Best Application Security Tools
Keeping your business’s networks and data secure can involve multiple steps and processes. One of the most effective processes is through the operation of application security tools.
Through scanning, the best application security tools will help your organization have a better chance of preventing data breaches and other malicious attacks.
We have narrowed down the six top application security tools available now. With the consistently high rankings users give these tools, you can use this list to find a great piece of software to protect your network and company.
Veracode
Compared to some of the other best application security tools, Veracode matches the strong security features they offer. However, it goes beyond the basics by adding numerous testing services for applications. It also offers consultancy work, giving you a full package of security services for your network’s applications.
In addition to finding security flaws and unsafe applications, Veracode works to help you fix the problems and move toward a safer network setting.
In terms of application security, Veracode’s greatest strength lies in its ability to create a centralized view for all of its security features and scans. If you currently use another package that forces you to switch windows each time you want to see the results of a different scan, you’ll quickly come to appreciate how Veracode operates. You can see everything you need at a glance.
The different types of analysis Veracode focuses on include:
- Static and dynamic network analysis
- Software composition analysis
- Security testing of interactive applications
- Penetration testing
Veracode has a strong track record of finding application security holes. Veracode can trace its roots to a release about 15 years ago, and it has a long-standing loyal user base that trusts this software.
Pros:
- Displays the most important information in one place
- Product longevity showcases its trustworthiness
- Works equally well in large and small organizations
- Offers plenty of versatility in the types of analysis it provides
Cons:
- Does not offer a free trial
- Customers report pricing is above average
Pricing:
Veracode does not publicly release pricing details for its services. Potential customers can request a pricing quote.
SonarQube
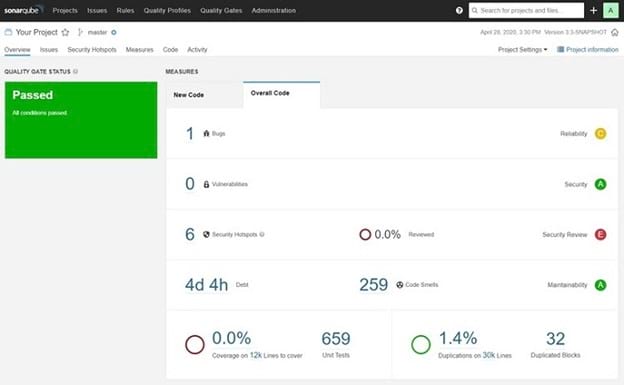
SonarQube is another highly popular tool for application security that also delivers the ability to help coders measure the quality of their work. It offers a free version that’s primarily for coders. If you want to make use of its advanced application security tools, you will need to use a paid tier, though.
For example, SonarQube delivers security reports in its Enterprise Edition that measure the danger of a particular security issue on the network.
In Enterprise, it sorts through the problems to mark certain applications on the network as potentially dangerous but not currently a significant security issue. Other applications may receive the designation of a vulnerability, which means you need to fix the problem immediately to maintain the security of your network.
SonarQube not only finds these potential security problems but also describes them in a manner that helps you determine the best way to fix them.
SonarQube went through its initial release about 15 years ago and has a long list of loyal customers using it for several years.
Pros:
- The interface is well-designed, making it easy to see the information you need
- Successfully finds issues with applications throughout the network
- Has a long track record of successful implementations
- Tends to deliver a high level of accuracy in its scans
Cons:
- Prices in the upper Enterprise tier can add up quickly
- Some users report disappointing results when needing to contact technical support
Pricing:
- Community Edition: Free
- Developer Edition: Starts at $150
- Enterprise Edition: Starts at $20,000
Customers can contact SonarQube for a precise price quote.
Checkmarx
Because Checkmarx provides such a wide range of security features for applications and coding, customers can trust it with multiple aspects of their networks. You can rely on Checkmarx to deliver useful security solutions with fantastic customer support.
One of the best features of Checkmarx is that it allows you to set the boundaries and high-level settings for your security needs. The Checkmarx tool then handles the day-to-day work involved in protecting the network based on your choices. It takes care of the precise steps involved in application security, so you can focus on the big picture.
Checkmarx offers a wide range of support options, including self-serve support with multiple types of resources. You even can interact with other customers to find answers to questions and to learn about new solutions.
Developers can take advantage of the flexibility found with Checkmarx to perform jobs ranging from identifying security vulnerabilities to scanning uncompiled source code, ensuring any release of code will be as safe as possible. You even have the option of running Checkmarx on-prem or from the cloud, depending on the specific needs of your network.
Pros:
- Offers usage for either on-premises or in the cloud
- Easily identifies and marks multiple types of software vulnerabilities
- The customer service team is extremely helpful
- Offers a full range of security monitoring options
Cons:
- Tends to deliver some false positives regarding security concerns
- Some customers report the price is higher than average
Pricing:
Checkmarx does not publicly release pricing details for its services. Potential customers can request a demo and pricing quote.
Fortify on Demand
You can use Fortify on Demand to monitor your network’s security settings without the need to hire specialized security personnel. Fortify on Demand is easy to implement and operate, and it offers key security needs without going into more advanced or detailed offerings you may not require.
Fortify on Demand has plenty of flexibility to match your needs, as it delivers multiple security features for testing and monitoring. It is a cloud-based solution, which greatly simplifies operation for those organizations that don’t have a dedicated security team in place.
If you are a growing organization that sees its user base and list of applications expanding quickly, Fortify on Demand can grow right along with you.
If you are looking to start your application security journey from scratch, Fortify is a solid choice. It helps you understand the different kinds of risks your organization is facing before allowing you to easily develop a risk profile.
Those with advanced application security needs may choose to look elsewhere, as Fortify’s design works better for those with basic needs.
Pros:
- Offers excellent customer service options
- Scans run faster than what’s available with competitors
- Offers a free trial period and a reasonable price point
- Reliable, as it delivers a solid set of results year after year
Cons:
- Some aspects of the interface and feature set seem a little dated
- Catches the most obvious security issues, but it sometimes struggles to identify complex and advanced issues
Pricing:
Fortify on Demand does not publicly release pricing details for its service. However, you can request a 15-day free trial of its cloud service without needing to submit a credit card.
PortSwigger Burp Suite
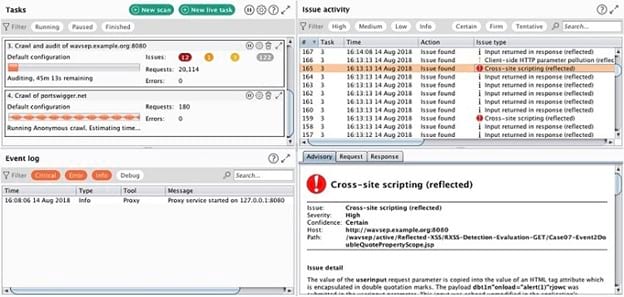
For organizations that have concerns regarding falling victim to newly-discovered security vulnerabilities, PortSwigger Burp Suite is here to help.
The PortSwigger Research segment of the company focuses on discovering vulnerabilities before hackers find them. PortSwigger then uses this information to make additions to Burp Suite, constantly keeping its security features up to date.
Another key feature of Burp Suite is its ability to measure the traffic coming from your applications. As your applications handle web-based requests, Burp Suite monitors the movement of data, looking for potential vulnerabilities. It also is able to fully scan a website, providing information about the flow of data across the site and whether any security issues exist.
Burp Suite has multiple subscription tiers available, along with a free version, making it easy to find just the right tier for your needs. The high-end Enterprise tier runs scheduled scans and delivers intuitive reports that drill down to the specifics you need for application safety and security.
Pros:
- You can customize the reports to match the needs of the recipient, such as managers or entry-level security personnel
- Uses an automated passive scanning feature to maximize efficiency and accuracy
- Wide range of pricing points for finding just the right features for your needs
- Allows you to monitor traffic emitting from applications to find uncommon vulnerabilities
Cons:
- Interface seems dated
- The free version is almost too basic to be truly useful
Pricing:
Burp Suite is available in Enterprise, Professional, and Community editions. The Enterprise and Professional editions have a free trial period available.
- Enterprise: Three tiers are available in the Enterprise edition. Starter costs $6,995 per year for five scanning agents; Grow costs $14,480 per year for 20 scanning agents; and Accelerate starts at $29,450 per year for 50 or more scanning agents.
- Professional: $399 per user per year
- Community: Free
GitLab Ultimate
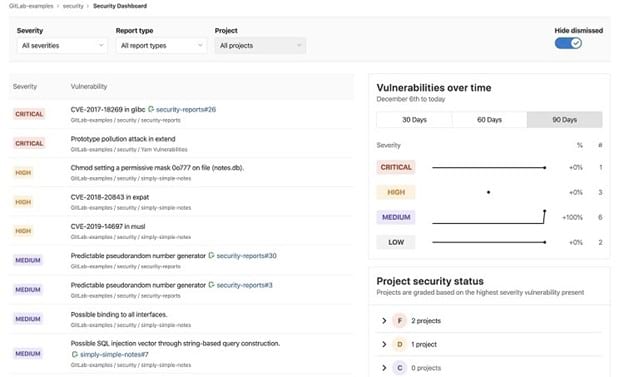
If your organization is looking to manage risk and gain access to the most valuable security monitoring capabilities for applications, GitLab Ultimate has the basic features you want.
With Ultimate, you can deploy security testing for your applications. You also have the ability to deploy preventive measures to enhance security for the applications and network.
GitLab Ultimate provides the basics for managing application security, helping your organization achieve the regulatory compliance standards you need to meet. You also can choose how you want to manage your security risk.
Ultimate is not going to meet the needs of your organization if you have advanced application security needs. It is more of a starter option. However, its price point reflects this, so you won’t break the bank if you choose to deploy Ultimate.
You’ll receive an easy-to-use dashboard that provides visibility into the security risk for your organization. It also can provide advice on how to manage that risk and on which application security areas need fixing immediately.
Pros:
- Works well for small organizations that have a tight budget
- The interface is extremely easy to use
- GitLab is a popular choice for coders, and Ultimate offers a nice extension of those features
- Excellent risk mitigation features for security risk
Cons:
- Doesn’t have the high-end security monitoring features that some of the others on this list provide
- For a busy network, add-on costs for extra storage and for CI/CD minutes can add up quickly
Pricing:
GitLab Ultimate costs $99 per user per month and there is a free 30-day free trial available to test it out.
How to Pick Your Best Application Security Tools
Step 1: Consider Your Level of Expertise
If your organization has a dedicated security team in place that can manage and operate the application security tool that you select, selecting a tool that has advanced features is a smart idea.
However, if you need help with managing your security requirements or if you only have time to handle the most basic features in your security tools, there’s no need to consider high-end tools.
The strong interface in SonarQube gives those who are looking for the basics in managing application security a great starting point. For tools that provide the highest levels of security, look toward Checkmarx and Veracode.
Step 2: Plan for the Growth of Your Organization
If your organization is small and budgets are tight, you may want to start with an inexpensive application security tool that provides the basic features.
If the plan is for the organization to become larger in short order, however, you don’t want to have to start over with a new tool. So seek out a tool that can meet the needs of your small organization now and that allows you to easily expand the number of users in the future.
One of Veracode’s best features is its ability to work equally well for organizations of varying sizes.
Additionally, look for a tool that has the ability to expand its security features as your demands change in the future. An application security tool that has multiple subscription tiers is a good choice if your organization plans to grow significantly in the near future. Both PortSwigger Burp Suite and SonarQube deliver a wide range of subscription tiers and fit this use case.
Step 3: Think About Using an On-Premises Solution Versus a Cloud Solution
Some organizations prefer to have an application security tool that will run as on-prem software, meaning your organization manages and operates the software on-site. Other times, you may want a tool that operates in the cloud.
Cloud-based tools can be advantageous because you don’t have to worry about updating the software yourself. However, some organizations feel more comfortable with having security software hosted locally.
Two strong cloud-only tools are GitHub Ultimate and Fortify on Demand. If you need the flexibility of either an on-premises or cloud-based solution, Checkmarx has strong capabilities for both of these types of use cases.
Step 4: Make Sure the Tool Is Trustworthy and Matches Your Specific Requirements
Finally, you need to ensure that the tool you select is able to match the security requirements and regulations that your organization needs. If you have vendors or customers that demand specific security requirements, take these into account as well when selecting a tool.
Two of the most trustworthy application security tools are Veracode and SonarQube, as both have loyal customer bases and many years of successful performance under their belts.

