The 7 Best Privileged Access Management (PAM) Tools and How to Decide
When you need to make sure that the people in your organization only have access to the network permissions they truly need, privileged access management (PAM) systems are a necessity.
A PAM system will give higher permission levels to the people on your network who need administrator controls or who need to access sensitive files. Using privileged access management tools helps with network security and protects confidential information. You can apply PAM settings to people, applications on the network, and individual machines.
We will help you determine which PAM tools will best fit the needs of your network and situation.
CyberArk
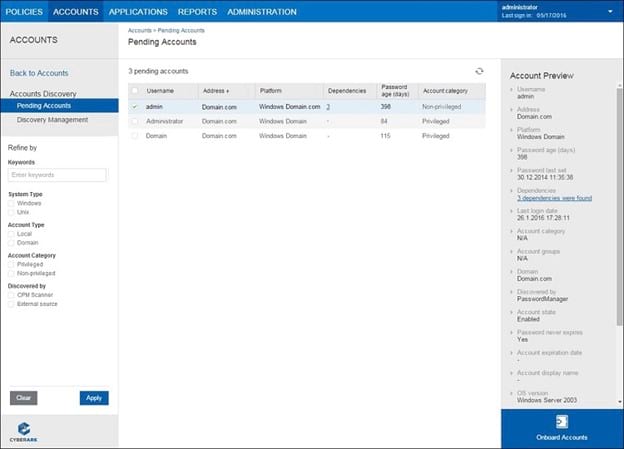
CyberArk is extremely easy to use when you want to be able to monitor exactly what is happening on your network with the network’s most sensitive data.
It is a popular selection among companies seeking PAM tools, in part because of its versatility. It works with any type of operating system, and it will fit the needs of almost any size of enterprise. It also is available as either a SaaS subscription installation or as an on-premises installation.
Known for constant innovation, CyberArk often leads the market with new technologies and solutions. CyberArk Labs drives much of this innovation, ensuring that the CyberArk PAM is on the cutting edge.
CyberArk closely guards passwords and credentials on your network, storing them securely in a vault. Administrators can force a certain strength level in the passwords in use on the network through the PAM software too.
Pros:
- Easy to authenticate users
- Administrators can force minimum password strength requirements
- Simplifies tracking the activity on accounts that can access sensitive data
- Automatically discovers new server installations and begins tracking them
Cons:
- Main page interface is too cluttered for some people’s liking
- Can be tricky to drill down to the precise data you want on a particular report
Pricing:
CyberArk does not provide public pricing for its PAM software but you can request a demo from CyberArk to learn more.
Delinea Secret Server
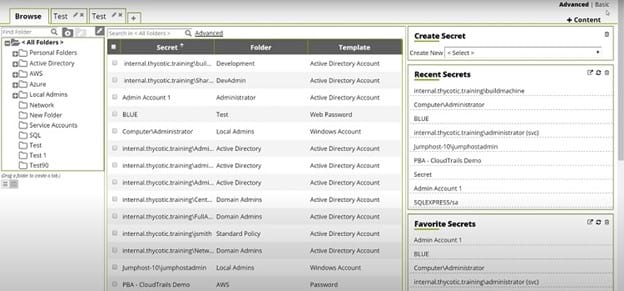
For those who are more familiar with the Thycotic or Centrify brand names in PAM software tools, Delinea Secret Server gives you the best of those tools. Delinea formed in mid-2021 through a merger of Thycotic and Centrify, both of which offered powerful PAM options on their own.
The merged product is excellent as well. Delinea Secret Server makes it easy for you to monitor any accounts with privileged access. Any credentials required for privileged access on the network reside in an encrypted vault, ensuring they receive the highest level of protection.
You’ll appreciate the interface with Delinea’s software, as it greatly simplifies finding the most vital information. For end users, the software makes using the network seamless. You really won’t notice complexities from the software’s security features as you’re using the network.
Pros:
- Well-designed user interface that makes managing your network easier than some other PAM software tools
- Integrates technology from two powerful PAM tools from Thycotic and Centrify
- Can limit the amount of time a user has access to certain privileges
- Offers better than average customer support versus other PAM tools
Cons:
- Some customers report that it has a higher than average price versus other PAM tools
- Doesn’t offer quite as much versatility and flexibility for administrators as some other PAM software
Pricing:
Delinea does not provide public pricing for its PAM software. You can request a pricing quote from Delinea, or you can sign up for a 30-day free trial of the software.
BeyondTrust
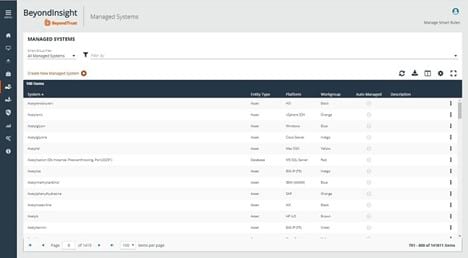
If you are seeking significant versatility and ease of use in a PAM tool, BeyondTrust is a popular selection. You should be able to quickly set up BeyondTrust and begin monitoring access to the network’s most sensitive data. Should you need help, technical support with BeyondTrust is extremely responsive.
BeyondTrust works in whatever way makes sense for your organization. You can deploy it on-premises, in a private cloud, or as a SaaS subscription. It works with all of the major operating systems too.
It typically will work better for larger enterprises than for smaller ones, especially larger groups that have quite a few mobile users. With BeyondTrust, users can gain remote access to the network securely without the need for a VPN. BeyondTrust has a mobile app available as well, simplifying gaining remote access.
Pros:
- One of the easiest PAM tools to learn to use
- Customer and technical support responsiveness is above average
- Allows for instant remote access of a user’s system
- Offers stronger reporting functions than you may expect for such easy-to-use software
Cons:
- It’s nice to have a mobile app, but it can be a little tricky to use
- Recovering from a significant security disaster takes a bit longer than some other PAM options require
Pricing:
BeyondTrust does not provide public pricing for its PAM software. You can contact the sales department to request a pricing quote or to schedule a demonstration.
Arcon

Arcon offers two levels of privileged access management software, allowing your organization to find the right version to meet your needs and budget. Arcon PAM is a full-fledged software package, while Arcon PAM Lite delivers a limited set of features at a lower price point.
Arcon includes a secure password vault that users must access through multi-factor authentication (MFA). This ensures maximum security for your system. The system will force frequent password changes and will require a certain level of strength from passwords as well.
You can set up detailed audit trails within Arcon, so if a security issue occurs, you can track it back to the source. Arcon’s auditing features will work nicely for organizations that need to match specific regulations for compliance.
Pros:
- Arcon is easy to set up and to begin using successfully quickly
- The software’s user interface is very well-designed
- Simplifies tracking any malicious activity on the network
- Can quickly access multiple servers with a single login
Cons:
- Doesn’t quite match the top security features of some of the other best PAM tools
- Automatic logout features are too aggressive, causing automatic logouts after short periods of network usage
Pricing:
- Arcon PAM Lite costs $75 to $125 per user per month, depending on your region of origin, but you must sign up in increments of 10 users. You can contact sales for Arcon PAM Lite for more information.
- Arcon PAM’s pricing is not available publicly. You can request a demo on the main Arcon PAM page.
WALLIX Bastion
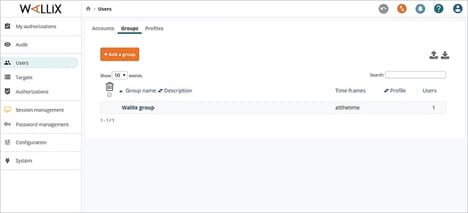
WALLIX Bastion provides a wide range of versatility for your organization versus other PAM tools. However, having multiple choices available does not make the software difficult to use.
You should be able to have WALLIX up and running very quickly. The well-designed graphical interface makes managing your system an easy process too.
WALLIX Bastion has all of the basic features you would expect to find in a top-shelf PAM tool. It also offers a detailed audit trail for the most sensitive network data. You can use this trail to match any regulatory compliance needs you have.
Regardless of the size of your organization, you should be able to deploy WALLIX Bastion successfully. If you have the need for precise management of passwords from the end-users, however, WALLIX’s features rank a little bit behind some of the other options on our list.
Pros:
- Graphical interface is easy to navigate
- Setting up and learning to use the system does not take much time
- Strong features for managing and controlling access to the privileged accounts
- Highly scalable with either the on-premises or cloud-based version
Cons:
- Some customers report below-average technical support and customer support response
- Password management features are a little less robust than some others
Pricing:
WALLIX does not provide public pricing for its Bastion PAM software. You can sign up for a 30-day free trial of WALLIX Bastion.
One Identity
When you need a PAM tool that simplifies the process of tracking the activity on the network of trusted administrators, third-party vendors, and everyone in between, One Identity is a strong choice.
Its tracking tools allow you to see exactly what is going on with the network’s most sensitive data. You can receive warnings about strange activity concerning the network’s most sensitive data based on behavioral analytics. You even can track certain movements in privileged accounts, including keystrokes, in real-time when necessary.
One Identity offers several different PAM software packages, led by the well-rounded Safeguard package. You can select one of the less-robust packages when you need to save a bit of money, but most organizations will select Safeguard.
You can manage the password settings for the network’s users relatively easily, including requiring automatic updating of certain passwords.
Pros:
- Easy to track the activity around privileged access, even when tracking third-party vendors
- You can be up and running quickly with the software
- Includes automatic updates of passwords for service accounts, which simplifies password management
- If desired, add an extra layer of security for the passwords used in the most critical areas of the network
Cons:
- Data reporting features aren’t quite as useful as with some other packages
- User interface design creates some unnecessary confusion and complexity
Pricing:
One Identity does not provide public pricing for its Safeguard PAM tool. You can request a demo or seek a price quote from One Identity.
Iraje
Although the majority of PAM tools in our list may be familiar to you, that may not be the case with Iraje. However, this doesn’t affect the quality of the Iraje PAM, as its feature set and usability factor both compare favorably to more well-known packages.
You can make use of behavioral analytics with Iraje to attempt to spot unusual behavior occurring on the network before you suffer a data breach. You can automate some of the processes inside Iraje for managing access, as well as for forcing password rotation from your privileged users.
Iraje doesn’t offer quite as many third-party integrations as some of the others on our list. If you need third-party integrations, the best options available with Iraje will primarily be for Windows users. Iraje does work with all major operating systems, though.
Pros:
- Delivers a wide range of security features to protect sensitive data
- Creates a secure vault to handle credential and password management
- You should have few problems deploying Iraje or being up and running in very little time
- Includes the ability to require users to deploy MFA
Cons:
- Graphical interface could be easier to use with an upgrade to the design
- Customers report that pricing is a little higher than average for a PAM tool, although some flexibility in pricing tiers is available
Pricing:
- Iraje does not provide public pricing for its PAM tool. You can request a demo from Iraje.
How to Pick Your Best Privileged Access Management (PAM) Tools
Step 1: Consider Your Level of Experience
Start your search by determining whether you need a package that’s easy to use and automated or whether you can deploy something that’s a bit more labor-intensive.
A PAM tool that has a well-designed interface can lead to faster success with the PAM software, for example, versus a tool with a complex interface. Delinea and WALLIX have particularly well-designed interfaces.
Finding automated features in the PAM tool can help by reducing the amount of time required to manage the system. Iraje has strong automated access management tools for managing the network. One Identity delivers useful password management automation features as well.
BeyondTrust has excellent technical support, helping you have a better chance to fix any issues that you encounter in a short amount of time.
If you have a security team available to help with the deployment and operation of your PAM tool, you may not have to worry as much about finding an easy-to-use package.
At the same time, security personnel may balk at having to spend a lot of their time managing PAM software. If the security team is already extremely busy with managing other aspects of the network, limit your search for the right privileged access management tools to easy-to-use packages.
Step 2: Think About Who Needs Access to Privileged Information
Depending on the type of work your organization does, you may only need to award access to sensitive information to a few administrators. Other organizations may need to give a wide range of people access, including third-party vendors and remote employees.
Some PAM tools offer strong mobile apps or allow highly secure mobile access. BeyondTrust offers particularly strong features for allowing mobile users to make a secure connection.
Other PAM tools work especially well when monitoring the activity of third-party vendors on the network. Delinea simplifies the process of monitoring the behavior of any user who is accessing sensitive data. Arcon creates detailed audit trails to help you track down any problems with access to the most important data.
Limit your search for PAM tools to those that give you the ability to manage your sensitive data in the manner that makes the most sense for your organization’s usage needs.
Step 3: Plans for Growth of the Organization
If you expect your organization to grow in the near future, you will want a PAM tool that can expand with you. One of CyberArk’s greatest levels of strength is its ability to work for any size network.
More importantly, though, the tool should automate some aspects of determining who needs access to sensitive data. Without close monitoring of the users on a growing network, it is possible for errors to occur in matching users’ changing job responsibilities to their network access. Without regular updates to the network privileges, users may still have access to sensitive data when they no longer need it.
Some users who gained privileged access years ago may not be using MFA, which would violate your updated security rules for the network that now requires MFA. The best PAM tools will ensure that credential enforcement remains consistent across all users, regardless of how long ago they joined the network.
Some network users may still be using password management criteria that fit under old rules. When the network grows quickly, it can be difficult for you to spot these security issues without automated work on the part of the PAM tool. CyberArk excels here too, ensuring that all password strength rules remain consistent.

