CIS Vs. NIST: Side-by-Side Comparison
There are multiple cybersecurity frameworks that organizations can use to improve their security posture. Perhaps the two most trusted sources for providing these standards are the Center for Internet Security (CIS) and the National Institute of Standards and Technology (NIST). Yet, despite the abundance of trusted frameworks, organizations still face the proverbial Goldilocks dilemma.
On the one hand, you want a framework that’s not too hard to implement, yet on the other hand, you don’t want one that’s too soft on your security defenses. So the real challenge is finding the“just right” standards for your organization. With this in mind, we’ll compare the two dominant compliance frameworks, namely, the CIS Critical Security Controls (CSC) and the NIST Cybersecurity Framework (CSF).
Our Recommendation = Use the CIS Critical Security Controls (CSC)
The main strength of CIS Controls lies in the organization itself. Unlike NIST, the CIS is not a function of government. Instead, the organization is drawn from all sectors, including government, manufacturing, vendors, academia, and research.
CIS membership also spans the globe, so its standards apply broadly to organizations regardless of industry, size, or country of operation. Therefore, the resulting guidelines are less concerned about regulation and compliance and more focused on defense and mitigation.
Specifically, the Critical Controls are detailed and explicit. These Controls offer practical step-by-step guidance for adoption and implementation. In addition, the documentation condenses expert-level cybersecurity knowledge using a common language that technical and non-technical people can agree on. This lingua franca is especially helpful for cross-functional teams developing and implementing a security program.
Additionally, the CIS Controls covers all common cybersecurity threats. To make it easier to prioritize, the latest version of the CIS Controls organizes the controls into three Implementation Groups (IGs). Just deploying Implementation Group 1, which covers 15 of the 18 CIS Controls, is sufficient to protect your organization against 85% of the most common internet threats.
In short, you can think of the CIS Controls as a framework of frameworks. It draws from the most widely used frameworks, including NIST frameworks, and condenses the ideas into cyber practices you can implement to get specific results. The action-oriented format is especially attractive for organizations lacking a comprehensive security policy and doesn’t know how to prioritize implementation actions.
When to Implement NIST Frameworks Instead
For full disclosure, it’s important to mention that this CIS vs. NIST comparison isn’t intended to crown a clear winner. Instead, these cybersecurity control frameworks are more complementary than they are competitors. Many organizations implement both frameworks for holistic cybersecurity.
Therefore, the primary intent of this comparison is to help you determine which framework to start with. With this in mind, there are explicit scenarios where the NIST Framework is the more relevant approach.
Remember, NIST is a federal agency under the Department of Commerce. Therefore, all Federal agencies must comply with NIST standards by default. Similarly, government contractors are required to comply with NIST standards.
Additionally, federal supply chain contractors must comply with one or more NIST special publications. For example, government contractors are typically required to comply with NIST Special Publications 800-53 and 800-171. In short, NIST compliance is mandatory for public and private companies that process, store, or transmit government data.
Some NIST mandates reach further down the federal supply chain than others. For example, many NIST standards apply only to prime contractors. Prime contractors work directly with the government. Other standards, such as the NIST 800-171, also apply to subcontractors working with prime contractors.
Private businesses that hope to bid for government contracts in the future may also want to prioritize NIST standards over CIS standards. NIST compliance, in this case, offers a clear competitive advantage. Early compliance also helps beat the last-minute rush when it’s time to bid for contracts.
NIST standards aren’t only for private companies that do business with the government. Notably, the NIST CSF works best for organizations with a mature security posture. In addition, these frameworks are more customizable to an organization’s resources, goals, needs, and risk appetite. As a result, it’s perfect for bolstering an existing security policy.
In short, CIS is the top choice for organizations looking to execute security controls. However, NIST is the better option for mature organizations more interested in diagnostics, organization, and planning. Where CIS Controls tell you what to do, NIST frameworks help you narrow down the areas for improvement in the context of your environment.
Pricing – Is CIS or NIST Cheaper?
Both CIS and NIST frameworks are free to download. You can visit the respective CIS or NIST websites to download the documentation for free. However, there are some differences in how you access the documentation.
The NIST CSF is undoubtedly more accessible. You only need to visit the NIST Website and download the document. It’s available in PDF, Excel, and a downloadable presentation.
You also don’t need to sign up to the NIST website or create an account. Instead, you simply click the format you want to download, and you’ll have it in no time.
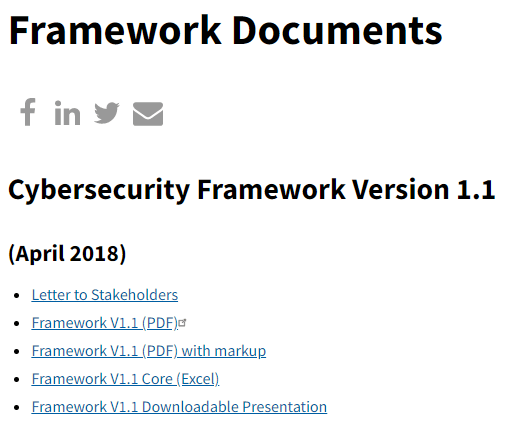
Accessing the CIS CSC is a little more complex but manageable. Again, the document is free to download from the CIS website. However, you’ll need to create an account, which is a simple and quick process. The account is free.
The CIS does offer paid membership. Unfortunately, the free version of the CIS Controls is only available in PDF. You’ll need to pay for a CIS SecureSuite Membership to access the document in alternative formats and unlock additional perks.
Membership pricing starts at $1,452 annually for organizations with up to 49 members. You can get a 10% discount by purchasing a two-year membership and a 15% discount if you opt for a three-year membership.
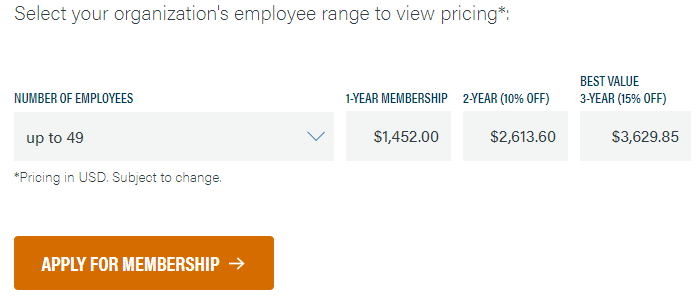
The NIST Framework is the better deal from a purely cost perspective. You don’t have to jump through hoops or pay a premium to access the documentation. However, price is hardly the only consideration when choosing between CIS and NIST.
CIS vs. NIST Use Cases
Winner = CIS
CIS and NIST frameworks share many similarities. Still, they are fundamentally different frameworks. For example, the CIS Controls are a Control framework, while the NIST Cybersecurity Framework is a Program framework. This difference is crucial when determining a framework’s best use case.
Control frameworks, like the CIS, focus on:
- Identifying baseline cybersecurity controls
- Assessing the organization’s technical capabilities
- Prioritizing implementation
- Creating an implementation roadmap
Conversely, Program frameworks like the NIST CSF focus on:
- Assessing current security program
- Building a comprehensive security program
- Measuring cybersecurity maturity against industry standards
- Simplifying communications with business leaders
The NIST frameworks assume at least some cybersecurity maturity. For instance, it assumes you already have a comprehensive security policy that you want to improve. It also takes that you have baseline cybersecurity standards.
In short, the NIST framework allows organizations to understand their current cybersecurity posture, visualize the desired security state, and establish a timeline for getting there.
Most organizations are interested in foundational questions, such as what to do, when, and how to do it. Therefore, the CIS framework is more accessible for most organizations regardless of their security posture.
CIS vs. NIST Adoption and Implementation
Winner = CIS
The NIST Framework is more widely used than the CIS controls. It’s not so much that the NIST Framework is better. A more straightforward explanation is the framework has been around for longer and is more familiar to most security personnel. NIST has been around since 1901, while the Center for Internet Security was founded in 2000.
Regardless, the CIS Controls are notably easier to implement. This is especially true for small businesses taking their first steps towards establishing a cybersecurity baseline. In addition, the documentation offers clear and actionable steps for neutralizing the most pervasive cyber-attacks.
The CIS Controls structure makes the recommendations easy to implement, even for non-technical personnel. It focuses on 18 critical controls, which reduce the implementation scope. Furthermore, the document categorizes the controls into priority groups as such:
Implementation Group 1 (IG1) – This includes the basic cyber hygiene controls that apply to everyone across the board.
Implementation Group 2 (IG2) – This includes foundational controls for organizations that handle sensitive data.
Implementation Group 3 (IG3) – For more mature organizations with in-house security teams for risk management, penetration testing, application security, etc.
In short, there is no ambiguity when applying the CIS Controls. For example, a small business without a security policy can start with IG1 controls to meet the minimum cybersecurity standards. Similarly, an enterprise with dedicated IT personnel may implement IG2 to meet regulatory compliance commitments.
By contrast, the NIST CSF puts the onus on individuals to choose recommendations based on the organization’s security maturity. This format may work well for a mature organization with clear cybersecurity goals. However, it might be too complex for less mature organizations to take their first steps towards compliance with cybersecurity best practices.
CIS vs. NIST – Cross-Compatibility with Compliance Frameworks
Winner = CIS
Both CIS and NIST conform with other cybersecurity standards and compliance frameworks. However, CIS Controls and Benchmarks do a better job of mapping into different standards. As a result, CIS documentation offers a terrific launching pad for complying with other regulations.
For instance, CIS Benchmarks and Controls cover change control, access control, patch management, and firewall and router configurations. Incidentally, the PCI DSS has these compliance requirements. Similarly, the CIS Controls and Sub-controls cover many security rules in the Health Insurance Portability and Accountability Act (HIPPA).
Furthermore, the CIS Controls V7.1 map directly to the NIST CSF. Other regulatory frameworks covered under CIS standards include GDPR and ISO/OEC 27001. Of course, this isn’t to say that implementing CIS standards guarantees compliance with regulatory frameworks. However, it’s still a great starting point.
Conversely, the NIST Framework is primarily designed to be a stand-alone resource. This makes sense since most NIST recommendations relate to government agencies and private contractors working in the federal supply chain. Where NIST is geared toward regulation and compliance, CIS covers all organizations regardless of industry, size, country, or compliance requirements.
CIS vs. NIST – Coverage
Winner = NIST
CIS frameworks have the edge over NIST in many areas. However, NIST documentation is far more comprehensive and offers better cybersecurity coverage than CIS. This advantage is especially beneficial for mature organizations that want to evolve and grow their security policies.
CIS standards are mainly captured in the CIS Controls and CIS Benchmarks. However, NIST provides extensive documentation in its Special Publications (SP), including:
- NIST Cybersecurity Framework (CSF)
- NIST SP 800-53
- NIST SP 800-171
- NIST SP 800-37
These are just some of the more popular frameworks. This diversity also means you get highly targeted standards. For example, NIST SP 800-171 covers how to safely handle controlled unclassified information (CUI). For their part, the NIST 800-53 standards are arguably the most comprehensive cybersecurity framework spanning more than 900 requirements.
In short, CIS recommendations are terrific for bringing your security posture up to par with industry standards. However, if you want to bid for Department of Defense (DoD) contracts or other high-level contracts, you are better off following the NIST standards, such as NIST SP 800-171.
CIS vs. NIST – Tooling
Winner = CIS
CIS and NIST standards offer comprehensive and consensus-driven recommendations for improving your security posture. However, these documents span hundreds of actionable items. Therefore, applying these standards manually isn’t an option for most organizations.
Tooling helps to simplify the implementation of these standards. For instance, it is helpful to have a tool to detect non-compliance. It’s even better to have a tool that automates remediation or offers guidelines for remediating non-compliant areas.
Many third-party tools help with CIS and NIST compliance. But, we’ll focus on native tools. These are tools developed by either NIST or CIS to help implement their recommendations.
The CIS offers the CIS-CAT. It’s an assessment tool that lets you scan your systems for compliance. You’ll also receive a score from 1-100 and actionable remediation advice to help you with compliance.
Additionally, CIS Members get access to Build Kits. These are in shell scripts for Linux and Group Policy Objects (GPOs). The Build Kits let you automate compliance with selected CIS Benchmarks.
On the other hand, NIST offers a reference tool. It helps sort the NIST Framework by informative references, categories, subcategories, and functions. You can also search for specific keywords to narrow down the areas for implementation.
However, the NIST CSF Reference Tool doesn’t scan your system to check for compliance. You also cannot automate any of the implementation recommendations. Instead, it’s simply a tool for making the complex and extensive NIST Framework more accessible.

