
A significant challenge in a collaborative business environment is ensuring that all team members have the information they need in a central place. As a result, employees often spend unnecessary time attempting to consolidate and find crucial information. Shared Drives offer a solution to this problem, allowing employees to access and share information in a central location.
A shared drive is much like My Drive. Except that the organization, rather than individual employees, owns the data. This setup allows teams to collaborate in a shared location easily. In addition, members can create, share, and access data from any device.
This convenience comes with certain risks. For example, data in shared drives often include sensitive information such as credit card numbers, Personally Identifiable Information (PII), financial statements, or patient health information. As such, it is crucial to protect sensitive data from leakage, loss, or damage, whether unintentional or malicious.
Google Drive data loss prevention (DLP) refers to a set of functions designed to monitor your organization’s Google Drive accounts to prevent potential data breaches or unauthorized data transfer. These functions are built into the service to enhance data security. Admins can manage user access to data and impose restrictions to promote data security further.
How Shared Google Drive Data Loss Prevention Works
Google Drive data loss prevention essentially gives you control over the content users can share inside and outside the organization. To do this, Google Drive lets you create and apply rules to govern how users in a group, organizational unit, or domain can share sensitive content.
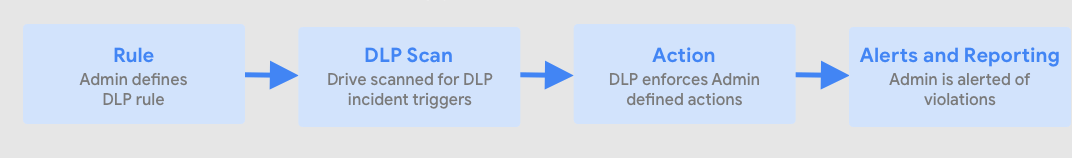
You begin by creating rules to define sensitive content that should be protected. For example, Google Drive has predefined classifiers for commonly entered data such as social security numbers, credit card numbers, bank account numbers, and phone numbers.
Alternatively, you can use a rule template or create your custom rules from scratch. You’ll also need to define actions for when a rule is violated. These actions may include warning end users, sending you an alert, or blocking externally shared links.
Next, DLP scans Google Drive files to detect rule violations. Then, it enforces the actions that you defined. Finally, DLP alerts you of any DLP rule violations. This system is designed to provide admins with better control over the organization’s data. It also adds an extra layer of safety besides the basic Google Drive encryption and other data security measures.
To recap, here is the process of Google Drive DLP:
- You (or the shared drive owner) create rules to clearly define what data needs to be protected
- DLP scans all drive files to detect rule violations
- DLP enforces the rules you previously defined
- DLP alerts you/the owner of rule violations
Here are two examples that demonstrate how Google Drive DLP works in the real world:
Example 1: UK Government Accidentally Shares Secret Plans for COVID-19 Contact Tracing App
Wired UK, a science and technology magazine, uncovered secret details for the NHS COVID-19 app. The incident happened when a government employee accidentally left the document on a publicly accessible Google Drive.
A magazine staff member found a link to the drive in a batch of published documents. Wired then alerted the NHS and the Department of Health of the publicly accessible document. The Google Drive account was quickly made private following the alert.
While the data leak didn’t lead to adverse consequences, things could have been a lot worse. The publicly accessible drive even contained documents labeled “OFFICIAL – SENSITIVE.” This example goes to show that classifying data according to risk level is not enough to protect it. Employees must also be vigilant when handling and sharing sensitive data.
Furthermore, a comprehensive DLP policy should have prevented the information from ending up on a public drive in the first place. The user and admin teams might even have received alerts about the compromise. Google Drive DLP crawls files to find sensitive data. So, the NHS would have easily avoided this incident by enrolling in the feature and using it appropriately.
Example 2: Protecting Against Unintentional Data Loss
Most employees think of cybercriminals and other malicious users any time DLP comes up. But unintentional data loss is a common concern for many organizations. For instance, a well-meaning employee may access a shared drive while working from home. However, the said employee may access the drive from an unsecured device or connection. Such a security lapse can put the team’s drive at risk of unauthorized access.
In another instance, an employee with Manager access may choose to rearrange files in a shared drive. While the files may not be lost, this situation can make it difficult for other employees to find the files. Also, a careless employee may accidentally delete files on a shared drive.
Moreover, unauthorized people can access an organization’s Google Drive if an employee’s device is stolen. The cybercriminals might then demand a ransom to secure the data. These incidents are common in business circles and can attract hefty fines and penalties for failing to secure customers’ private data adequately.
Fortunately, admins on shared Google Drives have the power to stop all these instances of unintentional data loss by:
- Blocking access to shared drives from unsecured devices
- Restricting access to modifying and moving files and folders
- Deleting user access in case of a stolen device
A comprehensive DLP policy also outlines what security teams should do in the event of a breach, depending on its severity.
How To Get Started With Shared Google Drives Data Loss Prevention
Below are a few critical steps to getting started with DLP for shared company drives.
Step 1: Classify Your Data
It is difficult to implement data loss protection if you don’t know which data needs protecting in the first place. So, data classification is a must for identifying sensitive data. Data classification involves categorizing data based on its sensitivity level. Here, users apply tags to all company-owned data. These tags may include:
- The location of the information
- The data’s sensitivity level
- The type of access required by users
How compliance regulations prescribe access
There are plenty of software tools you can use to automate this process. And Google also has a new beta data classification program you can sign up for. This program is currently only available to Enterprise plan Google Workspace users. The beta feature automatically classifies documents based on DLP rules. Here, you can create and apply labels to help organize data in shared drives.
Whatever data classification method you choose, be sure to determine data risk levels for all files in shared drives. Data risk categories include low risk, moderate risk, and high risk. Then, assign each file the appropriate tag or metadata.
Step 2: Create A DLP-Friendly Drive Structure
Your Google Drive account structure plays a significant role in data loss prevention. However, it may not always be clear who should get access to what information. For example, you may have all the admin staff on a shared drive. But only a few members need access to employee social security information to process payroll and taxes.
In this case, you can create groups based on who needs access to what information. This structure allows you to set access and sharing permissions appropriately, based on member roles within the organization.
When delegating members to shared drives, some factors to consider include their responsibility, authority, and job competency. This way, lower-level employees don’t get access to sensitive data that isn’t directly related to their duties. This structure is especially crucial in organizations with a large workforce.
Equally, create dedicated shared drives for external personnel, such as third-party contractors. You can create these groups based on projects. Finally, remember to delete users or groups when projects end. The same goes for departing employees with administrator access. Disgruntled employees may leak sensitive data, especially if there is a dispute surrounding their departure.
Step 3: Review Access and Sharing Permissions
Google Workspace allows admins to set up permissions for team members. This option gives admins more control over data security in shared drives. Different roles offer varying levels of access.
For instance, the Manager role gives users complete control of the drive’s contents, including the ability to modify shared drive settings, rename shared drives, move files between shared drives, and delete files and folders. As such, it is worth thinking carefully about which users you assign this role to. The Manager role is the highest level of access, while the Viewer role is the most restrictive, only letting the user view the shared drives, files, and folders. There are a total of five access levels.
Consider giving users only the access required to do their job. For example, the Commenter role allows users to view files and folders and comment on files without making permanent changes. Of course, you can always change members’ access levels if needed.
Step 4: Create a DLP Policy For External File Sharing
One of the most significant data loss risks is users sharing sensitive information outside the organization. As such, it is crucial to have complete control over files shared outside the organization. Fortunately, Google makes this process easy.
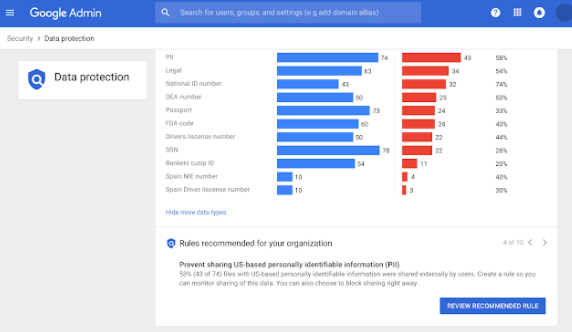
Google Drive already comes with ready-to-use DLP rules. Moreover, Google suggests personalized rules based on your data protection insight report. Admins also can edit and customize the rules if needed. This way, you’ll have complete control over the information users can share.
You can view the rules Google recommends for your organization by navigating to Admin Console > Security > Data Protection.
Sometimes, external file sharing is inevitable. So, it is worth creating a clear framework for how files should be shared externally. Google Workplace allows you to define a standard sharing policy covering all product suites, including Google Docs, Drives, and Gmail. Additionally, you can restrict external sharing only to trusted domains.
Aside from restricting external sharing for sensitive files, it is equally important that you educate employees on external file sharing. This way, employees can take ownership of data loss prevention. They’ll understand secure ways of sharing information externally, as well as the types of files they can’t share. It cannot only be up to the administrator to ensure that sensitive data doesn’t leak out of the organization.
Finally, don’t forget to develop incident management processes. These processes define your procedure for detecting, investigating, and responding to policy violations. A good incident violation process will allow IT teams to respond quickly to address vulnerability issues.
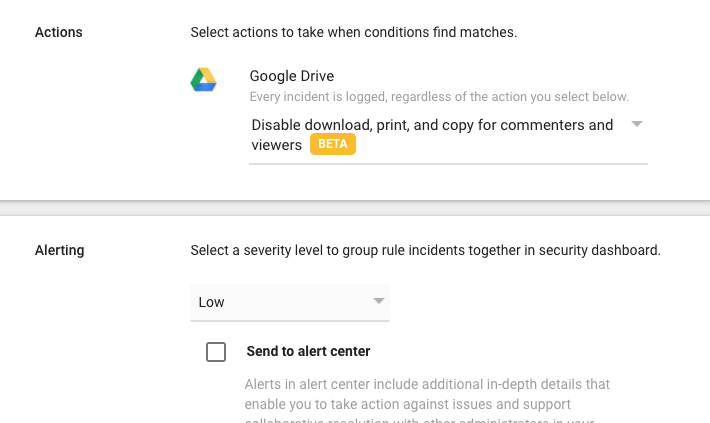
Step 5: Set Up Google Drive DLP Alerts
Google Drive DLP alerts make it easier to monitor data security without having to run periodic audit scans. This feature also makes it easier to respond to policy violations quickly and measure the policy’s success over time. Here, you’ll receive an alert in the alert center every time there is a policy violation.
Additionally, you can go to the alert center to get more information about the triggered rule. Google offers up to 50 alerts per day for each rule. In addition to alerts, it’s also worth monitoring Drive activity for unusual behavior. For example, increased deletions or external file sharing may indicate suspicious activity.
The Admin console offers two other great ways to keep tabs on Drive activity. For one, the file exposure report provides a complete breakdown of how file sharing exposes your organization’s data. The report displays details such as the most frequently triggered DLP rules, the most frequently shared-to external domains, and the different sharing methods on the shared drive.
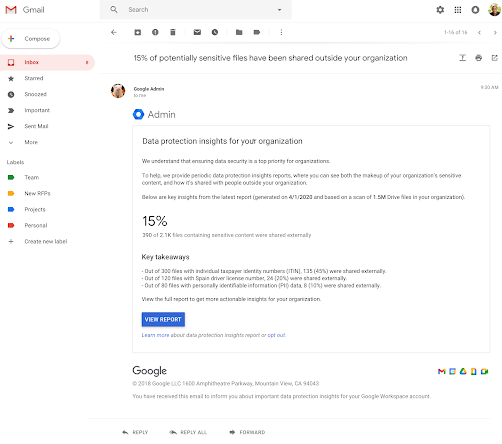
Secondly, the data protection insights report offers a candid look at your sensitive content. For example, the reports show how many files in the shared drives contain sensitive information, the type of sensitive information, such as social security numbers, and the number of sensitive files that have been shared externally.
These reports are generated automatically, so you don’t have to set up any DLP rules. They are great for understanding sensitive information in shared drives so you can make informed decisions to protect it.
Lastly, DLP alerts help to reduce alert fatigue for security teams. Security teams don’t have to guess what or who triggered the alert. Instead, admins can quickly answer the who, what, and where, allowing them to move swiftly to incident management.

