Phishing Attack Types: The Complete Guide
Phishing attacks are a widespread method of network infiltration, and today there are many different types. These attacks have become more sophisticated and harder to counter over time. Fret not, our guide will detail everything you need to know to keep your company safe.
What Is a Phishing Attack Anyway?
A phishing attack is a form of cyber attack where scammers typically—although not always—send out many fraudulent emails. The emails try to intentionally mislead recipients to either click on a malicious link or download infected attachments by attempting to look legitimate. Their purpose is to steal the recipient’s personal information, such as login credentials and credit card details.
Phishing attacks can also install malware on a victim’s computer with the same overall goal. These types of attacks are potentially more problematic if the malware has enough time to do severe damage. There are several different methods behind phishing attacks, so it’s essential to be mindful of the key ones.
How a Phishing Attack Works
We know what phishing attacks are, but how exactly do they work? While the methods used in the attacks differ, generally, the most common types of phishing attacks will proceed in an order similar to this:
- An email arrives in your inbox.
- The email looks and sounds legitimate. It often sets up a common scenario—for example, that your password will expire soon, and you need to take action or that there has been a suspicious login on one of your accounts.
- The instructions ask you to click a link to renew or change your password within 24 hours.
- You click the link and then get redirected to a false page that appears and looks like the actual renewal page. You enter your old password and “create” a new one.
- The attacker monitors and then hijacks your original password to gain access to multiple secure areas normally protected by that password. They may also set up a malicious script to run in the background of your computer or network to feed them more secure info.
Below is an example of what these emails commonly look like:
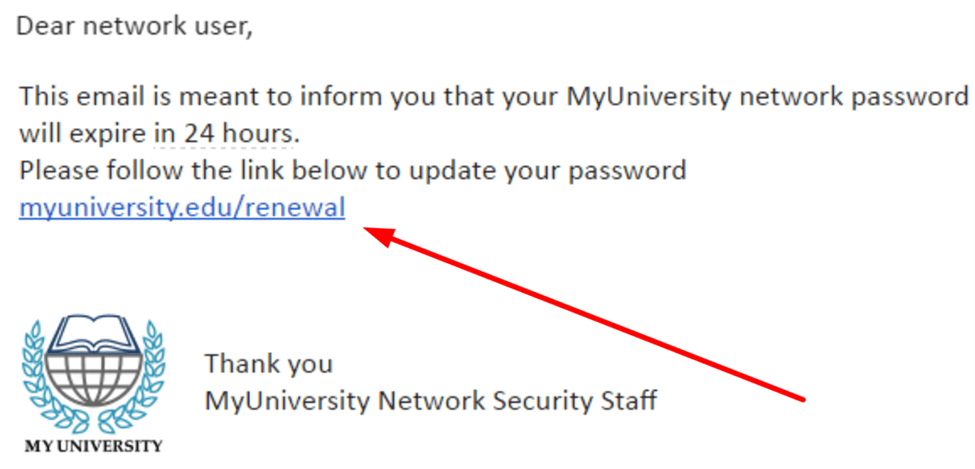
The user only needs to click the link once to begin the process, which is why these types of attacks are so difficult to deal with in the first place. These attacks can happen to anyone and even people who may be somewhat aware of them and how they work.
Let’s look at some more examples.
Example #1: The Attacker Employs Spear Phishing
An emerging type of phishing attack is known as “spear phishing.” Spear phishing targets a specific person or enterprise, in contrast to random users, as seen in the email example above. These attacks are more in-depth and require special knowledge about a company and its operation.
The attack starts with the perpetrator researching the names of employees, say within the marketing department. From there, they gain access to confidential invoices and then pose as the marketing director, sending an email with a link inside to someone like the project manager. The link in the email will redirect to a password-protected document, but in reality, it’s a false version of the stolen invoice.
Once the project manager has logged in, the attacker can steal their information and achieve complete access to a company’s network.
Example #2: The Attacker Employs Whaling or CEO Fraud
Another type of attack, certainly one on the rise, is what’s known as “whale phishing” or, alternatively, “CEO fraud.” In this type of attack, the attacker uses social media or the company website to look up and find the name of the CEO or someone else in a senior leadership position—possibly the finance manager.
They then imitate the person in question using a similar email address. Then they send an email where they may ask for something as direct as a money transfer or for the email recipient to review a specific document. These attacks are repeatedly successful as staff members are usually hesitant to refuse a request from someone high up in the business.
This type of attack is different from spear phishing because the fraudulent communications appear to have come from someone senior. They can do even more damage and are often severe if not countered.
How To Get Started and Counter Phishing Attacks
We know what phishing attacks are and have seen some examples of them in action, but that’s just the beginning. We’ve assembled some additional steps you can take below to minimize your chances of being a victim of one of these unwanted attacks.
Step 1: Stay Informed About the Latest Phishing Attacks
In the hyper-connected online world, phishing attacks are more common than ever—staying informed of the latest attack methods is critical. The quicker you find out about new attacks and share them with your employees, the sooner you can avoid them. Keeping your staff trained and aware is a big part of this, which we’ll look at a bit later in the guide.
So how do you stay informed? For one, be sure to sign up for email newsletters and prioritize reading blog posts every month. Useful publications you can read include Infosecurity Magazine, which covers the latest attacks and lists new and emerging strategies, and IT Security Guru, which features a dedicated newsletter focusing on cybercrime, ransomware, and other daily insights.

It’s worth staying up to date with free anti-phishing add-ons, too. Most browsers enable you to download add-ons that can detect the signs of a malicious site and let you know before the worst of the attack happens. These are typically free and get installed across a variety of different devices. A simple search under the “add-ons” section will do the trick in most browsers.
Of course, be sure you don’t readily give out your information to an unsecured site either. If the URL of a site doesn’t start with “HTTPS” or there’s no padlock icon, you should avoid entering sensitive information or downloading files whenever possible. A site without a proper security certificate might not always be a phishing scam, but it’s never worth taking unnecessary chances.
Step 2: Don’t Ignore Security Updates & Set Up Firewalls
While the sheer number of updates we receive today can be somewhat overwhelming, it’s important to stay updated as much as possible and not put them off. Security patches are released regularly for good reason; their frequency is often in response to the latest attacks. These updates patch holes in your company’s security, and if you don’t update, you can be at a much greater risk of phishing attacks through obvious and known vulnerabilities.
That said, there’s more you can do. For instance, firewalls are a highly effective way to prevent the most harmful attacks. Firewalls act as a shield between your system and the attacker and can limit the chances of the perpetrator successfully gaining entry into your company network. Although not commonly known, it’s best to use both desktop and network firewalls in tandem—when these get used together, they significantly enhance your overall security.
Most firewalls can be set up relatively quickly in a few straightforward steps, and the payoff is (almost) always worth it. You can configure firewalls to block data from specific locations such as apps or ports while allowing the required information through—most come preconfigured and ready to use. Be sure to identify your network’s assets and plan a structure for how your assets get grouped too. Just keep in mind that firewalls alone are typically not enough, so don’t become too reliant on them.
Step 3: Ensure Employee Training Gets Delivered Properly
Keeping a team aware of the latest threats and teaching them what to sidestep is crucial. The problem? Most training gets delivered at a yearly event or employee orientation, where much of it gets forgotten a week after the return trip. For online security training, most employees tend to click through the content as fast as possible with little in the way of retention. In-person training typically revolves around PowerPoint slides narrated by a speaker who would rather be elsewhere. This type of training rarely works.
Companies, especially enterprises, need a robust Security Education, Training, and Awareness (SETA) program to ensure proper security. These programs enable businesses to educate their employees about network security issues and help to set realistic expectations. The best programs—the ones that have seen the most success—are streamlined and highly focused in their production.
The security topics in these programs get prioritized, and the audience is determined well in advance—topics are presented in simple and exciting ways for them to digest. The training is all about raising awareness and seeks to make the information as memorable as possible. Education planning workshops often serve at the core of these programs to help keep employees engaged.
Step 4: Know Your Phishing Attack Prevention Best Practices
By now, you’ll have a firm idea of what phishing attacks are and should have some ideas on how to minimize your chances of being a victim. That said, the world of phishing attacks is vast, and there’s always more to learn.
As a result, we’ve put together some best practices for you and your company to ensure you remain as protected as you can. They are:
- Be aware that attackers can change the name that appears on an email, and they may be using a previously compromised account to take their attack further. The good news is that the URL of the email address, or the link, can only be falsified so far. Look out for strange punctuation or unusual letters, like seeing a small “l” when it should be a capital “I.”
- It’s important to hover over the sending address or the link given and check to make sure it looks legitimate. If an address looks strange, nine times out of ten, it’s because it’s redirecting the user to a dishonest landing page. The password gets quickly harvested on this page, and the rest of the attack can take place. If in doubt, don’t click the link. Instead, contact a team member, especially if the email is supposedly from them, and verify it first.
- Passwords typically act as the sole protection for accounts and systems, and as such, hackers focus on acquiring them above all else. We’ve all used the same password before across the web, but frequently doing it is a severe error. Doing so could mean that one data breach leads to all of your other accounts becoming compromised. Instead, practice password discipline and replace your passwords regularly. Try to avoid using the same password for different accounts—the short-term convenience doesn’t pay off.
- Emails that ask for login credentials or payment information should be treated with caution every time. Good phishing prevention requires a constant state of vigilance from you and your entire team. While firewalls and antivirus software can help, there’s nothing quite as important as educating your team and keeping them aware. Make it a practice at team meetings and other events to update everyone on the status of the latest attacks and the strategies to counter them wherever possible.
- Testing your employees with a mock phishing campaign is an excellent way of seeing how your company is doing. While these can be uncomfortable—nobody wants to be told they fell for something that could compromise the entire company—when implemented correctly, they can be an extremely effective defense against phishing attacks. Ensure that the tests are positive and feature constructive feedback so that employees stay motivated. Offering rewards for identifying scams often works well.
- Multifactor authentication is a small but powerful move you can make. Commonly known as MFA, this form of security prevents the information from being hijacked through a one-time secondary password that gets delivered via different formats, including SMS messages, physical tokens, or even biometric IDs. Contrast this to a simple user name and password, and the difference is noteworthy. Multiple authentications add additional security layers that are hard for phishers to get around.

