NIST SP 800-53 Revision 4 Vs. 5: Side-by-Side Comparison
NIST Special Publication 800-53 establishes information security standards and privacy control policies for federal agencies. Its goal is to secure assets, operations, users, and organizations in the US from a wide range of cyber threats—including malicious attacks, user error, and natural disasters.
Overall, NIST SP 800-53 offers a holistic framework for information security. Government agencies, government contractors, and any organization can use these controls to harden security protocols, protect data, and improve risk management.
The publication has gone through several changes since its initial release back in 2005. Some of those changes were minor, while others were more significant.
The differences between NIST SP 800-53 revision 4 compared to revision 5 definitely fall into the significant category. This guide will break down the differences between each version, so you can apply the correct controls and guidelines to your organization.
Our Recommendation = Use NIST SP 800-53 Revision 5
NIST SP 800-53 revision 5 has replaced its predecessor, revision 4.
To remain compliant with NIST SP 800-53, you must use the newest revision as a reference. While there are lots of similarities between revision 4 and revision 5, the differences are significant enough that any organization using revision 4 would be considered non-compliant.
Even if you’re not a federal agency or government contractor, and you’re just using the NIST SP 800-53 for information system security best practices, you should still be using revision 5.
The fourth revision was released in 2012. So if you’re following those guidelines, you’re using controls that are more than a decade old.
There have obviously been lots of changes to the world of cybersecurity in that time. So your organization will be vulnerable to newer threats if you’re not using the most updated standards and framework.
When to Use Revision 4 Instead
To remain compliant with NIST SP 800-53, organizations have to make adjustments within one year of a new revision release.
NIST SP 800-53 revision 5 was officially released on September 23, 2020. Since we’re no longer within that one-year grace period, any organization currently following the fourth reversion would be non-compliant.
Technically, using an outdated revision isn’t a requirement if you’re not a government agency or contractor. But it’s still not advisable to use the fourth revision since it’s so outdated.
There is no scenario where it makes sense for an organization to use the fourth revision of NIST SP 800-53 over the fifth revision. Revision 4 is obsolete.
We’ll take a closer look at the differences between rev 4 and rev 5 below.
Outcome-Based vs. Impact-Based
One of the key differences between the fourth and fifth revisions is the wording of the controls. Revision 5 is more focused on outcomes, whereas the fourth revision focused on impact.
This adjustment was made by focusing on the structure of the controls.
The control statements have been updated to put more emphasis on the desired goals of specific actions instead of focusing on an entity responsible for implementation. This restructuring acknowledges the fact that organizations need effective collaboration amongst teams to properly implement the controls.
Another reason why the NIST moved away from such a heavy focus on impact-based roles is that some of the roles in revision 4 were non-applicable on a broader scale.
For example, some of the wording in revision 4 referred to common roles within government agencies. But government contractors, private companies fulfilling government contracts, or non-government organizations seeking compliance don’t have those roles.
The switch of focus to outcomes makes the controls clearer for a wider range of organizations that want to apply these standards to information systems.
Here’s an example of the language in RA-1 that compares the phrasing adjustment to focus on outcomes in revision 5:
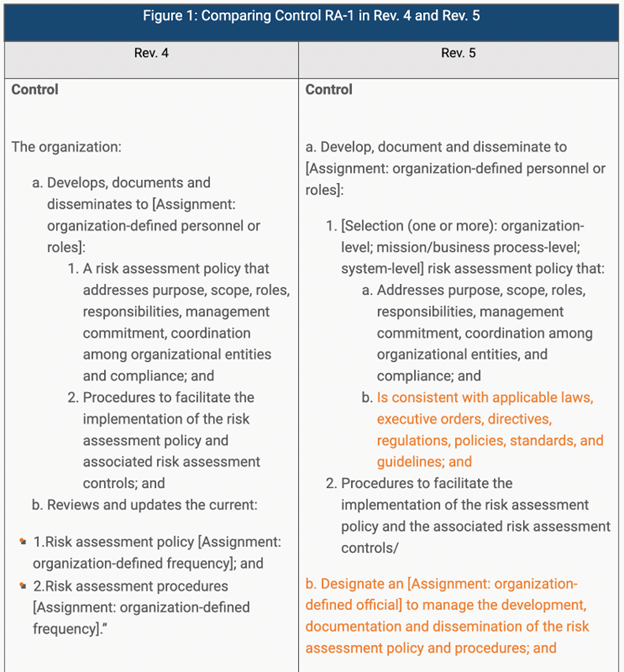
By removing the entity that performs the risk assessments, it removes implications that assessments must be performed by the organization. The newest revision makes it clear that a contracted third party could perform the assessment under this control.
It’s all about the outcome—not about who gets you there.
Controls and Control Families
NIST 800-53 revision 4 had a heavy focus on insider threats, privacy, cross-domain solutions, social networking, cloud computing, mobile devices, software application security, web apps, and persistent threats.
This version broke the controls down into 18 control families.
Revision 5 expanded upon these. The latest revision now includes 20 control families, which are:
- Access Control (AC)
- Awareness and Training (AT)
- Audit and Accountability (AU)
- Assessment, Authorization, and Monitoring (CA)
- Configuration Management (CM)
- Contingency Planning (CP)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Physical and Environmental Protection (PE)
- Planning (PL)
- Program Management (PM)
- Personnel Security (PS)
- Personally Identifiable Information Processing and Transparency (PT)
- Risk Assessment (RA)
- System and Services Acquisition (SA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
- Supply Chain Risk Management (SR)
The two new additions were Personally Identifiable Information Processing and Transparency and Supply Chain Risk Management.
66 additional controls were added to the fifth revision compared to the fourth revision. There were also 149 control enhancements between revisions 4 and 5.
Some noteworthy changes were made to the Access Control family. More specifically—AC-4: Information Flow Enforcement got ten new enhancements.
Big changes were also made to SA-8: Security and Privacy Engineering Principles, which received 33 new enhancements. Here’s a look at some of those new enhancements to SA-8:
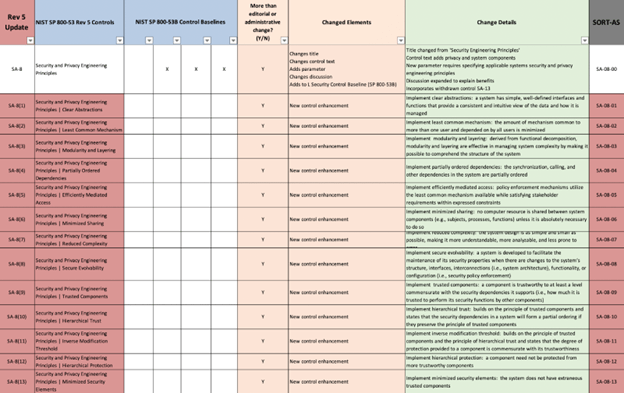
This was taken from the official analysis of updates between 800-53 rev 5 and rev 4, which can be downloaded directly from the NIST website.
It’s also worth noting that the Program Management control family doubled with new additions. All of the other enhancements and controls were spread fairly evenly across other families and existing controls.
Greater Emphasis on Privacy
Compared to revision 4, the fifth revision places more emphasis on privacy. It’s designed to bring privacy to the forefront of both implementation and system designs.
Previously, there was a separate appendix in revision 4 for all privacy controls. But these controls were not included in the security controls. In the newest version, privacy control families and security controls were used jointly in the main body of controls.
Some of the new controls are part of one of the two newest control families—Personally Identifiable Information Processing and Transparency. A new privacy baseline has also been established to enhance the controls within this family.
The privacy baseline is noted throughout the changed elements column of the release, especially within the PT control family.
In a snapshot of just 15 of the nearly 1,200 rows on this sheet, you can see that the new privacy control baseline was referenced seven times.
The new privacy baseline omits some base controls, but it directly incorporates the control enhancements. The standard low, moderate, and high baselines are a little bit more restricted here. Unlike other enhancements, the privacy baseline does not guarantee that those controls are part of the baseline.
Such an emphasis on privacy in the fifth revision is not surprising.
When you look back at the new privacy standards that have been put in place worldwide since revision 4 was released in 2012, there have been some significant strides. For example, GDPR in the EU wasn’t adopted until 2016 and the CCPA in California wasn’t passed until 2018.
These are just two of the many examples that showcase our world’s emphasis on privacy. So the NIST adjusted SP 800-53 to accommodate privacy concerns accordingly.
Supply Chain Risk Management
There have been growing threats in the world related to the supply chain for critical infrastructure and government organizations. As a result, the NIST added a new control family to address this concern.
The previous version did incorporate supply chains. But it did not group those controls into its own family.
The fifth revision also includes supply chain risk management aspects throughout other control families beyond SR. This is designed to help organizations protect services, products, and system components that are part of their critical infrastructure.
One common theme here is vendor risk management. Lots of organizations are turning to third parties for critical services.
The newest revision helps provide some guidance to help organizations assess the risks associated with using vendors for critical business functions.
Separate Control Baselines
With the newest version of this publication, the NIST also released 800-53B. This separate documentation helps organizations establish baseline controls.
Compared to the standard 800-53 publication that defines the controls, 800-53B gives organizations a starting point to protect information systems.
The three security baselines and one privacy baseline provided in this publication are specific to federal agencies that need to follow the requirements of the Federal Information Security Modernization (FISMA).
These are the same baseline categories in the Federal Information Processing Standards Publication 199 (FIPS 199), also published by the NIST.
Control baselines are segmented into three types of impact baselines:
- Low Impact — Limited adverse effect on operations, assets, or individuals if confidentiality, integrity, or availability is compromised.
- Moderate Impact — Serious adverse effect on operations, assets, or individuals if confidentiality, integrity, or availability is compromised.
- High Impact — Severe or catastrophic adverse effect on operations, assets, or individuals if confidentiality, integrity, or availability is compromised.
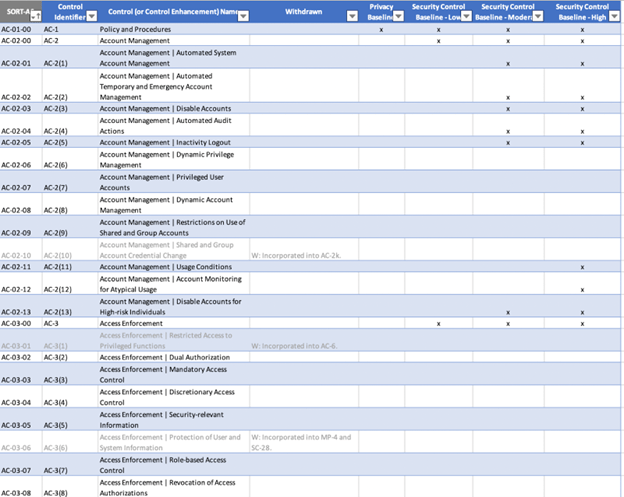
SP 800-53B uses a chart to assign controls and control enhancements to the appropriate control baseline. But since many control enhancements are unassigned, organizations need to do some research on their own to determine whether or not a control is required to mitigate risks based on their unique requirements.
Here’s a look at the latest version of SP 800-53B, which was originally published in September 2020 and includes updates from December 10, 2020.
Team Collaboration
Revision 5 puts more emphasis on teamwork and collaboration. It provides guidelines and recommendations to assign specific responsibilities to team members. A good understanding of the organization’s operations and policies is crucial here.
You’ll also find the terms “role” and “personnel” frequently used throughout the change details of revision 5.
Here’s an example from AT-3, which refers to role-based security:

To effectively apply all of the new changes related to team collaboration, there are a few big-picture initiatives your organization must handle.
You need to clearly assign roles and responsibilities to team members related to SP 800-53 implementation and compliance. The person responsible for rolling out new initiatives may not necessarily be the one who handles audits. Another person might be responsible for documentation.
Assigning roles to people with a good understanding of a particular topic is always in your best interest.
For example, having someone from HR assist with personnel security could be useful since HR should have a firm grasp on everyone’s roles and job requirements.
Properly training all of your team members to recognize and identify threats is also an important part of this revision. This ensures that anyone within the organization can make an impact on the path to information security safety.
Miscellaneous Changes
In addition to the major changes between SP 800-53 revision 4 and revision 5 highlighted below, there are several other miscellaneous changes that are worth mentioning.
Examples include:
- The term “information system” was widely replaced with “system” so that controls can be used for other systems (industrial control systems, IoT devices, general-purpose systems, etc.).
- The relationship between privacy and security has been clarified.
- Revision 4 had a priority concept for controls that organizations could use for baselines and control development. But these priorities were removed in the fifth revision—meaning it’s up to the organizations to come up with their own control priorities.
- The word “federal” was removed from the title in revision 5 to clarify that the SP 800-53 guidelines can be used by any organization.
- Revision 5 promotes risk management methodologies and cybersecurity principles, including the NIST Cybersecurity Framework.
- Newer controls for accountability, cybersecurity, threat intelligence, and privacy controls are referenced.
Overall, the changes between NIST SP 800-53 rev 4 and rev 5 were significant. The publication has been modernized to incorporate new threats and risks, as well as the ability to apply these guidelines to a wider range of use cases.

