Google Cloud Security – Is it Secure Enough?
Google Cloud Platform, also known as GCP or simply Google Cloud, provides companies with the cloud computing resources necessary to develop and deploy, and applications on the web.
Instead of having to purchase and maintain infrastructure, companies can add as many servers and disks as they like, virtually on-demand, and everything’s running in a highly fault-tolerant environment.
Companies used to turn to infrastructure-as-a-service (IaaS) as a matter of convenience, but now it is becoming a matter of security. Google, Amazon, and Microsoft can leverage their size and power to provide scalable infrastructure that’s far more secure that a company could build out on their own.
So how secure is Google Cloud?
Top of the line.
The built-in Google Cloud security features are comprehensive, the interface is easy to use, and there are a host of add-on security products available to repel the most challenging attacks.
What is Google Cloud Security?
Google Cloud security encompasses the technology, processes, and strategy that keep your data and workloads safe and accessible at all times.
With Google Cloud, security starts with the people they hire, hardware they manufacture, and remains a primary consideration for every decision they make. They’re aligned on privacy with customers, and continue to exert their massive resources in service of keeping information secure.
Key components of Google Cloud Security

Google data centers
The data centers that house Google’s infrastructure enjoy tremendous physical defenses, with security guards, perimeter fencing, alarms, metal detectors, custom-designed electronic access cards, and biometrics.
The data center floor has laser beam intrusion detection, and additional layers of security to prevent unauthorized access. The company says that less than one percent of Googlers will ever set foot in one of their data centers.
To ensure uninterrupted availability, all data centers have redundant power systems and environmental controls with state of the art cooling systems.
Global network security
By virtue of being linked to most ISPs in the world, Google Cloud limits the number of “hops” necessary between a customer’s ISP and the company’s data center. With fewer hops between devices across the public internet, it reduces opportunities for data interception.
All traffic routed through Google Front End servers, which detect malware and DDoS attacks. This base layer of security is routinely examined and improved.
Custom server hardware and software
The servers and network equipment in Google data centers are designed and manufactured in-house and run on a custom-designed OS. They control every aspect of the building process and do not sell their servers.
The servers are maintained by a proprietary software that continually monitors systems for modifications. The software has automated self-healing mechanisms that slow down attacks and help Google detect, assess, and remediate threats to the network.
Device Lifecycle Management
The servers and networking devices that comprise Google Cloud are closely tracked across their entire lifecycle: from being produced by Google themselves to retirement/destruction.
Any component that fails to pass a performance test is removed immediately to maintain network integrity, and the physical destruction of disks happens according to a strict disposal policy.
Data secure in transit and at rest
By default, Google Cloud encrypts your data at rest and while it’s in transit in order to ensure the authenticity, integrity and privacy of data at all times.
For data at rest, Google uses AES to keep information safe from system compromise or data exfiltration. For data in transit, Google uses TLS for transport security, and S/MIME for email and message security.
For customers with additional Google Cloud security requirements, such as encryption of data over wide area networks, there are additional protections available, including IPSec tunnels, managed SSL certificates, and Istio.
What Makes Google Cloud Security Different
Perhaps the biggest leg up that Google Cloud has on the competition with regards to security is experience. They haven’t been around as long as AWS or Microsoft Azure, but they are the world’s most popular email and search engine, which gives them a tremendous attack surface to secure.
In the world’s harshest real-time threat environment, Google continues to perform magnificently.
It starts with the company culture, which places a tremendous emphasis on security. They use background checks, training, and special events to ensure that all employees understand how to contribute to the safety and privacy of their customers.
Google employs a full-time security team, privacy team, vulnerability management team, and fleet of security engineers that oversee the company’s cutting edge infrastructure. As technology evolves, these teams coordinate to make sure that customer data and workloads remain safe from emerging threats.
On the customer side, Cloud IAM is integrated, which makes controlling permissions easy and provides a unified view of security policy for the whole organization.
The built-in Google Cloud Security Command Center provides managed vulnerability assessment scanning. This helps companies detect the most severe issues, such as insecure IAM configurations, misconfigured firewalls, and publicly exposed assets.
With the Premium tier of Google Cloud, the Security Command Center comes with additional tools including:
- Event Threat Detection
- Container Threat Detection
- Security Health Analytics
- Web Security Scanner
The ease-of-use with regards to Google Cloud security has been noted in many reviews, especially in comparison to Azure. The intuitive interface makes configuring and monitoring your security much easier, and the Google Cloud Marketplace has products and ready-to-go software stacks to help you secure and monitor your data.

One of the marquee Google Cloud security products is Chronicle, which allows you to store and continuously analyze massive amounts of security telemetry. The idea is to provide companies with the same AI and machine learning capabilities Google uses to monitor cloud security.
From the Chronicle dashboard, users can upload telemetry data, where it is normalized, indexed and correlated against existing incidents. Within a few seconds, analysts get comprehensive, real-time insights.
The speed of Chronicle is unmatched, and provides a unique tool for information security professionals responding to zero-day threats.
Pricing is complex for Google Cloud and its competitors, but one area where the service steps away from the competition are the sustained use discounts. After certain use thresholds on certain resources, discounts are applied incrementally.
The discount may be as much as 30% depending on your usage, as you can see in the following graph from Google:
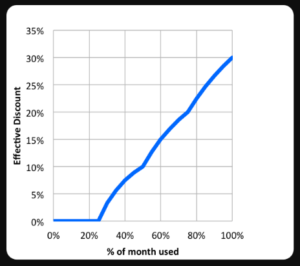
How Secure is Google Cloud Security?
Google, like every major cloud provider, has had their system compromised.
In 2018, hackers successfully used Google Cloud as part of an email phishing campaign to target banks and financial companies. By hosting malicious payloads on Google Cloud, hackers snuck under the radar of companies’ cybersecurity defenses. It’s essentially a reputation hijack, where bad actors use Google’s trusted platform to mask the attack.
Hackers have also been known to use Google Cloud to identify and exploit vulnerable routers, causing them to connect to malicious websites and addresses.
These risks are not unique to Google Cloud, as AWS and Azure have had their share of troubles with both phishing and DNS hijacking.
In many cases, businesses that suffer costly IT breeches can’t point the finger at their provider. Consider the DNS hijacking, where the routers were attacked via Google Cloud. All of the vulnerabilities were fixed years ago, but the patches hadn’t been installed.
With Google Cloud, security is a shared responsibility:
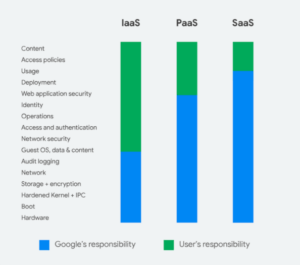
This framework for dividing responsibilities reflects the fact that Google values their customer’s privacy and control. You don’t have to think much about operating G Suite, a SaaS product, but you have virtually no control over the backend. With Google Cloud, there’s more control and more responsibility.
Although the company provides an excellent foundation and all of the tools necessary to grow, keeping Google Cloud well-defended comes down to the overall security posture at your company.
Taking steps to protect employees and their devices, like getting the best endpoint detection software, will alert your IT teams to outdated router firmware, and other million dollar mistakes.
How to Get Google Cloud Security
You can sign up for the free tier of Google Cloud, which comes with a surprising number of features.
It’s free forever, and you get 20+ tools and $300 to explore the platform.
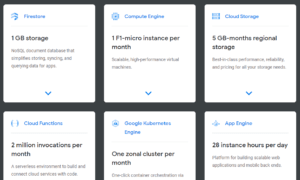
In terms of paid plans, Google Cloud is offered in two network service tiers: Standard and Premium. Standard delivers network performance that compares to other providers, whereas Premium is even faster, especially for companies with a global reach.
Pricing for Google Cloud is complex, but payment is not. You’ll receive a single bill for all your services, including those of third parties.
Additional Google Cloud security products are available in the GCP Marketplace.

