The Ultimate Manual for GitHub Enterprise Managed Users
Enterprise Managed Users (EMUs) represent a type of user account available with GitHub Enterprise Cloud accounts. You can manage these accounts from a central location through your existing identity provider (IdP).
Through Enterprise Managed Users, you as the administrator will have detailed control over the GitHub accounts, as long as you are using a compatible identity provider. We will discuss the most important aspects of taking advantage of EMUs.
What Are GitHub Enterprise Managed Users Anyway?
GitHub announced the plans for Enterprise Managed Users and placed it into beta testing in 2020. GitHub began allowing customers to use EMUs late in 2021.
Through EMUs, you as the administrator are able to create and suspend user accounts, manage any of the user profile information for the user accounts, and adjust memberships for your GitHub user teams, all through the identity provider.
Why Should You Use EMUs?
When subscribing to the GitHub Enterprise tier, you will gain access to the Enterprise Managed Users feature. In the past, you as the administrator could ask developers to join your GitHub user group, but they used their existing personal accounts to join the group.
With Enterprise Managed Users, however, you will be able to create accounts specifically for these developers. They then can make use of these accounts only on GitHub repositories that belong to your company. This is a helpful security measure.
Additionally, the owners of any of these Enterprise Managed User accounts linked to your GitHub repositories cannot move any code from a Private repository into a Public repository. This is a key security measure, but it also protects you against a team member accidentally making this error.
Finally, it is easy to track exactly who is signing in to your system when you are making use of EMUs, as everyone who signs in will have a company account. You can be certain that the person signing in has a verified identity. When people are signing in using their individual accounts, the security measures are a little less efficient than they are when using EMUs.
How GitHub Enterprise Managed Users Work
Enterprise Managed Users can make contributions to your enterprise’s various GitHub repositories with a few exceptions.
Public Repositories
Unless otherwise specified or granted, the EMUs will have read-only access to the GitHub community’s public repositories outside of your enterprise. They cannot push code to these repositories, nor can they make pull requests. They cannot even make comments on these repositories outside of their enterprise using the EMU account associated with your enterprise.
Private or Internal Repositories
Your EMUs will be able to make contributions within the private and internal repositories associated with their accounts within your company, as well as private repositories that the EMU owns. EMUs can only own Private repositories, and they can only invite other members of the enterprise to collaborate on these repositories that they own.
When the EMUs create content, only other members of the enterprise are able to view the content. The general GitHub community cannot view it.
GitHub Pricing
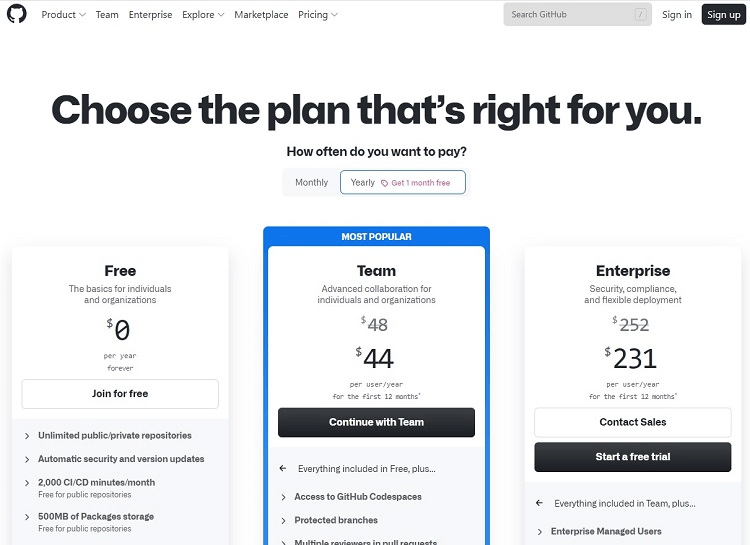
To make use of Enterprise Managed Users, you will have to subscribe to the Enterprise tier of GitHub, which is the most expensive of the three subscription tiers on GitHub.
- Free: The Free tier is available to use for as long as you want, as it is not a free trial. It only allows Public repositories, and it does not support EMU.
- Team: The Team tier costs $4 per month per user or $44 per user with the discounted annual price. It contains everything in the Free tier, along with support for both Public and Private repositories.
- Enterprise: The Enterprise tier costs $21 per month per user or $231 per user with the discounted annual price. It contains everything in the Team tier, as well as allowing for stronger security protocols than the other tiers. This stronger security capability enables the use of EMU. The Enterprise tier also offers Public, Private, and Internal repositories.
If you want to make use of Enterprise Managed Users, it may not be enough to simply subscribe to the Enterprise tier of GitHub. You may also need to contact GitHub to make sure that the EMU feature is active with your subscription, especially if you have an existing Enterprise tier subscription that dates back prior to the 2021 introduction of EMU capabilities.
Provisioning for Enterprise Managed Users
To have the ability to create, disable, and manage your EMUs, you must configure the provisioning for them. With provisioning activated, any time you make changes to the information for a particular user with your IdP, the IdP will automatically update that information in GitHub with the user’s account.
Through provisioning, you also can disable any user’s account through the IdP, and GitHub will then disable that user’s access to the repositories. When you disable an account, it also invalidates SAML (Security Assertion Markup Language) sessions for that user.
However, GitHub will maintain the user’s account information and username. You then have the option to reactivate the account in the future, maintaining the same settings and username.
Before you can configure the provisioning for your EMUs, you will need to create a personal access token. You as the setup user must create this token, and you must set it so that it never expires. You then can begin integrating your EMUs with your identity provider (as we’ll discuss later).
Managing Team Memberships for EMUs
When you want to manage the team memberships for your EMUs, you can do this through your identity provider. The identity provider then will share those changes with your GitHub account automatically, saving time and preventing the potential for manual entry errors. Some of the different rules you may encounter when managing team memberships through your identity provider include:
- Joining new teams: Making a change to one of the groups consisting of EMUs stored with your identity provider may cause your Enterprise Managed Users to join a new team in GitHub. This occurs automatically, rather than requiring manual intervention on your part.
- Removal from teams: If you remove a certain group from a team in the organization, and if certain EMUs only joined that team because of being a member of that group, those EMUs will no longer be part of the team. Additionally, if those EMUs are not a member of any other team in your organization, the process will automatically remove them from the organization.
- Managing repository access: One thing you cannot do through your identity provider is manage repository access for the teams in your enterprise. You will need to make these changes through your GitHub account.
- No manually added EMUs: If you have users you added to your GitHub groups and teams through a manual process before you began using Enterprise Managed Users, you will have to delete those users and re-add them through the identity provider to take advantage of the features and capabilities that EMUs offer.
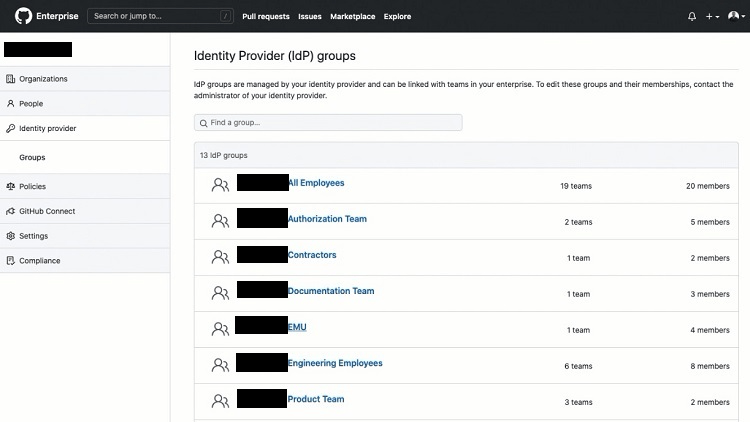
Viewing Connected Teams and Members
If you would like to see the lists of groups in your IdP or see the membership of EMUs in your IdP groups, you can do this through GitHub.
From GitHub, click on the profile icon in the upper right corner of your GitHub window. Then select Your Enterprises from the drop-down menu. Click the name of the enterprise for which you want to view membership. Click Identity Provider along the side of the window.
In the next window, click the name of the group you want to view. In the next window, click Members to see the members of the group or click Teams to see which teams are part of the group.
How to Get Started With SAML SSO for GitHub Enterprise Managed Users
One of the advantages of making use of Enterprise Managed Users is that you can use SAML SSO (Single Sign-on) to authenticate any EMUs. SAML is an open standard used for authentication of users while maintaining online security measures. SSO is a type of sign-on method that requires you to only log in one time while gaining access to multiple apps.
Your Enterprise Managed Users will use SAML SSO to log in to the identity provider securely. They then will have access to a number of other apps, including all aspects of using GitHub, as the identity provider verifies their login credentials. This creates a seamless user experience.
You currently can use SAML SSO with your EMUs if you are using either the Okta or Microsoft Azure Active Directory (AD) IdPs. (In the future, GitHub may add support for more IdPs to its EMU feature.)
To allow your Enterprise Managed Users to take advantage of SAML SSO, you need to take a few preparation steps. Understand that once you activate SAML with GitHub, Enterprise Managed Users will no longer be able to sign in to GitHub with their original username and password. They will need to sign in through the IdP you are using.
Step 1: Integrate EMU With Azure Active Directory
As long as you have a subscription to Azure AD and to EMU through the GitHub Enterprise tier, you can integrate the two. (If you are using Okta instead of Azure AD, skip ahead to Step 2.)
Start by signing in to your Azure AD portal. On the left side, click on the Azure AD service you want to use. Scroll down until you can click on Enterprise Applications. Then click on New Application.
In the search box, type GitHub Enterprise Managed User and hit Enter. In the results box, click on GitHub Enterprise Managed User, followed by clicking on the Create button. (It will take a few seconds for the process to occur.)
Next, configure Azure AD to make use of SAML SSO with EMUs. Back at your Azure AD portal, open the GitHub Enterprise Managed User page. Look for the section labeled Manage and click on Single Sign-On.
In the setup window, click the pencil icon on the far right to change the settings for SAML SSO. (You will need to know the name of your enterprise to be able to continue.)
In the Identifier text box, type https://github.com/enterprises/ followed by the name of the enterprise. In the Reply URL text box, type https://github.com/enterprises/ followed by the name of the enterprise. Then add /saml/consume to finish the URL.
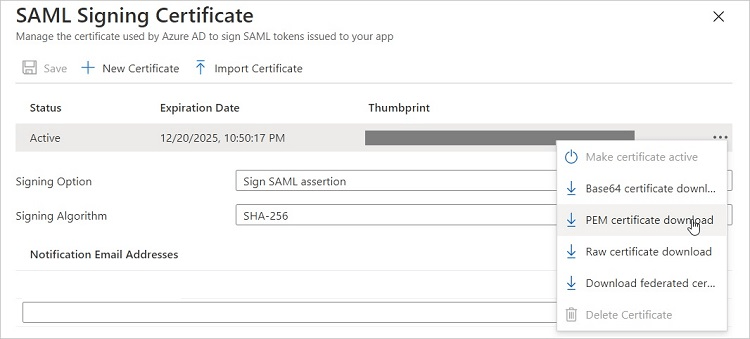
In the SAML Signing Certificate section of the page, you can click on Base64 Certificate Download in the drop-down menu along the right side, which downloads the certificate to your system, so you can copy it. The certificate consists of a text string.
Finally, you will need to take note of the URLs and text string listed in the Set Up GitHub Enterprise Managed User section, because you will need them later.
Step 2: Integrate EMU With Okta
You will need a subscription to both Okta and the Enterprise tier of GitHub with EMU activated to integrate the two.
From the Okta portal, click on the Sign On tab for the GitHub Enterprise Managed User app, followed by clicking Edit. Then enter your enterprise name, so you can sign in to GitHub as the administrator.
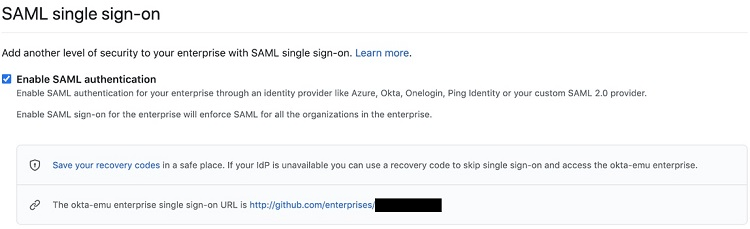
From your organization’s page, click on Settings, followed by clicking on Security. Scroll down to the SAML Single Sign-On section of the page. Place a checkmark in the checkbox for Enable SAML Authentication.
You then will need to enter some specific information for your Okta account into the next three text boxes. When you sign in to your Okta admin dashboard, you can generate these variables and then copy the results over to these boxes. The Sign On URL and Issuer boxes will be URL addresses. The Public Certificate box will contain a text string unique to your account’s security settings. (You also will need this information later, so take note of it.)
After generating and entering this information, click on the Test SAML Configuration button. If you entered the information correctly, you should see a message that your integration passed. Click the Save button.
Step 3: Configure Your Enterprise
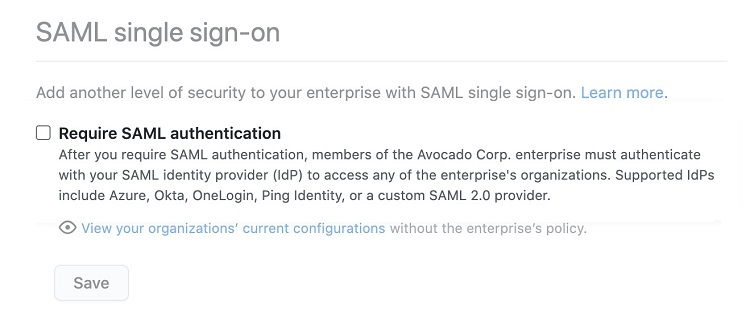
You now are ready to configure your GitHub enterprise to enable Enterprise Managed Users.
Sign in to GitHub as the setup user for your new enterprise. From the home page for GitHub, click on your profile photo in the upper right corner. Then click on Your Enterprises from the drop-down menu.
You may see more than one enterprise listed on the next page. Click on the name of the enterprise you want to use. Along the side of the window, you can see the various menu options for your enterprise. Click on Settings, followed by Security.
In the SAML Single Sign-on window, click on the checkbox for Require SAML Authentication.
Scroll lower in the window, where you will need to enter the URLs and text string that you generated in either Step 1 or Step 2. Enter this information in the Sign On URL, Issuer, and Public Certificate text boxes.
Then click on the pencil icon. You will see a box labeled as Your SAML provider. There are two drop-down menu options within this box. In the drop-down menus to the left of Signature Method and Digest Method, select the hashing algorithms that your SAML issuer is using.
Before you can begin using SAML SSO with your Enterprise Managed Users, you will need to take one more step. Click the Test SAML Configuration button. You should receive a message that you entered the information correctly and that you passed the test. If not, you will need to double-check whether you entered the information correctly and try the test again. If you do receive a positive message, click the Save button.
After you click Save, you should see a box that contains recovery codes. You can click on the Download, Print, or Copy buttons to save your recovery codes. You would need these codes if you ever cannot sign in to your identity provider, meaning you need to access your GitHub account directly.
Remember, once you set up EMU with your identity provider, your users cannot sign in to GitHub directly, unless you make use of these recovery codes. They must sign in through the IdP.

