Best Threat Intelligence Platforms of 2022
Threat reactions are no longer an option given today’s porous threat landscape. Instead, organizations need to take a proactive approach to identify and mitigate persistent cyber threats before they occur. To this end, threat intelligence involves collecting, organizing, and managing threat data to understand the Indicators of compromise (IOC) and tactics, techniques, and procedures (TTP) of threat actors.
However, this process can be cumbersome and frustrating without help from automation. Threat intelligence platforms allow security teams to identify and block attacks before they occur. Security Operations Center (SOC) now has real-time and contextual threat data at their fingertips thanks to the automation of the threat intelligence lifecycle that these platforms offer.
This guide outlines the best threat intelligence platforms of 2022, as well as a step-by-step guide to help you pick the right platform for your organization.
Anomali ThreatStream
Anomali ThreatStream is designed to help security analysts gain clear insights into the most serious threats facing their organization. The platform uses a combination of threat information, threat data, machine learning, and partners to automatically detect, prioritize, and analyze threats. Your analysts can investigate and respond to security incidents quickly and accurately using evidence-based insights.
ThreatStream does a great job of bringing all of the crucial information in one place. The portal dashboard features a widget-based view of critical data, including feeds, intelligence sources, alerts, latest activities, and pending tasks. The platform also offers quick access to global threat intelligence with its MyEvents map feature. Here, you’ll get an overview of the most recent threat intelligence, down to the country of origin and detailed Indicators of Compromise (IoC) picked up by other security tools.
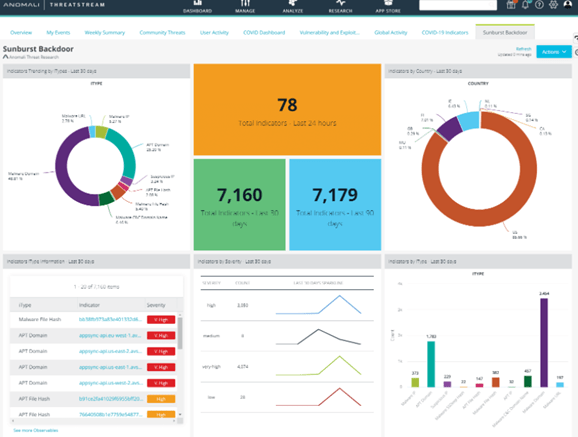
The platform gathers threat data from a wide range of sources, including the Anomali Labs curated feeds, specialized premium feeds, open-source OSINT feeds, ISAC/ISAO shared threat intelligence, and other intelligence and machine-readable IOCs. The tool takes measures to provide actionable data, including removing inaccurate, out-of-date, and duplicate information. It also automatically prioritizes information based on your organization’s needs.
Other noteworthy features and capabilities include:
- Contextualized information – Threat data includes relevant tactics, techniques, and procedures (TTP), actors, and campaigns.
- Threat intelligence scoring – ThreatStream uses a robust machine-learning algorithm to aggregate threat data based on severity.
- Integrated sandbox detonation – Where you can upload suspicious files for investigation and detonation using MRTI.
- Turnkey integrations – The platform easily integrates third-party with firewalls, SOARs, SIEMs, and EDRs.
- Collaboration – Connect with other ThreatStream Trusted Circles users spread across more than 2000 organizations.
The only major complaint about the platform is it is resource-intensive. It takes up a lot of storage space and system resources, which can be a problem for some users.
Anomali ThreatStream offers flexible deployment options depending on your security requirements. For example, you can host the platform on-premise, the native cloud option, or airgap. Anomali ThreatStream features custom pricing, so you’ll need to contact the company to get a quote.
CrowdStrike Falcon X
CrowdStrike takes a holistic approach to cybersecurity by combining threat intelligence and endpoint protection. The platform uses lightweight agents to continually monitor endpoints such as desktops, servers, and IoT devices for threats. The cloud-native platform automatically analyzes malware found on endpoints and compares it to other known malware in an expansive malware search engine. The result is detailed and customized threat intelligence and indicators of compromise (IOCs).
Falcon X is naturally conservative on your computing power. Aside from the lightweight agents installed on endpoints, most of the computing and processing takes place on CrowdStrike’s servers. So, you get world-class endpoint protection and threat intelligence at a fraction of the resources required to operate an on-premise solution.
The platform also automatically conducts investigations. Then, security teams receive customized and actionable reports to make accurate and timely decisions. These reports cover each incident’s details, down to the who, why, and how.
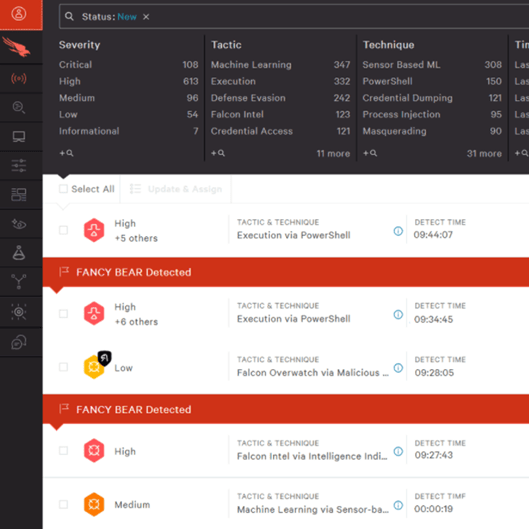
The Falcon X premium plan offers even more robust threat intelligence capabilities, including social media intelligence. Here, the tool scours the internet to monitor your company name and brand. So, you’ll instantly know if there is any stolen company data like passwords or personally identifiable information (PII) for sale on the dark web or other places. This plan even comes with daily actionable reports to help your SOC team accurately prioritize incidents.
Falcon X Elite takes threat intelligence to the next level by giving you access to the industry’s top threat intelligence experts. CrowdStrike’s intelligence teams track hacktivists and cybercrime groups in more than 121 countries. You’ll be assigned a dedicated Intel analyst who’ll take over all your threat intelligence tasks. This is an excellent choice if you are looking for a managed service.
The main downside of CrowdStrike Falcon X is its log management. This feature can be overwhelming for some users. But, the service offers excellent support in case you find the feature too complex or confusing. There’s also detailed documentation to help clear up any confusion.
CrowdStrike Falcon X prices start at $25 per endpoint per year.
IBM X-Force Exchange
IBM X-Force Exchange gives you access to more than 900 terabytes of threat intelligence generated by humans and machines. It seamlessly integrates with your existing security systems such as firewalls, security information and event management (SIEMs), and intrusion prevention systems. Then, the platform feeds your security systems with actionable threat data.
The platform’s intelligence reporting is arguably its most robust feature. Here, you can generate detailed reports, including threat actor groups, industry assessments, malware, and threat activity. These reports are handy for executive management and can help paint an accurate picture of the threats to the organization and possible remediation measures. IBM X-Force advanced reporting is also at the heart of formulating a security roadmap.
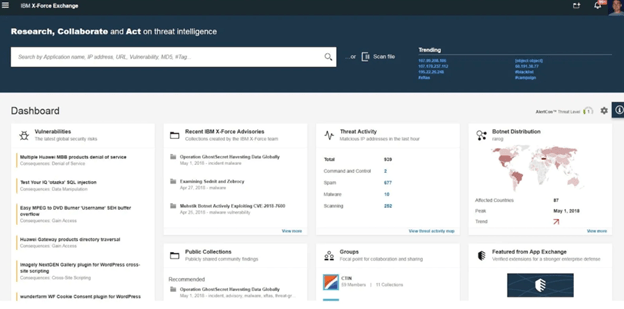
You also get four kinds of reports, including Threat Group Profiles, Malware, Industry Analysis, and Threat Activity.
IBM X-Force Exchange also sports a customizable dashboard. You can organize threat data based on your needs by prioritizing vulnerabilities or advisories. The dashboard also offers quick insights into your security posture, including the risk level of each potential threat. In addition, the Timeline view lets you track changes in the risk level over time.
Other noteworthy features include:
- Early warning feed, which provides a current list of malicious domains. You can integrate the feed to your security tools to automatically block these domains as they are discovered.
- RESTful API to help you easily integrate with your existing security solutions.
On the downside, IBM X-Force can be complex to use. The platform offers many useful features and advanced reports, but it has a steep learning curve. Otherwise, this is the platform of choice for organizations primarily interested in advanced, accurate, contextual, and actionable reporting.
IBM X-Force offers customized pricing, so you’ll need to schedule a call to get your price based on the platform edition you choose.
Insights Threat Intelligence Platform
The Insights Threat Intelligence Platform (TIP) lets you automate the entire threat intelligence lifecycle, including data collection, analysis, and enrichment. The platform also offers strong collaboration and dissemination capabilities to make it easier for security teams to investigate and pre-empt threats.
The platform organizes massive intelligence data on a single dashboard. It gathers intelligence data from various sources, including industry threat feeds and public and private threat feeds. It also comes with built-in credibility scoring to help reduce noise and false positives.
The threat intelligence platform also offers integrations with your existing enterprise security tools. These include firewalls, SOARs, EDRs, and SIEMs. You also get insights into deep-web activities, so you can pre-empt future attacks before they happen.
This is an excellent platform for organizations that prefer on-premise solutions. It offers easy deployment in as little as 24 hours and a plug-and-play functionality with your existing security devices.
On the downside, Insights Threat Intelligence Platform reporting isn’t as deep and robust as some of the alternatives featured here. Still, it is an excellent platform for organizations more focused on external threats. In addition, you’ll be able to conduct deep investigations into the clear and dark web to gain credible information about the newest threat actors.
You can request a demo and get a quote for services through the Insights TIP website.
Mimecast Threat Intelligence
Mimecast Threat Intelligence is a terrific platform for organizations whose email systems are consistently targeted by phishing, spam, malware, social engineering, and similar threats. Mimecast’s dashboard provides detailed threat information, including indicators of exploitation and end-users who pose an imminent cyber risk. It also provides detailed information about malware, such as its origin.
The platform secures your email system at three points. The first point is your email perimeter, the second is inside your organization and network, and the third is beyond your perimeter.
Mimecast also offers a robust threat feed. Here, you can view detailed malware information and actionable advice on how you can minimize future attacks. Mimecast also easily integrates with other security solutions such as EDRs, SOARs, and SIEMs.
The platform offers automated threat remediation capability. This feature automatically remediates attachment malware, including zero-day malware found in the organization’s mailboxes. The platform also alerts admins when it detects malicious attachments in your email environment.
Other noteworthy Mimecast features include:
- Mimecast Secure email gateway featuring advanced features like DNS authentication.
- Mimecast URL protects, which uses multi-step detection to monitor and block malicious URLs. It scans inbound emails in real-time.
- Mimecast Impersonation Protect helps to identify and isolate suspicious email tags.
This option is undoubtedly one of the best threat intelligence platforms focusing on email security. However, it is not a comprehensive platform, meaning that you might need additional security tools to cover your entire attack surface.
Mimecast features custom pricing, so you’ll need to contact sales to determine how much it will cost you.
How to Pick Your Threat Intelligence Software
Every company has a unique security posture. As such, the best threat intelligence software will adequately solve the organization’s peculiar security needs. Here’s how to go about choosing the best threat management platform for your organization:
Step 1 – Determine Why You Need a Threat Intelligence Platform
It is difficult to overstate the importance of integrating threat intelligence into your system security. But, you’ll need to be specific about what you need the platform to do. This step will make comparing different providers much more straightforward.
Be sure to involve stakeholders such as your security or IT analyst, security operation center (SOC) personnel, computer security incident response team (CSIRT), and executive management in your discussions. As a result, you’ll be more likely to procure a tool that satisfies the needs of the entire security team.
Some of the reasons you might need a threat intelligence platform include:
Incident analysis – This helps gather information about the who, what, why, when, and how of attacks. Successful incident analysis requires a vast knowledge base that includes threat indicators, targets, threat actors, and attack techniques and histories. A platform like Anomali ThreatStream is ideal in this case.
Incident validation and prioritization – This feature helps identify the most significant risks to your organization. This use case also lets you prioritize which risks to mitigate. A platform featuring threat indicators linked to threat data is ideal in this situation. Again, great options are Anomali ThreatStream, Insights Threat Intelligence Platform, and CrowdStrike Falcon X.
Hunt missions – This use case requires a tool that provides context for threat indicators. This context includes threat actors, campaigns, and targets. Hunt missions also help to find previously undiscovered attacks. IBM X–Force Exchange is a prime candidate for hunt missions given its in-depth reporting.
Containment and remediation – Involves eliminating vulnerabilities and identifying and removing malware. A tool like Mimecast Threat Intelligence is perfect for the job, especially email security. However, given its robust endpoint monitoring and protection capabilities, CrowdStrike Falcon X is an even better option for overall containment and remediation.
Proactive threat blocking – Helps detect vulnerabilities and prevent attacks before they happen. A tool with sophisticated end-point protection like CrowdStrike is perfect in this scenario.
Intelligence reporting and distribution – Requires producing and disseminating threat intelligence reports. As such, the platform should have built-in workflows that allow users to create, collaborate, and share comprehensive intelligence data via PDF reports.
External threat landscape modeling – Attempts to discover details of attacks and how an organization may be vulnerable to these attacks. To do this, the platform should be capable of profiling attacks. Most platforms featured here offer some form of external threat landscape modeling. For example, Insights Threat Intelligence Platform focuses on external threats.
Now you’ll have a clearer picture of which platform fits the bill based on your organization’s specific needs.
Step 2 – Compile a List of Your Must-Have Features
The previous step will inform your must-have features based on what you need the threat intelligence platform to do. Again, consult with your security team about critical features that make their work easier, more accurate, and faster. Some of the essential features to think about include:
- Deep and dark web monitoring
- AI-powered investigations
- Simple and advanced reporting
- Real-time information and alerts
- Statistics and visualization
- Automation at scale
- Integrated workflows
- Customizable threat monitoring
- Operational intelligence
- Threat research
- Feedback
- Severity and level of confidence guidelines
There’s always the temptation to prefer a platform with all the bells and whistles. But, you may end up paying for underutilized features or features that won’t be used at all. Also, such a platform can take a toll on your network resources. But, you’ll be able to narrow your choices even further once you’ve identified the critical features you need from your platform.
Step 3 – Consider Integration with Existing Security Tools
Threat intelligence isn’t the end-all of your security troubles. You’ll still need to retain and maintain many of your existing tools, including Intrusion Prevention Systems (IPS), firewalls, Data Loss Prevention (DLP), and sandboxing. So, make a list of all the network security tools you already use, including legacy systems.
There are two ways to choose the best threat intelligence platform for your existing network security infrastructure. The first important consideration is integration. You want a platform that seamlessly integrates with your current systems. Therefore, find out whether the platform you are eyeing easily integrates into your security infrastructure.
The next consideration is whether your chosen platform comes with features to make existing tools obsolete. Maintaining disparate software is expensive and resource-intensive. Ideally, you want a platform that unifies some of the software you already use.
For example, Mimecast Threat Intelligence comes with built-in email security, meaning you don’t have to keep your old email security tool. Similarly, some platforms also come with a sandboxing feature, so you don’t need to maintain separate software for that.
Step 4 – Sign Up for a Free Trial
Most threat intelligence platforms give you the option of trying the software for free for a limited time. First, take advantage of the free trials and product demonstrations to get a first-hand feel of the software. Then, pick the two or three most promising options and sign up to try the software. Again, be sure to include your team and end-users in this process.
Use the list of the must-have features you created in the second step to zero in on what to test. Also, create criteria for testing these platforms, including ease of use, deployment, and general functionality. Then, take your time to try out the different features and compare the platforms to decide which one best suits your needs.
Also, utilize vendor resources like documentation, training, and support. Threat intelligence platforms have a considerable learning curve, especially if you use one for the first time. Finally, compare notes and pick the best threat intelligence platform for your organization based on your collective experience.

