Best Endpoint Detection and Response (EDR) Tools
Even if you secure your company network’s primary components using traditional security tools, a modern network offers new challenges for security. Endpoint devices, such as laptops, mobile devices, and other remote devices, represent a different type of security threat to the network.
Endpoint detection and response (EDR) tools are the solutions to secure these remote devices. EDR adds another layer of security to the network, guarding endpoint users. These types of tools monitor for threats in real-time. They also track any threats if they penetrate the network through an endpoint, allowing you to stop them.
Our list of the six best EDR tools can help you figure out which solution will best fit the way your network operates.
Sophos Intercept X Endpoint
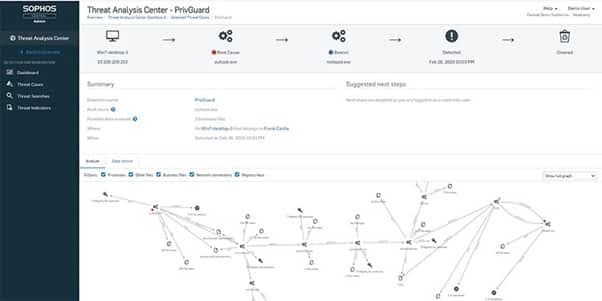
When you have concerns about the use of endpoints exposing your network to potential ransomware attacks, Sophos Intercept X Endpoint provides sophisticated protection in this area. Other EDR tools rarely provide the same level of ransomware protection as Intercept X provides. This tool will block the specific processes involving malicious encryption that ransomware attacks frequently use.
Sophos Intercept X Endpoint makes use of artificial intelligence to analyze behaviors on the endpoints on the network. This gives it the ability to take proactive actions to detect odd behaviors involving endpoints and block them automatically.
The full suite of automated features found with Sophos Intercept X Endpoint makes it easy to use. It also has a well-designed dashboard that simplifies finding the information you want.
With Intercept X, you can combine endpoint security tools with other types of network security tools, including server and email security. This gives you a comprehensive set of solutions, yielding the highest level of protection and defense for the network.
Pros:
- Intercept X provides specific ransomware protection
- Updates are frequently available to ensure that your network receives maximum protection from the latest threats
- Can automate many aspects of protecting your endpoints, including through removal of viruses
- The dashboard is easy to understand and simplifies monitoring the network’s endpoints
Cons:
- Generates a higher level of false positives than some other EDR tools
- Requires more network resources than some others on our list, causing sluggish network performance occasionally
Sophos does not publicly release pricing for Intercept X Endpoint, but you can request a pricing quote, a free trial version, and a free online demo as well.
CrowdStrike Falcon
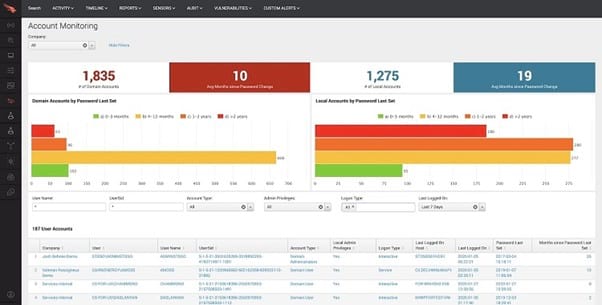
With CrowdStrike Falcon, you’ll receive multiple EDR features in a single tool, providing a high level of protection. Depending on the pricing tier you select, you may receive threat intelligence features, antivirus capabilities, and other features.
With continuous monitoring of all your network’s endpoints, Falcon is able to create real-time analysis in its reporting data. This feature is important for giving the tool the ability to not only detect threats as they are happening, but also to predict which actions may create a greater possibility of attacks. Identifying and studying the behaviors of attackers can deliver fewer false positives as well.
It then gives you significant information about each threat, making it easier to prioritize the most important threats. When it’s time to investigate an incident, this detailed information simplifies the process of determining exactly what happened.
CrowdStrike constantly refreshes its database of threats, ensuring that your network always has the latest information and can respond quickly to any new attacks.
Pros:
- This tool does a good job of remaining up to date to handle the latest attacks
- Uses artificial intelligence to stay on top of threats
- Provides detailed information on each threat
- Simplifies the process of locking down an endpoint as needed
Cons:
- Finding the information you want in the user interface takes some time
- More documentation of administrative control usage options would be helpful
Pricing:
- Pro: $8.99 per endpoint per month (for 5 to 250 endpoints)
- Enterprise: $15.99 per endpoint per month (for 5 to 250 endpoints)
- Elite: Contact CrowdStrike for pricing options
- Complete: Contact CrowdStrike for pricing options
You can request a free on-demand demo from CrowdStrike and try a 15-day free trial as well.
Trend Micro Apex One
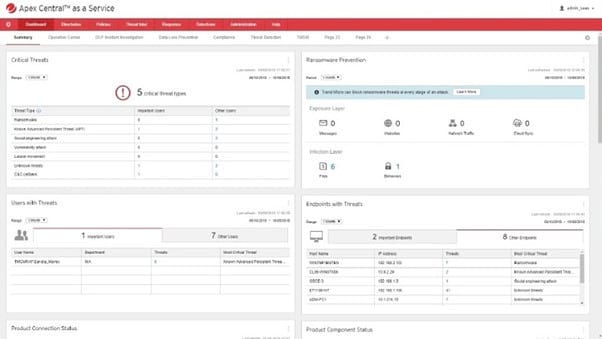
For those who want EDR services along with other protective options, Trend Micro Apex One is a popular selection. This software delivers high levels of security and protection for your network endpoints through multiple layers of security.
Apex One can monitor for malware that arrives at the endpoint. It then can isolate any endpoints that are experiencing attacks, or it can automatically run other responses, depending on the needs of your network.
Trend Micro makes use of predictive machine learning and behavioral analysis to prepare for potential attacks. Apex One uses both indicators of compromise (IoC) and indicators of attack (IoA) to deliver the highest level of prediction success with fewer false positives. This ensures your network is ready for any potential problems.
Trend Micro does a great job of updating its software, giving your network protection against the latest attacks. Its database of known threats is always up to date.
Although Trend Micro does not release pricing data, customers report that its pricing options are reasonable compared to competitors.
Pros:
- Apex One simplifies the management and deployment of endpoint security through automated features
- Able to find and provide alerts for suspicious behavior from endpoints
- Tends to minimize the number of computing resources it requires, so it won’t bog down network performance
- Trend Micro provides seamless updates and upgrades, ensuring the software always has the latest threat information
Cons:
- The interface requires switching between screens to perform common tasks
- Incident reports are less detailed than we’d like to see
Pricing:
Trend Micro does not publicly release pricing information for Apex One. You can request more information on Apex One pricing and also request a free 30-day trial of Apex One.
SentinelOne
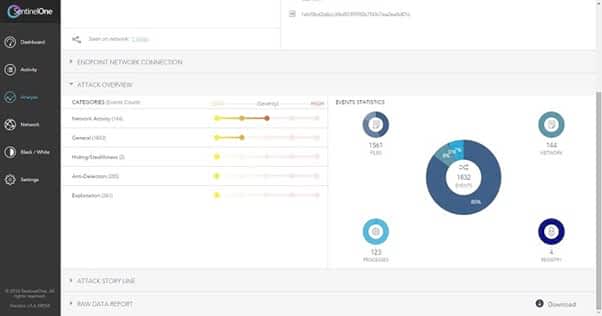
When you want a strong set of automated features in your EDR tool, SentinelOne delivers. Although some users may want more extensive manual control options, SentinelOne’s automated features are so good that you may be able to set it up and leave it running with minimal tweaking required.
SentinelOne relies on artificial intelligence models to find malware and other threats to your network’s endpoints before they have a chance to actually deploy. It is able to use predictive analysis to discover threats as early as possible without generating a significant number of false positives.
In sticking with its easy-to-use theme, the setup of the SentinelOne package is among the easiest in the endpoint detection and response tool market. Small businesses that don’t have a lot of resources available will appreciate its level of automated performance to defend the network’s endpoints against sophisticated attacks.
SentinelOne does a good job of updating the tool’s database of known attacks, ensuring that your network always has the level of protection it needs against zero-day threats and the latest attacks.
Pros:
- Setup is an easy process
- Provides extensive details about endpoint attacks, providing the information you need to deal with them
- Gives you the ability to deal with threats in real-time
- To simplify the management of endpoints, you can create groups to assign one collection of settings to several machines
Cons:
- Some customers will want the ability for more manual controls
- The user interface feels a little bit outdated
Pricing:
- Singularity Core: $6 per agent per month (but it does not offer endpoint control features)
- Singularity Control: $8 per agent per month
- Singularity Complete: $12 per agent per month
SentinelOne does provide a free demo for its EDR solution.
Cynet 360 XDR
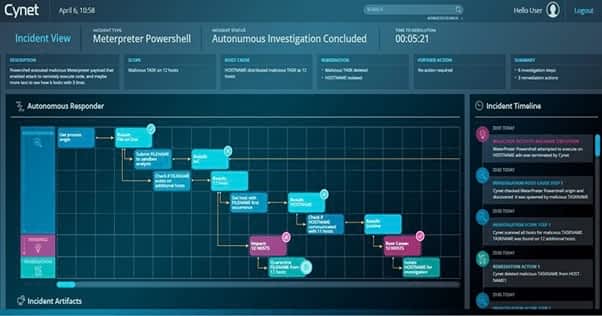
Cynet 360 XDR automates many aspects of monitoring and responding to endpoint threats. This gives those who don’t have significant resources to devote to manual management of endpoints the protection they need. You also won’t need to spend much time with setup and installation with Cynet 360 XDR.
When an attack on an endpoint occurs, Cynet gives you significant information about the attack, simplifying deciphering exactly what happened. It also provides guidance on how to prevent similar attacks in the future.
Another advantage of Cynet is that it can provide additional security options that monitor your entire environment, rather than focusing only on endpoints. This allows Cynet to handle certain types of threats that other EDR tools may miss.
Cynet can monitor and obtain attack data from a wide range of sources on your network, which gives it an extensive amount of information for deciphering attacks before they happen.
Pros:
- Cynet 360 XDR is able to run in the background without occupying a significant amount of network resources
- It does not take much time or effort to set up and begin using the software
- Offers a strong set of automated features that can block attacks without manual intervention
- Includes a dashboard that makes it easy to find the information you’re seeking
Cons:
- Adding individual endpoint devices to the software can be challenging
- Doesn’t excel in detecting and eliminating zero-day threats
Pricing:
Cynet does not publicly release pricing for Cynet 360 XDR, but you can request a free Cynet 360 demo or test it with a 14-day free trial.
VMWare Carbon Black
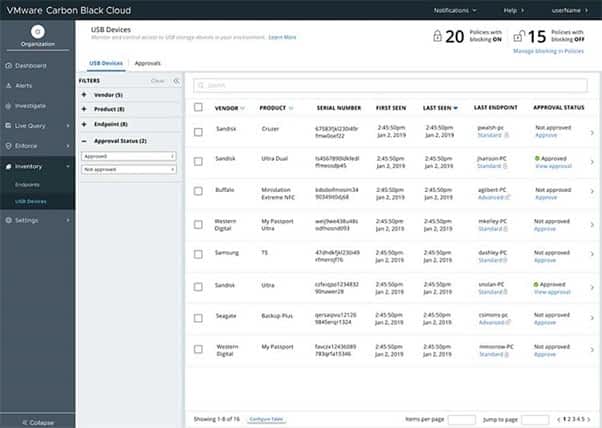
VMWare Carbon Black tends to appeal to teams with networks that require complex solutions in an endpoint detection and response tool. It can handle basic network endpoint defense needs successfully, but its greatest strengths show up when it’s running on networks with complexity.
The well-designed user dashboard for Carbon Black makes the software easier to use than you may expect. The dashboard also simplifies the process of tracking down exactly what happened when an attack occurs on one of the network’s endpoints.
Carbon Black provides real-time monitoring of the endpoints on the network, allowing for quick responses to threats. You can allow Carbon Black to automate responses to certain threats, and you can address other threats manually for maximum protection. The software generates significant levels of information about threat events in its reports.
When you want to add features like monitoring for vulnerabilities and hunting for threats, you may have to purchase add-on packages to your normal subscription.
Pros:
- Uses automated monitoring to block suspicious apps and behaviors from endpoints on the network
- Provides a high level of explanation about most threats, which simplifies making decisions about handling the threat
- Even though VMWare doesn’t publicize pricing, customers report that it is an affordable EDR option, although you may have to pay extra for some features
- The dashboard is well-designed and makes the software easy to use
Cons:
- Generates more false positives than you may want to see at first, at least until you can adjust the settings
- It tends to occupy more network resources than we’d like to see, creating some sluggish network performance issues
Pricing:
VMWare does not publicly release pricing for Carbon Black, but it does offer three usage tiers: Standard, Advanced, and Enterprise.
You can view multiple demos for Carbon Black and also schedule a personalized demo for free with a VMWare representative.
How to Pick Your Best Endpoint Detection and Response Tools
Step 1: Determine Your Need for Time-Saving Features
To start your search for the best EDR tools, think about how many IT resources you have available to devote to managing the tool. If you have a small security department, you may want to select an EDR tool that automates many of the endpoint monitoring processes. This will save you time and free up your personnel to focus on other security tasks.
Sophos Intercept X Endpoint, Trend Micro Apex One, and CrowdStrike Falcon all make use of AI features that automate many aspects of running the software.
SentinelOne uses AI as well, and you can set up groups of endpoints and then assign the same settings to all members of the group, saving quite a bit of time in setup. VMWare Carbon Black carries a well-designed dashboard, simplifying your ability to find the information you need quickly.
Step 2: Select a Tool That Guards Against Specific Threats
Next, think about the most common types of threats that your network faces through its endpoints. If you don’t have specific threats to worry about, any of the EDR tools on our list should fit your needs to guard against general and common threats.
However, if you have significant concerns about ransomware threats occurring through an endpoint on the network, you may want to select Sophos Intercept X Endpoint, as it offers specific defensive tools against ransomware.
If you have primary concerns about defending against the latest threats (zero-day attacks) to your network’s endpoints, SentinelOne, CrowdStrike Falcon, and Cynet 360 XDR focus heavily on these types of attacks.
Step 3: Avoid Sluggish Network Performance
Some EDR tools may cause some issues with sluggish performance on the network for your endpoint users. When these tools run active scans, they can demand a higher share of network resources than normal.
If it is important for you to avoid sluggish network performance, think about making use of tools that run smoothly with fewer resources, like Cynet 360 XDR or Trend Micro Apex One.
Step 4: Think About Whether You Need Extra Features
Finally, think about whether you need an EDR tool that includes extra network security features beyond endpoint security. Having an EDR tool with multiple security tools wrapped into one package or with the ability to work with other tools seamlessly can enhance your overall network security plan.
CrowdStrike Falcon, Trend Micro Apex One, and Sophos Intercept X Endpoint do a good job of meshing a variety of security tools with their EDR tools. You also can receive extra security features with VMWare Carbon Black, but you may have to pay more for them.

