Best Container Security Solutions
Containers play a key role in creating cloud-native applications. A container allows the application to run quickly and efficiently, as it holds all of the code and other items needed to run the app.
As you begin deploying containers, though, you’ll quickly realize you need to secure them. Because containers frequently undergo updates and changes, the possibility of introducing vulnerabilities seems to never disappear.
Container security tools give container-based systems the protection they need, securing all aspects of the container and its related components. Use our list of the best container security solutions to find the right option for your network usage.
Aqua Security
If you like the idea of selecting a container security solution that has a track record of success, Aqua Security is one of the pioneers in this space. It remains a popular selection, as the early adopters who began using Aqua Security often will stick with it.
One of the most popular aspects of this solution is its Dynamic Threat Analysis. As Aqua Security analyzes images, its DTA measures and ranks the potential for threats, based on abnormalities in behaviors and the potential severity of the vulnerability. DTA is an advanced threat analysis tool that outperforms many other options on the market.
Aqua Security can manage your network firewall to prevent images without authorization from operating. It checks all images for any security issues, such as viruses and malware.
You can select among either cloud-based or on-prem deployments of Aqua Security, giving it excellent flexibility. It also works with either Windows or Linux container environments. Additionally, it scales nicely to match the requirements of a growing organization.
If your enterprise runs a Kubernetes container orchestration system, Aqua Security matches up especially well with Kubernetes.
Pros:
- Its security features are among the best in the industry
- Product routinely undergoes updates to incorporate the latest technology
- Doesn’t require much time to set up and begin using
- Does a good job of minimizing false-positive readings
Cons:
- Self-training materials are not quite as readily available as they could be
- Costs a bit more than some others
Pricing:
- Team: $849 per month for up to 10,000 Aqua units
- Advanced: $2,099 per month for up to 25,000 Aqua units
- Enterprise: Custom price quote available
You can request a free trial or you can schedule a demo from Aqua Security
Sysdig
When you want a unified security system for managing both your container and cloud deployments, Sysdig is a very popular choice. It is able to scan containers and hosts at the same time, which means you can operate one tool to do both jobs, rather than having to run separate tools.
Sysdig offers multiple automated tools for local scanning as well. Deploying Sysdig allows you to validate your compliance across multiple standards, including for NIST and SOC2.
It works especially well with Kubernetes if you are running this open-source orchestration system. It also has compatibility with Prometheus, which is another open-source tool used in container monitoring.
Customers really appreciate the level of customer service and technical support options they receive with Sysdig. If you anticipate you will need significant help with the setup or operation of your container security solution, Sysdig will be with you every step of the way.
Pros:
- Offers some of the best customer support options among the tools on our list
- Gives you a high level of flexibility in choosing how the scan process runs
- Has an above-average set of security features
- The user interface is easy to learn, and it provides valuable information
Cons:
- Tends to generate false positives in the early days of the deployment, until you have the chance to adjust the settings to match your network
- It sometimes produces such a large amount of information that reports are slow to load
Pricing:
- Sysdig Monitor: $20 per host per month, but it is a container monitoring tool
- Sysdig Secure: $60 per host per month for a container security tool
You can request a free trial or you can schedule a demo from Sysdig
Snyk
If you have a focus as a developer, Snyk is one of the top container security solutions. It offers a wide range of useful integrations aimed at coding and developers, including with Jira Software and GitHub. If your developers do not have extensive experience with fixing container issues, Snyk can simplify the process for them.
If you have concerns about falling victim to new vulnerabilities, Snyk has particular strength in monitoring the system for the newest vulnerabilities. Its database of vulnerabilities receives constant updating, ensuring you always have the highest level of protection for your containers. Should your network receive exposure to a new vulnerability, you can receive alerts in the best way for your needs, including through Slack or Jira.
Snyk has a well-designed integration with the Kubernetes container orchestration system. It also supports multiple programming languages to aid developers.
Pros:
- You’ll receive plenty of information about each vulnerability, including potential suggestions for mitigating them
- Integrates closely with Jira Software, GitHub, and GitLab, making it especially beneficial for developers
- The database of potential vulnerabilities is accurate and constantly up to date
- Offers a responsive customer service team
Cons:
- Could use an improved reporting function
- For those who have a large number of vulnerabilities in their containers, it’s difficult to filter the list of results
Pricing:
- Free: The Free tier allows for an unlimited number of developers to use it, but it limits the number of tests you can run.
- Team: The Team tier costs $23 per developer per month with an unlimited number of tests for the container features only (and up to $96 per developer per month for all Snyk features).
- Business: The Business tier costs $33 per developer per month with an unlimited number of tests for the container features only (and up to $139 per developer per month for all Snyk features).
Qualys
The Qualys Cloud Platform delivers more than a dozen security applications under one package, including the Qualys Container Security application. If you are running a network at a large organization, you will appreciate all of the security applications under the Qualys umbrella.
With its Container Security app, Qualys uses its various sensors to constantly monitor your IT assets and your containers. It works with assets on-premises, in the cloud, or at endpoints.
Its container sensors will ensure that the container images exactly match the original images. If not, Qualys can automatically block certain behaviors, if desired.
Additionally, Qualys can sort the threat level for each vulnerability it detects, so you can make the decision on how to proceed. It will thoroughly investigate any high-severity vulnerabilities, providing the information you need to decide how to proceed.
Qualys offers constant monitoring of the containers as they run, giving you real-time information on any behavioral events. It then displays the information on the Qualys dashboard, giving you the ability to investigate further.
Pros:
- Qualys is able to monitor all of your IT assets together, including containers, creating a high level of efficiency
- Makes any security configuration issues easy to spot
- Monitoring functions are in constant operation and are highly accurate
- Sorts each of the vulnerabilities based on the threat level, so you can prioritize your response
Cons:
- Reporting functions don’t allow for enough output formats
- The user interface could use a better overall design
Pricing:
Qualys does not make its pricing publicly available. You can request a quote from Qualys, or you can try it out with a 30-day free trial period. You can request a demo as well.
Palo Alto Prisma Cloud
Palo Alto Networks is one of the biggest software security providers for enterprise networks. Thanks in part to its size, Palo Alto was able to strengthen its container security solution, called Prisma Cloud, by acquiring other solutions. If you have some familiarity with container security tools like Twistlock and Aporeto, their features now are part of Prisma Cloud after Palo Alto acquired them.
Prisma Cloud offers extensive support for AWS and Azure, making it a strong selection when you are running an enterprise network. It also closely integrates with and supports Kubernetes.
With the wide range of security features in Prisma Cloud, it can be challenging to use the software to focus on container security alone.
As an advantage of the power behind Prisma Cloud, though, it is able to scan for vulnerabilities in containers in real-time. You can receive reports that reflect the vulnerabilities at any point in time, giving you the information you need to make the best security decisions.
Pros:
- Its reporting functions allow you to take a snapshot of the status of the containers at any point
- Simplifies the process of ranking the threat level of the vulnerabilities
- Delivers a host of network security features, all under one umbrella
- Its preset security policies work well for many use cases, so you can be up and running quickly
Cons:
- It may be too comprehensive for those who only want a container security solution
- Can be challenging to narrow the scope and breadth of the network scans
Pricing:
Palo Alto does not publicly release information about pricing for Prisma Cloud. You can download a Prisma Cloud pricing guide for more information. You can request a Prisma Cloud demo as well. Palo Alto offers a free 30-day trial period for Prisma Cloud.
Anchore
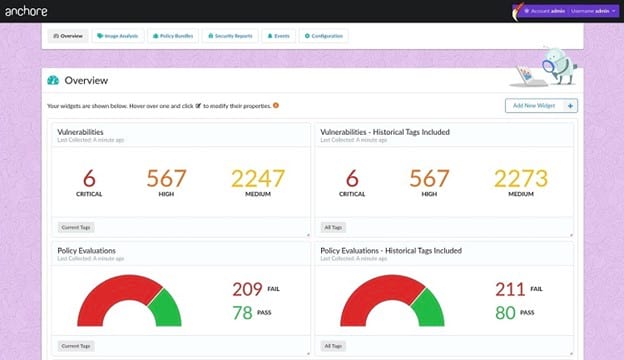
Because Anchore focuses fully on container security, it may be a preferable option for those who want only the basics. It will perform scans on both public and private images in the containers, ensuring a highly comprehensive solution.
When you set up the security policies for your containers through Anchore, it can run automatic scans to ensure they are in constant compliance.
Anchore keeps things simple when running its scans. Container images must either receive a passing grade, based on your policies, or they must fail if they have vulnerabilities. By avoiding complexity, Anchore is able to deliver its results with maximum efficiency.
Anchore is able to run either on-premises or in the cloud, giving you the versatility that you may require on your network. It has a high level of compatibility with Kubernetes.
Pros:
- The primary code is open source, so you can verify it, if desired
- It focuses completely on container security, rather than muddying the waters by incorporating other network security features
- Allows you to create highly detailed rules for container security, which enables monitoring of complex scenarios
- Anchore does not place any limits on the number of users, enabling scaling
Cons:
- It offers technical support options, but they aren’t as comprehensive as some others on our list
- Even though Anchore uses open-source software at its core, it is not free to use, as the company has enhanced the open-source software with additional tools.
Pricing:
Anchore does not release pricing information publicly. You can request a pricing quote for the Enterprise tier or for the Federal tier. You can request an Anchore demo, too.
How to Pick Your Best Container Security Solution
Step 1: Determine Your Level of Expertise
When seeking a container security solution that will meet your specific requirements, you should start the process by determining how much help you will need. If you believe you will want an option that offers responsive technical support and customer support, focus on those areas first.
Most container security tools have extensive online resources, but some of these tools can be difficult for newcomers to use. You may prefer to be able to reach out to someone for help with your specific problem.
Aqua Security and Snyk both offer responsive customer service teams. Additionally, their technical support teams do a good job of constantly updating their vulnerability databases to ensure your network has the latest information.
However, the best technical support options on our list come from Sysdig. Its support personnel will walk you through the entire setup process, if needed, as well.
Step 2: Decide Whether You Want a Comprehensive Option
When seeking the best container security software, you next should consider how container security will fit in with the overall security strategy for your network.
You may simply want a solution that focuses only on containers. You may have other software options you trust to handle other security needs on your network. Anchore is a strong contender for those who want the tool to focus completely on container security.
Aqua Security and Sysdig both offer some extra network security features, but their container security capabilities are so strong that they remain the focus of these tools.
For those who want to implement container security tools within a wide range of related network security tools, Prisma Cloud and Qualys are outstanding choices. Even better, because of the strength of the container security tools within these larger security packages, you won’t be missing out when you select them.
Step 3: Figure Out the Importance of Kubernetes Compatibility
Finally, determine the importance of having compatibility with Kubernetes in your container security tool.
Kubernetes is a container orchestration framework that helps with managing workloads within containers. If your team wants to be able to use Kubernetes within your container security solution, it’s important to select a tool that integrates seamlessly with it.
Several of the tools on our list offer close compatibility with Kubernetes, including Aqua Security, Sysdig, Anchore, and Snyk. Additionally, Prisma Cloud is a Kubernetes Certified Service Provider. Qualys offers support for multiple orchestration frameworks, including Kubernetes, but it doesn’t focus on Kubernetes like some of the others on our list.

