CASB Security Vendors: The Ultimate Manual
All cloud-based infrastructures need robust cloud access security broker (CASB) solutions. CASB security vendors provide organizations with data security, application security, and integrity throughout the cloud.
This in-depth guide explains everything you need to know about CASB security vendors, how they work, and how to get started with them.
What is a CASB Security Vendor Anyway?
CASB is an acronym for “cloud access security broker.” CASB security vendors provide cloud-based technology to enforce enterprise security policies—specifically for cloud services access.
The vast majority of CASB software is packaged as SaaS (software as a service). The technology is designed to secure cloud data or data stored within cloud-based applications.
CASB security vendors offer solutions with protection between users and cloud services, whether the users are remote, on-site, authorized, or unsanctioned.
Vendors offering CASB technology can prevent unauthorized users from accessing cloud applications. These tools also help fight against data breaches and data loss.
CASB security brokers ensure that cloud applications can run in a secure environment. They also offer a secure, single source of truth for users to access those applications.
Enterprise organizations turn to CASB security vendors as a way to enforce cloud security policies, address risks with cloud-based applications, and remain compliant.
How CASB Security Vendors Work
CASB security vendors work in many different ways. But in the simplest possible terms, they act as a filter, proxy, or firewall between cloud applications and users.
These systems are designed to detect unauthorized usage and access to cloud infrastructures based on an organization’s cloud security policies. CASBs can encrypt traffic from cloud providers and protect sensitive data while it’s in transit.
Internet-enabled technology and cloud computing come with a fair share of risks for organizations. Security measures like web gateways, web application firewalls, and enterprise firewalls are definitely a start. But these don’t always accommodate security threats for cloud-specific applications.
The same systems that protect the information in a private data center don’t translate to the cloud. That’s where CASB security vendors come into play.
CASB security vendors offer technology to protect cloud applications. Cloud-based operations still need solutions for access control, data loss prevention, breach logging, network visibility, threat protection, and more.
This is especially true as remote work continues to grow and end-users are trying to access enterprise cloud apps from anywhere. When users aren’t limited to a single location, it poses additional threats to enterprise security.
But without a CASB security vendor, complete visibility into the wide range of access points, devices, and users in your BYOD policy won’t be effective. You can’t rely on a legacy security system designed to monitor threats on a local network. You need a CASB for monitoring and authentication that works from anywhere.
Benefits of CASB Security Vendors
At their core, CASB security vendors offer solutions for cloud application control, data access, and security enforcement. These can come in the form of device profiling, encryption, single sign-on, authentication and authorization, tokenization, and more.
Many CASB security vendor solutions come with alerting capabilities, malware prevention, credential mapping, and other useful features.
Some of the top benefits of using a CASB security vendor include:
- Continuous monitoring for threats and vulnerabilities in the cloud
- Audit trail recording for potentially dangerous behavior
- DLP (data loss prevention) for cloud applications and environments
- Account takeover detection
- Restricting unauthorized users, devices, and access
- Detect and prevent shadow IT
- Apply internal data access controls
- Apply external data access controls
- Detect and prevent phishing and malware in the cloud
It should be noted that CASB security systems are not a replacement for IAM (identity and access management) solutions. With that said, CASBs can work in tandem with IAM systems or identity-as-a-service security tools.
CASB security brokers help improve IAMs by offering cross-application security and behavior monitoring across cloud applications.
Four Pillars of CASB Security
There are four main foundations of all CASB security solutions.
- Visibility — CASB security vendors provide complete visibility into enterprise cloud application usage. This includes who is using which cloud apps, the user’s location, what department they’re in, and what devices they’re using.
- Compliance — CASBs can apply regional or industry-specific compliance mandates based on your data security policies. For example, they can help you remain SOX compliant, HIPAA compliant, PCI compliant, and maintain ISO 27001 standards.
- Data Security — Unlike traditional DLP (data loss prevention) solutions, CASB security vendors can help detect what data has been shared with external sources outside of the organization. The vendors can also tell your IT security team who is sharing that data and when the external share occurred.
- Threat Protection — This pillar is designed to safeguard against malicious actions of both authorized and unauthorized users. For example, a disgruntled employee or ex-employee with a grudge can pose a significant risk to an organization, as they still have access to cloud applications with sensitive data. But CASBs help detect suspicious behavior and usage patterns to protect and fight against these types of threats.
Now let’s take a look at some real CASB security vendors. This will help you better understand exactly how CASB security vendors work.
Example #1: iboss
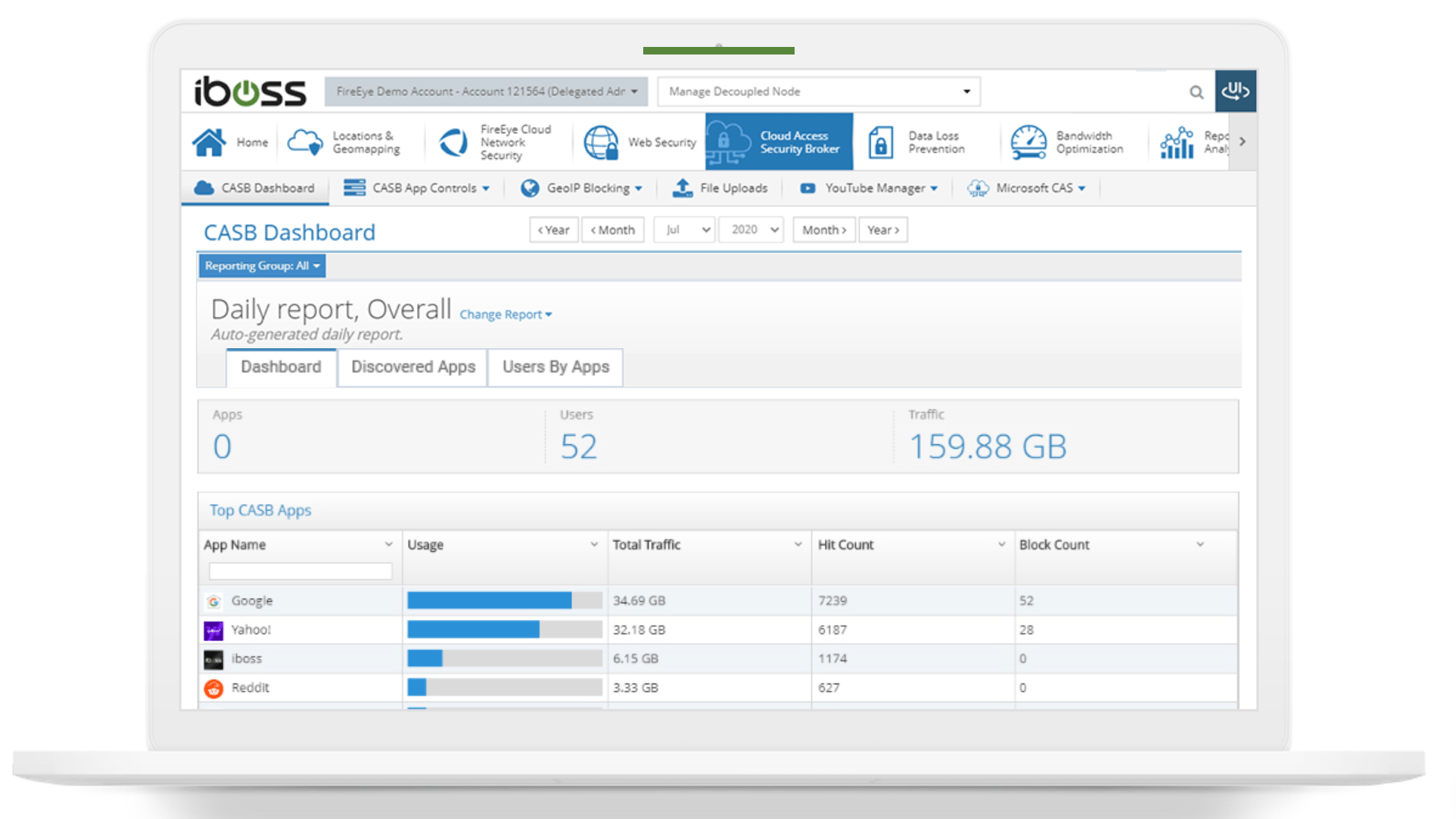
The iboss CASB platform offers cloud application visibility and controls for organizations. It gives companies the ability to see exactly how users and applications are being used.
It integrates natively with Microsoft CAS and can be deployed using API CASB—also known as “out-of-band” protection.
This CASB security vendor is versatile enough to accommodate the needs of organizations across a wide range of industries. It supports cloud security in finance, education, government, healthcare, and business.
iboss lets you control cloud applications like Twitter, LinkedIn, Facebook, search engines, and more to ensure organizational users are meeting industry-specific compliance requirements. For example, you can make sure sensitive data isn’t posted to social sites that violate PCI or HIPAA compliance.
Example #2: Lookout
Lookout is another excellent example of a CASB security vendor. The vendor offers advanced features like integrated endpoint protection, DLP, zero-trust security, UEBA, and more.
It’s a great option for organizations that want to see deep analytics on both user and entity behavior across cloud applications. The vendor can assess cloud network traffic, users, and the devices that they’re using as well.
Lookout also offers enterprise-grade mobility management features that your IT admins can apply to your endpoint policies. This is ideal for organizations that allow BYOD.
You can also use Lookout for contextual tags related to devices, operating systems, behaviors, locations, users, and more.
Example #3: Palo Alto Networks

Palo Alto Networks has a wide range of services in the enterprise security space, particularly when it comes to CASBs. NEXT falls under the security vendor’s Prisma Cloud Services blanket.
NEXT is a next-gen CASB designed for real-time protection for cloud access and proactive network visibility.
This CASB security vendor allows organizations to rapidly deploy new SaaS solutions without hindering the user experience or sacrificing cloud security. It supports apps both in the cloud and on-premises.
The tool scans all of your traffic, ports, and protocols as well. It supports API-based deployments and automatically discovers new applications in your cloud infrastructure.
As a cloud-delivered enterprise DLP solution, this CASB security vendor will automatically enforce your data policies at scale. It’s one of the easier solutions to deploy in the broader CASB category.
How to Get Started With CASB Security Vendors
Getting started with a CASB security vendor might seem intimidating, especially if you haven’t been through this process before. Fortunately, these simple steps below will walk you through the process with ease.
Step 1: Audit Your Network Applications and Cloud Usage
The first thing you need to do is get full visibility into your existing cloud network.
What applications is your organization using? Who is using those applications? What are those applications being used for?
Go deep here. Identify users along with their devices, location, and departments. This step is designed to give you more visibility into how people are using applications within your cloud infrastructure.
From here, you can begin to forecast your risk. Where is your organization vulnerable in terms of cloud security? How do these vulnerabilities align with your company’s security goals?
As we’ve seen from the examples earlier in this guide, not every CASB security vendor is the same. Yes, many offer similar solutions, tools, and products. But some specialize in certain categories or specific areas of cloud security.
For example, are you more vulnerable to hackers gaining access to your cloud applications using leaked credentials? Or are you more vulnerable to former employees who still have access to organizational cloud applications?
Both pose unique risks to network administrators, especially if those users have malicious intent. But the way to detect and prevent those threats will be slightly different.
Step 2: Identify Your Must-Have Features
Before you start comparing different CASB security vendors, take some time to assess what you’re looking for in a CASB solution. Write out a list of your must-have features, and then compare that list against the various features offered by different security vendors.
Some common examples include:
- User Analytics — Ability to monitor and view users on an individual level. This includes suspicious behavior and alerts to IT security admins when anomalies occur.
- SSO — Single sign-on features offer one point of access for users working with multiple cloud applications without needing to use multiple credentials. This feature helps improve the end-user experience and boost productivity without compromising security.
- Access Control — Features such as LDAP (lightweight access directory protocol) help simplify the admin’s ability to update applications and information in conjunction with security policies.
- Mobile Device Management — Also known as MDM, this capability allows organizations to enforce BYOD policies and manage mobile devices accessing enterprise applications. The security team can customize all of the permissions and mobile access requirements of users on-site or working remotely.
- Cloud Gap Analysis — This feature looks at data like policy violations and denials. These reports help IT security admins identify threats and see where they can improve different protocols.
- Anomaly Detection — You want the ability to see behavior that falls outside of what’s considered “normal.” By comparing usage with benchmarked patterns, CASB security vendors can potentially identify malicious users.
You should also look at the cloud registry of every CASB security vendor. This typically comes in the form of a list of all SaaS applications that work with the CASB tool. With a cloud registry, users can look at different integrations or new applications, knowing that they’re compatible with the CASB security vendor.
Step 3: Consider Your Deployment Options
Again, not all CASB security vendors are the same. One differentiator to consider is how they’re deployed to secure your organization’s cloud infrastructure.
Let’s take a closer look at those options.
One deployment method is known as a forward proxy. This positions the CASB closer to the users and proxies the traffic to different cloud services. With this deployment method, the security solution uses “man-in-the-middle” practices to guide traffic towards the proxy.
If you’re using a forward proxy, you need to install self-signed certificates on every device that’s accessing the proxy. This method can also cause some latency on your network if a lot of users are using applications.
Alternatively, you could deploy your CASB solution with a reverse proxy. As implied, this is the opposite of a forward proxy—meaning the proxy is deployed closer to the cloud applications.
Typically, reverse proxies integrate better with IAM tools and IDaaS (identity-as-a-service) solutions. Reverse proxies usually don’t need any certificate installations or specialized configurations, making them easier to scale. They simply get requests from the cloud application and apply your organization’s predefined security policies.
API-based deployment is the third most common option. This is also known as “out-of-band” CASB protection.
Refer back to what we said earlier when describing how CASB security vendors work. Think of your CASB as sitting in the middle of your cloud applications and users.
To make this happen, you can use asynchronous APIs to enforce your security policies. The APIs can take all of the traffic events and your security configurations to apply the appropriate rules.
As APIs become more sophisticated, they could eventually eliminate the need for proxy-based deployment methods for CASBs.
But for now, you’ll still have to weigh your options to determine what’s better for your organization and cloud security policies.

