CIS Controls V8 Vs. CIS Top 20 Critical Security Controls
The CIS Controls serve a single purpose: to identify the most common and important cyberattacks in the real world that affect enterprises and then translate the knowledge and experience into constructive action for business leaders.
Created by the Center for Internet Security (CIS), these benchmarks have since matured into an internal community of dedicated volunteer cyber experts and institutions. Some of the responsibilities include:
- Sharing insights into attacks and attackers, identifying root causes behind these attacks, and distributing their information to the wider audience to help them form a solid defensive action
- Creating and sharing effective tools, working aids and guidelines, and the adoption and problem-solving stories
- Mapping the CIS controls into compliance and regulatory frameworks, ensuring alignment, and bringing collective focus and priority to them
- identifying common problems and barriers (implementation roadmaps, initial assessments) and solving them together as a community
Recently, CIS released version 8 of these controls at the global RSA Conference 2021, lowering the number of critical security controls to 18 from 20. While the former is now known as CIS Controls V8, the latter is called CIS Top 20 Critical Security Controls.
This Nira guide will explore CIS Controls V8 vs. CIS Top Critical Security 20 Controls in detail to help you prioritize security controls and effectively protect your systems against real-world threats.
What Is the Center for Internet Security (CIS)?
The CIS is a non-profit NGO that creates its own Configuration Policy Benchmarks (CPB)—benchmarks that serve as guidelines for organizations to improve their cybersecurity and compliance posture and programs. It comprises the following four program divisions that are designed to promote internet security at the global level:
- Integrated Intelligence Center. This division facilitates relationships between private sector entities and the government to build and disseminate in-depth, coordinated security intelligence.
- Multi-State Information Sharing and Analysis Center. This division tries to improve the overall cybersecurity across all levels of the government—state, local, territorial, and tribal—through information sharing and collaboration among members, private sector partners, and the U.S. Department of Homeland Security.
- Security Benchmarks. This division develops and promotes consensus-based best practice standards usage to improve the security and privacy of internet-connected systems. It also ensures the integrity of internet-based functions and transactions on public and private platforms.
- Trusted Purchasing Alliance. This division helps the public and private sectors procure cybersecurity tools and policies cost-effectively.
In a nutshell, the CIS strives to create a dedicated community who are responsible for developing security configuration baselines for IT and security products. It also issues a series of trusted protocols called CIS Controls that are regularly updated and reviewed by an informal community for relevance.
What Are CIS Top 20 Critical Security Controls?
Previously known as the SANS Top 20 Critical Security Controls, the CIS Top 20 Critical Security Controls are a prioritized set of cybersecurity best practices that can help protect enterprises from the most pervasive and dangerous attacks.
These 20 Controls are based on information the CIA‘s team of experts found most relevant to curb common attacks a few years ago. Here’s a rundown of each one:
1. Inventory of Authorized and Unauthorized Devices.
Organizations should actively engage all hardware devices connected to corporate assets—the network, email services, or cloud applications—so that only authorized devices get access. This will also help quickly identify unauthorized devices and disconnect them before they cause any harm.
Malicious hackers are continuously scanning the address space to find new and unprotected organizational systems attached to corporate assets. Luckily, this control can protect you from falling victim to these hackers’ whims.
2. Inventory of Authorized and Unauthorized Software
Organizations should manage all software on their networks in a way that only allows the installation of authorized software. Taking relevant security measures like application whitelisting can help you quickly find and flag unauthorized software before anyone on your team installs it on your system, compromising its security.
This control is critical as attackers are always looking for vulnerable versions of software that can be exploited remotely. They tend to distribute virus-infected web pages and other forms of media content or use zero-day exploits to take advantage of unknown vulnerabilities. But when you have proper knowledge of what software has been deployed in your organization, it’s easier to ensure data security and privacy.
3. Secure Configurations for Hardware and Software
Establishing, implementing, and managing security configurations of everyday devices like servers, laptops, and workstations is a common cybersecurity best practice. Your team should follow strict configuration management and implement change control processes to stop attackers from exploiting vulnerable services and settings.
4. Continuous Vulnerability Assessment and Remediation
Business leaders should continuously acquire, assess, and act on newly acquired information concerning their systems and the current head landscape. This can include software updates, patches, threat bulletins, and security advisories.
This information will help you identify and remediate vulnerabilities that cybercriminals could otherwise leverage to penetrate your networks.
5. Controlled Use of Administrative Privileges
Under this control, companies are encouraged to use automated tools to monitor user behavior and track how administrator privileges are assigned and used. In turn, this prevents unauthorized access to critical systems.
6. Maintenance, Monitoring, and Analysis of Audit Logs
Organizations are responsible for collecting, managing, and analyzing event logs. Doing this will allow them to detect any suspicious activities and investigate security incidents.
This control seeks to eliminate the lack of security logging and analysis, thereby preventing attackers from hiding their location and activities in the network.
7. Email and Web Browser Protections
Organizations should use (fully) supported web browsers and email clients to minimize their attack surface.
Email clients, for example, are a common entry point as they are fairly technical and flexible. They can create content spoofing users into taking actions that may introduce malicious code into their system, leading to the loss of valuable data.
8. Malware Defenses
This control suggests automated tools for monitoring workstations, mobile devices and servers with antivirus, anti-spyware, and firewalls. It also helps detect malware and unknown suspicious software as well as test evasion techniques for malware defenses.
9. Limitation and Control of Network Ports, Protocols, and Services
Tracking in managing ports, protocols, and services or network devices is another organizational responsibility to reduce the windows of vulnerability available to attackers.
10. Data Recovery Capability
Companies should back up critical systems and data every week (at the minimum).
Attackers often change the configuration, software, and data during a cyberattack. Without a reliable backup and recovery system, you may not recover post-attack.
11. Secure Configurations for Network Devices
Organizations must create, implement, and manage security configurations of network infrastructure devices such as routers, firewalls, and switches.
Network infrastructure configurations are geared for ease of deployment and not security. Plus, network devices are less securely configured over time, allowing malicious hackers to exploit these configuration flaws and get access to networks or exploit compromise machines to pose as trusted systems.
12. Boundary Defense
Businesses have to detect and correct information flow between networks of different trust levels while focusing on data that could damage security. The best defense, in this case, is to use technologies providing deep visibility and control over data flow across your environment (think: intrusion prevention systems, intrusion action).
13. Data Protection
Organizations are required to use appropriate processes and tools to eliminate data exfiltration risks while ensuring the integrity of sensitive information. This control outlines a combination of best practices concerning encryption, integrity protection, and data loss prevention techniques.
14. Controlled Access Based on the Need to Know
Tracking, controlling, and accessing critical assets is crucial—and it allows leaders to easily determine which people, computers, or applications should have the right to access them and at what level.
15. Wireless Access Control
Organizations need to implement certain tools and processes to effectively track and control how their employees use wireless local area networks (LANs), wireless client systems, and access points.
For this, they will conduct network vulnerabilities scanning and ensure all wireless devices connected to the network have an authorized configuration and security profile.
16. Account Monitoring and Control
Business leaders are responsible for actively managing the lifecycle of user accounts (creation, use, and deletion) to prevent creating opportunities for hackers to misuse them. All system accounts should be regularly reviewed, while accounts of former contractors and employees should be disabled as soon as they leave the company.
17. Security Skills Assessment and Appropriate Training to Fill Gaps
It’s important to identify the specific knowledge and skills organizations need to strengthen security. This requires developing and executing plans to identify and fix gaps through policy, planning, and training.
18. Application Software Security
Managing the security lifecycle of all software is another necessary activity.
This is important to detect and correct security weaknesses which is why IT teams should regularly check employees are only using the most current versions of an app and that all relevant patches have been timely installed.
19. Incident Response and Management
Organizations have to develop and implement proper incident response. This includes creating plans, defining roles, training, management oversight, and other related measures that can help them discover attacks and control damage faster and more effectively.
20. Penetration Tests and Red Team Exercises
This control requires organizations to gauge their overall defense security, including the technology used, processes implemented, and the expertise of people responsible for executing them. It involves conducting regular external and internal penetration tests to identify vulnerabilities and attack vectors that malicious hackers may use to exploit systems.
What is CIS Controls V8?
CIS Controls V8 is just the new and improved version of the CIS 20 Critical Controls.
CIS wants these standards to be as relevant as possible and, therefore, keeps rethinking versions to focus on the role of these controls in the end picture of enterprise security.
Since the last version, the world has seen significant changes in the technology and cybersecurity ecosystem. As a result, physical devices, discrete lines of security implementation, and fixed boundaries are less important today.
Version 8 reflects these changes and has revised the terminology and Safeguard grouping for greater relevance. Here’s a comparison diagram:
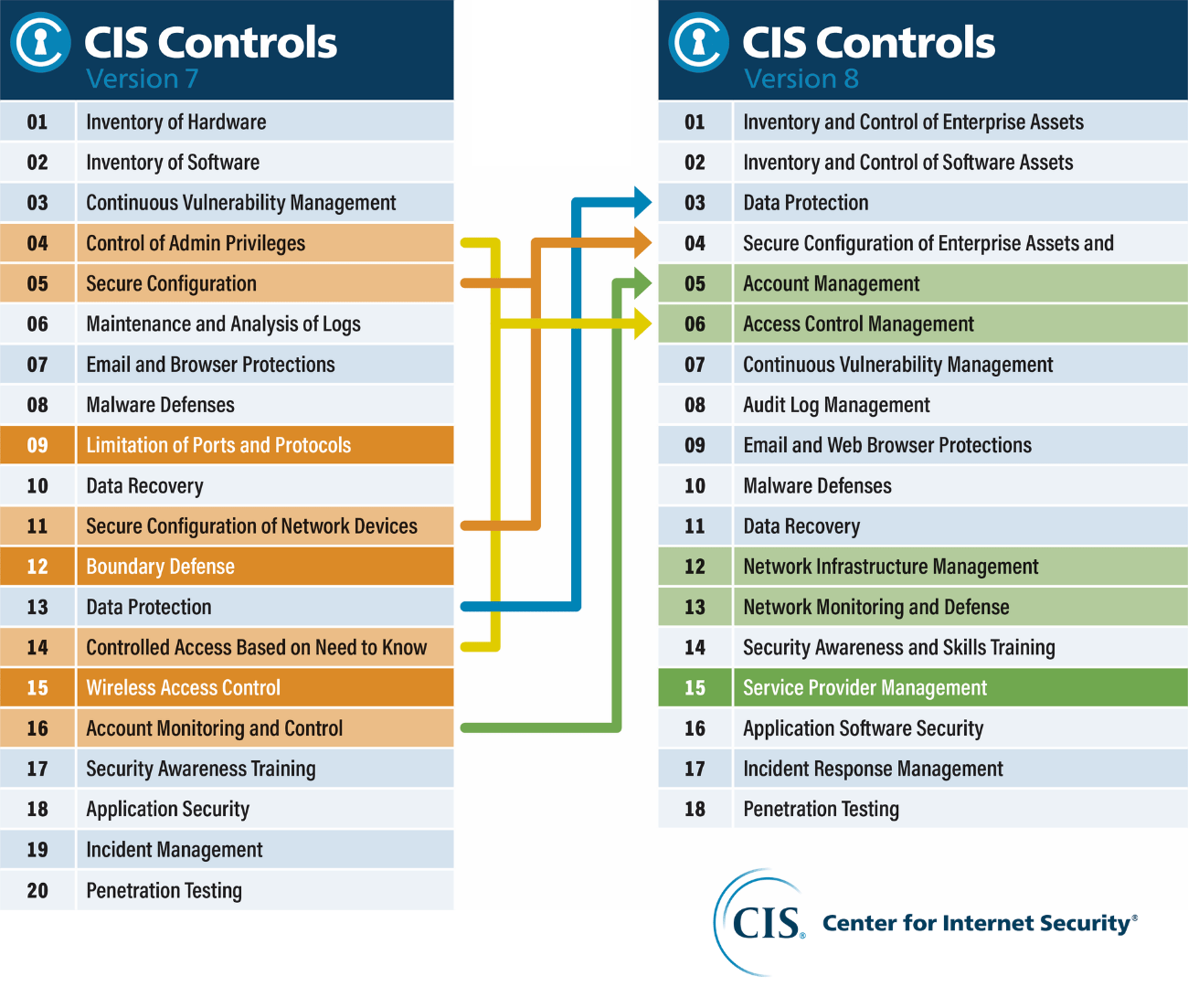
Let’s discuss these changes in more detail below.
Updated for Relevance in the Current Cyber Ecosystem
CIS Controls V8 is designed to keep up with modern systems and software.
This was prompted by the movement to cloud-based computing, mobility, outsourcing, work-from-home, virtualization, and changing attacker tactics. As a result, the new Controls can better support your organization’s security requirements, regardless of whether you adopt a cloud or hybrid environment.
Implementation Group 1 (IG1) Definition
IG1 primarily defines basic cyber hygiene while representing an emerging minimum standard of information security for enterprises. Think of it as the foundational set of cyber defense safeguards that can be applied to safeguard your systems against common cyber attacks.
IG2 and IG3 build up on previous IDs, but IG1 is the on-ramp to the Controls.
Simplified and More Consistent
Each Safeguard has been created in a way that requires minimum interpretation.
Focused on measurable actions, each Safeguard defines the measurement as part of the process and is drafted using simple language to avoid duplication.
Task-Based Focus Regardless of Who Executes Controls
You may have noticed that CIS Controls Version 8 combines and consolidates controls by activities instead of who manages the device.
This is because fixed boundaries, discrete islands of security implementation, and physical devices aren’t as important today, thereby decreasing the number of Controls from 20 to 18.
Controls Name Update
Besides the revised terminology and grouping of Safeguards, the consolidated Controls are now officially called the CIS Controls. Previously, it was known as the SANS Critical Security Controls (SANS Top 20) and the CIS Critical Security Controls.
SANS served on the editorial panel of Controls v8.
Other Cybersecurity Best Practices Guidance
Version 8 Controls cooperate with and align with existing independent standards and security recommendations wherever possible.
The CIS Controls Ecosystem Isn’t Only About the List
While the CIS Controls are essentially security recommendations, it “isn’t only about the list.“
Instead, think of these Controls as the starting point to improve your organization’s overall security posture. Try to look for the ecosystem that grows up around this list. What’s more, the new version also provides backward compatibility with previous versions, plus a migration path to help past version users upgrade to v8.
CIS simply acts as a catalyst helping you avoid making the same mistakes as other enterprises and create a mutually beneficial environment where we can all learn from each other.

