Google Vault: Managing Administrative Access
Google Vault has fundamentally transformed the way companies approach electronic discovery and information governance in Google Workspace. Organizations can use Vault for various legal, compliance, and security needs including legal holds, data retention, and security investigations.
It’s a powerful tool that gives insight into employees’ documents, emails, and more. But, with that power, comes responsibility.
Using Vault, administrators can search and access employees’ chats, documents, and emails, including variations of drafts in Gmail. Administrators can also give temporary Vault access to people outside of their company who may need to use it, such as external legal counsel or auditors.
Not just anyone in an organization should be able to access private employee data and communications. Considering the depth and breadth of information that Google Vault provides, managing access to Vault is essential. Companies need to ensure that only people who absolutely need access to Vault, have access.
In this post, we’ll go over how to control access to Vault and how to set Vault privileges, so that only verified and approved end users can access the tool’s powerful capabilities.
How to change who can sign in to Vault
Administrators can decide who is able to sign in to Vault, by altering the service status. They can also choose to turn this function on or off for specific organizational units. Here are the six key steps:
- In the Admin console, go to “Menu” > “Apps” > “Google Workspace” > “Google Vault.”
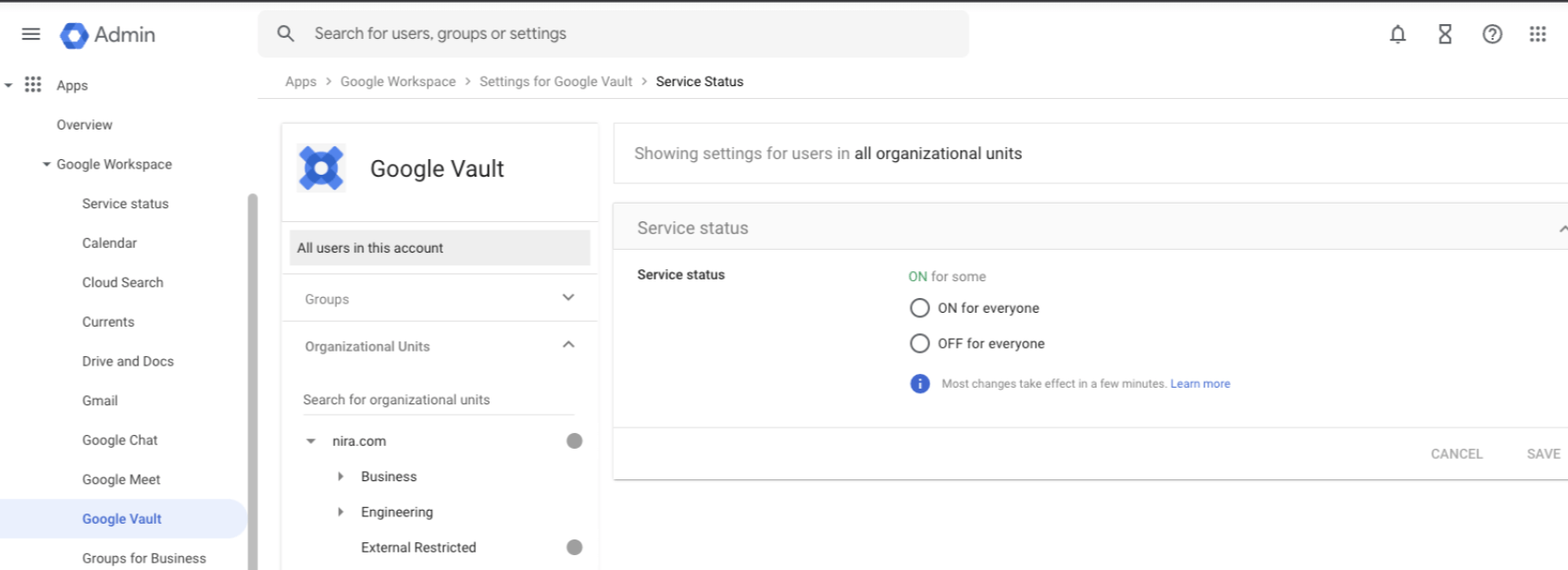
- Click “Service status.”
- Click “On for everyone” or “Off for everyone,” and then click “Save.”
4. There is also the option to turn a service on or off for an organizational unit.
-
- Select the organizational unit.
- Select “On” or “Off” to change the Service status.
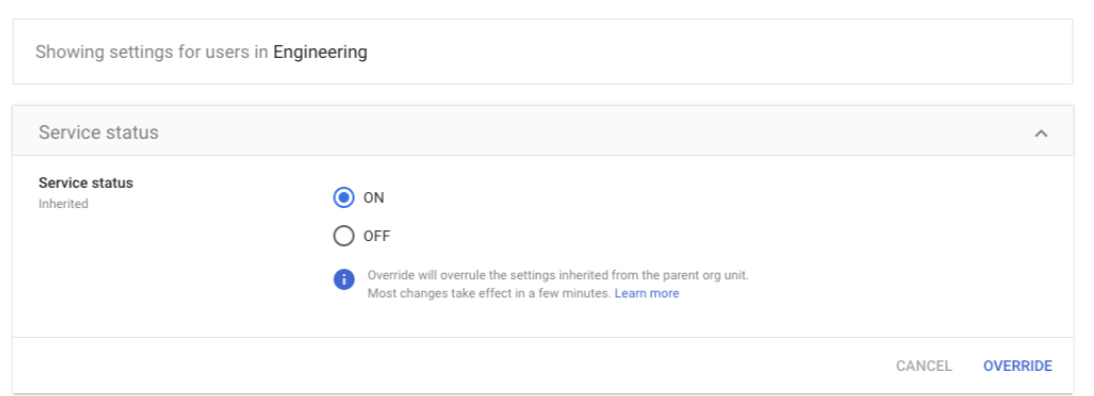
- You can now choose if the Service status should be “Inherited” or “Overridden.”
- If the Service status is set to “Inherited:” If you want to keep the updated setting, even if the parent setting changes, click “Override.”
5. If the Service status is set to “Overridden:” Either click “Inherit” to revert to the same setting as its parent, or click “Save” to keep the new setting, even if the parent setting changes.
6. Select an access group to turn on a service for a set of users across or within organizational units.
Please note: Changes can take up to 24 hours to happen.
How to give an external user access to Vault
To ensure compliance with investigations or audits, administrators have the capability to provide external users, like members of a regulatory agency or external legal counsel, with Vault access. They must first add these users to their organization in the Admin console and give them privileges to search in Vault, view reports, or other tasks. Once these steps are completed, administrators should notify the external users that they can access Vault using the provided accounts.
- Sign in to the Admin console.
- Create a new organizational unit for external users.
- Turn services on or off for this organizational unit as required.
- Add external users to this organizational unit.
- For example, if you want ashleigh@acmecorplegal.com, an external investigator, to access Vault, you can add her as ashleigh-acmecorplegal@your_domain.com.
- Create a new admin role with the required Vault privileges.
- Assign the admin role to external users as needed.
- These external users do not require a Vault license.
How to set Vault privileges
Google Workspace administrators have the flexibility to grant varying levels of access to users within their organization for Vault tasks. This can be done by allowing specific users to perform all Vault tasks or only a specific subset based on their role.
Before granting Vault privileges to users, it’s a good idea to consult with an organization’s legal team or business personnel to determine which users truly require access to Vault tools. Some Vault privileges, such as managing searches or exports, can be restricted to work exclusively with user data within an organizational unit.
It’s important to treat accounts with Vault privileges as sensitive because they possess access and control over other users’ data within the organization.
To assign privileges to a user, administrators can create an admin role encompassing one or more Vault privileges and then assign this role to the respective user. For more information about Privileges, check out the table in the Google Vault Help Center.
Step 1: Create an admin role with Vault privileges
Please note: Super administrator status is needed to perform these steps.
- In the Admin console, go to “Menu” > “Account” > “Admin roles.”
- Click “Create a new role.”
- Enter a name and description for the role.
- Click “Continue.”
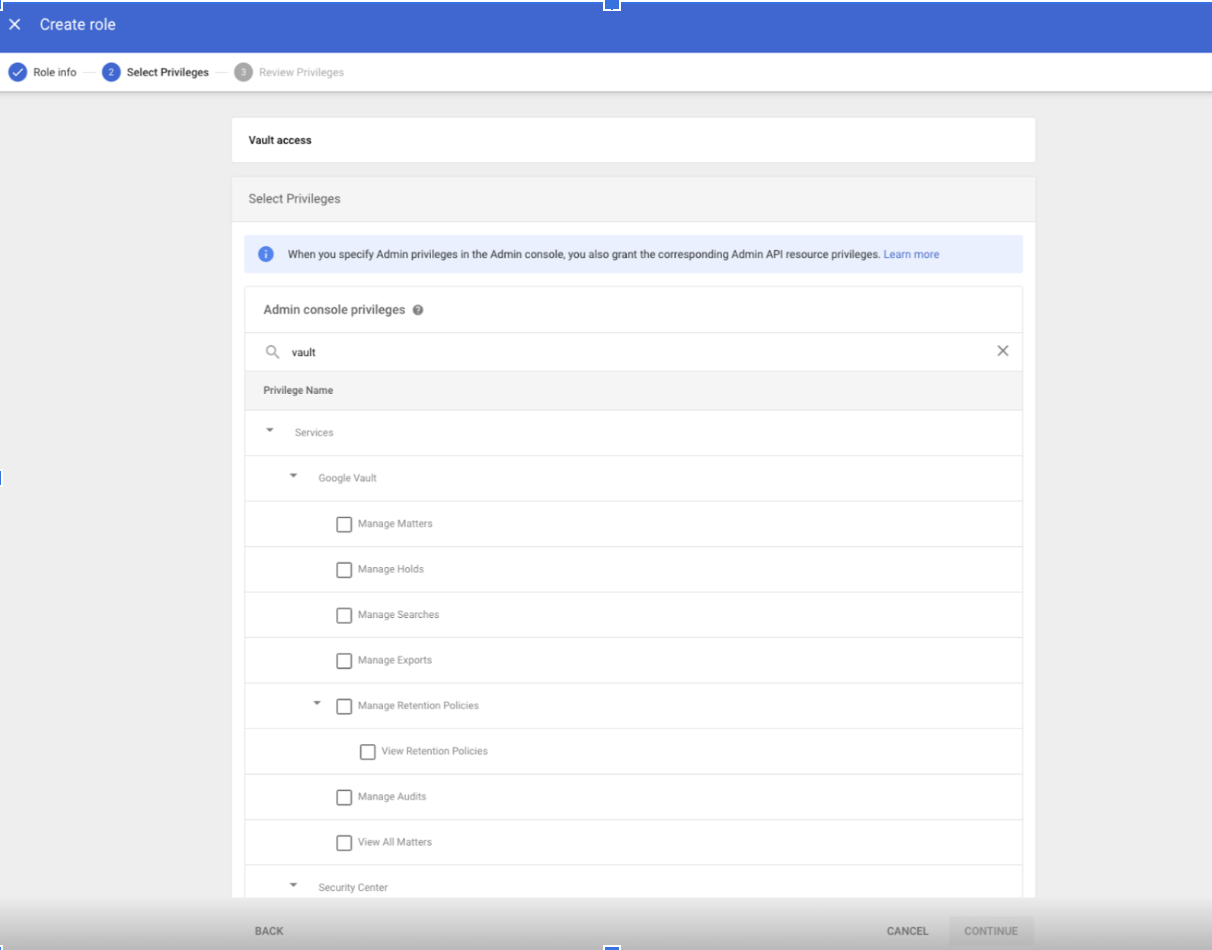
- Locate and expand the Google Vault section; in the search box, enter “Google Vault.”
- Select privileges for the role. For more details, go to the Vault privileges reference.
- Click “Continue.”
- Review the selected privileges, then click “Create Role.”
Step 2: Assign Vault privileges to users
Administrators can assign Vault roles to one user at a time, or to several users at once. They can also assign a role to numerous users using a group or assign a role to a service account.
Assign roles to one user
- In the Admin console, go to “Menu” > “Directory” > “Users.”
- Find the user in the list.
- Click the user’s name to open their account page.
- Scroll down and click “Admin roles and privileges.”
- Next to the prebuilt or custom role, click “Turn on.”
- If you don’t see “Turn on” click anywhere under “Roles” to reveal the switches.
- You have the option to restrict the admin’s role to a specific organizational unit:
- Next to “All organizational units,” click “Edit,” select the organizational units, and click “Done.”
- If you don’t see “Edit,” you cannot apply the role to organizational units.
- Click “Save.”
Assign roles to several users at one time
- In the Admin console, go to “Menu” > “Account” > “Admin roles.”
- Point to the role that you want to assign and click “Assign admin.”
- Click “Assign members.”
- Enter the first few letters of the user’s email address and select the user’s address from the options. You can assign a role to up to 20 users and groups at a time.
- Click “Assign Role.”
- You have the option to restrict the admin’s role to a specific organizational unit:
- Next to “All organizational units,” click “Edit,” select the organizational units, and click “Done.”
- If you don’t see “Edit,” you cannot apply the role to organizational units.
Assign a role to a group
- In the Admin console, go to “Menu” > “Account” > “Admin roles.”
- Point to the role that you want to assign and click “Assign admin.”
- Click “Assign members.”
- Enter the first few letters of the group’s email address or name and select the address from the options. You can assign a role to up to 20 groups and users at a time.
- You have the option to restrict the admin’s role to a specific organizational unit:
- Next to “All organizational units,” click “Edit,” select the organizational units, and click “Done.”
- If you don’t see “Edit,” you cannot apply the role to organizational units.
Assign a role to a service account
- In the Admin console, go to “Menu” > “Account” > “Admin roles.”
- Point to the role that you want to assign and click “Assign admin.”
- Click “Assign service accounts.”
- Enter the email address of the service account.
- To find the email address, open the Google Cloud console and click “Menu” > “IAM & Admin” > “Service Accounts.”
- Click “Add” > “Assign role.”
What Privileges can administrators assign?
Administrators can restrict some Vault privileges, such as managing exports, to an organizational unit. Other privileges apply to all organizational units.
- Manage Matters
- This allows a user to create matters and share those matters with other users.
- They can also close, reopen, and modify matters.
- They can delete and restore matters.
- If the privilege is restricted to an organizational unit, the user can share matters only with accounts in the organizational unit.
- Please note: Admins need at least one other privilege—Manage Holds, Manage Searches, Manage Exports, or Manage Audits— to open and work with matters.
- View All Matters
- View all matters in your entire organization.
- This privilege applies to all organizational units.
- Manage Holds
- View the list of user accounts on hold.
- Create, modify, and remove holds.
- Vault users outside the organizational unit can see holds on users in the organizational unit.
- Manage Searches
- Search data and count results.
- Create or delete saved search queries.
- View the contents of messages and files that are returned with search queries.
- When this privilege is restricted to an organizational unit, the user can search only for data associated with accounts and shared drives in that organizational unit.
- Manage Exports
- View and download exports.
- Delete all exports.
- To create exports, a user needs this privilege and the Manage Searches privilege.
- When this privilege is restricted to an organizational unit, the user can export only data associated with accounts and shared drives in the organizational unit.
- Super administrators don’t have access to all exports. They can only work with exports they own and exports in matters shared with them.
- Manage Audits
- View audit logs for matters that were created by or shared with the user.
- View all hold reports for your entire organization.
- View holds in matters that the user has access to.
- This applies to all organizational units.
- Manage Retention Policies
- Create and view retention rules for your entire organization.
- Update retention rules for your entire organization.
- Delete retention rules for your entire organization.
- This privilege applies to all organizational units.
- View Retention Policies
- View all retention rules for your entire organization.
- This privilege applies to all organizational units.
Google Vault is a powerful solution that can help companies with eDiscovery, data storage, information governance, and more. However, it is absolutely essential that only authorized users have access to the tool.
With strong capabilities for security investigations, legal holds, and data retention, Vault’s power should only be in the hands of administrators, legal advisers, or auditors who truly need access. What’s more, when access by external parties is no longer required, those privileges should immediately be removed, to ensure that company and employee privacy is upheld and protected.
Administrators can manage access to Vault through their Admin console and by assigning privileges to certain users or organizational units. Complement this with the ability to audit in Vault, and administrators have better control over who can view and use the tool.
For further information on access control, auditing, and more, check out our full guide to Google Vault.

