SAST vs. DAST: Side-by-Side Comparison
Even the best developers in the world write code that’s susceptible to breaches and data loss. Application security testing is critical to ensure your code is free of security risks and vulnerabilities.
Today’s risks are greater than ever before, as the list of potential software vulnerabilities seems to be growing exponentially every year. When you pair this with development teams trying to release new deployments in faster cycles, there’s a good chance your applications aren’t bulletproof.
That’s why SAST (static application security testing) and DAST (dynamic application security testing) are so important. Both of these application security approaches help teams test and release secure software.
This in-depth guide compares the features, benefits, drawbacks, pricing, and use cases of SAST and DAST. You can use the information below to see which application security method is right for your software.
Our Recommendation = Use SAST
SAST and DAST are both viable options to test security vulnerabilities in software.
In a perfect world, your team will use a combined approach of SAST and DAST for application security. But if you’re forced to choose between the two, go with SAST.
SAST is a white-box application testing method. This means that you’ll be evaluating a wide range of static inputs, including documentation, design, specification, requirements, and application source code, to test for known problems.
There are lots of SAST tools out there that will scan your code, frameworks, and libraries. During the process, the scan will detect issues and security vulnerabilities in the application and identify the exact location of the problem.
The SAST approach can be used early and often during the development process. There’s no need to have a running application to start a scan, which means you can detect security vulnerabilities throughout the development process. As soon as a developer on your team commits code to your source code repository, you can begin using SAST.
Here are some of the top advantages of using SAST:
- Detects known issues based on internationally recognized security standards, safety, and quality for coding.
- Allows for early detection and fixes, which translates to lower remediation costs.
- Easy to automate and scale.
- Quickly identifies the exact location of a known vulnerability and its cause.
Overall, SAST is arguably the best quality assurance method for any software deployment throughout the development process.
When to Use DAST Instead
DAST is still a highly effective method of application security testing. It uses the opposite method of SAST—black-box testing instead of white-box testing.
The black-box approach is used when the testers don’t have any knowledge of the software. This is also known as the “hacker’s” approach instead of the “developer’s” approach. In this scenario, testers rely purely on the application’s available inputs and outputs.
That’s why black-box tests are dynamic. Whenever the application runs, the number of inputs and outputs is constantly changing, along with the data consumed and released.
To use DAST for application security testing, you must have a working version of the app. This means you’ll be using DAST in the later stages of development when the application is ready for release.
A dynamic approach to application security testing means you can test a wide range of vulnerabilities, including SQL injections, authentication issues, XSS (cross-site scripting) attacks, encryption problems, and more.
In fact, DAST can detect all of the vulnerabilities listed on the OWASP top ten. This makes DAST extremely valuable to the IT security community.
Let’s take a look at the top benefits of using DAST:
- Assesses the entire application and full system environment while the app is running.
- Tests for vulnerabilities while attempting to break in from the outside.
- Checks resource usage, memory consumption, hard application failures, and third-party interfaces.
- Looks for SQL injections, XSS attacks, and cookie manipulation.
DAST is one of the best ways to test a running application for security vulnerabilities.
Pricing – Is SAST or DAST the Better Deal?
When comparing SAST software and DAST software side-by-side, you’ll find a wide range of different price points between solutions. There are lots of factors to consider here, including your team size, application type, and use cases.
But generally speaking, SAST software will be more affordable than DAST software.
SAST is also cheaper than DAST beyond the initial software costs. That’s because SAST can be applied early in the development process, as soon as code gets committed to source code repositories.
Vulnerability issues are much less expensive to fix in the early stages of development, which is another reason why so many development teams lean towards SAST for quality assurance.
DAST software is usually more expensive than SAST tools. In addition to the software price, the costs associated with fixing security vulnerabilities on a running application are significantly higher. So you can expect your total DAST investment to be more than the SAST counterpart.
Let’s take a look at some real prices from SAST and DAST solutions so you can compare the costs.
DeepSource is a reliable solution for static analysis. The software makes it easy for developers to find and remediate security vulnerabilities and performance issues throughout the software development lifecycle.
The entry-level plan for up to three team members and one private repository is 100% free.
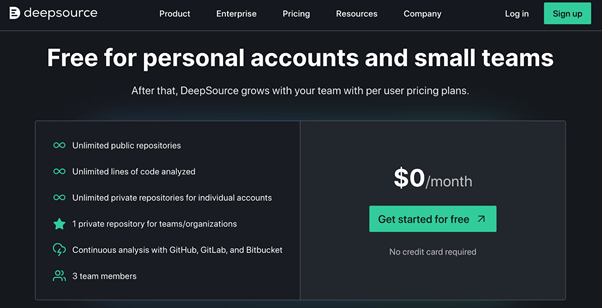
This is an excellent option for single developers and small teams.
Even for growing teams and developers that want a bit more from a SAST solution, DeepSource is surprisingly affordable.
Here’s a look at its paid subscriptions:
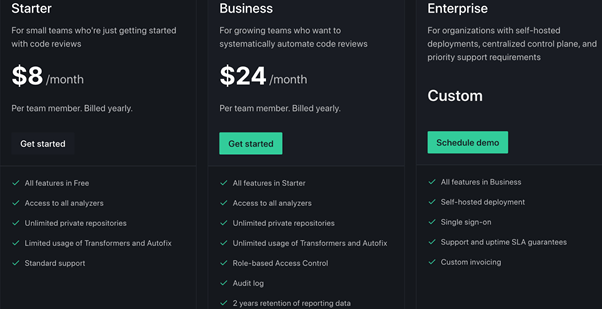
For just $8 per user per month, the software will scan an unlimited number of private repositories. That’s huge for any team that needs SAST as they’re working on more than one project.
Now let’s turn to DAST pricing. Most of the DAST software you’ll find on the web requires you to sign up to see a demo to get more information about custom pricing. But there are some basic tools out there that aren’t really enterprise-grade, and you can sign up without a demo.
Detectify is one of those solutions.
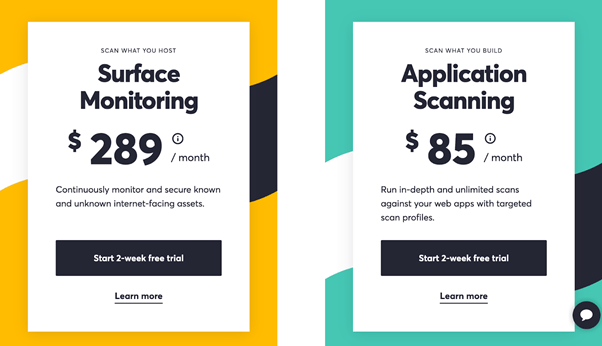
The application scanning tool starts at $85 per scan profile per month with an annual subscription. The month-to-month rate starts at $105 per scan profile.
This solution is geared towards web applications. So it won’t accommodate all of your deployments if your team builds native apps.
Even for a basic solution, you can see the significant price difference between SAST tools and DAST tools.
CI/CD Pipeline Integration
Winner = SAST
Compatibility with your existing continuous integration and the continuous delivery pipeline is critical whenever you’re evaluating a solution to assist with software development. SAST definitely has the edge over DAST in this category.
SAST can be easily integrated into the development stage, meaning your development team can monitor the code on a regular basis. This includes every phase of the continuous integration process, from automated repository scans to security analysis and application testing.
Since dynamic testing tools aren’t used until after the application has been deployed, it’s not really suitable for CI/CD pipeline integrations.
Run Time and Environment Issues
Winner = DAST
As the name implies, SAST is only scanning the static source code. Since the application isn’t actually running during this process, the SAST method can’t detect issues related to run-time vulnerabilities and problems with the environment.
The dynamic approach used for DAST does allow you to find environment-related issues and any existing run-time problems.
This is crucial for finding any issues outside of the application. For example, a defect in third-party interfaces could not be identified using SAST. But DAST makes it possible to find these types of problems with ease.
Mitigation and Remediation
Winner = SAST
The continuous and automated scans associated with SAST make it much easier to mitigate and remediate any issues. Security vulnerabilities are found early in the development process, and the exact location of the issue is also identified.
This process allows developers to quickly detect and fix the problem. It also helps them avoid the same mistakes moving forward as they continue committing code to the repository.
DAST mitigation and remediation are a bit more complex. Unlike SAST, dynamic testing won’t provide the exact location of an issue or vulnerability. So security teams, quality assurance agents, and developers must look through the code to detect the issue, which is obviously time-consuming.
Since the application has already been deployed by the dynamic testing stage, fixing those issues is more complex as well.
False Positives
Winner = DAST
SAST tools are only as good as the rule set that you’re running. Some rules are a bit more ambiguous, which leads to a high volume of false positives.
Effective static application security testing will require human intervention. Even though many of these solutions run automatically, a quality assurance agent or a developer will need to look at the issues manually to see if the issues are legitimate. This essentially neutralizes the benefits of using automation for SAST.
Before you sign up for SAST software, read the reviews and see if existing users are having problems with lots of false positives. While some false positives will still be normal, you obviously want to limit the number of items in your issue tracking system—especially the ones that don’t belong there.
DAST doesn’t have the same challenges with false positives.
Testing Scope and Coverage
Winner = Tie
In terms of what can be tested between SAST and DAST, each method has its benefits. One really doesn’t have an edge on the other since they both can’t actually test everything.
SAST tools help identify server-side and client-side vulnerabilities with a high level of accuracy. These tools can also accommodate a wide range of code for different programming languages and application types.
DAST can look for vulnerabilities in external libraries, template codes, legacy systems, and more. It’s a great option for testing new vulnerabilities and different source codes. You can use DAST to find XSS attacks, encryption issues, authentication problems, SQL injections, and more.
This is another reason why effective application security testing uses both SAST and DAST. Since each one has a unique approach, you’ll have a wider testing scope if you’re using both methods.
Application Support
Winner = SAST
As previously mentioned, the type of application you’re building will have a significant impact on whether SAST or DAST is right for you.
SAST is more versatile for application security testing. It typically supports a wide range of software, including web apps, web services, and thick clients.
DAST is really only useful for web applications and web services. It’s usually not very useful for testing other types of software applications, like native apps.
You just need to make sure that your SAST software is compatible with the programming language you’re using. Some solutions support all major programming languages, like Java, Swift, Objective-C, C++, .Net, and more. But others are a bit more use-case specific.
Holistic Security Overview
Winner = DAST
DAST has the edge over SAST in terms of big-picture security insights. SAST focuses strictly on the source code of an application. But DAST takes this a step further.
With dynamic application tests, you can assess a wider range of different application types, web assets, and sites across unique origins and programming languages.
This gives you a deeper understanding of the application’s security status and its visibility across different environments. As a result, DAST makes it easier to test outdated technology and vulnerabilities beyond your application source code.
Implementation
Winner = Tie
SAST and DAST are equally challenging to deploy. Each one has some easy steps and quick wins, but both have some tricky parts that require appropriate technical knowledge.
Static application security testing requires intimate knowledge of the source code. Testers using SAST will have full access to the framework and design of the application. So it’s best used by developers or quality assurance team agents who are familiar with what’s happening throughout the development process.
An outsider or third party will definitely have problems using SAST. As previously mentioned, SAST tends to yield lots of false positives. This also adds to the complexity.
DAST is the hacker approach, meaning the tester doesn’t have any prior knowledge of the technology or framework that the application was built with. Obviously, this comes with its fair share of challenges as well.
Overall, you can’t definitively say that SAST or DAST is easier to use than the other.

