Best Static Application Security Testing (SAST) Tools
Software development offers a clear path for organizations looking to innovate, stay ahead of the competition, and disrupt markets. However, most applications aren’t built for security, a flaw that cybercriminals are more than willing to exploit. Static application testing offers the opportunity to build security into software and applications right off the bat.
In particular, static application security testing (SAST) tools scan your source code for vulnerabilities. Now development teams can improve security without reducing their development timelines. We’ve created this guide to help you identify the best SAST tools on the market and offer step-by-step advice to help you choose the right tool for your business needs.
Checkmarx CxSAST
Checkmarx CxSAST is an enterprise-grade static analysis tool supporting more than 25 coding languages and frameworks. You can use the tool right out of the box without customization for your preferred language.
The tool also offers many developer-centric features, including integrating with CI servers to automate security testing. You can also integrate it with your source repositories, bug tracking solutions, project management software, version control system, or build servers to accommodate your development environment and workflow.
Many SAST tools rely on lengthy complete scans. Checkmarx CxSAST uses incremental scanning, reducing the scanning time. In addition, the tool analyzes new or changed code, reducing the scanning time further. The platform also offers multiple deployment options.
Checkmarx CxSAST is also very user-friendly. Development teams can easily see the proof and reasoning behind identified vulnerabilities. There’s also room to customize the rules, so you aren’t stuck with the same old intellectual research that everyone else uses.
The tool even suggests the best place to fix code issues with its “Best Fix Location” feature. You can also get scan results as a static report for a quick overview or use the interactive interface for in-depth reporting. Finally, you have the option to manually activate scans, schedule the scans, or automatically initiate the scan for new builds.
Other noteworthy features include:
- Fewer fire drills and false positives
- Intuitive UI
- Customizable queries
- Automate code repository
CxSAST isn’t perfect. Installation and configuration on some platforms, such as the Linux PostgreSQL client, can be challenging. Checkmarx does offer extensive documentation and free installation, though, in case you run into any problems during deployment. Finally, a significant number of CxSAST users complain about too many false positives.
Checkmarx doesn’t provide public pricing for CxSAST, but it does offer a 14-day free trial.
Veracode Static Analysis
 Veracode Static Analysis promises to secure applications without interfering with development timelines. The platform offers three testing methods for different parts of your software development lifecycle, namely:
Veracode Static Analysis promises to secure applications without interfering with development timelines. The platform offers three testing methods for different parts of your software development lifecycle, namely:
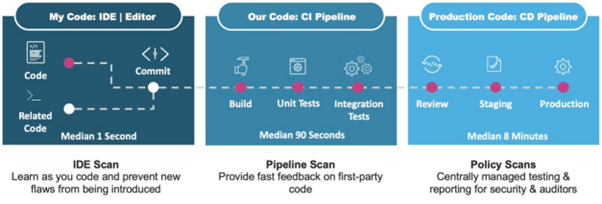
- IDE Scan – This testing method is designed for the pre-commit stage. It offers real-time feedback as the developers work on the code. The scan eliminates the possibility of committing vulnerable code into the central repository in the first place. This robust feature even offers code examples, links to tutorials, and remediation guidance to correct and educate developers.
- Pipeline Scan – This scan integrates into the CI pipeline and is invaluable to DevOps engineers. The capability enables engineers to identify vulnerable code immediately it is introduced into the development pipeline.
- Policy Scan – This scan is perfect for assuring external compliance auditors and stakeholders that the application is safe. The test scans the entire application against one policy. You also get a comprehensive report detailing the apps’ security posture.
Veracode Static Analysis boasts a 1.1% false-positive rate for teams worried about accuracy. In addition, each flaw is accompanied by detailed information about how it was identified and the potential risk if left unfixed. Finally, the platform also offers in-line remediation advice to help developers resolve the issues.
Furthermore, you can schedule a call with Veracode’s consultants if you face remediation issues. Other noteworthy Veracode Static Analysis features include:
- Automated testing
- Out-of-the-box and custom policies
- Hundreds of analytics metrics
- Supports 25+ languages and 100+ frameworks
- Yearly language releases and updates
- Extensive APIs
- Native integrations with popular developer IDE plugins, ticketing, and bug tracking tools, build systems, web application firewalls (WAF), workflow & orchestration tools, and GRC systems.
On the downside, Veracode’s reporting can be overwhelming. As a result, it may take time to cut through the noise to find the most relevant information. This flaw also extends to numerous email alerts and you can’t choose which alerts you want to receive.
Veracode prices start at around $690 per year.
SonarQube
SonarQube is an open-source static analysis tool perfect for creating a uniform standard for coding within an organization. The tool checks code against global default or customized rules called quality profiles. In addition, SonarQube offers multiple deployment options, including cloud-hosted and on-premise versions.
The platform covers more than 25 programming languages and offers two scanning options. You can run the scan directly on your build or integrate it into your CI pipeline. You can also analyze branches and pull or merge requests to ensure that the code is consistent at every level.
SonarQube’s most essential tools include:
- SonarLint – This tool allows you to analyze code as you work on it. You get immediate feedback about issues right from the code editor.
- Clean as You Code – This allows you to focus on new or changed code.
- Quality Gate – This feature measures the project against predefined conditions.
- Issues – SonarQube sends alerts for multiple code issues such as maintainability, vulnerability, and bugs. The warning also triggers when a developer breaks a coding rule.
- Security Hotspots – The platform highlights pieces of potentially vulnerable code.
Other noteworthy SonarQube features include taint analysis, OWSAP/CWE security reports, go/no-go indicators, docker support, and built-in methodology.
SonarQube offers a free community edition with decent capabilities. For instance, the free version supports 17 coding languages, CI/CD integration, and review security hotspots.

However, you’ll need to upgrade to one paid version to enjoy all SonarQube functionality. The tiers here include Developer starting from $150, Enterprise starting from $20,000, and Data Center starting from $130,000. Each package also offers a free trial.
On the downside, configuring SonarQube can be complicated and time-consuming. The developer community is also smaller and less active than others, including Checkmarx.
Perforce Klocwork
Perforce Klocwork is a robust SAST tool that supports C, C++, C#, Python, JavaScript, and Java. The platform uses differential code analysis fast feedback static analysis to scan large and complex codebases quickly. Klockwork also automates security testing by integrating CI/CD pipelines, machine provisioning, cloud services, and containers.
The tool’s centralized dashboard is highly customizable, allowing you to quickly view codebase analysis data, configurations, metrics, and trends. You can also collaborate with other team members by inviting them to view the latest revisions. Furthermore, participants can comment on the code and stay updated on new edits and comments via RSS feeds.
Klocwork gives you options for when you’d like to perform a code review, such as before or after developers submit the code. You can also set up feeds to stay updated on any code changes. Finally, you can invite team members to view the code and even reject a code review if necessary.
Klocwork also integrates with Secure Code Warrior (SCW). Here, developers have access to extensive resources to help mitigate vulnerabilities.
Other notable Klocwork features include:
- Detailed feedback and help
- No user configuration required
- Easy to use
- Architectural analysis
- Custom rules
You’ll need to contact Klocwork to get pricing information, as they don’t post their prices publicly.
Codacy
Codacy seamlessly integrates with your development environment and supports more than 40 programming languages. Depending on your needs, it is available in software-as-a-service (SaaS) or on-premise deployments. The SaaS version is straightforward to get started, requiring just a few clicks to set up your git repository.
The platform counts some of the biggest brands as its customers, including PayPal, Deliveroo, Cancer Research UK, and Adobe.
You can use Codacy to identify problematic areas of your code, check the code’s overall quality, and discover your project’s technical debt. Additionally, you can use the platform to standardize code across your organization.
This SAST tool also comes with advanced features. For instance, you get 1-click commit suggestions and inline annotations in real-time. It also has deep integrations with Stack and other project management platforms. You can configure Codacy to receive notifications on Slack.
Codacy comes with hundreds of rules built into the platform. This makes it easier to choose the rules that suit your organization’s workflow. There’s also the option of using your own rules to suit your workflow even better. Some of the platform’s notable features include:
- Code review automation
- Engineering analytics
- Code quality analytics
- Cluster installation / multiple instances
- Security code analysis
This SAST tool has a clean and intuitive dashboard. You get widgets that provide the necessary information, including violation statistics and metrics. You can also easily track duplicate code right from the dashboard.
On the downside, Codacy can be complicated to configure and its settings can be overwhelming. Codacy also isn’t as fast as some of the other SAST tools out there despite claiming otherwise.
Codacy pricing starts at $15 per user per month. However, there are also Startup and Open Source options available for free.
How to Pick The Right SAST Tool
Each SAST tool has its strengths and drawbacks. Unfortunately, this can make it difficult to determine the best tool for your organization. But there are a few steps you can take to help point you in the right direction.
Step 1 – Determine Who Develops the Source Code
Code authorship plays a critical role when choosing a SAST tool. This is important since code is assessed differently depending on who wrote it. If your code is developed in-house, this doesn’t need to be a significant deciding factor. However, you may need a combination of Dynamic Application Security Testing (DAST) and SAST tools if you outsource code development to third parties.
SAST tools are comprehensive and work best for in-house development. Third-party code has already been developed. So you will be testing for vulnerability while the application is running. DAST is the only way to achieve this.
You may want to consider a combination DAST/SAST application either way. This is especially true if you expect to integrate third-party development sometime in the future.
Step 2 – Decide the SAST Tool Features You Need
It’s crucial to get app development and AppSec teams to discuss the most valuable features required in a SAST tool. Some of the standard features that come to mind include:
- Secure code integration with SAST
- Fix complex security issues
- Fast and automated scans
- Integrates with the CI/CD pipeline
- Real-time feedback
- Compatible with your development platform and programming languages
Similarly, you’ll need to identify the specific defects you’d like your static analysis tool to find. This step will make it much easier to sort through your options. You can simply discard the tools that don’t have the capability you are looking for. Some of the static analysis defects worth considering include:
- Security vulnerabilities
- Syntax violations
- Unreachable or dead code
- Programming standards violations
- Declared variables that are never used
It is also worth carefully reviewing a few different tools for convenient features. Some features are helpful but not immediately apparent. For instance, you may want a SAST tool to pause a scan in progress and resume from the last point. Other tools may alert you if your testing computer is not connected to a network.
SAST is a day-to-day tool, so you need all the helpful features you can get.
Step 3 – Review Potential SAST Pitfalls
SAST tools are handy in app development projects. However, these tools aren’t an all-in-one solution. Instead, they come with various pitfalls that you need to know about. This way, you’ll be prepared to cover potential vulnerabilities that appear beyond your software’s capabilities.
For instance, static tools are known for producing false positives. Some tools do this more than others. So it is worth looking deeper into this perspective before making a final decision. Customer reviews are great for determining the false-positive rate of the tools in question.
You may also want to shy away from simple open-source bug finders that tend to have a high rate of false positives. Additionally, choose a tool that allows you to create custom context-specific rules to reduce the number of false positives.
Additionally, your static analysis tool is only as good as the rules it uses. So it is worth investigating these rules before purchasing. For example, check if the tool follows coding standards such as MISRA C or CERT C.
Step 4 – Test A Few SAST Tools
You should have narrowed down your options to two or three at this point. Most SAST tools offer a free trial. So request your development team to assess the tools and decide the best option. Some of the things they should be looking for include:
Ease of use – Ideally, the SAST tool should fit your current SDLC cycle. A product that requires you to overhaul or radically change your development process will likely cause more problems than necessary. A promising sign is if the tool easily integrates into your development infrastructure. Ideally, the system also shouldn’t require lengthy employee training to deploy successfully.
Actionable diagnostic output – The ideal tool should provide clear and concise results. The results should be understandable even to the less experienced coders and security experts. At the very least, your tool should identify the specific place in the source code where the defect exists. Additionally, the tool should suggest clear and actionable remediation steps.
These steps will help you select the best SAST tool for your organization.

