Best Dynamic Application Security Testing (DAST) Tools
Application security is a foremost concern for modern businesses scaling their app usage. These applications are common targets of layered attacks, forcing organizations to rethink their security policies. Dynamic Application Security Testing (DAST) offers developers a crucial lifeline to detect vulnerabilities during the production stage.
DAST uses penetration testing techniques to discover vulnerabilities such as broken authentication flaws or code injection vulnerabilities while the app is running. This step is crucial for uncovering vulnerabilities that can’t be detected with static analysis.
Standard DAST tools have varying features, capabilities, and price points. So we created this guide to help you cut through the noise and choose the best DAST tool for your organization.
Acunetix

Acunetix is an industry leader in securing application programming interfaces (APIs), websites, and web applications. The software also combines the power of Interactive Application Security Testing (IAST) with its DAST capabilities to offer robust vulnerability scanning. The additional IAST testing compensates for dynamic testing shortfalls to ensure solid underlying code.
The software exposes hidden files, inputs, and configuration information that a DAST-only test misses. Thanks to the Acunetix AcuSensor set up on the application’s back-end. Furthermore, the additional IAST capability reduces false positives. Finally, the tool easily integrates with the continuous integration and continuous development pipelines and popular issue trackers like GitHub and Jira.
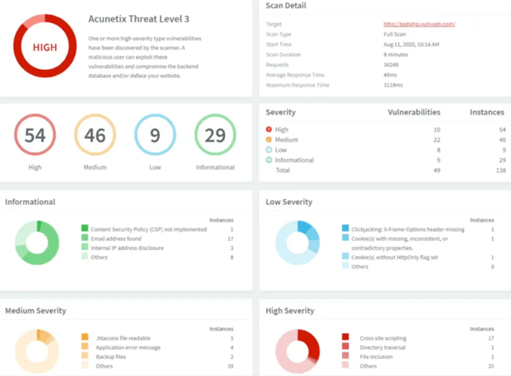
Acunetix also provides comprehensive reports to help with remediation. The Scan Results page is packed with actionable information, including the affected item and POST data used. You can also enable the AcuSensor Technology feature to view the source code line number causing the vulnerability. Finally, you get easily digestible feedback on how to fix detected vulnerabilities.
Other notable Acunetix features include:
- Advanced crawling technology capable of scanning multi-level forms and password-protected pages
- Schedule automated scans
- Detect 7,000+ vulnerabilities
- Built-in vulnerability management
- Software Composition Analysis (SCA) for open-source components
- Unlimited users and scans
- Flexible API
You’ll need to request a quote to get your individual pricing. However, base pricing starts at $4,500 for the Standard package and $7,000 for the Premium package.
HCL AppScan Enterprise
HCL AppScan Enterprise uses a powerful engine to crawl web applications and test for vulnerabilities automatically. In addition, the platform easily integrates into your source code development lifecycle (SDLC), which is perfect for DevSecOps. AppScan also offers multiple deployment options, including cloud, on-premise, and hybrid environments.
The software offers flexible scanning options. You can perform full scans or focus only on changed code. AppScan also provides deep integrations with issue management systems so you can quickly push vulnerabilities to where your team is likely to notice. The detailed security reports prioritize and classify applications assets, making identifying high-risk areas easier. You can also customize the reports to define risk on your terms.
HCL AppScan simplifies remediation by offering actionable suggestions for fixing vulnerabilities. It includes some white-hat capabilities, such as indicating problematic code and a task list for remediation. Other AppScan features include:
- Centralized management
- Regulatory compliance
- Automated security testing
- Scalable
- Risk-based management
- Actionable reporting
You’ll need to contact HCL AppScan to get your quote.
Detectify

Detectify is more than your typical DAST tool. It is a robust vulnerability scanner that allows you to test for thousands of potential vulnerabilities in your applications. In addition, the tool is flexible, allowing you to choose the assets you want to scan. You can also define the settings to create a customized scan profile for more granular control.
Alternatively, you can schedule automated scans in the different SDLC stages, including development, staging, and production. This is perfect since you get the internal scanning capabilities lacking in standard DAST tools.
You can also stick with the Asset Monitoring tool if you’re only interested in external vulnerability scanning. Even then, the tool offers deeper testing than a standard DAST tool.
Detectify also has a large open-source community of ethical hackers. As a result, new and emerging threats are constantly added to Detectify’s already robust library. The software company also works on a bug bounty system. There’s a prize for anyone who can find a new vulnerability in a specific system.
Again, the software offers three options. These include:
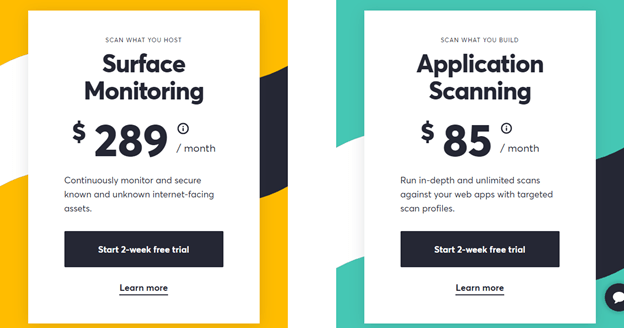
Deep Scan – This is an internal scanning tool not unlike a static application security testing (SAST) tool. You can easily integrate it into your CI/CD pipeline. Prices start at $289 per month.
Asset Monitoring – This checks for external vulnerabilities. Prices start at $85 per month.
Get All – Which offers the best of both worlds. You can also add custom services to this package. You’ll need to contact sales to get your custom pricing.
Detectify also offers an overview of all detected vulnerabilities. The tool provides expert tips on how to fix the vulnerabilities. Additional features include:
- Discover undocumented vulnerabilities
- Fast implementation
- Native integrations with the most popular project management software
Invicti (NetSparker)
Invicti is a terrific web application security solution that uses Proof-Based Scanning to minimize false positives. It can also detect versatile vulnerabilities besides the common standard SQL Injection and Cross-Site Scripting (XSS) vulnerabilities. In addition, the system is easy to set up and use and provides adequate proof of discovered vulnerabilities.
It is worth noting that NetSparker is part of the Invicti family. The company also produced Acunetix featured earlier in this review. Invicti is a long-term player in the cybersecurity space and is always a safe bet.
Invicti also includes an interactive application security testing (IAST) known as Invicti Shark. This addition allows the software to trace vulnerabilities back to their root cause. You also get a detailed report of all vulnerabilities, including actionable suggestions for remediation.
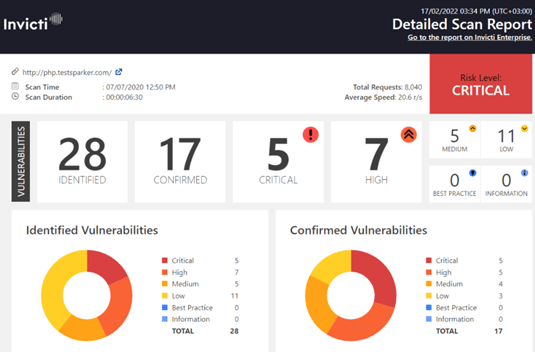
The report also automatically ranks vulnerabilities according to severity. This feature makes it easy to decide which issues to solve first. Invicti also automatically re-tests all fixed vulnerabilities to ensure that the issues are addressed satisfactorily.
Furthermore, Invicti offers native integration with popular issue trackers. For instance, you can mark fixed issues on Invicti or your chosen issue tracker. The platform seamlessly adapts to your existing ecosystem and development tools so you don’t disrupt your workflow.
You’ll need to contact sales to get your custom quote. However, Invicti’s pricing starts at $666 per month.
Speed is the main complaint about this DAST tool. Invicti performs deep scans, which can take more time than some developers prefer. This case is especially true if you have a slow network connection.
OWASP ZAP
OWSAP Zed Attack Proxy (ZAP) is an open-source DAST tool for those looking for a free vulnerability scanner. Surprisingly, it is valuable for a free tool and embedded in your CI/CD pipeline. The tool offers automated scanning and manual pen testing to fit your organization’s needs. ZAP is a man-in-the-middle proxy tool. This means that the tool sits between your browser and web application.
The tool is also designed to suit a range of skill levels. Security testing specialists, developers, and novice testers will find the DAST tool extremely useful. For instance, the automated tests provide comprehensive reports, including suggestions for fixing discovered vulnerabilities. In addition, more seasoned testers can manually inject payloads to expose potential vulnerabilities when the application is in an undesired state.
ZAP also allows versatile scripting for a wide range of scripting languages. This feature helps create custom scripts to automate tasks. You can also generate scan policies from scratch for each application you wish to test.
On the downside, ZAP requires some level of proficiency to use correctly. The dashboard can be overwhelming, and analyzing results can be difficult for a novice. However, the platform offers extensive and accurate documentation to smoothen the learning curve.
As an open-source tool, ZAP is free to download and use.
Rapid 7 InsightAppSec
Rapid 7 offers a robust DAST tool known as InsightAppSec. The tool provides deep technical insights and context for each discovered vulnerability. In addition, InsightAppSec offers native integrations with Jira and Atlassian to speed up remediation and precisely match your workflow.
The tool offers a simple and intuitive interface. You view your entire app portfolio on a single dashboard, including internal and external apps. You can also easily add new apps to your dashboard.
InsightAppSec comes fully configured right out of the box. So you can get directly to scan your apps without lengthy configuration. However, the Scan Configuration Wizard is simple to use. This is convenient for customizing settings to balance speed and comprehensiveness.
The Audit Logging feature lets you keep an eye on everything. For instance, you can see all manual activity, including who performed the action and the exact time it was triggered. This feature is handy for fulfilling compliance requirements.
Finally, InsightAppSec makes managing vulnerabilities simple. You can create unique filters or use the custom filters to find specific vulnerabilities based on criteria such as new vulnerabilities or most critical issues. You can also export vulnerabilities to CSV, Jira, or ServiceNow.
InsightAppSec pricing starts at $166 per month per app.
On the downside, reporting can be challenging to use and digest for some users.
How to Pick Your Dynamic Application Security Testing (DAST) Tool
It may not be apparent which DAST tool featured here is the best option for your organization. Many more options are available on the market, making this decision even more difficult. However, you can take a few quick steps to help you pick the best choice for your organizations’ needs.
Step 1 – Consider Coverage First
Long gone are the days when applications were only built on HTML. Instead, today’s developers use a combination of complex frameworks like AJAX and JavaScript. Add JSON and REST interfaces and CSRF for security, and you need a complex tool that can keep up with your needs.
However, most legacy DAST tools are only adept at scanning HTML with minimal variation. So the first step is to rule out any DAST tool that doesn’t support the web technologies you use for app development.
Step 2 – Outline Your Most Important Features
DAST tools come with all kinds of features. So your feature set plays a significant role in choosing the best tool. Accuracy is a great place to start. You need a tool with zero false positives to avoid slowing down your development lifecycle.
Other features to consider when choosing your DAST tool include:
- Test both web apps and APIs
- DevOps friendly
- Test for a broad range of vulnerabilities
- Remediation guidance
- Reporting on critical vulnerabilities
- Innovative attack simulations
- Seamless integrations
- Automated testing
Consider a brainstorming meeting between your development and security teams. DAST tools shift security left, meaning that your developers are also responsible for security. Therefore, their input is crucial to avoid rolling out a tool with features only security professionals can use.
Your developers shouldn’t need advanced cybersecurity training to understand the tool’s output and configure tests in an ideal environment.
Step 3 – Consider Your Deployment Model
DAST products are available as on-premise or Software as a Service (SaaS) solutions. Each option has its pros and cons, so think about your business case before deciding.
SaaS deployment is generally the better option. On-premise deployment often requires a much more significant upfront investment. However, on-premise deployment integrates better with existing IT infrastructure. Consider the pros and cons of each option before making a final decision. Some DAST tools also offer support for hybrid environments.
Step 4 – Decide the Best Scanning Method
DAST tools offer diverse scanning frequencies and methods. So it is good to decide this aspect upfront to narrow your option further. The most common scanning options here include:
CI/CD Automated Scan – This option comes highly recommended since the application scanning is built into your DevOps pipeline. Therefore, developers discover vulnerabilities before the application hits the production environment.
Manual Scans – These scans help validate fixes and are easy to set up. However, they aren’t as easy to reproduce when vulnerabilities are found.
Scheduled Scans – These scans are suitable for developers who aren’t ready to automate testing. However, these scans may have limited scope since they happen against the production site.
Some DAST tools offer flexible scanning options to suit your needs at a particular time.
Step 5 – Test a Few DAST Tools
You may have narrowed down your choices to two or three tools. Then, you can take advantage of the free trials and product demonstrations to see how they work in a real-world scenario. Some of the factors to consider when testing your DAST tool include:
Collaboration with DevOps – Good software should easily integrate with your existing bug tracking and ticketing systems. Check how well the software creates issues or tickets for your DevOps team to fix.
Integration with your SDLC – Consider how early your tool allows you to detect vulnerabilities. A good tool will enable you to see vulnerabilities before production, where remediation is easier and cheaper.
False positives – You want zero false positives whenever possible.
Ease of use – Review the tool’s user interface (UI) and how easy it is to navigate and configure it. Then, check the reports and evaluate if there are adequate for your organization’s purposes.

