The Ultimate Manual To Box Security and Compliance
Cloud storage is a highly convenient option for organizations that need to share and collaborate files and data. However, without the right security and compliance features in place, this convenience can become a security nightmare in very little time.
The Box cloud storage service has strong security and compliance measures built into it versus other cloud storage providers, providing peace of mind for organizations.
What Is Box Security and Compliance Anyway?
Box’s security and compliance features provide assurances to customers that Box’s hardware, software, and data storage policies will protect customer data.
Different customers will have varying requirements, and they are able to configure Box to match the security and compliance needs they have.
Understanding Box Security
As organizations rely on cloud storage services like Box to store data remotely, security is a significant concern. Security involves protecting the data as it passes from the organization to Box and as Box stores it.
Customers need to feel comfortable that the data is secure from viruses and malware during storage at Box. They need to have assurances that data breaches will not occur. And they want to feel comfortable that Box has backup procedures in place that protect the data from potential physical disasters.
Cloud storage services like Box must be able to protect the information at the highest possible levels. Mistakes that lead to security breaches are devastating to both the cloud storage provider and the customer.
At the same time, if the security measures prevent end-users from accessing the data easily, they create frustration. End-users may attempt to skirt the security measures to speed up the process, which is a significant concern. Cloud storage providers must balance these two needs.
Understanding Box Compliance Standards
When using a cloud storage service, organizations need to be certain that the service meets any compliance standards the organization must follow for its sensitive data.
For example, organizations working in the healthcare industry may need to provide compliance with the HIPAA (or Health Insurance Portability and Accountability Act) standard.
PII (or personally identifiable information) and PHI (or protected health information) fall under HIPAA. An organization that is storing this patient data must comply with HIPAA standards wherever the storage occurs, including in the cloud.
This means Box must be able to assure customers who have these compliance standards requirements that Box follows the rules. If an organization is storing data in a way that violates the industry compliance standards, it could be subject to significant fines and penalties.
How Box Security and Compliance Works
To aid in the implementation of security measures and processes that comply with industry standards, Box uses a number of features, including the following.
- Encryption: Box makes use of strong security measures, including AES 256-bit encryption to protect data in storage.
- Machine Learning: Box deploys AI and machine learning techniques in its system that constantly monitor for threats to data security. The system studies any attempted attacks, learning how to better protect the data from similar attempts going forward.
- Organization-Wide Controls: Administrators can use Box to create security settings that affect the entire organization at once. Use this to avoid having certain teams set up their own security measures that may or may not comply with the industry standards that the entire organization needs to follow.
- Audit Logs: Through detailed audit logs, organizations can track the way users are accessing sensitive data. This may provide the first clue to some sort of potential data breach.
Box Pricing
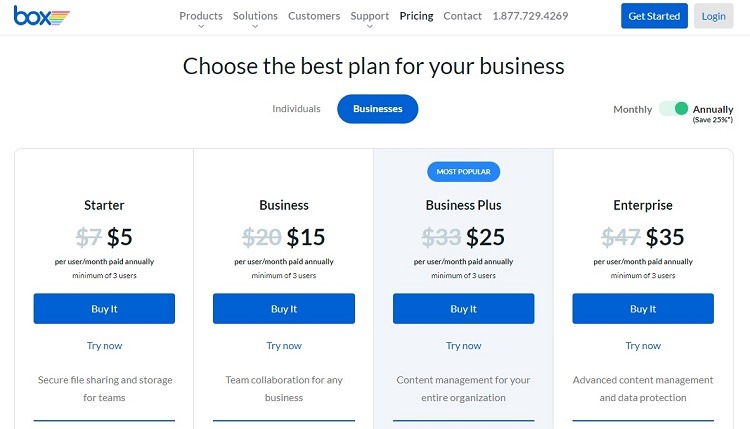
Box provides four different pricing options for organizations. Users can try any of the tiers for a 14-day free trial period before purchasing a subscription. Here are some of the security and compliance features found in each pricing tier.
- Starter: The Starter tier supports encryption for data at rest and in transit, as well as for two-factor authentication (or 2FA) for sign-ins. The cost for this tier starts at $5 per user per month.
- Business: In addition to offering the security features found in the Starter tier, the Business tier offers advanced security controls for mobile users. This tier starts with a cost of $15 per user per month.
- Business Plan: The Business Plan tier includes the security features found in the Business tier, as well as the inclusion of the Box KeySafe feature. This tier offers built-in support for the PCI DSS compliance standard as well. Its price starts at $25 per user per month.
- Enterprise: With this highest pricing tier, customers receive all security and compliance features found in the Business Plan tier. They add built-in HIPAA and FedRAMP compliance with the Enterprise tier. For those organizations that need to provide access to Box for external customers, this tier allows administrators to force the external users to use 2FA. The Enterprise tier starts at $35 per user per month.
All of these tiers require at least three users on the account. The Starter tier has a limit of 10 users, while the other tiers don’t have maximum user limits.
As part of the Enterprise tier, Box offers additional features for a custom price. Many of these features help an organization ramp up its security and compliance performance. Some of these extra features include the following.
Example 1: Box Trust Integrations
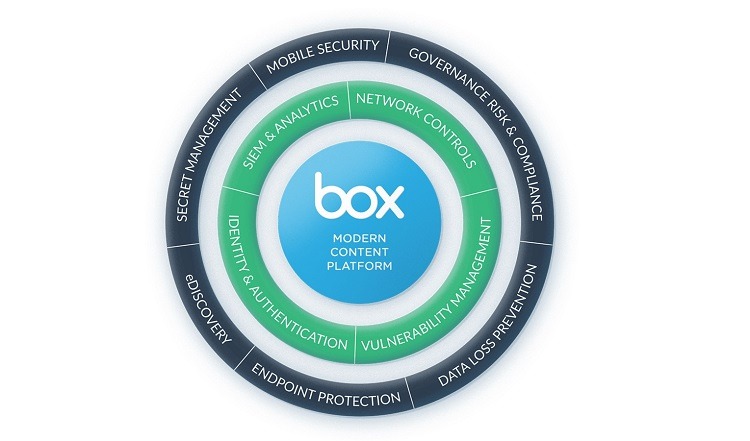
When using Box integrations, customers can gain extra features that allow them to mesh Box with the other apps and software they’re already using. This gives users the ability to use Box as efficiently as possible.
However, when the Box customer is choosing Box because of its strict security and compliance standards, it’s important that any integrations follow the same standards as Box.
Box uses what it calls the Box Trust ecosystem to deliver these integrations with the desired level of security. Box partners with these companies to ensure that they all follow the required standards. Box has two levels of partners, including:
- Universal Control Partners: These partners build extra security controls into their integrations with Box. Things like vulnerability management and network controls are part of the integration automatically.
- Discrete Control Partners: These partners will give organizations the ability to specify the extra security settings they want to deploy as part of the integration. These may include data loss prevention measures and mobile security.
Example 2: Box Shield
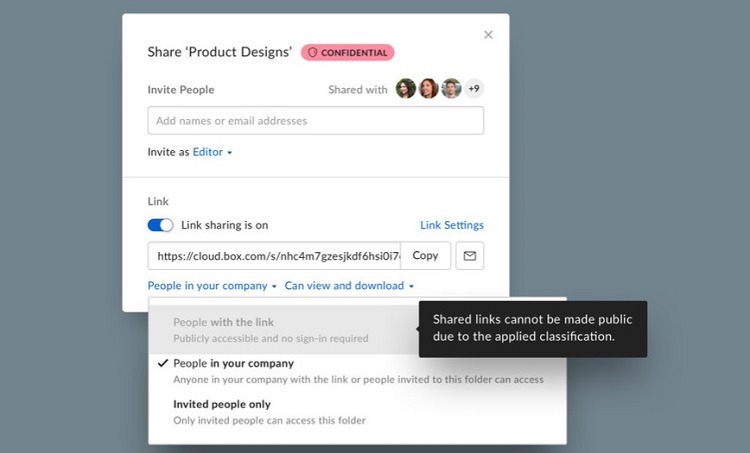
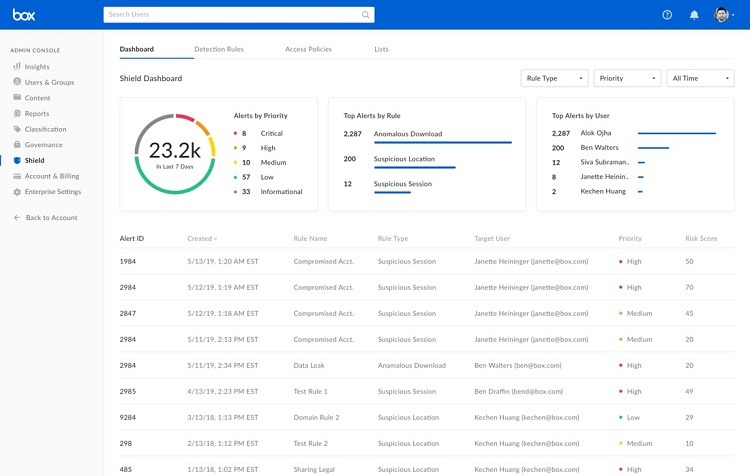
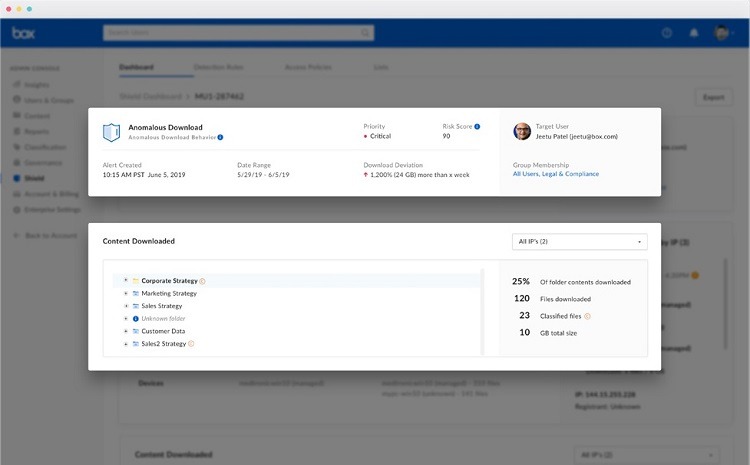
Box Shield gives organizations the ability to set up automated rules for sorting and classifying data into certain silos. Administrators then can enable certain security policies for the silo. All data and files in the silo receive the same policies.
This greatly simplifies the process of protecting certain types of data.
Box even automates the process of sorting the data into silos, using machine learning and AI features. The Box Shield system uses AI to seek out files containing PII and PHI for healthcare organizations, for example, ensuring the data ends up in the proper silo.
Protecting Data in Real Time
As another aspect of Box Shield, the system monitors how users are attempting to use the data and files.
Sometimes, an end-user may attempt to share or copy a file in a way that would violate the silo in which it resides. Box Shield then will provide a notice to the end-user and prevent the selected usage of the file.
Even if the user normally would have permission to share files in a certain way, Box Shield can override this permission, based on the silo for the data.
Protecting Against Attacks
For an organization that wants protection against the possibility of insider attacks, Box Shield offers this feature. The machine learning aspect of Box Shield monitors the system for threats from internal users, as well as for any compromises to an account.
As Box Shield provides alerts about potential attacks, security personnel can review the alerts from within the Box software.
If an alert requires additional actions from security personnel, they can evaluate the alerts through their preferred security software interface. Box Shield integrates with many different security tools.
Example 3: Box Governance
For organizations that must maintain compliance with industry regulations, the Box Governance platform helps with management in a few different ways.
Disposing of Documents
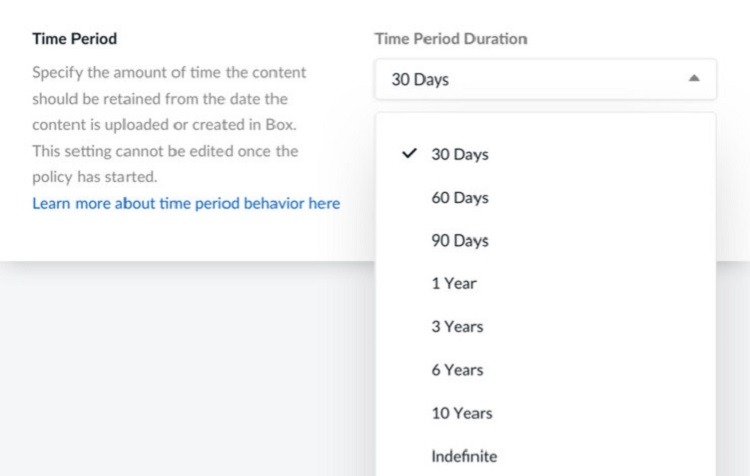
To meet certain industry standards, organizations may need to follow specific schedules for how long they can hold data and files. Some financially sensitive files or files that contain data about customer engagements may need to follow automated disposal schedules, for example.
Through Box Governance, administrators can set policies for the retention of the files. Users can set a time period between 30 days and 10 years from the date of creation for automatic deletion.
Preventing Inadvertent Deletion
It’s also possible that an organization may need to retain the files for an indefinite period, ensuring they don’t suffer an accidental deletion. Administrators can set this feature through Box Governance too.
As another security measure regarding file deletion, administrators can ensure that team members with certain privileges are the only team members who can perform deletions. This prevents someone in the organization from accidentally deleting an important file.
Administrators also can set up Box to allow users to immediately reverse a file deletion command. However, use this feature carefully. For certain compliance standards, deleted files must go through a permanent deletion process. Allowing restoring of deleted files may violate these standards.
Example 4: Box Zones
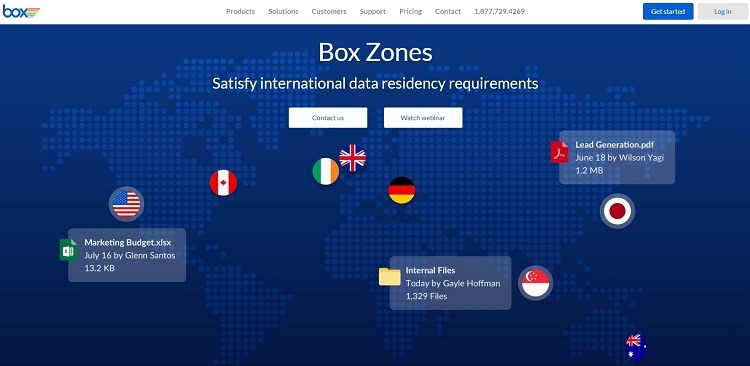
For organizations that must follow data residency requirements, the Box Zones feature will help with meeting these standards.
When working in certain countries, companies may need to follow local standards regarding the data storage location. Box maintains the ability to use physical data server locations in many different countries. This gives organizations the ability to select the location for storage of certain types of data.
Box accomplishes this by partnering with other cloud storage service providers around the world. These partners adhere to the same security standards that Box uses, ensuring a seamless process.
Using Box Zones
Administrators are able to create a default storage zone to use with Box. They also can add secondary zones they may need to meet certain national data storage standards.
Box Zones gives companies the ability to adhere to standards like GDPR (or General Data Protection Regulation). GDPR works to ensure data protection rules for those living in the EU.
They then can assign certain users to access their data from certain zones. This ensures they’re accessing data from the required location. Users who have no particular zone assignment automatically become part of the default storage zone. Administrators can adjust the zone assignments at any time.
Helping End Users
When using Box Zones, end-users should notice minimal or no data lags or other problems. Box closely monitors this process to ensure a seamless experience for users, minimizing frustrations.
For end-users who don’t have particular zone designations, the Box Zones feature works to ensure they are accessing data from servers as close to them as possible. This speeds up data downloads and uploads, providing a better experience.
End users will not need to see the location from which they are receiving data, and Box Zones can hide this information. However, administrators will always be able to see this information.
How to Get Started With Box Security and Compliance
Administrators have multiple options for configuring the security and compliance settings in Box. Here are some options for administrators to consider.
Step 1: Adjusting Security Settings
To begin using Box’s security settings, the administrator will need to click the Admin Console link, followed by the Enterprise Settings link. Then click the Security tab near the top of the page.
Through this section, administrators can create rules for the following items.
- Signup and Login: Administrators can receive notifications when a new user requests an account or when a particular user name has a certain number of failed login attempts. This could be a sign of a cybercriminal trying to access the network.
- 2-Step Login Verification: Using this setting forces all users on the organization’s Box account to use 2FA to access the account. This prevents threat actors from gaining access to Box by simply stealing a current user’s login information. The cybercriminal would need access to the current user’s smartphone too.
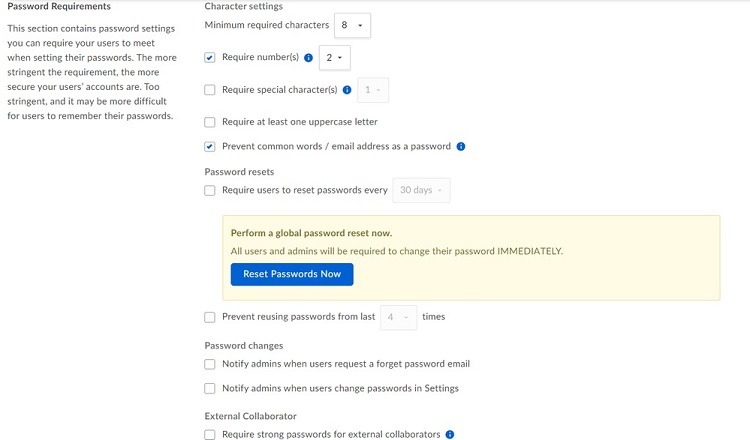
- Password Requirements: Administrators can use this section to force passwords to be a certain length or to use certain characters. They also can track when users choose to change their passwords.
- Session Duration: Use this setting to determine the length of time a user can go without needing to log in to Box again. The software’s default is two weeks before automatically logging users out of the software. Depending on their security needs, administrators may want to reduce this time to 24 hours or less.
Step 2: Determining Data Encryption Settings
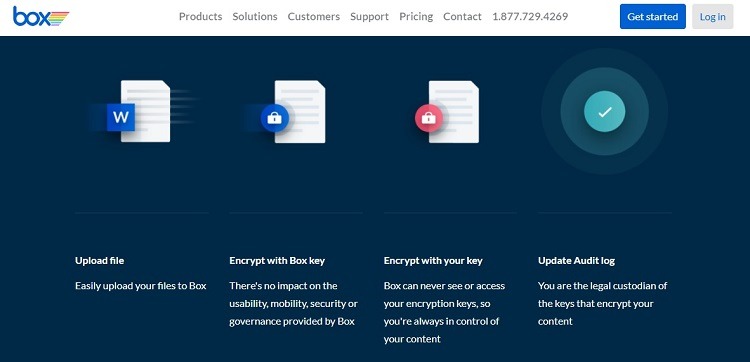
Box automatically uploads data with one of the strongest encryption protocols available in TLS 1.2 (or Transport Layer Security). This protocol works especially well for protecting data going across a network.
When storing customer data in the cloud, Box makes use of 256-bit AES (or Advanced Encryption Standard) for the data. Box also uses a key-wrapping encryption technique that further protects the data using another 256-bit AES encryption key.
Box does support other encryption protocols, including RC4 (or Rivest Cipher 4), for those users who need it. This is an older encryption technology that some organizations need to support. Administrators can choose to use these other protocols as needed.
As another layer of security, Box offers KeySafe, which gives the organization full control over its own encryption keys for data stored in the cloud. Box personnel never see or gain access to the organization’s keys with KeySafe. This local control is important for some organizations that want to take advantage of cloud storage.
KeySafe is easy to use. It doesn’t add a layer of complexity to the process that will frustrate end users.
Step 3: Managing Compliance Standards Settings

Box provides multiple ways to manage the software’s data settings to enable compliance with various industry standards.
For those customers that need to follow HIPAA standards, for example, Box will meet these requirements through its software. Box also supports the ability for organizations to sign BAAs (or Business Associate Agreements) with Box that ensure compliance with standards.
Some of the industry compliance standards that Box supports include:
- FedRAMP
- FINRA
- FIPS 140-2
- HIPAA
- HITECH
- ISO 27001
- ISO 27018
- PCI DSS Level 1
- SEC 17 a-4
- SOC 1, 2, and 3
- SSAE 16 Type II
Box’s compliance with these standards starts by encrypting all data in transit and at rest, limiting physical access to the Box servers, and giving organizations the ability to monitor usage of their systems. Box then adds the ability to handle other aspects of industry standards for its customers that need them.
Box allows for setting up data governance standards that will meet the requirements of nearly any industry, including education, financial services, government, healthcare, and non-profit.

