Ransomware Statistics
Ransomware is a growing problem in the world of data security.
While ransomware attacks aren’t new, ransomware incidents have gained international attention in recent years. We’ve seen attacks on supply chains, healthcare systems, government organizations, and even educational institutions.
Is your business prepared for a ransomware attack? This in-depth guide will explain everything you need to know about ransomware trends and statistics, how to prevent ransomware attacks, and what to do if you’re infected with ransomware.
What is Ransomware?
Ransomware is an evolving form of malware. Malware is defined as software that’s intentionally created to harm computers, servers, or networks. With ransomware, the malicious software infects a system and prevents a user from accessing information until a ransom is paid.
Ransomware is designed to encrypt files on a device or storage system. It could lock the screen of a computer or simply prevent the user from accessing specific files.
Historically, ransomware was all about cybercriminals attempting to get a payout. But now, hackers are using ransomware for double extortion. In addition to demanding payment to unlock a system, cybercriminals are threatening to leak company data and personal information if payment isn’t received.
Top 101 Ransomware Statistics You Need to Know
Through extensive research on the latest ransomware trends, I’ve identified the most significant ransomware statistics that everyone needs to know about.
Before we dive into the different ransomware statistics by category, I want to quickly share the top 10 most eye-opening ransomware facts:
-
- There are over 4,000+ ransomware attacks per day.
- 37% of organizations were attacked by ransomware in 2021.
- On average, just 65% of data gets restored after a ransom is paid.
- 54% of organizations infected with ransomware say the hackers were successful in encrypting the data.
- In 2021, an insurance company in the US paid hackers a $40 million ransom.
- There were over 304+ million ransomware attacks across the globe last year.
- 68% of US companies infected with ransomware decided to pay the ransom.
- 84.5% of companies worldwide that did not pay the ransom still managed to recover data.
- On average, organizations experience 21 days of downtime after a ransomware attack.
- Half of all ransomware attacks infect more than 20+ computers in an organization.
Below you’ll find even more ransomware statistics, segmented by category and relevance.
Ransomware Statistics by Industry
Certain industries are targeted more than others by ransomware attacks. Sectors like government, education, healthcare, and financial services are typically the top targets.
Government Ransomware Statistics
The ransomware stats below provide greater insight into local, state, and national government organizations fighting ransomware.
-
- 33% of all cyber attacks on government organizations are ransomware.
- Just 38% of government employees are trained to prevent ransomware attacks.
- City mayors in 40 states have agreed to deny all ransom payments to hackers.
- 48 of 50 US states were attacked with ransomware in a five-year period.
- Ransomware attacks against municipalities increased by 60% from last year.
- Roughly 950 government entities in the US were attacked with ransomware in 2019.
- 17% of state and local government organizations paid the ransom.
Government entities tend to be top targets of hackers because the data is so sensitive. The data targeted can range from voter records to confidential information. If that data was leaked or sold on the open market, it could prove catastrophic for the organizations involved.
With that said, less than 20% of government organizations targeted by ransomware will actually pay the ransom. As you can see, city mayors collectively agree not to pay a ransom demanded by cybercriminals.
Education Ransomware Statistics
Public schools, K-12 institutions, colleges, universities, and other higher education institutions are all vulnerable targets to ransomware attacks.
-
- The average ransomware recovery cost in the education industry is $2.73 million.
- Ransomware attacks against universities doubled between 2019 and 2020.
- Over 1,680+ higher education institutions have been impacted by ransomware since 2020.
- 66% of colleges lack basic security configurations for email.
- K-12 schools are experiencing an 18% increase in ransomware attacks.
- More than 200 universities in the US were affected by data theft last year.
Schools have tons of sensitive information on file about students and faculty. Generally speaking, hackers target schools because these organizations lack proper IT security standards. Devices, networks, and records could be easy targets for hackers to exploit.
Healthcare Ransomware Statistics
The healthcare sector is another hard-hit industry by ransomware. If healthcare networks or devices are compromised, it puts patient care at risk.
-
- 50% of all healthcare data breaches come from ransomware.
- Ransomware attacks have cost the healthcare industry more than $157+ million in five years.
- 74% of ransomware attacks in the healthcare space target hospitals and health clinics.
- 26% of attacks target medical labs, nursing homes, medical supply companies, and private practices.
- The 2015 Anthem security breach affected up to 80 million individual records.
- 67% of healthcare organizations have been targeted by ransomware.
- 34% of healthcare institutions will pay a ransom to get the data back after an attack.
- 50% of IT professionals in the healthcare space say that the industry is not ready to handle ransomware threats.
- It takes healthcare organizations an average of 300 days to discover a data breach.
As you can see from the numbers, healthcare organizations are more likely to pay a ransom compared to companies in other industries.
It’s also eye-opening when you see that nearly two-thirds of all healthcare companies have been targeted by ransomware. When a healthcare company experiences a data breach, it takes the organization nearly an entire year to identify the problem.
Finance and Banking Ransomware Statistics
Banks, credit unions, and other financial institutions are obviously a prime target for cybercriminals. These types of data breaches can give hackers direct access to individual bank records, account numbers, and money.
-
- The banking industry experienced a 1,318% year-over-year increase in ransomware attacks in 2021.
- 90% of all financial institutions have been targeted with a ransomware attack.
- Banks in the US saw a 520% rise in ransomware and phishing attempts in 2020.
- 62% of financial service organizations were able to restore encrypted data from backups.
- 25% of banks pay the ransom demanded by hackers.
- 33% of financial service organizations got less than half of the data back after paying the ransom.
- The average ransomware recovery cost in the financial services sector is $2.1 million.
- Ransomware attacks are increasing against smaller banks and credit unions with less than $35 million in annual revenue.
It should come as no surprise to see this industry experiencing such a significant year-over-year increase in ransomware attacks.
Many of the organizations in this space have cyber insurance policies to help cover the costs of ransoms demanded by hackers. But just one in four banks will actually pay a cybercriminal during a ransomware attack.
Cost of Ransomware Statistics
The financial impact of ransomware has reached astronomical numbers. The ransomware stats below speak for themselves:
-
- The average ransom payment made by a mid-size organization is $170,404.
- The average cost to mitigate a ransomware attack is $1.85 million.
- Hackers received a $40 million ransom payment from CNA Financial in 2021.
- The average ransomware attack against a higher education organization costs $447,000.
- The combined costs of ransomware incidents exceed $7.5+ billion per year.
- It takes businesses an average of 287 days to recover from a ransomware attack.
- A startup company called GroupSense negotiated a $200,000 ransom to hackers after the initial ransom demanded was $1 million.
- Ransomware attacks cost businesses around 15 days of downtime.
- The cost associated with ransomware downtime averages $8,500 per hour.
- Businesses with over 100+ employees are four times more likely to pay a ransom.
- Ransomware costs will exceed $20 billion in 2021.
Unless we can collectively improve IT security standards and ransomware mitigation practices, these costs will continue to rise in the coming years.
Cryptocurrency Ransomware Statistics
Due to their anonymity, cryptocurrency and ransomware tend to go hand in hand.
-
- BTC-e, a cryptocurrency exchange platform, was responsible for cashing out 95% of ransomware payments until the US government seized the website in 2017.
- 7% of ransomware payments in 2020 were sent to a cryptocurrency address.
- Hackers responsible for the Colonial Pipeline ransom received over $90 million in bitcoin.
- UCSF paid hackers $1.14 million in bitcoin during a 2020 ransomware attack.
- 50% of ransom payments were paid in bitcoin in 2018.
Many hackers rely on crypto payments in an effort to keep ransom money untraceable. That’s one of the many reasons why we see payments made in bitcoin and crypto.
Ransomware Statistics by Country
Below you’ll find the percentage of organizations by country that were hit with ransomware attacks within the last year. All of the data comes from Statista:
-
- India – 68%
- Austria – 57%
- United States – 51%
- Israel – 49%
- Turkey – 48%
- Sweden – 47%
- Belgium – 47%
- Switzerland – 46%
- Germany – 46%
- Australia – 45%
- Spain – 44%
- Philippines – 42%
- Canada – 39%
- UAE – 38%
- Brazil – 38%
- Global Average – 37%
- United Kingdom – 35%
- Chile – 33%
- Netherlands – 32%
- Italy – 31%
- France – 30%
- Czech Republic – 30%
- Malaysia – 30%
- Singapore – 30%
- Mexico – 25%
- South Africa – 24%
- Nigeria – 22%
- Saudi Arabia – 17%
- Japan – 15%
- Poland – 13%
Here’s a visual representation of the data, showing the top 15 countries and the global average:
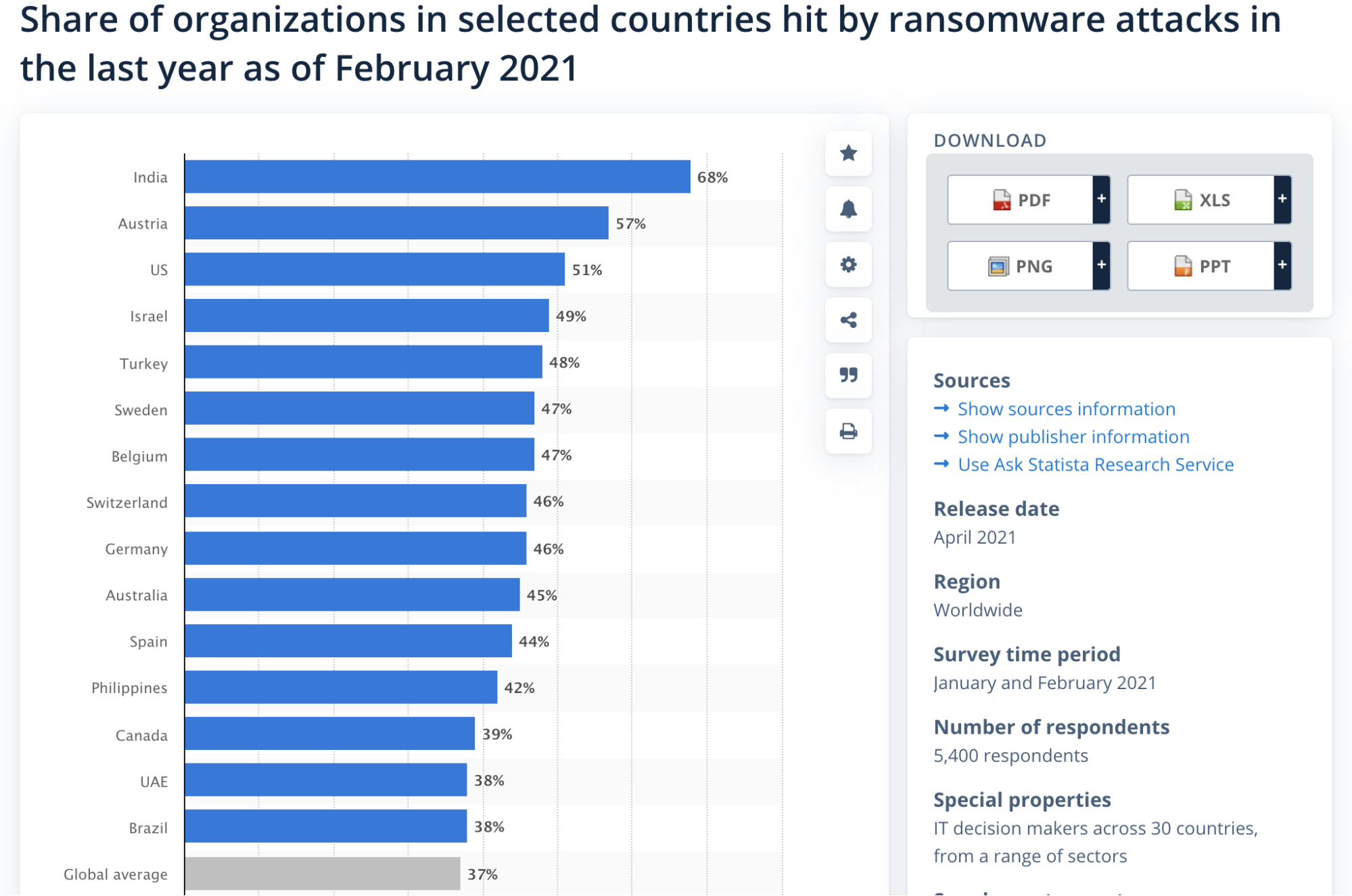
It’s amazing to see how ransomware incidents disproportionately impact businesses across the globe. Some countries are significantly higher and lower than the worldwide average.
Mobile Ransomware Statistics
Everything mobile has been trending upward for years now. Mobile ransomware stats are no exception.
-
- More than 4.2+ million people in the US have been victims of mobile ransomware attacks.
- Over 60,000+ mobile ransomware Trojans were detected in 150+ countries worldwide.
- There are over 4,000 mobile ransomware variants.
- Over 900,000+ Android devices were hit with the ScarePackage ransomware within 30 days in 2020.
- The media and information communications industry, which includes mobile communication providers, was targeted by 10% of all ransomware attacks last year.
With smartphones never leaving our side, it’s clear that hackers are looking for new ways to target these devices with ransom attacks.
Ransomware Trends and Recent Ransomware Attacks
Here are some additional ransomware trends that I thought were worth mentioning. The ransomware stats below also include some of the most relevant and infamous ransomware incidents in recent years:
- Ransomware is the fastest-growing type of malware.
- Experts predict that ransomware will cost $6 trillion per year by 2025.
- 37% of organizations worldwide were hit with a ransomware attack in the last year.
- The hacker group responsible for the infamous oil company attack received ransom payments from 47 additional victims in nine months.
- CNA Financial, one of the largest insurance companies in the US, paid a $40 million ransom in a 2021 attack.
- The chemical distribution company, Brenntag, paid a $4.4 million ransom in May 2021.
- In July 2021, an IT solutions organization had its systems infiltrated by hackers demanding $70 million in bitcoin.
- One of the largest meat suppliers in the United States, JBS, had to close five plants in May 2021 due to a ransomware attack.
- CWT paid a ransom to retrieve sensitive files and get back 30,000+ company computers that went down in July 2020.
- More than 200,000+ computers worldwide were affected by the infamous 2017 WannaCry ransomware attack.
These are just a handful of the millions of ransomware attacks reported worldwide every year.
How to Prevent Ransomware Attacks
Ransomware can clearly cause lots of problems, especially for businesses. In an effort to right ransomware, here are some of the security best practices your organization needs to follow:
- Educate Your Staff — Make sure your employees are adequately trained in security protocols. They need to understand the importance of cybersecurity and its potential impact on your business. You can even start by sending a company-wide email with this resource as a reference.
- Leverage Endpoint Protection — All company devices should be secured with endpoint protection software. Make sure those solutions are updated on a regular basis to fight off new malware and ransomware threats.
- Implement Stronger Password Policies — Employ stricter password policies organization-wide. Make sure passwords are changed on a regular basis and don’t allow your staff to use the same passwords for multiple accounts. You can also beef-up security standards by implementing SSO and two-factor authentication for logins.
- Avoid Suspicious Emails and Links — The vast majority of malware, including ransomware, starts with a phishing email. Make sure that you and your employees are aware of this. Downloading an untrustworthy file can lead to a serious data breach, even if it was an accident.
- Keep Offsite Backups — As we’ve seen from the statistics in this guide, not all data from a ransomware attack is recovered—even when the ransom is paid. An offsite backup can ensure that you get all of your data back.
If you follow these ransomware best practices, it reduces your company’s risk of being attacked.
What to Do If You’re Infected With Ransomware
If you or one of your employees sees a ransomware message, you need to isolate the infected device immediately. The system should be removed from the network ASAP to prevent the attack from infiltrating other network devices or shared drives.
Other devices on the network that haven’t been infiltrated should be powered off immediately.
Before you start backing up additional data or changing passwords, you need to make sure that the devices you’re using haven’t been corrupted. That’s why it’s so important to apply the ransomware prevention practices that we discussed above.
The US Justice Department recommends contacting law enforcement immediately. More specifically, you should contact your local FBI field office or the US Secret Service.
The United States Government discourages ransom payments. It’s also worth noting that paying a ransom doesn’t guarantee that you’ll get your data back. If you decide to pay a ransom, the hackers could always demand more money or target your organization again.
With that said, this is obviously a serious decision. As you’ve seen from the ransomware statistics in this guide, some organizations have decided to negotiate with hackers and pay the ransom demands.
But that doesn’t necessarily mean that this will be the best course of action for your organization. That’s a decision you’ll need to make on your own with company leaders, decision-makers, and stakeholders.

