Best Penetration Testing Tools
When you want the ability to spot security threats on your network before a hacker finds them, the best penetration testing tools will give you this capability. Compared to manual testing procedures, these tools deliver efficient automated testing procedures.
Also known as a pen test, this type of tool will give you the ability to evaluate your network’s security safely. The penetration testing tool behaves like a hacker, attacking your network to show you security flaws.
Through our list of the seven best pen test tools, we hope you will discover the right tool for your particular needs.
Metasploit
With its origins as a free open-source tool, Metasploit is almost certainly the most widely used penetration testing tool in the world. These days, though, you also have the option of selecting a paid version of the tool, called Metasploit Pro, from Rapid7.
Metasploit is extremely easy to use, featuring an interface that makes a lot of sense. Security personnel appreciate Metasploit because of its ability to automate many penetration testing tasks that otherwise require manual steps. It is able to save you quite a bit of time with these automated features.
It offers one of the most extensive databases of potential vulnerabilities, allowing it to have success in finding both older and newer vulnerabilities.
Some users call it a collection of the best features of many different pen testing tools. This gives it a high level of versatility. You can deploy Metasploit on a network to search for vulnerabilities, but it also will scan a single server or application.
Pros:
- The developers constantly keep the databases of potential exploits updated
- Metasploit can run tests focused on a single workspace, keeping projects separate
- The interface makes this pen testing tool easy to use
- Intuitive automation features are sure to save you quite a bit of time when running tests
Cons:
- The open-source Framework version’s interface feels dated
- The Windows version of Metasploit doesn’t run as smoothly as the Linux version
Pricing:
- Framework: The Framework version of Metasploit is open-source software that is free to download and use.
- Pro: Pro is the commercial version of Metasploit. Rapid7 does not publicly reveal pricing for the Pro version, but you do have a 14-day free trial option with Pro. You can request a product demo of Pro as well.
Wireshark
An open-source software, Wireshark, delivers a free pen testing tool. Yet, it competes at a high level with the other tools on our list, offering highly versatile features and testing capabilities.
In fact, if Metasploit is the most widely used penetration testing tool, Wireshark almost certainly ranks a close second. Because it’s free, you may decide to try Wireshark first and just never see a need to switch to a paid tool.
Its best feature is its ability to deliver precise details about individual aspects of your network, helping you drill down to find the biggest security flaws.
Wireshark provides real-time analysis of traffic passing through the network, seeking areas where potential security issues may lurk. You have the option of monitoring the testing in real-time as it happens, or you can allow the testing to run on its own and download the report for consideration later.
Pros:
- It provides a strong level of detail regarding the network’s activities, helping you drill down to the exact security flaw
- You can view the testing results in real-time, or you can view them later
- Considering this pen test tool is free to use, it has more features than you may expect to find
- It can focus on the busiest accounts on the network, showing you the areas of greatest risk to data
Cons:
- The mostly text-based interface will not appeal to all users
- For those who need high levels of customer service, this open-source software will lag behind others on our list
Pricing:
Wireshark is free to download and use, as it is open-source software. You can purchase third-party add-ons if desired.
Nmap
Nmap is another open-source penetration testing tool that has an extensive following among security personnel. It will perform well in scanning the entire network, allowing it to map out vulnerabilities. However, its greatest area of focus will be on testing for any vulnerabilities found on open ports on the network.
It is able to work on a wide range of networks. No matter what kind of setup and network software you’re using, chances are high that Nmap will be compatible. It also fits in nicely with other security tools you may be running.
Although it can run on either a large or small network, Nmap is especially useful on large networks. It can run tests on thousands of machines and open ports extremely quickly.
Pros:
- Its strongest features involve testing your network for penetration issues through vulnerable ports
- Nmap is available for free, making it a popular tool for those who want to try a penetration testing tool
- If you dislike the text-based interface, you can operate Nmap inside the Zenmap graphical interface
- Offers a high level of versatility, ensuring it will work on almost any configuration and size of network
Cons:
- It relies fully on community support, so it may not be the best option for novices
- If you need a more rounded set of features, Nmap’s focus on testing the vulnerability of open ports may not fully meet your needs
Pricing:
Nmap is open-source software that’s available as a free download.
John the Ripper
If you are seeking a penetration testing tool that can discover weak passwords on your network, John the Ripper is a great selection. It is free to use and it works nicely alongside other security tools, so it is a popular addition to networks.
The free version of John the Ripper is extremely easy to use. However, it does rely on being able to make use of the command line. This means some people will dislike using it versus a pen test tool with a graphical interface.
It runs extremely fast, so you’ll be able to save a lot of time testing your network security functions related to passwords when using this tool.
It can make use of four different operation modes, so you can match the password cracker tool to the specific security flaw you notice most frequently.
Pros:
- It focuses on helping you perform penetration testing of password usage across the network
- Its primary penetration testing tool is available in the free open source version, so you can save money
- Tends to work extremely fast in finding vulnerable passwords
- Will mesh nicely with other security tools you are running on your network
Cons:
- Because its primary focus is on passwords, it may not deliver the well-rounded features you’re seeking for pen testing
- The interface relies heavily on using the command line, so it may not work well for everyone
Pricing:
- John the Ripper is open-source software that’s available as a free download.
- John the Ripper Pro is available for Linux for between $39.95 and $185.
- John the Ripper Pro is available for the Mac OS for between $39.95 and $185.
Burp Suite
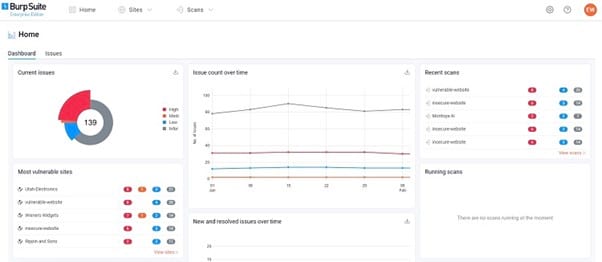
Burp Suite from PortSwigger may have an odd name, but don’t let that fool you. Burp Suite is a highly respected penetration testing tool because of its extensive feature set.
One of its most useful features is its ability to operate both manual and automated scans from within the same interface. Other pen test tools may make you switch back and forth to handle the different types of testing.
Its area of focus resides with testing the security configuration of web applications as traffic moves through them. If you are deploying web applications as part of your network, rather than desktop apps, Burp Suite will be a valuable security tool for you.
Pros:
- With three different versions available, it’s easy to find just the right option for your pen test tool needs
- Offers a passive scan feature, so it’s always testing for network vulnerabilities
- Includes a manual testing feature, so you can set up the exact type of testing you want
- Able to test traffic passing through web applications, discovering any security flaws in the apps themselves
Cons:
- The level of detail in the testing reports needs improvement
- The free version has some significant limitations
Pricing:
- Community: The Community edition is available for a free download, but it lacks many of the automated features for pen testing that Burp Suite’s pay versions have.
- Professional: The Professional edition delivers a mid-range penetration testing tool for $399 per user per year. You also can request a free trial version of Professional.
- Enterprise: The Enterprise edition contains the strongest collection of penetration testing features in these three tiers. It starts at $6,995 per year for five scanning agents, and other pricing levels are available. You can request a free trial version or check out a live demonstration.
Aircrack-ng
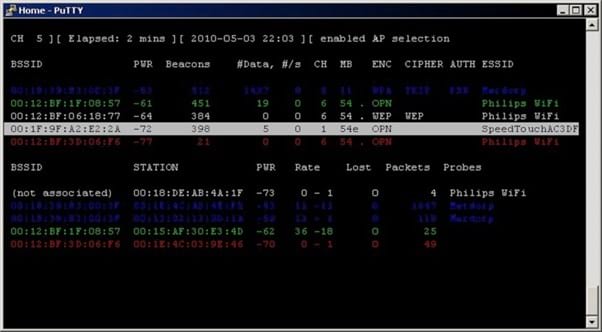
When you want to test your network for flaws in its wireless connections, Aircrack-ng provides a focus in this area. Even though some aspects of Aircrack-ng are a bit older and seem dated, it still has a place among the most respected penetration testing tools.
It helps you spot weaknesses in the network’s wireless communication features by testing the WiFi capabilities. It also can help you measure the strength of passwords used as part of the WiFi connections.
Aircrack-ng can find outdated wireless networking encryption protocols, helping you spot areas of vulnerability to hackers. It can run tests that simulate attacks performed through packet injection as well, giving it a nice set of versatile features.
Pros:
- It has versions available for all of the major operating systems
- It is completely free to use as open-source software
- Its primary focus is on testing for vulnerabilities in WiFi connections and capabilities
- Will find areas of your WiFi setup that are making use of outdated encryption protocols
Cons:
- Novices will encounter some significant challenges learning to use this tool
- It does not offer a graphical interface
Pricing:
Aircrack-ng is open-source software that’s available as a free download.
Kali Linux
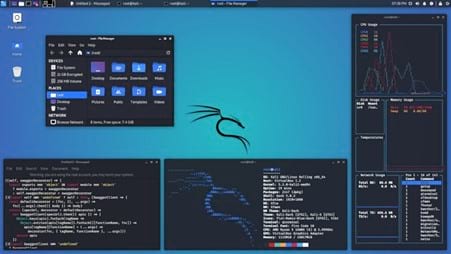
Including Kali Linux on our list of the best penetration testing tools may seem a little odd. After all, Kali Linux is like no other pen test tool on our list.
At its heart, it is an open-source version of the Linux OS that has a primary focus on performing security tasks, including penetration testing. Its pen testing tools can operate in a general manner, or they can focus on a specific testing task, such as password cracking or mimicking an SQL injection attack.
It also is one of the few penetration testing tools that offers support for mobile platforms. Kali simply is a highly versatile penetration testing tool packaged differently than other options.
If you don’t want to run Linux or if you want a more traditional means of performing penetration testing, though, other options on our list will serve your needs better.
Pros:
- It offers hundreds of security tools wrapped into one interface
- As open-source software, it is free to use
- It provides support for mobile devices and a variety of network setups, making it far more versatile than competitors
- If desired, you can completely customize it to deliver the exact testing methods you want to use
Cons:
- Kali Linux has so many different offshoots to it that some people find it confusing to use, especially if they only want penetration testing
- The default security capabilities of Kali are weak, meaning you will need to run security tools over the top of it to protect your data
Pricing:
Kali Linux is free to download and use as open-source penetration testing software.
How to Pick Your Best Penetration Testing Tools
When trying to find the penetration testing tool that will best fit your needs, you should start by thinking about the types of tests on which you want to focus.
Some tools have specific areas of strength, while others offer versatility. You may want to combine your penetration testing tool with other security processes and tests to achieve the highest level of security. We’ll break down some of the specific features you may want in a pen test tool.
Port Scanning and Connection Scanning
When your network has open ports or unsecured WiFi connections, hackers may be able to introduce malicious code to your network.
Open ports alone don’t always represent security issues, as they offer a means of accepting communication. But when not secured properly, they can create a pathway for potential attackers to take advantage of other security flaws that exist in the network.
Nmap has a particular strength in monitoring open ports for any vulnerabilities. When you want to monitor the security flaws that may exist with your WiFi connections and overall WiFi setup, Aircrack-ng is an outstanding choice.
Network Sniffing and Traffic Monitoring
Network sniffing refers to the process of collecting and monitoring traffic that moves across your network. A penetration testing tool often passively monitors the most active applications on the network that are using this traffic.
The tool looks for any exposed credentials moving across the network through the apps. This would indicate a potential security risk. Some pen test tools also monitor for sensitive data moving across the network in an unsafe manner.
Burp Suite is one of the strongest penetration testing tools for testing traffic passing through web applications on your network.
Password Strength Measuring and Cracking
When you secure your data and network apps through passwords, the level of security you have is only as good as the strength of the passwords. Hackers looking to exploit a network may attempt to steal or crack passwords to gain access.
A penetration testing tool that focuses on measuring password strength through running simulated attacks on passwords can discover any weak areas. John the Ripper is one of the strongest password cracking penetration testing tools available.
Overall Network Vulnerability Scanning
Some penetration testing tools don’t have a single primary area of focus. They deliver versatility and the ability to test a wide range of items on the network.
Kali Linux can deliver a wide range of penetration testing tools, but its nonstandard interface may leave some people looking elsewhere.
Our two favorite penetration testing tools that offer the highest level of versatility are Metasploit and Wireshark.

