Best Botnet Detection Tools
Are you on the lookout for the best botnet detection tools to secure your network and avoid unwanted bot traffic? If the answer is yes, this article is for you.
We examined several botnet detection tools rigorously and have shortlisted the top seven that have proven themselves to be among the best.
Whether your requirement is for an individual user, a small business, or an enterprise-level solution, we believe these tools are going to meet or exceed your expectations.
We understand your requirements are unique and some tools might be more suitable for your needs than others. Therefore, to help you make the best decision for yourself, we are going to analyze the core features, pros and cons, and pricing plans for each of the tools separately.
ESET Endpoint Security
ESET Endpoint Security is antivirus software for small businesses. It includes numerous security features and a user-friendly dashboard that allows easy access to reports, options, and features. The software helps businesses secure all the machines on their network by shielding them from a broad spectrum of security issues.
ESET Endpoint Security’s malware detector is among the best in the industry. Be it trojans, adware, worms, or viruses, the software offers robust defense capabilities. It’s an intelligent program that can differentiate well between friend and foe. Therefore, the rate of false positives is very low.
Living up to its name, ESET Endpoint Security focuses on securing network endpoints – the joints where your internal network connects with the outside world. It’s also capable of recognizing patterns to flag and block unknown threats. It continuously monitors system memory to identify suspicious programs including any malware that would otherwise sneak through the cracks easily.
The software can be purchased on an individual license or as a more robust security suite in groups of five or more seats.
ESET Endpoint Security Pros
- Frequent updates.
- Audit and automation reports.
- Hardware inventory status.
ESET Endpoint Security Cons
- False positives.
- Lack of integration with some operating systems such as Debian and Rhel-based distributions.
- May affect mobile device performance.
Pricing
- ESET Protect Entry: Starting from $312.4/year.
- ESET Protect Advanced: Starting from $216.5/year.
- ESET Protect Complete: Starting from $266.5/year.
All plans come with a 30-day free trial.
DataDome
DataDome not only offers robust botnet detection capabilities, but it also scans for the top ten threats on OWASP – a community that lists the most serious new network threats and vulnerabilities. This makes DataDome a vulnerability scanner in addition to an anti-botnet solution.
DataDome effectively deals with DDoS attacks, account takeover attempts, data scraping, and click fraud. With the help of its threat intelligence feed, DataDome receives information on the attack experience of all its customers to continuously optimize its defensive capabilities.
You can integrate DataDome with your website, mobile app, and services using a plugin. Its cloud-based console presents detailed reports based on the collected data from these agents.
DataDome Pros
- Integration with OWASP threats – updated regularly.
- Robust protection against scraping, DDoS, ATO, and click fraud.
- Intuitive web interface, easy-to-use.
DataDome Cons
- Not suitable for small businesses.
- May send CAPTCHAs to real humans at times.
Pricing
- Business: $3890 per month billed monthly or $2990 per month billed annually.
- Corporate: $7790 per month billed monthly $5990 per month billed annually.
- Enterprise: Custom pricing.
All plans come with a 30-day trial.
Radware Bot Manager
Radware Bot Manager works as a plug-in or an API with a variety of integration methods available. Whether it’s a web server, CDN, or cloud server service, Radware Bot Manager can be integrated easily as an add-on.
The tool can also be used to pre-filter traffic from your network gateway in the form of a “virtual appliance”. The program is capable of creating a profile for each IP address through the traffic it filters. This profiling allows it to track users and flag any bots that come along. The software refers the IP profiles to the Radware server, where a decision to allow or reject the traffic is made.
At the setup stage, the program allows you to select from a range of actions to be taken automatically when bots are spotted. Depending on the kind of threat it encounters, the program can serve reCAPTCHAs to potential suspected bots or directly block traffic from known bots.
Radware Bot Manager Pros
- Intuitively designed admin dashboard.
- Can act as a WAF to filter traffic.
- Automated actions for when a botnet is detected.
Radware Bot Manager Cons
- Offers limited features against DDoS attacks.
- The trial period is too short.
Pricing
Radware Bot Manager has not provided pricing information publicly. Please contact the vendor for detailed pricing information.
A free trial is available before you pay for a subscription.
FortiEDR
Formerly known as Ensilo, the FortiEDR endpoint protection and antivirus tool by Fortinet is designed to safeguard networks and every device running on them. The program offers security automation for risk mitigation and solid endpoint detection and response capabilities.
FortiEDR’s next-generation antivirus capabilities provide a robust line of defense against viruses and other malware. Available on Windows, Mac, and Linux machines, FortiEDR ensures the security of your network with its strong malware and botnet detection tools.
FortiEDR Pros
- Playbooks for automated responses to threats.
- Simple and easy-to-navigate UI.
- Real-time incident management.
FortiEDR Cons
- It takes time to integrate with other applications.
- The website can be buggy at times.
Pricing
No pricing information has been provided publicly by FortiEDR. Please contact the vendor for a quote based on your requirements.
A free demo is available for you to experience before you pay for a subscription.
Netacea Bot Management
Netacea is a powerful botnet detection tool. It combines traffic analysis with real-time and historical trends to analyze user behavior and identify potential threats. Netacea is uniquely capable of detecting complex botnet threats. It conducts extensive signal gathering and presents its analysis via an easy-to-use dashboard.
If your business needs to safeguard against a wide range of traffic, Netacea is a great match for your needs. Its server-side-only version allows it to monitor and defend against any bot traffic coming from mobile devices, APIs, internet apps, IoT-enabled devices, or any other forms of online threats.
Furthermore, Netacea’s Intent Analytics feature allows the analysis of network and API logs in real-time to counter any botnet threats. Businesses can make informed decisions about their web traffic using Netacea’s transparent and actionable threat intelligence system.
Netacea Bot Management Pros
- Great customer service.
- Real-time metrics and data.
- Easy integrations.
Netacea Bot Management Cons
- Automated rule-setting doesn’t offer a lot of flexibility.
- New AI models can take a long time to develop.
Pricing
The pricing plans are flexible and depend upon your monthly web traffic, web infrastructure, and integration points. For a more detailed quote, please contact the vendor.
PPC Protect
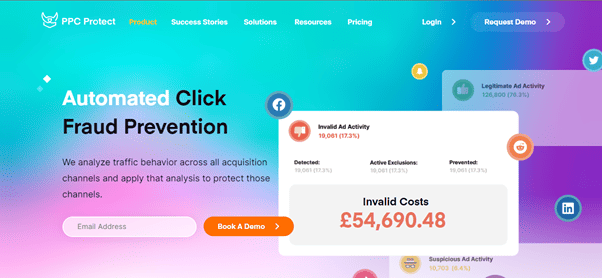
PPC Protect is a robust software to detect and prevent fraudulent clicks on ads. Designed with an enterprise/agency-first approach in mind, this SaaS solution for PPC marketers monitors ads in real-time for suspicious behavior.
Based on your requirements, you can set up PPC Protect to monitor a single domain or multiple ones simultaneously. A web-based dashboard allows you to administer the tool and analyze reports. The software is capable of real-time IP address and device blocking, detection of new threats via a self-learning AI algorithm, and protection against an infinite number of fraudulent clicks.
PPC Protect doesn’t require any installation. Simply, copy and paste code into your website to start full traffic monitoring. This results in a smooth user experience with no impact on website performance. The software collects over 100 data points about incoming traffic and cross-references it with PPC Protect’s threat database.
PPC Protect Pros
- Powerful reporting tools provide easy-to-understand insights.
- The dashboard is simple yet powerful.
- Easy implementation.
PPC Protect Cons
- Not easy to determine how much money you’ve saved.
- The ability to pull data from the platform can be improved.
- The social media monitoring tool may get clunky at times.
Pricing
The pricing plans are:
- Pro
- Elite
- Agency
Detailed pricing information has not been provided. However, a more detailed quote can be obtained from the vendor. A demo can be requested before the purchase of a subscription plan.
Beacon
![]()
Beacon Click Fraud Protection offers comprehensive cross-platform protection against fraudulent clicks. The networks it covers are Google Ads, Bing, Facebook, and Instagram. Marketers using Beacon can reliably measure campaign results, knowing the reports are fraud-free.
Fraudulent bot clicks and other forms of invalid traffic waste nearly half of all ad budgets. Beacon is capable of reducing this waste by as much as 66%.
Beacon offers bot detection, bot blocking, and the ability to reach more humans instead of bots, boosting the return on ad spend for marketers. You can install the software in a matter of minutes with zero impact on system performance or user experience.
Beacon Pros
- User-friendly dashboard.
- Great customer service
Beacon Cons
- Only works best with high-spending accounts.
- Setting it up for a new client is time-consuming.
Pricing
Pricing plans depend on your needs. Therefore, no detailed pricing information has been provided. Please contact the vendor to schedule a call for more details.
How to Pick Your Botnet Detection Tool
With so many botnet detection tools and even a greater number of threats to contend with daily, selecting the right software for your business can be tricky.
Make sure to consider the following steps before committing your time and money to an available solution.
Step 1 – Understand Your Requirements
The first step in this process is to understand your botnet detection requirements based on the kind of threat your business is facing. Are the bots trying to artificially deplete inventory from your store? Are they stealing your price lists using scraping? Are they trying to brute force their way in using compromised credentials?
Once you’re aware of the specific nature of the threat you’re facing, you put yourself in a better position to select the right software for your business. For instance, some tools are only designed to detect bots after receiving multiple requests. Such solutions won’t help you ward off scraping bots that rapidly move in and out.
Step 2 – Look for Compatibility
The second step is to shortlist tools that integrate well with your existing Web Application Protection/Firewall solution. In addition, make sure to look for solutions that are compatible and can integrate with mainstream analytics dashboards so you can analyze potential bot activity in more detail.
Ensuring compatibility is an important step in selecting the right botnet detection tool for your business. It makes the deployment of the solution smooth and easy for all stakeholders involved and can save you tons of time and money.
Step 3 – Think Long-term
Botnet detection tools have come a long way in terms of keeping existing botnet threats at bay. But at the same time, bad actors are evolving quickly in an attempt to get past the strongest defenses we have available.
The third box to check in your search for the right botnet detection solution is to make sure it’s positioned to combat emerging threats and attacking methods never seen before. Ask the sales representative about the steps being taken to ensure long-term deterrence against new threats as well the research being conducted to always stay one step ahead of the game.
Step 4 – Consider Ease of Deployment
Once you’ve shortlisted botnet detection tools based on compatibility and long-term reliability, the next step is to make sure they’re easy to deploy. Some important questions to ask at this point are:
- Are the integrations easy to execute?
- Would you have to make any architectural changes?
- How extensive is the documentation?
- What is the onboarding process like?
Ease of deployment is an important topic because a cumbersome deployment process can affect your organization’s productivity and cost extra time and money. It can even create bigger technical challenges for your IT team if the integrations are difficult and architecture changes are required.
Step 5 – Take the Free Trial
Finally, take advantage of the free trials usually available before you purchase a paid plan. Try out the shortlisted tools to make sure they’re working smoothly. Test them against real traffic and take note of what they block and what they let through, keeping in mind that not all bot traffic is bad. So it’s important to find the right detection balance for your business. Have some of your IT team review the results before making your final decision.

