How To Prevent Data Leaks
Data breaches are devastating, but they require some effort and expertise for hackers to execute. On the other hand, data leaks are just as dangerous but can happen much more easily because they occur primarily due to human error. The effects of a data leak can be far-reaching, including financial loss, reputation damage, steep fines from regulatory authorities, and even criminal prosecution.
Here’s how you can prevent data leaks within your organization.
Step 1 – Conduct Data Inventory and Classification
If you don’t have a complete picture of all your data, it is difficult to tell what information needs to be protected. You may also be compelled to inventory your data by regulations such as the California Consumer Protection Act (CCPA) or General Data Protection Regulation (GDPR).
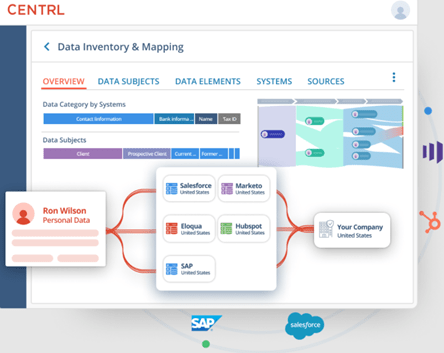
The best place to start your data inventory is to assess where your data comes from. Familiar sources of data may include:
- Internal business systems such as point-of-sale or accounting systems
- Third-party systems such as electronic data interchange (EDI)
- Cloud-hosted and cloud storage systems
- Internet of Things (IoT) devices such as smartphones, cameras, and sensors
- External data sources like public information, geolocation, and maps
It’s generally worth assigning a project manager to oversee this process. You can also recruit supervisors from each department who report to the project manager. The supervisors will act as the contact people to discuss their departments’ data.
Next, identify the specific type of data your company collects, stores, and transmits. Common types of data in this case include:
- Personally identifiable information (PII) – PII includes first and last names, email addresses, business or home addresses, bank account and credit card numbers, medical records, taxpayer identification numbers (TIN), and social security numbers. The information may also extend to date of birth, age, gender, phone numbers, and license numbers.
- Intellectual property – This information includes sensitive and proprietary business data, including human resource records, product designs, financial records, internal reports, and internal correspondence.
- Customer information – This data may include purchasing history, verification codes, shipping addresses, and phone numbers.
- Finally, you can classify your business data based on its type and sensitivity. Typical data classification categories include:
- Public data – Public data is generally the lowest data classification. It includes information that is available to the public. This type of data may consist of press releases, job descriptions, and other data that can be freely used and redistributed without ramifications.
- Internal data – As the name suggests, internal data is meant strictly for internal company employees and personnel. Examples here include business plans and internal-only memos.
- Confidential data – Confidential data refers to data that requires specific clearance or authorization to access. Such information may include mergers and acquisitions documents, cardholder data, and Social Security numbers.
- Restricted data – Restricted data refers to data that may result in adverse effects if exposed. These consequences may include reputation damage, legal fines, or criminal charges. Examples of restricted data may include financial data, patient health data, and proprietary information.
Step 2 – Implement Access Control
Data inventory and classification make it easy to determine who should have access to which data. After all, you want to ensure that the right people have access to the correct data. You can start by assessing the access levels and controls in place currently, which makes it easier to identify flaws in the current process.
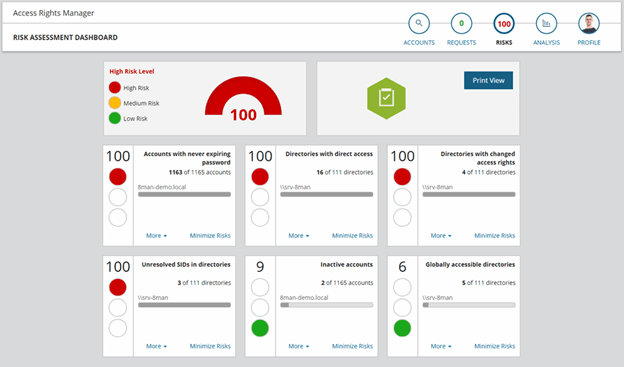
You can refer to your applicable regulations to determine the type of access control you need to implement. For instance, you’d need to restrict access to personal financial information under the Payment Card Industry Data Security Standards (PCI-DSS). Similarly, the Health Insurance Portability and Accountability (HIPPA) regulations mandate access to personal health information on a need-to-know basis.
It is also good to automate account provisioning, de-provisioning, and password management. This strategy will help reduce the workload for employees tasked with account administration. Similarly, segregating access using roles also helps with access control. For instance, only developers and their direct managers should access the developer environment.
Other possibilities for improving access control include:
- Auditing all access
- Controlling remote access
- Monitoring access patterns for unusual activity
- Applying the principle of least access
- Centralizing access management
- Creating and defending chokepoints
- Updating access control rules regularly
Step 3 – Encrypt Your Data
Besides categorizing data and controlling who has access to it, data encryption adds an extra layer of security. Data encryption refers to converting information into ciphertext, a kind of encoding that requires a unique decryption key to convert it back into readable form. You can encrypt data during storage or transmission.
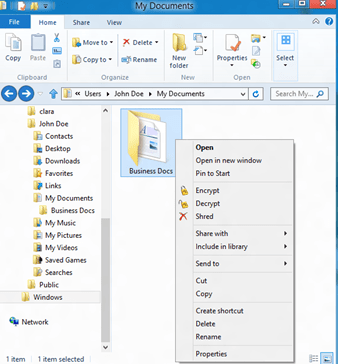
There are many data encryption solutions to help you protect data at scale. These tools use advanced encryption algorithms to encrypt data. They also help set access policies, manage keys and passwords, and deploy encryption.
Some of the features to prioritize when searching for an encryption solution include:
- Strong Encryption Standards – Advanced Encryption Standard (AES) with a 256 key is currently the strongest encryption available. It is also the industry standard.
- Encrypt Data in Transit – A good solution should use transport layer security (TLS) to encrypt data during transmission.
- Encrypt Data at Rest – Choose a tool that can encrypt data regardless of where it is stored, including employee workstations, databases, file servers, and the cloud.
- Key Management – This feature is critical for encryption management. Choose software that quickly generates encryption keys, gets them to the right hands, and destroys the keys in case of revoked access. The tool should also be able to back up the keys.
- Granular Control – A good encryption tool should allow you to encrypt specific data without requiring you to encrypt all data stores regardless of their information.
- Consistent Encryption – Insist that your solution encrypts sensitive information even when they are modified, emailed, or copied.
You’ll also need to identify which data to encrypt. Again, you can refer to the relevant compliance standards for guidance. Furthermore, consider the worst-case scenario if a specific data set is compromised. This approach should clarify which data sets to prioritize for encryption.
Finally, don’t forget to encrypt your backups. This step is vital for covering all your bases. You may also be subjected to fines or criminal prosecution if your unencrypted data is leaked, subject to relevant compliance regulations and standards.
Step 4 – Secure All Endpoints
An endpoint refers to any remote point that can communicate with your business. This includes devices such as computers, laptops, and smartphones. So again, you can start by taking a complete inventory of all your endpoints.
Furnishing employee endpoints with anti-virus software, automated application updates, and multi-factor authentication is a good start. Next, it’s worth deleting any unused or unnecessary employee or customer data discovered during the inventory from endpoint devices.
Then, it’s worth enrolling the help of advanced endpoint protection software. For instance, the software may automatically use threat intelligence to detect and stop potential attacks.
Step 5 – Don’t Forget Third Parties
Third-party data leaks can be just as likely and devastating as internal leaks. Fortunately, there is much that you can do to avoid or minimize the possibility of a third-party data leak.
The first line of defense is thoroughly vetting any third parties you work with. Automated security questionnaires and external attack surface assessments are great ways to determine your vendors’ security posture.
It is equally prudent to have a centralized communication platform for your third-party vendors. Security teams and vendors can openly discuss any security gaps or concerns. This line of communication should also extend to the remediation phase. Vendors should report the steps to resolve security concerns within a specific time frame, such as 72 hours.
It is also worth incorporating cyber risk into vendor contracts. For instance, you may require that any third-party vendors that handle credit card information must maintain a security rating above 900. This strategy is perfect for holding vendors accountable for your organization’s data leak prevention program.
Lastly, monitor your vendors consistently for security risks. Vendors’ security controls are bound to change over time, and you need to be aware of their security posture throughout the contract term. For instance, keeping track of the vendor’s security rating over time is a good indicator of their commitment to cyber security.
Step 6 – Conduct Employee Security Awareness Training
Most data leaks happen as a result of human error. So all the data leak prevention measures won’t help if your employees put your data at risk. Employee security awareness training complements the efforts mentioned above perfectly. This training should include all employees connected to your company network.
Some of the topics to cover during security awareness training include:
- Physical security
- Phishing
- Desktop security
- Malware
- Password security
- Wireless networks
- Ransomware
- Information security
- Social engineering
- Removable media
- Incidence response
- Browser security
- Mobile security
- Business email compromise
Admittedly, it is challenging to create a cybersecurity course in-house from scratch. But there are plenty of companies that provide comprehensive training. Some great examples here include Curricula and Mimecast. Finally, remember that practical security awareness training is continuous.
Common Problems When Attempting to Prevent Data Leaks
Protecting company data should be a priority for any company. The steps we’ve outlined are perfect for getting you started in the right direction. However, some challenges are bound to come up during implementation. Understanding these challenges is crucial for helping you develop a robust strategy right out of the gate.
Below are some common challenges you’re likely to face when embarking on data leak prevention.
Lack of Executive Buy-In
Preventing data leaks within an organization sounds good on paper. But the process can be exhausting for everyone involved. You’ll likely need to purchase new and expensive software. Implementing new data protection policies also requires a shift in the company culture. Furthermore, they’ll probably be at least some disruption in workflow.
Securing executive buy-in can be challenging given these circumstances. There’s always the temptation to maintain the status quo, especially if your company hasn’t yet been the victim of a significant data breach.
The best strategy is to arm yourself with numbers and results. C-suites are always interested in metrics like financials and brand image. Show them how implementing your Data Loss Prevention (DLP) program will guarantee compliance, boost reputation, and save costs on potential breaches.
Similarly, highlight how your new access management policies will make data transfer to the right people more efficient and improve productivity within the workforce.
It is also necessary to quantify the risk of maintaining the status quo. This is especially true when scaling the organization. Explain to C-suite the actual cost of data leaks with examples of similar organizations.
Finally, recruit the employees responsible for day-to-day workflows, such as mid-level managers, to your cause. It is much easier to get executive buy-in when the higher-ups see your peers already understand the value of your proposed changes.
Government Regulation and Legal Requirements
Data privacy concerns have led to stringent government and legal regulations such as the California Consumer Privacy Act (CCPA) and General Data Protection Regulation (GDPR). These regulations are well-meaning but present some challenges in how organizations handle data.
These regulations change often, can be difficult to understand, and are challenging to comply with when sending data across global networks. However, security tools with built-in compliance help overcome these challenges.
It is also worth having a dedicated data controller or data protection officer (DPO). This individual is responsible for compliance with data protection principles. This position is crucial in large organizations that process large amounts of personal data.
Exponential Data Growth
Data continues to grow exponentially, which can put a strain on even the best data privacy policies. This growth can also increase the risk of data leaks and the costs associated with preventing the said leaks. The key to this challenge is efficient data management.
Cloud-based data archiving is a practical first step to managing data growth. This process involves identifying inactive data and moving it to separate long-term storage. This data may be retrieved at any time for business reasons but is separated from day-to-day information. Fortunately, data archiving systems can help to automate this process.
You can also take advantage of cloud-based storage consolidation. Here, the cloud service provider is responsible for consolidating, managing, and maintaining your data in the cloud. This frees up your IT department, reduces administrative complexity, and offers centralized and managed storage.
Lastly, take advantage of technology to store only the needed data. For example, various tools can help eliminate duplicate or irrelevant data.
Controlling the Cost of Data Leaks
Sometimes information may be leaked regardless of your best efforts. Therefore, it helps to have contingency measures against any eventuality.
Automated incident response is a reasonable precaution in case of a breach or leak. SIEM tools that incorporate artificial intelligence can help to automate responses such as identifying potential leaks and alerting incident response and remediation teams,
Lastly, a cyber insurance protection policy can come in handy in the unfortunate event of a significant leak. It is a reactive approach, but it can help mitigate the financial impact of data leaks.
The insurance premiums may hire forensic experts or acquire additional resources to contain the incidents. The insurance payout can also help cover business losses such as repairing reputation damage or legal expenses.

