Best Breach and Attack Simulation (BAS) Tools
Professional athletes and musicians practice a lot to make sure they’re ready when the pressure ramps up. Similarly, when you deploy a breach and attack simulation (BAS) tool on your network, you are practicing to make sure your network is ready to go when hackers put your security measures to the test.
BAS tools will simulate a network attack at varying levels of intensity and complexity. The hope is that the simulations allow you to see any weak spots or gaps in your security setup before hackers take advantage.
We will outline some of the best breach and attack simulation tools and explain the most important steps you should follow when selecting one for your network.
AttackIQ
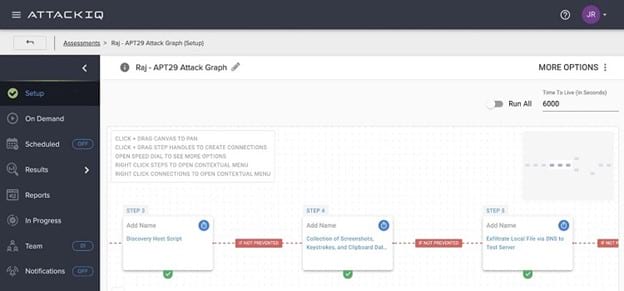
The AttackIQ BAS tool is a highly popular choice, as it delivers an easy-to-use platform for testing the effectiveness of your security system.
AttackIQ likes to describe its BAS as an “offensive defense” system because of its aggressiveness in running scenarios that will greatly test your system. Running complex scenarios can be challenging, but running these with AttackIQ will deliver the best ability to find security flaws.
Even with complex scenarios in hand, AttackIQ’s user interface is easy to understand and set up, helping you run more tests in a shorter amount of time. It also runs these scenarios in an extremely safe manner, so you never actually place your network at risk.
AttackIQ has a research team in place that constantly works with new security scenarios. This allows the team to update this BAS tool frequently to deal with any new attack vectors.
Pros:
- Offers multiple scenarios for simulated attacks
- Easier to set up and use than you may expect
- AttackIQ quickly adjusts its list of scenarios based on new attacks, so you’re always up to date
- Technical support options and other research options are strong
Cons:
- Analytical reports can be a little confusing to decipher
- The product is newer than some others, so minor changes to the platform occur frequently
Pricing:
AttackIQ does not offer public pricing information but you can request a demo on the website.
Cymulate
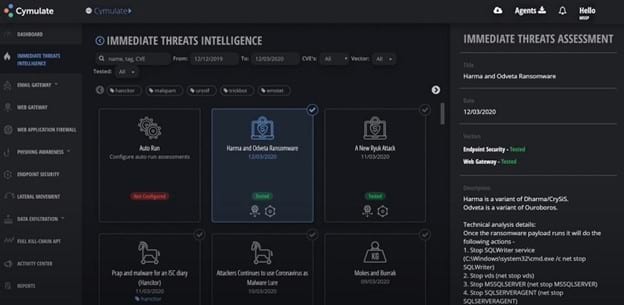
When you want to be up and running with your BAS tool in a short amount of time, Cymulate is an excellent choice. You can install and begin using Cymulate very quickly, ensuring that you are measuring your security performance safely.
Cymulate offers a wide range of attack scenarios, so you can always be certain you are testing your system in the most efficient way possible. Cymulate can run complex and simple scenarios with equal levels of success, measuring vulnerabilities and delivering security scores for different aspects of the network.
After Cymulate simulates an attack, it is able to provide insight and advice for remediating the problems. As part of the advice, Cymulate will help you figure out which vulnerabilities are the most pressing and severe, making it easier to budget for the security work that needs to occur.
Pros:
- Offers multiple resources to help you improve your system security with risk assessment information
- Fast and straightforward setup
- Technical support personnel are extremely helpful and responsive
- Offers a scoring system that makes assessing the system performance easy
Cons:
- Report function could be better by giving you more control over the final results
- Doesn’t offer as many third-party integrations and resources as some others on the list
Pricing:
Cymulate does not offer public pricing information. You can request a free trial or request a free demo from Cymulate.
SafeBreach
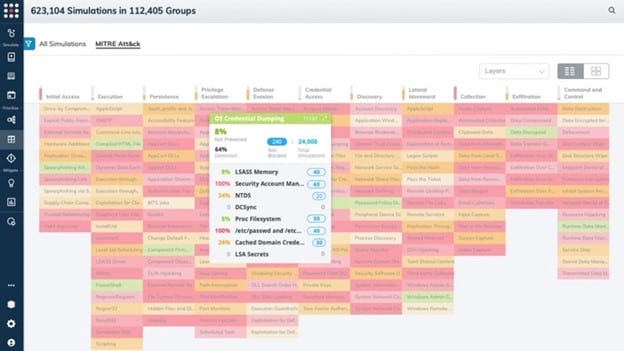
The development and deployment of BAS tools really have only been occurring for roughly a decade, so it can be tough to find a tool that has proven itself over time. If longevity is a primary concern for you, SafeBreach was one of the first BAS solutions on the market, and it continues to offer a highly successful service.
The SafeBreach team delivers regular updates to this BAS tool, ensuring that it always has the ability to run scenarios involving the latest attacks. It is able to simulate more than 15,000 attacks, including those that originate either inside or outside your organization. This yields a well-rounded picture of the system’s performance.
SafeBreach is easier to install than some other BAS tools. It generates easy-to-use reports, so you can quantify the risk your network is facing. You then can prioritize the investments you are making in network security, as the entire team will be on the same page.
Pros:
- SafeBreach is one of the oldest BAS tools, so it has a loyal customer base
- Works across the entire network, including cloud and endpoint
- The simulations do not place the network in any danger
- SafeBreach team constantly updates the tool to ensure protection against the latest attack vectors
Cons:
- Doesn’t work quite as well for smaller networks and organizations as it does for large networks
- Interface is not as easy to use as some others on our list
Pricing:
SafeBreach does not offer public pricing information. HOwever, you can request a free trial or request a free demo from SafeBreach and also request a free network assessment.
XM Cyber
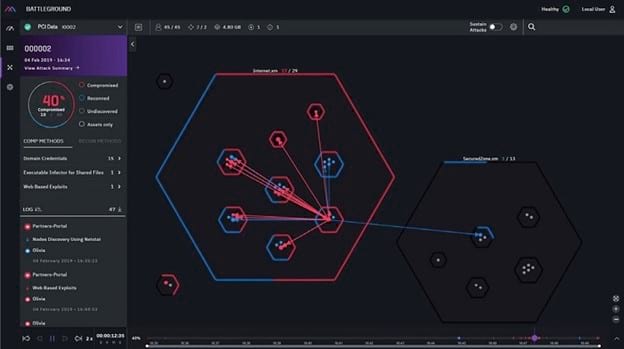
When you want a BAS tool that can run in the background and automate attack simulation processes, XM Cyber is a strong contender. It will scan your network from end to end, constantly looking for issues that could leave you vulnerable to an attack.
Even though XM Cyber operates continuously, it should not bog down your network performance, meaning your users should not notice any slowdowns.
You also have the option of selecting attack targets on your network manually and allowing XM Cyber to focus on those simulations. Multiple attack scenarios are available, varying in complexity, to ensure you receive the most accurate possible results.
This BAS tool does a good job of determining exactly which aspects of the network are the most valuable, ensuring that it focuses on running scenarios that protect those areas from attack.
Pros:
- Delivers advice on remediation efforts you should use after discovering vulnerabilities
- Many aspects of XM Cyber run automatically across the entire system to simplify the process
- Finds both human error vulnerabilities and improperly configured software vulnerabilities
- Determines which aspects of the network require the highest levels of protection
Cons:
- Requires a bit more know-how to start using this product than some others
- Some customers report that the pricing is a little higher than average versus other BAS tools
Pricing:
XM Cyber does not offer public pricing information, though you can request a free trial or free demo from XM Cyber.
Picus
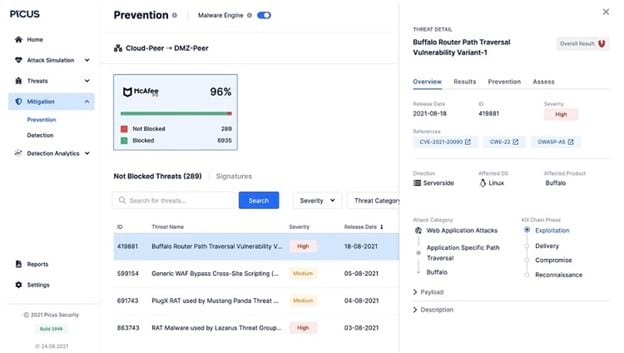
Picus is a good choice when you want your BAS tool to provide information about network vulnerabilities in real-time as it runs its scenarios. This gives you immediate feedback, so if your network has significant issues, you can begin addressing them quickly before a hacker could take advantage of them.
Another advantage of Picus is that you can start operating the tool in very little time. Installation does not take long, giving you the ability to begin running simulations within several hours.
Even though this tool is easy to use, it can still handle complex simulations. In fact, it probably is better suited for networks that have quite a few complexities versus only simple designs.
Picus was one of the earliest BAS tools that appeared in the market, meaning it has proven its capabilities over several years. It has a user base that believes in it, meaning you often can find some answers to problems you may be having through fellow customers.
Pros:
- The Picus team keeps its list of available simulations up to date with frequent releases
- You can set up the BAS tool to focus primarily on new attack scenarios
- Reports help you focus on the most vulnerable areas of the network
- Has been around for nearly a decade and has a loyal customer base
Cons:
- Reporting options could use more customization features for end-users
- Dashboard has some complexity to it, which may be tougher for novices to decipher
Pricing:
Picus does not offer public pricing information. You can request a free demo from Picus.
Infection Monkey
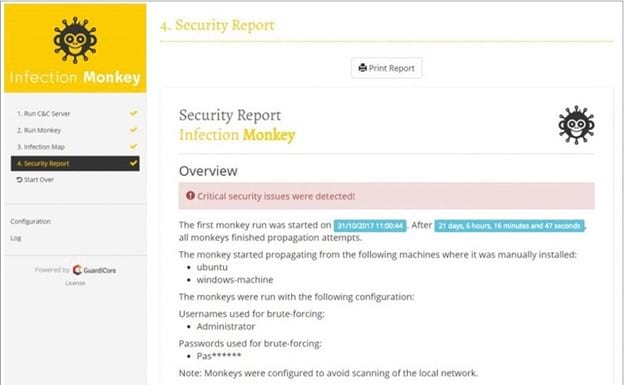
If you are a fan of open-source software, Infection Monkey is one of the best open source BAS tool options. Guardicore Labs maintains Infection Monkey.
As an open-source BAS tool, you will need to feel confident about installing and operating the software on your own without extensive technical support options. Fortunately, Infection Monkey has a great user interface and is easier to use than the majority of open-source software packages.
Infection Monkey generates stronger reports than you may expect to find. It will make recommendations regarding protecting your network from attack. Its reports produce enough detail that you can see the exact machines on the network that have vulnerabilities.
Pros:
- As open-source software, it’s free to use and you can verify the coding yourself if desired
- It especially functions well in cloud-based environments
- Versus typical open source tools, it has a better-looking user interface and is easier to use
- The attack scenarios are extremely realistic, especially for a free tool
Cons:
- Infection Monkey doesn’t offer the customization features that others on our list have
- Accessing information to help with troubleshooting can be more challenging than with subscription-based BAS tools
Pricing:
Infection Monkey is available as a free download, as it is open-source software.
Rapid7 InsightVM
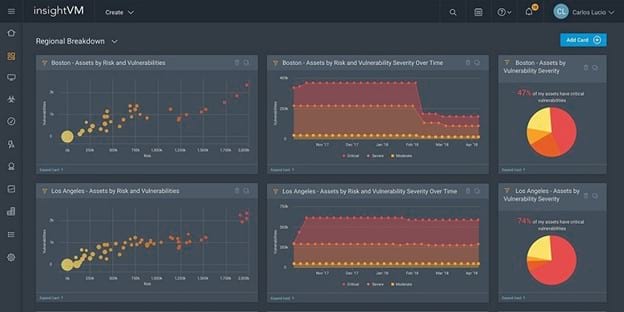
Rapid7 offers a number of different security-based tools, and InsightVM fits right in with those tools. InsightVM is the BAS tool in the Rapid7 family. If you already use other Rapid7 tools, you’ll find that InsightVM runs nicely alongside them, giving you a powerful set of security tools.
InsightVM differs from some other BAS tools in the way you can set it up to focus on any vulnerabilities in the credentials of network users.
When InsightVM scans the entire network and runs attack scenarios, it will provide detailed explanations of the vulnerabilities it finds. It also will provide recommendations on how to fix the problems successfully.
InsightVM provides a real-time risk assessment for the network that you can view in the dashboard, so you always have an understanding of the network’s current risk.
Pros:
- InsightVM’s reports deliver detailed results about vulnerabilities but remain easy to understand
- You can control whether the scans run on-demand or automatically
- Offers the ability to run scans that focus on the vulnerability of credentials and of the authentication of users on the network
- InsightVM provides advice on mitigating the problems the tool discovers
Cons:
- The user interface could use a refresh
- The vulnerability scans seem to run slowly on a busy network
Pricing:
InsightVM costs $19.56 per year per asset for 1,000 assets. InsightVM’s pricing will vary based on the number of assets in use.
You can request a personalized quote from InsightVM, request a free trial, or request a free demo.
How to Pick Your Best Breach And Attack Simulation Tools
Step 1: Understand Your Level of Expertise
When beginning your search for the best BAS tool, it’s important to start with an honest assessment of your ability to manage the tool.
If you or your team has plenty of experience with managing these tools, ease of use will not be a significant consideration for you. You may prefer an open-source BAS package, such as Infection Monkey, because you may not need much in the way of technical support.
If ease of use is going to be a key component of your BAS tool, however, you will want to stick with an option like SafeBreach or Picus. You can be up and running quickly with these tools.
Step 2: Complexity of Your Network’s Scenarios
Some networks have a simple layout, meaning almost any BAS tool will be able to deliver the desired scanning results. However, you may have significant complexities in your network’s operation that could leave your network exposed to unusual vulnerabilities.
So the second step in searching for the best BAS tool should involve measuring the level of complexity you need in your scenarios.
AttackIQ offers some of the most complex scenarios for finding network vulnerabilities. It can run these complex scenarios in a short amount of time, all without placing your network in any unsafe situations. Cymulate and XM Cyber also are able to run extremely challenging scenarios that can help you discover vulnerabilities that less complex BAS tools may miss.
Step 3: Receive Advice on Fixing Problems
Next, take some time to think about whether you and your team will want some help with deciphering the results of the scenario scans. If you do not need advice about fixing the problems the BAS tool finds, you can make use of any of the tools on our list successfully.
However, if you would like some help with remediating problems, including advice that helps you focus on the most serious problems, you will want to select a tool like Cymulate or Rapid7 InsightVM. With Infection Monkey, you’ll receive details about vulnerabilities down to the level of an individual machine on the network.
Step 4: Importance of Constant Updates
As a final step, think about the level of concern you have regarding falling victim to new attacks. If you don’t believe your network is any more vulnerable to newly discovered attacks versus traditional attacks, any of the tools on our list should be able to help you with scenarios.
However, if you want to receive constant updates from the BAS tool developer about new scenarios based on new attack vectors, we’d suggest focusing on AttackIQ or SafeBreach. The teams behind both of these BAS tools focus heavily on research and on constant measuring for new methods of attack.
They both update their BAS tools and scenarios regularly to account for their findings of new attacks.

