The Ultimate Guide to NIST Cybersecurity Framework (CSF)
Today’s organizations must fulfill business requirements in the face of a complex and ever-changing cyber threat landscape. The NIST Cybersecurity Framework (CSF) provides a common language for understanding cybersecurity risks across all industries. We’ll explore everything you need to know about the NIST Cybersecurity Framework and how you can apply it to improve your organization’s cybersecurity posture.
What is The NIST Cybersecurity Framework Anyway?
The National Institute of Standards and Technology (NIST) is an agency operating under the United States Commerce Department. It is primarily responsible for developing research, science, standards, and technology to enhance American innovation and industrial competitiveness.
NIST developed a set of guidelines to enable private sector companies to identify, detect, and respond to cyberattacks. This framework and subsequent guidelines are referred to collectively as the NIST Cybersecurity Framework (NIST CSF). The framework was developed in response to the lack of uniform cybersecurity guidelines in the private sector.
Although not mandatory for the private sector, the NIST Cybersecurity Frameworks provides organizations of all sizes with recommendations, standards, and best practices for improving their security posture. In short, if your organization doesn’t have a cybersecurity program, the NIST Framework provides all the information, guidelines, and resources required to create one.
The NIST Cybersecurity Framework is a gold standard regardless of the organization’s size or the industry it operates. It offers the private sector access to established, proven, and repeatable data security processes to help organizations secure their networks. Finally, the framework is designed to be cost-effective and aligns with most other mandated regulations such as HIPAA, ITAR, and SOX.
How the NIST Cybersecurity Framework Works
It’s worth reiterating that the NIST CSF is entirely voluntary for private sector businesses. However, the framework is mandatory for government offices under the 2017 executive order signed by then-president Donald Trump. Still, it is a critical resource for private-sector businesses looking for a clear, proven, and cost-effective path toward improving their cybersecurity posture.
Again, the NIST Cybersecurity Framework covers most major industries. Therefore, the implementation might vary from one organization to the next. However, the fundamentals remain the same across the board, which helps understand NIST CSF.
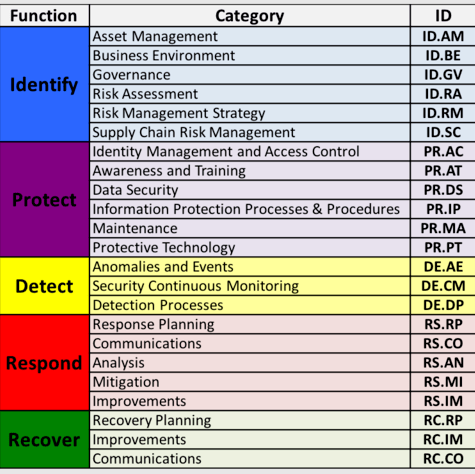
Once you grasp its five core functions, the NIST CSF is easy to understand. These core functions are at the heart of the framework’s cybersecurity processes, capabilities, projects, and daily activities. The fundamentals of the NIST CSF include:
Identify
As the name suggests, the Identify function aims to discover the specific risks that the organization faces. So naturally, it’s essential to understand what needs protecting and why before implementing the necessary protections. For example, the Identify phase may uncover crucial financial information, personal files, critical assets, sensitive client information, or intellectual property that needs protecting.
The Identify function covers all the bases, including data, assets, and systems. Therefore, it’s necessary to perform an inventory of all assets, establish how the assets are connected, and define employee roles and responsibilities for protecting these assets.
The NIST CSF further breaks down the Identify function into five key categories, including:
Asset management – Identifies the organization’s critical resources such as data, devices, employees, facilities, and systems.
Business environment – Identifies the organization’s context, such as business goals and objectives, key stakeholders, mission, and operations.
Governance – Refers to the organization’s official processes, policies, and procedures for assessing and managing risk.
Risk assessment – Involves evaluating the potential risks to the organization’s personnel, assets, and operations.
Risk management strategy – A detailed roadmap for how the organization intends to mitigate the identified risks, including risk prioritization, tolerances, and constraints.
In short, successfully implementing the Identify phase helps understand the organization’s current security posture. This phase is also helpful for creating a plan to reach the desired security state.
Protect
While the Identify function is more concerned with monitoring and assessment, the Protect function is more action-oriented. It aims to limit or contain potential cyber threats.
Some of the actions that a business might take to protect its environment include:
- Awareness training
- Identity management and access control
- Information security processes and procedures
- Data security
- Protective technology
- Maintenance
It’s worth noting that the Protect function isn’t only about preventing cyber threats. Sometimes, cybersecurity events are inevitable. So the safeguards should also include measures to contain the impact of these events if and when they happen.
Detect
The Detect function is mainly concerned with uncovering cybersecurity events as soon as they happen. There’s an emphasis on timeliness in identifying security breaches. Additionally, the Detect function is concerned with all cybersecurity events besides potential breaches.
Cybersecurity events in this context refer to abnormal behavior in a given system or environment. For example, this behavior may include detecting new devices or failed login attempts from authorized users. So the Detect function takes a broad view of network security to identify any changes to the typical business environment.
The main categories in this function include:
- Security continuous monitoring
- Anomalies and events
- Detection processes
Respond
As the name suggests, this function is concerned with the ability to contain the impact of a cyber-incident. Therefore, a comprehensive cybersecurity incident response plan is the best place to start. This document includes detailed instructions on what an IT team should do in the event of a breach, leak, or attack.
Some of the categories under this function include:
- Response planning
- Analysis
- Communications
- Mitigation
- Improvements
It is equally important to have defined roles and responsibilities in the context of a cyber event. It’s difficult for employees to follow an incident response plan if they don’t know their role in securing the business environment.
Finally, it’s essential to report all security incidents. These reports are crucial for identifying what went wrong and what can be improved in the future.
Recover
Recover is the last core function of the NIST CSF. The function’s primary concern is timely recovery and restoration of normal operations after a cybersecurity event. The categories that fall under this function include:
- Recovery planning
- Improvements
- Communications
Comprehensive business continuity and disaster recovery plan are critical for successfully implementing the Recover function. The plan should include complete instructions for backing up data. It should also prioritize the action steps for the proposed recovery plan.
Below are a few great examples of how the NIST Cybersecurity Framework works:
Example 1: Using NIST Implementation Tiers
The NIST Cybersecurity Framework provides clearly defined functions to help you improve your security posture. Similarly, the framework offers implementation tiers to guide businesses through the implementation.
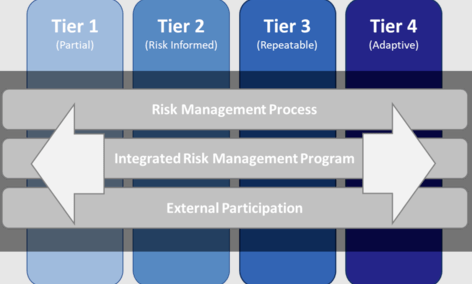
Tier 1 is referred to as Partial. Businesses in this tier typically haven’t invested much in clear security policies and prevention measures. Organizations in this tier also don’t have much money, time, and resources to invest in their security posture. As a result, businesses in this category have the most to gain by understanding and addressing cybersecurity risks.
NIST refers to Tier 2 as Risk Informed. Businesses in this category fare slightly better than Tier 1. Here, an organization may understand some of the cyber risks it faces and is actively working to address some of these risks. However, Tier 2 businesses may not address their security needs quickly enough.
Tier 3 is called Repeatable. Businesses in this category typically have comprehensive risk management and cybersecurity policies. The executive also approves these policies. It’s a desirable level of cyber maturity since organizations in Tier 3 are typically more prepared to counter security threats while also actively addressing vulnerabilities in their environment.
The highest NIST CSF tier is Tier 4, known as Adaptive. Businesses in this tier focus more on potential threats and eliminate vulnerabilities before they are exploited.
The NIST Cybersecurity framework also recommends specific action items for each tier. For instance, businesses in Tier 1 and 2 can benefit from developing information security policies, implementing password policies, and mandatory security awareness training at least once a year.
The NIST tiers are an effective way to benchmark your organization’s cybersecurity posture. Then, you can follow the recommendations for your specific tier. Finally, the goal is to climb the tiers to grow your cybersecurity maturity continually.
Example 2: Using the NIST Cybersecurity Framework Profiles
The NIST Cybersecurity Framework outlines its core principles known as Functions. It also offers a methodology for assessing your current and desired cybersecurity maturity level known as the Implementation Tiers. Lastly, the framework also provides Profiles to help you align your cybersecurity efforts to your specific industry.
The NIST CSF Profiles essentially customize the framework based on an organization’s specific objectives, resources, business requirements, and risk tolerance. For example, a private business in the manufacturing industry has a different set of cybersecurity requirements than the US Coast Guard.
Therefore, the framework’s profiles allow businesses to align with the security requirements of their specific organization and industry closely. The framework also suggests using Current and Targeted profiles.
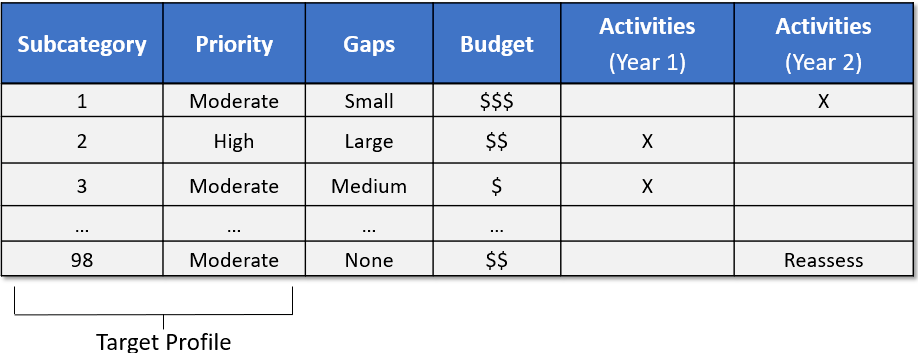
The Current Profile indicates your organization’s current outcomes, while the Target Profile indicates the desired results based on your organization’s risk management goals. It’s a quick way to identify flaws in your current cybersecurity posture and find improvement opportunities.
You can then use your profile to create a detailed roadmap for improving your cybersecurity posture.
Example 3: Complying With the NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) is a non-regulatory agency. The agency doesn’t enforce or certify for the NIST CSF. Instead, the agency relies on self-assessment, which means businesses officially declare their compliance without requiring an independent supporting audit.
NIST CSF compliance is also voluntary for private sector businesses, raising the question of certification. However, the advantages of certification are self-evident. They include boosting your reputation, guaranteed compliance, and avoiding legal issues.
For this, NIST partners with independent third-party cybersecurity and compliance firms such as Baldrige and 360 Advanced to develop self-assessment and certification standards. For example, in collaboration with Baldrige, NIST developed the Baldrige Cybersecurity Excellence Builder (BCEB).
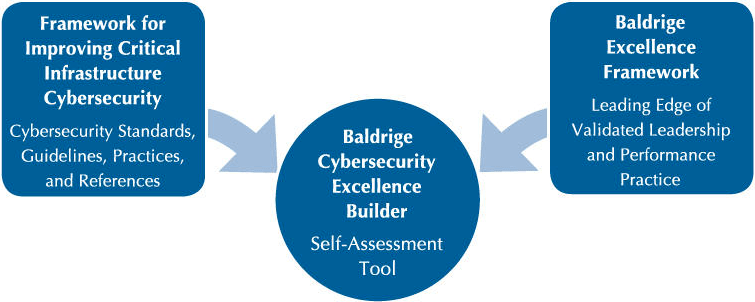
The BCEB is a self-assessment tool designed explicitly for NIST CSF compliance. Businesses can use it to measure the effectiveness and efficiency of their cybersecurity approaches as recommended by the NIST Cybersecurity Framework. Additionally, the tool allows companies to measure their results. It’s a valuable tool for determining NIST CSF compliance within an organization without the help of third-party auditors.
Self-assessment may not be sufficient for businesses that want compliance certification. For this, 360 Advanced partners with NIST to provide certification. This independent cybersecurity compliance firm offers a professional NIST CSF compliance assessment. This assessment includes an actionable report with feedback such as identified unmitigated cyber risks, maturity level based on the CSF Implementation Tiers, and recommended remediation.

This alternative to the self-assessment tool is a perfect solution for organizations that require professional guidance to guarantee compliance. Additionally, 360 Advance offers certification as proof of compliance with the NIST CSF. It’s a valuable badge, especially for businesses competing for government contracts.
How to Get Started With the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a vast collection of standards, guidelines, and best practices. It is no wonder many businesses feel overwhelmed with the momentous task of applying the framework. In reality, the framework is easier to implement than most people think.
Below are a few critical steps to help you improve your cybersecurity posture with the NIST Cybersecurity Framework.
Establish Your Cybersecurity Goals
The first step toward successfully implementing the NIST framework is establishing specific cybersecurity goals. This step is crucial for creating a roadmap toward improving your security posture. Of course, it’s impossible to do everything at once, so a set of clearly defined goals helps jumpstart your action plan.
The best place to start is with your risk tolerance. Involve stakeholders such as the IT department and upper management in deciding a tolerable level of risk. Then, it is easier to prioritize the business systems that require the most attention.
Other crucial goal-setting considerations include your business objectives, budget, and high-level priorities. The primary purpose of this step is to identify the critical systems and assets and prioritize their protection.
Finally, it’s a good idea to start small. For instance, you can pick one or two mission-critical departments to focus on. It’s a great way to get feedback about what works and what might be improved in the future. In most cases, starting with an organization-wide rollout may be too complex, cumbersome, expensive, and error-prone.
Tailor the Framework to Your Business Needs
You can think of the NIST CSF as a set of recommendations rather than cast in stone. So it’s essential to tailor the framework to your business environment. The Framework Implementation Tiers offer critical guidance in this step.
You can use the Implementation Tiers first to identify critical areas for improvement. Below is a quick recap of the tiers:
- Tier 1: Partial – This tier means your business has an underdeveloped cybersecurity stance. Companies in this category tend to deal with threats reactively and inconsistently.
- Tier 2: Risk Informed – Your business has some awareness of the cybersecurity risks it faces. There are also plans to respond to the threats.
- Tier 3: Repeatable – Businesses in this category have clearly defined organization-wide repeatable cybersecurity processes and procedures.
- Tier 4: Adaptive – Companies in Tier 4 have a mature cybersecurity stance and proactively prevent threats before they occur.
Understanding your positioning concerning the Implementation Tiers further narrows down your priorities. Each tier has recommended guidelines and action steps. The main goal is to move to the next level as quickly as your budget and priorities allow.
Conduct a Risk Assessment
Conducting a risk assessment during this stage is crucial for aligning the framework’s implementation to your unique security posture. Specifically, the risk assessment should cover the priority areas you identify in the previous steps. In addition, this assessment should provide a clear understanding of the likelihood of cybersecurity events and the potential impact of such events.
Additionally, the risk assessment will allow you to identify the current cybersecurity efforts that comply with NIST standards. You’ll also discover areas for improvement. Therefore, it’s critical to score your security efforts during the assessment.
Develop Your Target Scores
The risk assessment is a good indicator of how your cybersecurity efforts fare in relation to NIST CSF standards. You can use these scores as a baseline for setting your target scores. Your target scores help determine the gap between your current security posture and where you hope to go.
Finally, identify the specific actions you need to take to achieve the target scores. It’s important to involve stakeholders to prioritize and develop a comprehensive action plan. Then, you’re finally ready to implement your action plan.

