The Ultimate Manual for Security Awareness Training for Employees
A successful security awareness training program offers numerous benefits for your employees. Such a program can help reduce cyber threats, prevent downtime, improve your reputation, and make employees aware of their role in protecting critical business assets. We outline everything you need to know about implementing a successful security awareness training program to reap these benefits.
What is Security Awareness Training for Employees Anyway?
Security awareness training is a formal education program designed to train employees on protecting an organization’s data, computer systems, and colleagues from cyberattacks and other internet-based threats. The employee training program may sometimes include third-party actors such as contractors, vendors, and business partners.
A good security awareness training program is people-centric. It identifies people, usually employees, as the weakest link in effective information security. It is a justifiable proposition. Numerous studies, including IBM’s Cyber Security Intelligence Index Report, reveal that 95% of cybersecurity breaches result from human error.
Therefore, security training programs aim to equip employees with the necessary tools and knowledge to identify, prevent, report, and resolve cybersecurity events before they severely impact the organization. These training programs also typically include any employee with access to a work computer, regardless of their position, cybersecurity knowledge, or technical aptitude.
How Security Awareness Training for Employees Works
The particulars of security awareness training may vary from one organization to another. But, certain fundamentals remain the same across training programs. Therefore, we can rely on these fundamentals to understand how an employee security awareness program works.
Training Content
The first critical element of an effective training program is the content. Content encompasses the specific topics covered during the training.
The training content isn’t one-size-fits-all, even within a single organization. For example, a typical organization has different employees, including interns, new hires, seasoned employees, C-suite executives, and contract workers. Additionally, some roles are more vulnerable to targeted cyber attacks than others.
For instance, social engineering attacks typically target c-level executives, executive assistants, accounting and finance employees, and engineering staff. These attacks use psychological manipulation and impersonation techniques to trick employees into revealing sensitive information or data.
Therefore, the content should be tailored for each role. Furthermore, contractual obligations and government regulations may require role-based security awareness training in some industries. While not always mandatory, it’s still worth implementing role-based awareness training.
Finally, the most commonly covered topics in employee security awareness training content include:
- Phishing
- Passwords
- Ransomware
- Information security
- Removable media
- Social engineering
- Physical security
- Browser security
- Incidence response
- Mobile security
- Business email compromise
Most successful programs adapt the content to industry-specific and current threats.
Training Sessions
Training sessions refer to how the training material or content is delivered. Most organizations use a mix of formal and informal training sessions.
Formal training sessions typically cover technical and complex security awareness material. These sessions are structured and depend on well-developed teaching systems. The instructor-led sessions also include assessments and certifications at the end of the course to measure learning outcomes.
However, formal training sessions can be dull, even with visual aids such as charts and graphs, videos, graphics, and slide presentations. Therefore, formal training usually makes up only a tiny proportion of the overall training program.
Many organizations use informal training in tandem with formal training. Informal training is less structured, more flexible, and generally more engaging. The training models may include collaborations, videos, and webinars.
Regular Refreshers
Formal and informal training sessions take place a few times a year. These sessions may be based on departments or all-hands sessions. They typically last a few hours, usually two hours.
While effective for delivering course materials, training sessions aren’t enough to improve employee security awareness. The training material is soon forgotten, and employees may revert to their old high-risk behaviors.
Therefore, most training programs include regular refreshers, usually monthly. The refreshers may have valuable tips delivered to employees via email, monthly newsletters covering the latest cybersecurity trends, or survey questions to provide feedback on the training sessions.
Regular updates help employees to keep cybersecurity best practices at the top of their minds throughout the year. These refreshers also don’t have to be monthly. You can choose the appropriate cadence to avoid bombarding or overloading employees with information, regardless of its usefulness.
Testing
Good employee security awareness training should have a way of measuring the learning outcomes. Tests are a reliable measure of the program’s success or failure. So most training programs include some form of employee testing.
While some organizations still rely on written tests, there are far more exciting and effective testing methods. These include:
Password Enumeration Tests – Many employees still ignore proper password hygiene despite this being an elementary cybersecurity best practice. A Password Enumeration Test attempts to subvert weak passwords, such as birthdays, children’s names, pet names, addresses, etc. An ethical hacker or third-party security expert can conduct this test to reveal the extent of weak passwords.
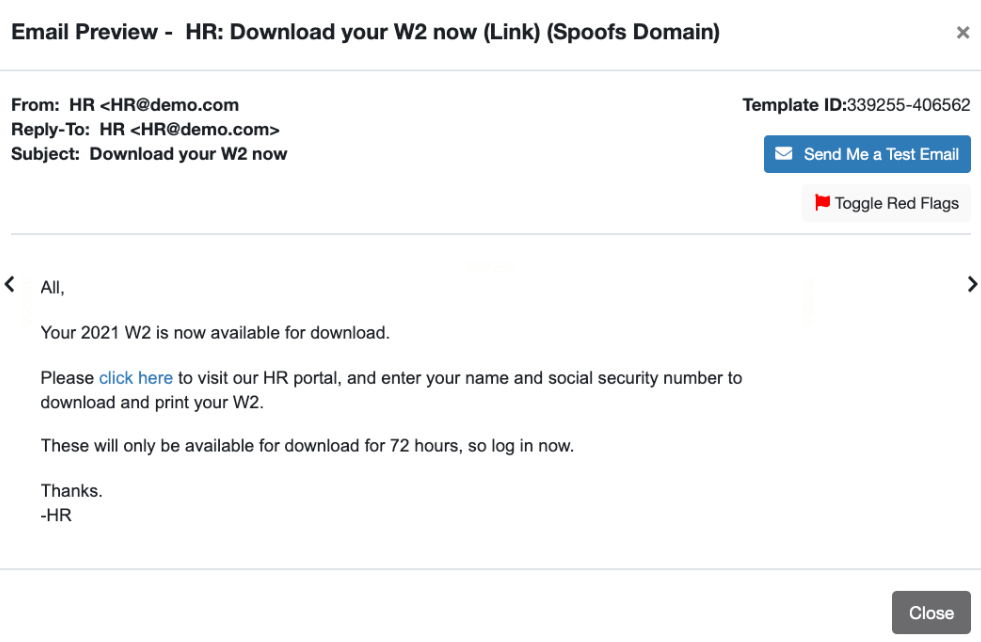
Simulated Phishing Test – This test involves sending malicious dummy links to employees. The object is to see how many employees can potentially fall victim to phishing attacks. The links may include dummy malware or a request to enter sensitive information on a dummy website.
USB Drops – This is a simple test where an IT personnel or consultant drops USBs in common areas such as break rooms or parking lots. These USBs contain special keys that track who plugged the USB and which machine. It’s an effective way of gauging whether employees appreciate the importance of not using unknown USB drives.
Eye Test – Again, a security consultant or IT personnel may walk around the office. They’ll be looking for overt signs of poor security awareness, such as unsupervised third-party visits, unattended logged-in PCs, sensitive documents left on printers, and unapproved file sharing methods such as USB drives and Dropbox.
Reporting
It’s good practice to report on the results of the tests we outlined above. These reports help determine the program’s success. They are also a great way of identifying areas for improvement.
Regular Program Updates
The cybersecurity landscape is constantly shifting. Therefore, a good employee training program should be reviewed and updated annually. This update involves refreshing the training content to cover the newest threats and trends.
It’s also helpful to conduct annual surveys and quizzes to gauge the level of security awareness among employees. You can use this information to guide the training program update.
Now let’s look at some examples of successful security awareness training.
Example 1: Boosting Engagement with Interactive Security Awareness Training
Most organizations rely on the IT department to create their employee security awareness training program. This makes sense since the IT staff is the backbone of any organization’s network security. However, such training can be too technical for the average employee.
Interactive awareness training is a terrific solution for boosting employee engagement. This module relies less on traditional text and video delivery. The session may include slides asking participants to identify a suspicious email.
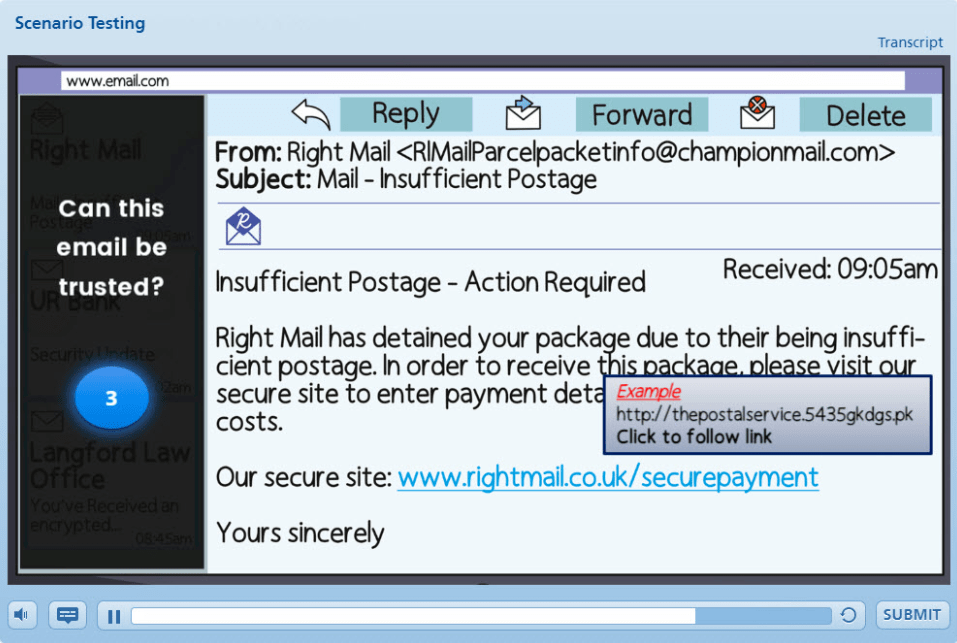
The visual imagery and practical scenarios are perfect for internalizing the training material. These interactive sessions also typically use ordinary language that most employees understand. In addition, technical jargon may be difficult to grasp. Finally, many training vendors offer interactive modules, so you don’t have to worry about developing them in-house.
Example 2: Security Awareness Training with Attack Simulators
Similarly, simulated attacks are a great way of reinforcing cybersecurity best practices in a context your employees understand. This method doesn’t rely on cramming course material with the hope of passing a final exam. Instead, employees are tested on their competence in dealing with real-world threats that may come up in their daily workflow.
The advantages of simulated attacks are two-fold. First, the simulation may be delivered before the training program to assess your employee’s current security awareness status. It’s an excellent solution for identifying areas to emphasize during the training. Next, the simulation may be delivered after the training to gauge the program’s effectiveness.
The most commonly used tool is the phishing simulator. It makes sense since most social engineering attacks are based on phishing. These programs also cover multiple phishing attacks, including spear phishing and clone phishing.
How to Get Started With Security Awareness Training for Employees
Getting started with a security awareness training program for employees isn’t difficult if you know where to start. Below are a few action steps to help orient your program towards success from the beginning.
Create a Structure for Your Awareness Training Program
The first step toward an effective training program is to create a structure for designing, developing, and implementing the training activity. Unfortunately, who should be responsible for creating the program is not always apparent. However, there are three main options for structuring your training program.
The first option is to designate a central authority to oversee the entire training program. For example, the central authority might be the IT department or human resources. The central authority is in charge of the program’s aspects, including a budget, scheduling, strategy development, planning, training material, etc.
The central authority is also responsible for the assessment after the training program. It is an effective model for small organizations. It also works well for organizations with highly structured IT departments.
The second option is for the central authority to conduct a needs assessment and define the strategy for the training. Then, the budget allocation, course material development, and scheduling are delegated to management officials. This option is perfect for role-based training. The various departments can take charge of implementing training programs that fit their mission.
Finally, the third option is to leave the awareness training to the various department heads. There’s no central authority except a program manager who distributes broad training awareness policy and expectations. This model is perfect for large organizations with decentralized structures or organizational units.
Conduct a Needs Assessment
Security awareness training is a broad concept that doesn’t specify what the training should include. The cyber threat landscape is also porous, with numerous subject matter materials. Therefore, a needs assessment is crucial for determining the specific needs the training should address.
Including all major stakeholders in the needs assessment phase is also essential. These stakeholders include executive management, system administrators, system owners, security personnel, IT support personnel, operations managers, and system users. The idea is to gather as much information as possible to help you prioritize the training program’s needs.
The techniques for conducting a needs assessment include organizational surveys, stakeholder interviews, recommendations from oversight bodies, and events analysis. Finally, some of the questions that the needs assessment should answer include:
- The awareness training required
- The current activities being conducted to fulfill the identified training requirements
- The effectiveness of the current awareness training activities
- The gap between the present and desired awareness training
- The most critical awareness training needs
Finally, decide the specific training requirements. For instance, assess if your existing infrastructure, such as computers, bandwidth, video cards, and speakers, can deliver an effective training program. This evaluation should be based on the delivery method you’ve chosen.
Develop Your Awareness Training Plan
You should have gathered enough information to develop a strategy for implementing the employee awareness training. The plan is a working document that outlines your process. It should include:
- Existing policies and regulations that mandate the awareness training
- The scope of your training program
- Specified roles and responsibilities for designing, developing, implementing, and maintaining the training material
- Clear goals and desired outcomes for each training session
- The program’s learning objectives
- Deployment methods
- How the success of the training program will be measured
- The frequency of the training
You can find awareness training plan templates online. These templates are helpful, so you don’t miss any crucial plan elements. They also speed up the planning process and can be adjusted to fit your training requirements.
Establish Your Priorities
Your plan charters the path towards unrolling a successful employee awareness training program. However, you might need to implement the plan in phases due to budgetary constraints. Therefore, prioritizing the action steps is crucial for deciding which part of the plan is scheduled first.
Some of the considerations for prioritizing your program plan include the availability of resources and materials, the organizational impact of the program, and your current state of compliance with the relevant regulations and standards.

