The Ultimate Manual to Cloud Access Security Brokers
Cloud access security brokers, or CASBs, have become a crucial aspect of enterprise security in the modern era. CASBs allow organizations to use the cloud safely while protecting sensitive company information and data.
This in-depth guide will explain everything you need to know about cloud access security brokers and how to use a CASB solution for your business.
What is a Cloud Access Security Broker Anyway?
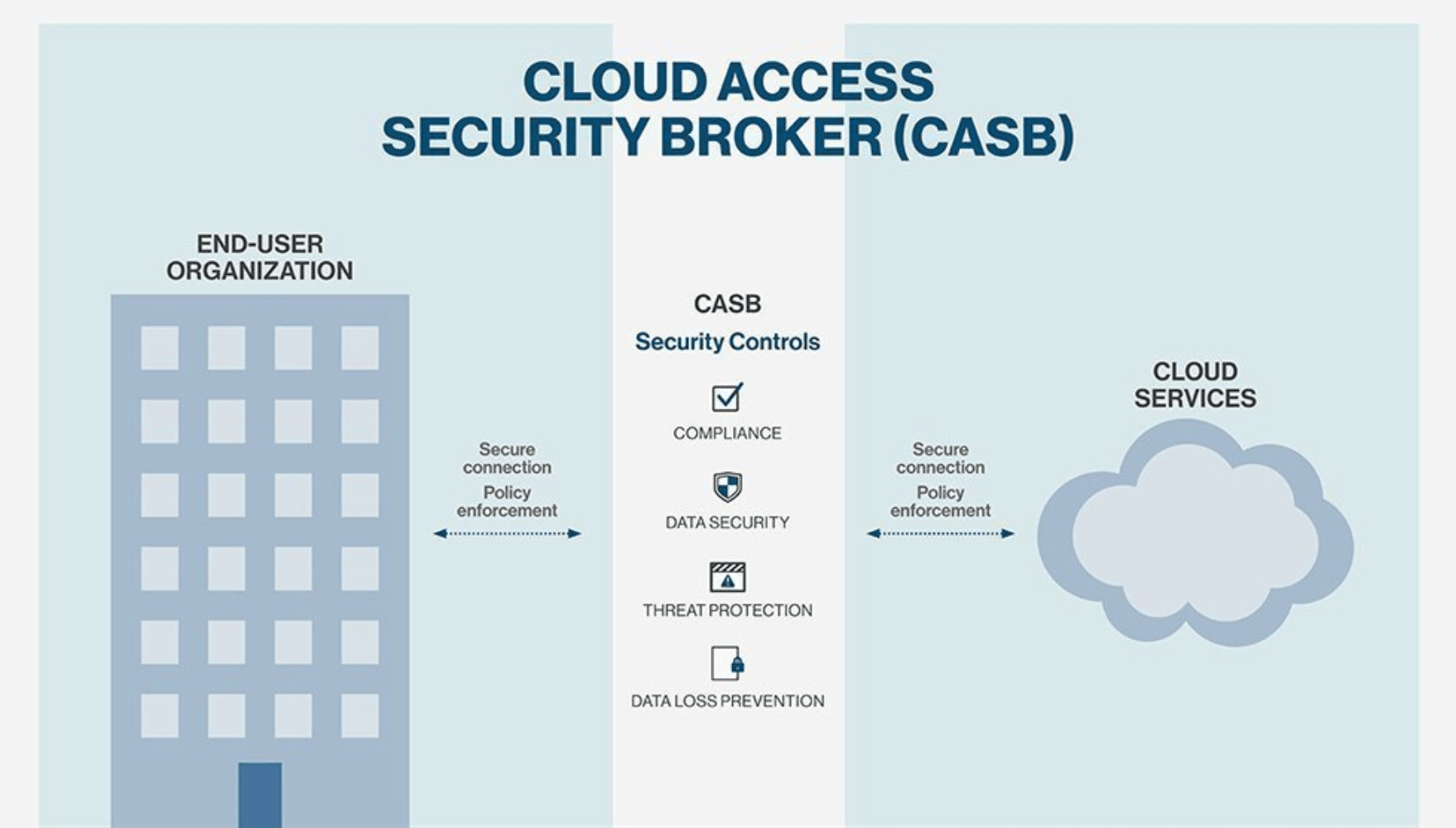
CASBs are security policy enforcement points that separate cloud service customers from cloud service providers. They can be deployed on-premises or as a cloud-based solution.
As cloud-based resources are accessed by users, the CASB enforces the policies set by the cloud service administrator.
In the simplest terms, a cloud access security broker is a policy enforcement center.
The CASB consolidates different types of security policies and applies them to everything an organization uses in the cloud. CASBs work regardless of the device attempting to access resources, including workplace devices, personal smartphones, laptops, and even IoT devices.
CASBs have become extremely useful in recent years as workplace mobility has increased. As BYOD at work has grown in popularity, the ability of IT security departments to monitor and govern the usage of cloud applications has become more important than ever before.
Instead of eliminating cloud services altogether, which could potentially harm employee productivity, CASBs allow organizations to enforce data protection policies with a granular approach. This helps save time and money without hindering workplace productivity.
CASB vendors help businesses reduce cloud service risks, comply with certain regulations, and enforce security policies—even when the cloud services being used aren’t directly in control of that business.
How Cloud Access Security Broker Works
Before the days of BYOD in the workplace and cloud computing, enterprise security was fairly straightforward. Everything was controlled within the “walls” of an organization.
But once employees started to use cloud services (with or without IT security approval), companies needed a way to enforce security policies consistently across multiple cloud platforms—and they had to do so while protecting their users and corporate data alike.
With the development of CASBs, IT security professionals gained more visibility into the cloud, including shadow IT and sanctioned SaaS usage. The results were shocking. According to a recent report from McAfee, the average IT professional thought that businesses were using roughly 30 cloud services—but they were actually using an average of 1,935.
This is one of the many reasons why CASBs have become so widely adopted in the enterprise security space. With most businesses moving data from on-premises data centers to cloud storage systems, CASBs helped protect the way the data moved while simultaneously protecting the data’s contents.
Security protocols like sharing privileges, access controls, and encryption can all be enforced using a CASB.
The exact features offered by a CASB vendor will vary from solution to solution. But many CASBs offer features like:
- Data loss prevention tools
- Data encryption
- Key management
- Contextual access control
- Threat prevention
- UBEA (user and entity behavior analytics)
- The ability to control native features of cloud services (such as sharing and collaboration actions)
- Configuration audits
- Cloud governance
- SSO and IAM integrations
- Malware detection
There are four foundational pillars of CASBs—visibility, compliance, data security, and threat protection. Each pillar is required to have an effective cloud access security broker program.
Let’s take a closer look at each CASB pillar below:
Visibility
A cloud access security broker all starts with visibility. Organizations need this visibility to control access for managed and unmanaged cloud services alike. So instead of just allowing or blocking all cloud service systems as a whole, the brokerage system allows the IT team to allow services while governing the usage and activities within the service itself.
For example, an organization could grant access to the full suite of Microsoft Office 365 when employees are accessing the tools on a corporate device. But if the users are trying to access Microsoft Office 365 from a personal device, the CASB could enforce email-only access while restricting the rest of the suite.
The reason why visibility is so important is that it allows IT security professionals to discover what cloud services are being used and how they’re being used. Then you can use that information to enforce enterprise security policies.
Compliance
When enterprises decide to move their data from an on-premise storage system, compliance must be a top priority. A potential breach here can be extremely costly if the wrong personal or corporate data is exposed to the wrong hands.
For example, a healthcare organization migrating data would need to be concerned with HIPAA and HITECH compliance. Retail organizations that process credit cards need to focus on PCI compliance. Financial institutions need to comply with FINRA and FFIEC regulations.
With a cloud access security broker, all of this sensitive data can be safeguarded and upheld with the data regulations imposed by your specific industry. CASBs will also help you identify the highest areas of risk, which can help provide your team with security protocols to prioritize.
Even if you’re outsourcing data storage to the cloud or using a third-party system, it’s still your responsibility to uphold all compliance standards.
Data Security
Cloud systems have essentially eliminated barriers when it comes to collaboration in the workplace. Data can move seamlessly from one entity to another.
While this type of data movement can make operations more seamless and efficient, it also exposes businesses to potential threats. Sensitive data and confidential information can easily end up in the wrong hands if data security protocols aren’t properly implemented.
There are plenty of on-premises data loss prevention (DLP) solutions designed to safeguard data, but these alone don’t extend to cloud services. But combining CASBs with a DLP tool helps IT pros monitor when sensitive data is traveling to or from a cloud system and monitor movement within the cloud.
CASBs can govern access control, information rights, data loss prevention, collaboration, encryption, and tokenization—all of which can limit enterprise data leakage.
Threat Protection
Whether it’s done with malicious intent or negligent behavior, sensitive data can easily be stolen from cloud services. All it takes is for someone’s credentials to leak or end up in the wrong hands.
To protect against these types of threats, CASBs can compile a view of user behavior patterns. Then they’ll use this information to create a basis for comparison purposes. Machine learning technology paired with user and entity behavior analytics (UEBA), a cloud access security broker can detect threats if improper access is gained to a system.
Furthermore, CASBs can also implement security protocols for adaptive access control and use threat intelligence to block malware threats.
Example 1: Usage Governance For Cloud Solutions
CASBs give organizations the ability to govern cloud usage with granular control and visibility.
Instead of imposing a one-size-fits-all solution by blocking or denying cloud solutions, you can govern usage with a CASB. You’re able to govern that usage based on things like data, application, service, identity, activity, and more.
Furthermore, you can define data governance usage policies based on a specific risk or service category. For example, you can choose an action like:
- Alert
- Block
- Encrypt
- Bypass
- Quarantine
These actions can be applied and enforced automatically based on a trigger. Your IT team can be notified of a specific behavior or incident that violates your organization’s enterprise security policies.
Example 2: Secure Sensitive Data
A CASB allows businesses to protect data while it’s stored, while it’s being accessed, and while it’s being shared.
In addition to protecting the data in your enterprise environment, CASBs extend to all cloud services—including unsanctioned resources.
Many organizations pair CASBs with advanced DLP (data loss prevention) software. This helps IT security teams monitor and protect data whether users are accessing it remotely, on-site, from the web, from a mobile device, or accessing from a sync client service.
CASBs also fight data loss using principles like tokenization, encryption, and upload prevention rules.
Example 3: Prevent and Protect Cloud-Based Threats
Another common use case for CASBs is protecting data from cloud-based threats, like ransomware and malware.
This all begins with having full visibility into all cloud services, including the ones using an SSL-encrypted connection.
CASBs can leverage anomaly detection and threat intelligence to determine which user credentials have been compromised. Then the system can use both static and dynamic anti-malware detection and machine learning to prevent ransomware.
The CASB can ultimately arm your IT security infrastructure with its findings, then deploy automated rules and workflows to prevent these threats from accessing sensitive data or internal systems.
How to Get Started With Cloud Access Security Brokers
Now that you fully understand what a cloud access security broker is and how CASBs work, it’s time to get started with one of your own. These are the steps you must take to have success rolling out a CASB for enterprise data security:
Step 1: Perform Due Diligence
Before you deploy a new system, you need to take a comprehensive look at your options.
It’s common for CASB providers to offer things like free trials and cloud audits to get the ball rolling. These types of solutions will help you gain a big-picture view and perspective of your overall IT security infrastructure.
Assess your existing cloud security tools and strategies. I’m referring to things like web gateways, firewalls, DLP software, and more. Will these tools play nice and integrate seamlessly with a CASB?
In many cases, you’ll have the option to integrate your cloud access security broker with an IAM (identity and access management) application or SSO app. It’s in your best interest to narrow down your needs sooner than later as you’re shopping around.
Take full advantage of different free trials and audits offered by your top considerations. This will help you feel confident about your selection, so you won’t need to second-guess or change tools down the road.
Rather than testing a CASB solution across your entire organization, deploy it on a smaller scope during the trial phase. You’ll still want to use it on an essential cloud service, so you know that it’s compatible when you’re moving forward. From there, you can expand the tool on a broader basis.
Step 2: Choose a CASB Solution
After you finish the due diligence phase, it’s time to narrow down your options to a single solution. Here are some questions you should ask during the evaluation process to help you finalize the winner:
- Is the solution a good fit for your organization?
- Can the CASB grow and adapt as your needs change?
- Does the tool protect IaaS environments?
At the end of the day, you need to select a CASB that addresses your top business goals. These goals can easily get lost in the shuffle throughout this process.
Enterprise cloud usage is continuing to grow exponentially, with no signs of slowing down in the foreseeable future. That’s why it’s so important to ensure your CASB solution can scale with you as your company grows.
Things like compliance, new cloud security policies, and data migrations all need to be taken into consideration here.
Finally, your IaaS (infrastructure as a service) environments must be protected. The cloud access security broker should not only protect the activity and configurations of your infrastructure but also needs to defend against your customers and end-users.
Step 3: Deploy Your Cloud Access Security Broker
Similar to the testing and audits performed back in step one, CASB deployment should be done in phases. Trying to do too much too quickly can spiral out of control.
First, assess your deployment location. Do you want to deploy on-premises or in the cloud? The majority of cloud access security brokers are SaaS-based, but some organizations prefer on-site deployment.
You’ll also need to choose a deployment model. In most cases, CASB deployments can be broken down into three major categories:
- API Control — Provides visibility into the cloud for data and threats, offering comprehensive coverage and fast deployment
- Reverse Proxy — Better for devices outside the scope of network security
- Forward Proxy — Typically works jointly with endpoint protection and VPN clients
Proxy deployments are commonly used for data residency compliance and inline control enforcement in real-time.
Your deployment should cover a wide range of cloud access scenarios. This can help you expand as your needs change, and the deployment will roll out in stages.

